Vulnerability Management Evolves to CTEM
A look at Zafran's Practical Guide for Evolving from VM to CTEM
If you’ve been following me for any time, you inevitably know I’m passionate about all things Vulnerability Management. I’ve even written a book on the space, titled “Effective Vulnerability Management: Managing Risk in the Vulnerable Digital Ecosystem”.
It’s also no secret that the Vulnerability Management space is evolving quite a bit, looking to address systemic challenges on various fronts, from exponentially growing vulnerability backlogs, capacity and reliability issues with leading vulnerability databases, and organizations looking to coherently stitch together a real picture of risk across diverse environments from endpoints, Cloud, SaaS, Code, and more.
That’s why we’ve seen the rise of “Continuous Threat Exposure Management” or CTEM (we love our acronyms in cybersecurity). The term was initially coined by industry-leading firm Gartner in 2022 and has continued to gain traction.
CTEM, in short, focuses on continuously assessing, prioritizing, validating, and remediating exposures across an organization’s attack surface.
Unlike traditional Vulnerability Management, CTEM is an ongoing activity that accounts for risk exposure, utilizes vulnerability and threat intelligence, provides comprehensive attack surface visibility and coverage, and optimizes risk prioritization and remediation tied to business outcomes and impact.
Unlike traditional VM, which is often periodic, reactive, and manual, CTEM focuses on being continuous, proactive, and automated. It also utilizes attack simulation and threat validation to understand real-world risks, rather than relying on static CVEs that lack environmental context.
But what does this look like in practice?
That’s where this article comes in. We will examine Zafran’s “A Practical Guide for Evolving from VM to CTEM.”
Interested in CTEM?
Grab a FREE copy of A Practical Guide for Evolving from VM to CTEM.
5 Stages of CTEM & Setting the Stage for Evolution
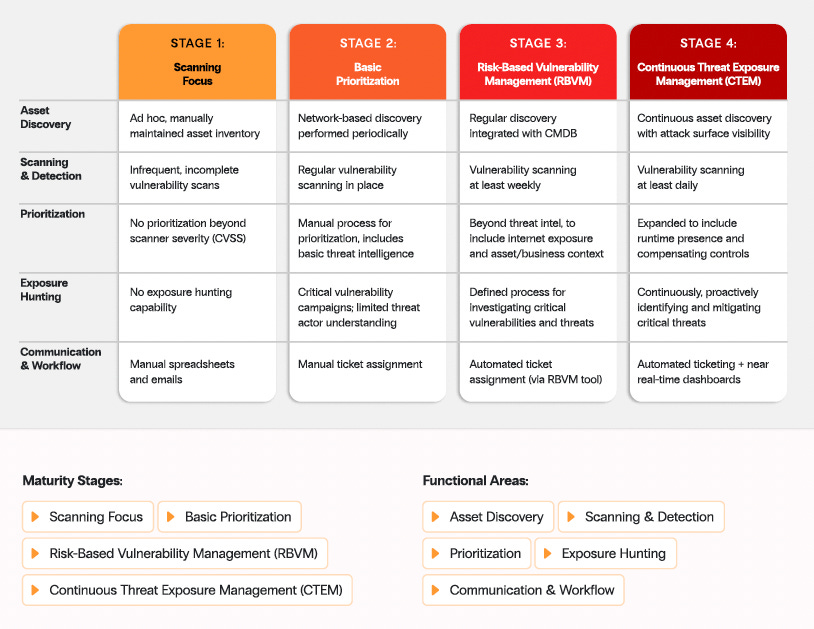
Zafran makes the case that there are five stages of CTEM, as seen below:
We will walk through each of these in the context of their guide below and unpack the broader topic of evolving from traditional VM to CTEM.
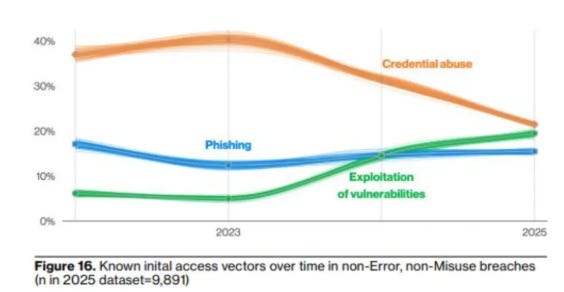
As Zafran points out, vulnerability exploitation is now the leading initial access vector in attacks, something I’ve discussed at length in articles such as:
This reality is driving organizations and the industry as a whole to take a step back and reflect on how we understand and manage risk that impacts us.
Another major problem facing the industry is that of security tool sprawl. Teams are overwhelmed by alerts, notifications, findings, and vulnerabilities, yet they lack a cohesive understanding of comprehensive risk and its potential organizational impact. CTEM aims to bring together insights from disparate tooling and disjointed assessments, moving towards an outcome-focused process.
CTEM summarizes these into core questions such as:
What matters most?
Where are we exposed?
What could realistically happen?
Are we taking action quickly and effectively?
Unfortunately, most organizations following traditional VM practices can’t answer this, as they continue to rely on snapshot-in-time assessments/scans, blanket “severity” scores without environmental and organizational context, and disjointed tooling that lacks the whole picture.
Exposure Management Model
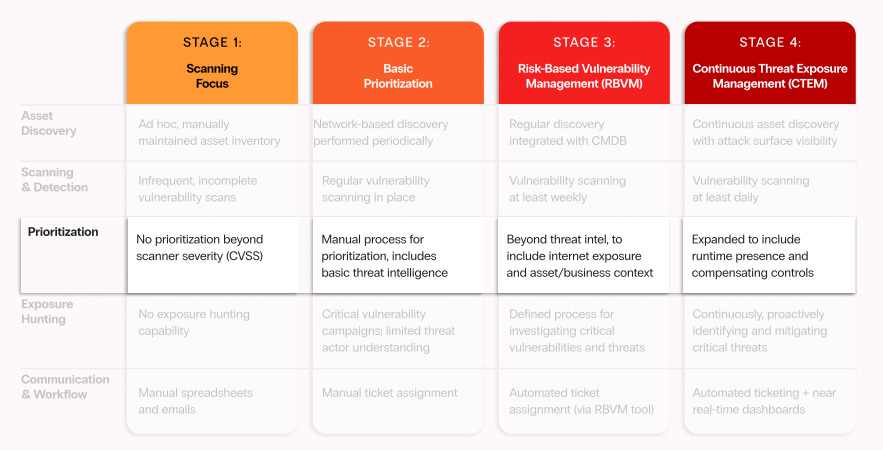
Zafran provides an Exposure Management Maturity Model for organizations looking to start with CTEM, drawing on thousands of real-world conversations with security teams dealing with production enterprise environments.
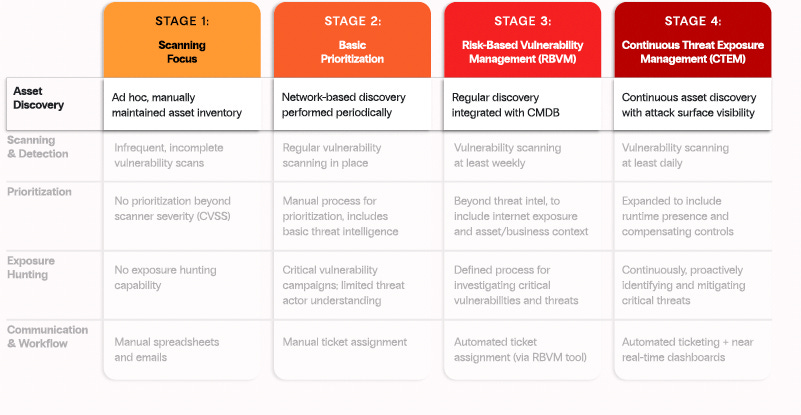
It provides a matricide maturity model with four stages and five functional areas. Below, I’ll walk through each functional area, the various maturity levels, and the associated activities.
Asset Discovery
I was pleased to see Asset Discovery as the first functional area. Not only is this routinely listed as one of the top CIS/Critical Security Controls, but as the saying goes, you can’t protect what you can’t see. Having a valid asset inventory is non-negotiable in risk management.
Despite this, many organizations struggle to obtain and maintain an accurate asset inventory. Zafran emphasizes that it isn’t enough to have a status inventory; instead, organizations must constantly discover and verify their asset inventory for effective CTEM.
This includes all asset types, such as VMs, Containers, Cloud-native assets, endpoints, servers, and even Shadow IT (including Shadow SaaS), which is not governed centrally by IT or Cybersecurity.
Not only do most organizations struggle to obtain and maintain an accurate asset inventory, but they also often struggle to assign ownership to assets once they are discovered. Zafran's guide emphasizes the importance of assigning ownership and highlights various activities that can be impacted when there is no clear accountability, including patching, incident response, and remediation.
Anyone who has done risk management in large, complex enterprise environments knows how difficult it is to identify the owners of assets and then coordinate remediation activities with associated risks. This has led to an entire category of cyber on its own, often referred to as “RemOps,” or Remediation Operations.
For effective CTEM adoption, organizations need to assign asset ownership and define SLAs for the remediation of risks associated with those assets.
Zafran advocated that organizations take various steps to mature towards Continuous Asset Discovery, such as introducing systematic network-based discovery, expanding the frequency of scans, coupling it with context-related exposure, and moving towards normalized governance with real-time visibility. This is underpinned by a unified inventory continuously sustained and aligned with accountable asset owners.
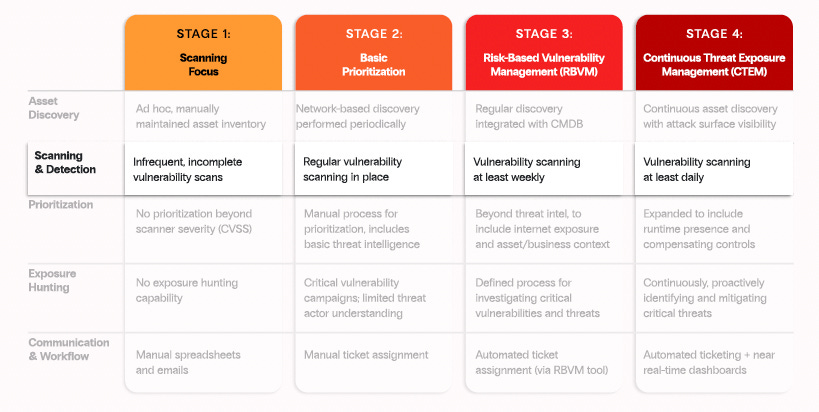
Scanning & Detection
Next in the Exposure Management Maturity Model is Scanning & Detection, which moves from infrequent and incomplete vulnerability scans to daily, ongoing, comprehensive vulnerability scanning coverage.
Zafran discusses some common gaps organizations have in vulnerability management, such as a lack of comprehensive scanning coverage, frequency, and depth. Zafran’s CTEM guide highlights the three primary means of vulnerability scanning:
We’ve seen systems evolve in the cloud-native environment for example, towards agent-based scanning to provide deeper context and visibility of findings, and contributing to the emerging category of cyber, often called “Application Detection & Response (ADR)”, which I’ve written about in prior pieces, such as:
Most organizations perform vulnerability scans on a cadence tied to compliance requirements, such as monthly or quarterly. Zafran highlights how exploitation often occurs within days or even hours, making the legacy approach of broad vulnerability scans insufficient.
Recent reports, such as Verizon’s DBIR or Mandiant’s M-Trends, highlight this decrease in exploitation windows. Recent research even shows researchers using AI and LLMs to develop exploits in minutes for CVEs, for example. The more frequently and comprehensively organizations can make their vulnerability scanning efforts, the more they can minimize their exposure window to exploitation.
The stages of maturity that Zafran’s CTEM guide covers span maturity from an initial effort to establish a cadence and improve visibility gaps, through automating and aligning with real-time changes to assets and environments.
This includes key activities such as resolving gaps in coverage, building on the comprehensive asset inventory, driving down the frequency of scanning to get closer to real-time visibility and insights, leveraging integrations with asset management tools, cloud environments, and more to trigger scans based on new assets being created, software installed, code deployed, and more.
Organizations should utilize dashboards coupled with KPIs to constantly ensure they align with asset owners' SLAs and keep organizational leadership abreast of performance and residual risks.
Prioritization
Prioritization is problematic - to put it lightly.
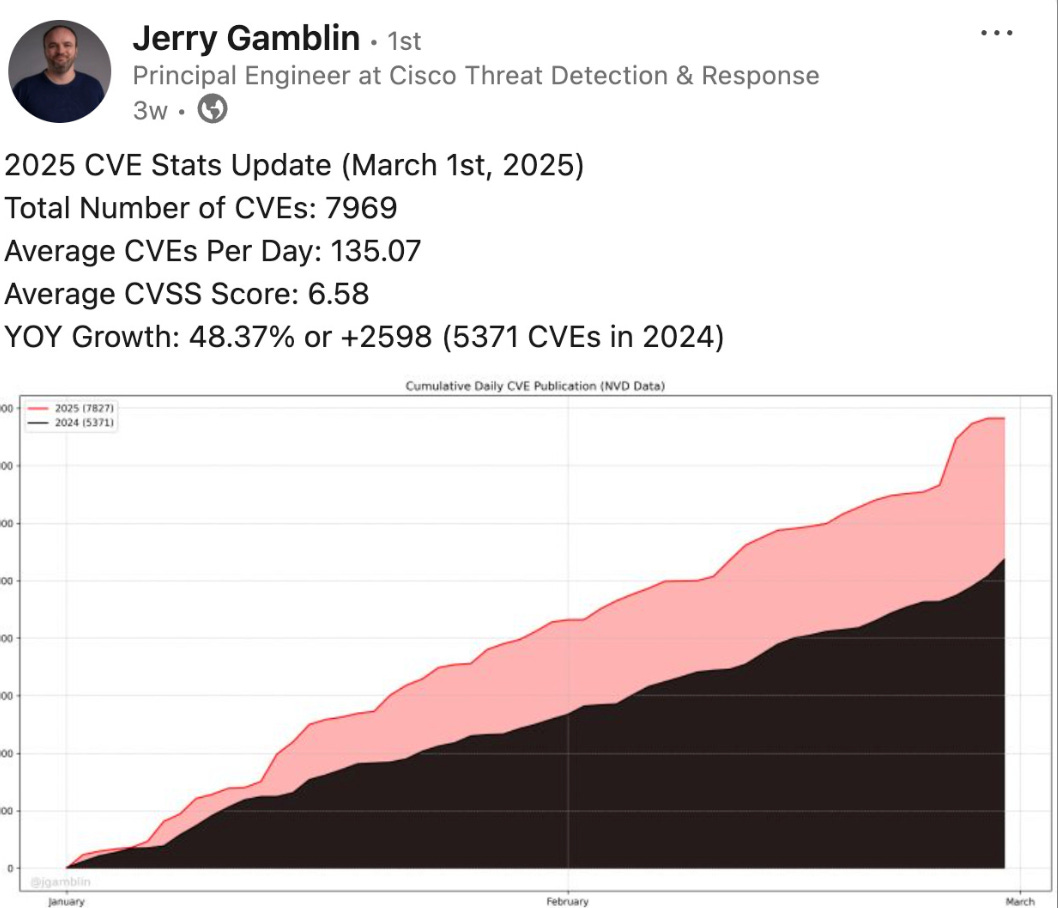
So, you’ve compiled an asset inventory and optimized your scanning. Now, you have to prioritize the remediation items you’ve found. Many organizations struggle with this activity. Despite advancements in vulnerability intelligence, such as CISA’s KEV, EPSS, and organizational context, most organizations still use legacy approaches, including base CVSS scores.
It’s a widely discussed topic that CVEs are growing exponentially YoY. Earlier this year, I published a piece on prioritization, citing metrics from Vulnerability Researcher Jerry Gamblin, which projected what 2025 would look like. So far, we’ve stayed true to the projections and even exceeded them.
Despite the growth in vulnerabilities, we know that less than 5% are ever exploited annually. Couple that with factors such as reachability, data sensitivity, business criticality, and more, and organizations are overwhelmed by vulnerability backlogs, struggling to match them with context to prioritize their remediation activities effectively.
As Zafran’s CTEM guide rightly points out, detecting vulnerabilities and exposures is merely a first step. From there, organizations must assess and prioritize accordingly to drive effective risk reduction within their organizations.
The organizational context is key here, not just CVSS base scores, which, unfortunately, is still how many organizations operate. They focus on “Critical” and “High” CVEs per CVSS, regardless of whether they’re known to be exploited, likely to be exploited, reachable, the potential organizational impact, compensating controls, and other factors.
Zafran’s CTEM Guide cites key factors for prioritization, such as:
Threat intelligence
Business criticality
Runtime presence
Internet exposure
Compensating controls
These should contribute to an organization’s prioritization activities and drive SLAs for remediation accordingly. However, it is unrealistic to expect organizations to transition from CVSS-based score prioritization to context-based risk decisions overnight. A reasonable maturity curve will unfold. This includes moving beyond CVSS, defining relevant SLAs, factoring in Internet exposure and business criticality, and incorporating runtime signals and defensive posture.
This also needs to be an iterative and ongoing activity, with organizations revisiting their prioritization framework to incorporate the latest data, additional tools, and organizational context.
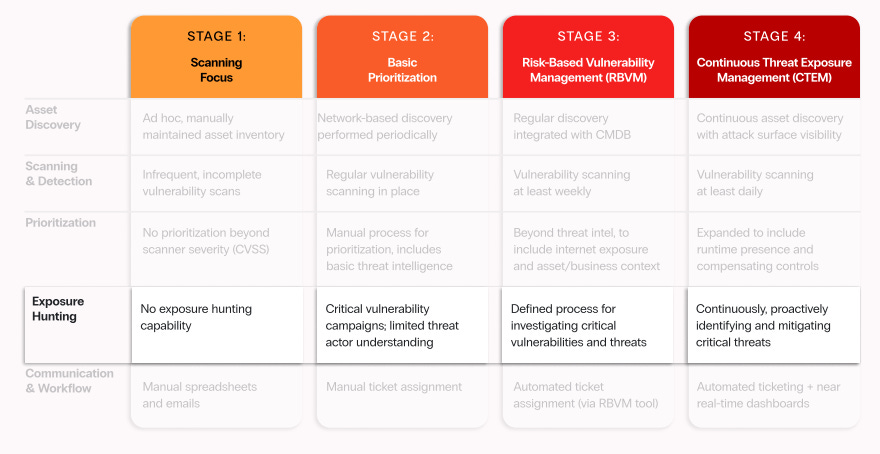
Exposure Hunting
While all the activities we’ve discussed are significant and foundational for implementing CTEM, they are reactive rather than proactive. This is where exposure hunting, as described by Zafran’s CTEM guide, comes into play, looking to identify and mitigate risks across the enterprise proactively.
Zafran’s CTEM guide notes that utilizing scan findings for known vulnerabilities is beneficial. Still, exposure hunting is the proactive activity of identifying the organization's exposures that typical alerting systems may have missed.
Additionally, organizations often have tens to hundreds of security tools, leading to a disjointed lack of a comprehensive approach to risk visibility. Exposure hunting involves proactively identifying and addressing neglected critical risks that could harm the organization before they materialize.
Much like the earlier aspects of CTEM we have discussed, this should occur on a spectrum of maturity, with an initial targeted hypothesis and hunting, then expanding to include more organizational assets, software, and environments. For those looking to dig deeper into exposure hunting specifically, Zafran has an entire series on the topic.
This maturity curve involves introducing structured investigations, expanding context, and operationalizing the activity, scaling the hypothesis-driven discovery of exposures, and validating the effectiveness of controls.
This could start by stepping back and thinking through what your typical vulnerability scans may be missing, standardizing exposure hunting processes, gaming out specific scenarios, and even moving towards automated capabilities to help facilitate exposure hunting iteratively.
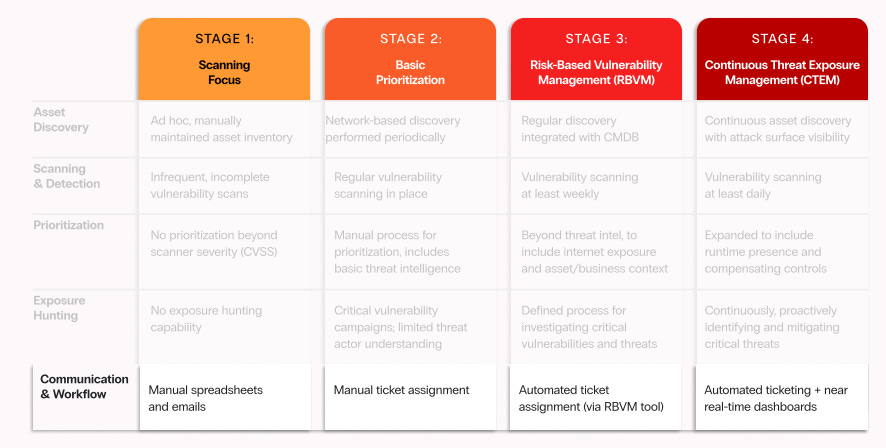
Communication & Workflow
Last but not least are the actual communication and workflows that facilitate effective CTEM within the organization. While this may seem like a trivial topic and less enticing than the exciting aspects of tools, automation, and technical vulnerabilities, the day-to-day communications and workflows of CTEM are where effectiveness can either thrive or falter.
This activity has become so problematic and critical for effective CTEM that an entire category, often referred to as “Remediation Operations” or “RemOps,” has begun to grow as organizations look to optimize their communications and workflows for effective risk mitigation. Zafran has a piece on the topic, for those wanting to learn more.
Zafran’s CTEM guide points out that this phase of activity is all about turning insights into action. Cyber may be the ones using AppSec and vulnerability management tools, conducting scans, and more. Still, it is often engineers, developers, and business peers who are responsible for implementing the remediations that lead to the actual risk mitigations.
This means providing the correct information to the right points of contact in a format and delivery mechanism that facilitates action. While not technical, it also means building healthy relationships with our engineering and development peers, who, due to many bad habits on the part of security, often view us as a blocker, the office of now, and an overall pain to deal with.
Despite security anointing ourselves as " business enablers,” how we treat our peers regarding risk management and vulnerabilities has proven anything but enabling.
Building effective communication and workflows as part of CTEM involved key questions, such as who is responsible for addressing vulnerabilities, the organizationally defined SLAs, where and how they are communicated, the organization's risk tolerance, and more.
Zafran recommends a phased maturity approach, moving from reactive, disjointed communications to real SLA-driven coordination. This includes establishing ownership and setting up timely notification channels, automating ticketing, standardizing workflows, and operationalizing end-to-end exposure response processes.
All of these can lead to more productive communications and workflows that truly position those responsible for remediations to take action and drive down organizational risk exposure.
Closing Thoughts
While it is clear that the vulnerability management space is evolving, and the Continuous Threat and Exposure Management (CTEM) category represents the next logical step in this evolution, many organizations are unsure where to begin.
Zafran’s CTEM Guide offers an informative and actionable resource for organizations seeking to elevate their vulnerability management and transition from a reactive to a proactive approach to mitigating organizational risks.