The DBIR is entering its Vulnerability Era
A look at the 2024 Verizon Data Breach Investigations Report (DBIR) and the role of vulnerability exploitation
Welcome to Resilient Cyber!
If you’re interested in FREE content around AppSec, DevSecOps, Software Supply Chain and more, be sure to hit the “Subscribe” button below.
Join 5,000+ other readers ensuring a more secure digital ecosystem.
If you’re interested in Vulnerability Management, you can check out my book “Effective Vulnerability Management: Managing Risk in the Vulnerable Digital Ecosystem” on Amazon. It is focused on infusing efficiency into risk mitigation practices by optimizing resource use with the latest best practices in vulnerability management.
In cybersecurity it can be tough to find quality data around incidents, root causes, and systemic issues plaguing the ecosystem. Among vendor claims, marketing and FUD, there is a lot of noise.
That said, there are some key sources that are longstanding, and both highly trusted and cited. The Verizon Data Breach Investigations Report (DBIR) is high on that list. The report that is published every year looks at incidents, trends and key findings.
The 2024 DBIR was just released and it examined a record 30,458 incidents and 10,626 breaches in its data set, representing a two fold increase over the previous years report.
There’s a lot of excellent insights in the report, ranging from vulnerabilities, phishing, GenAI, the human element and more.
That said, given my focus is often on the software supply chain, application security and vulnerability management, including my latest book “Effective Vulnerability Management”, I will be focusing on some key insights from the DBIR related to vulnerabilities.
Vulnerability Exploitation Seeing Explosive Growth
One thing the report makes abundantly clear is that the number of attacks involving exploitation of vulnerabilities is seeing explosive growth. In fact, it tripled, growing 180% over the previous years report.
While it still ranks below common attack vectors such as phishing and credential compromise, the 180% growth in vulnerability exploitation isn’t something to neglect and it is fair to say we should expect this attack vector to continue to climb.
Verizon even published a 2024 DBIR recap from Chris Novak, their Sr. Director of Cybersecurity Consulting titled “Vulnerability Exploitation Boom Threatens Cybersecurity”, which can be listened to below:
In the video, Chris discusses the rise of exploitation of zero day or newly discovered vulnerabilities, and cyber criminal groups such as ransomware leveraging these vulnerabilities and the fact that they now account for 1/3rd of ALL incidents DBIR sees.
Chris goes on to discuss how the industry should be looking at activities with risk exposure and vulnerability management as ways to beat the odds. Of course these aren’t new, although we do see the rise of categories such as Attack Surface Management (ASM) beginning to grow.
However, Vulnerability Management on the other hand is a practice nearly as old as the field of software and cybersecurity itself. That said, and as I have written about extensively both in articles and in the book “Effective Vulnerability Management”, legacy approaches to vulnerability management simply aren’t sufficient and organizations are drowning in vulnerability backlogs numbering in the hundreds of thousands to millions, with no hope of ever catching up.
Additionally, in security’s hyper focus on “shifting left”, we’ve jammed a bunch of low fidelity noisy scanners and tools into things such as CI/CD pipelines as part of “DevSecOps” which are taxing development teams with dumps of vulnerabilities with little to no context around key criteria such as known exploitation (e.g. CISA Known Exploited Vulnerability Catalogue KEV), exploitation probability (e.g. Exploitation Prediction Scoring System EPSS), or critical information such as business context, asset/data sensitivity and modernized tooling that provides capabilities such as reachability analysis, to show what is actually reachable and poses real risk, to cut through the noise of legacy tools.
The DBIR has a portion of the report that states:
“The DBIR is entering its Vulnerability Era”
They cite that the MOVEit vulnerability alone accounted for 1,567 breaches and cite a metric from CISA showing Cl0p Ransomware was able to compromise more than 8,000 organizations around the globe with a handful of zero-day vulnerabilities.
DBIR does some excellent analysis and highlights some key points:
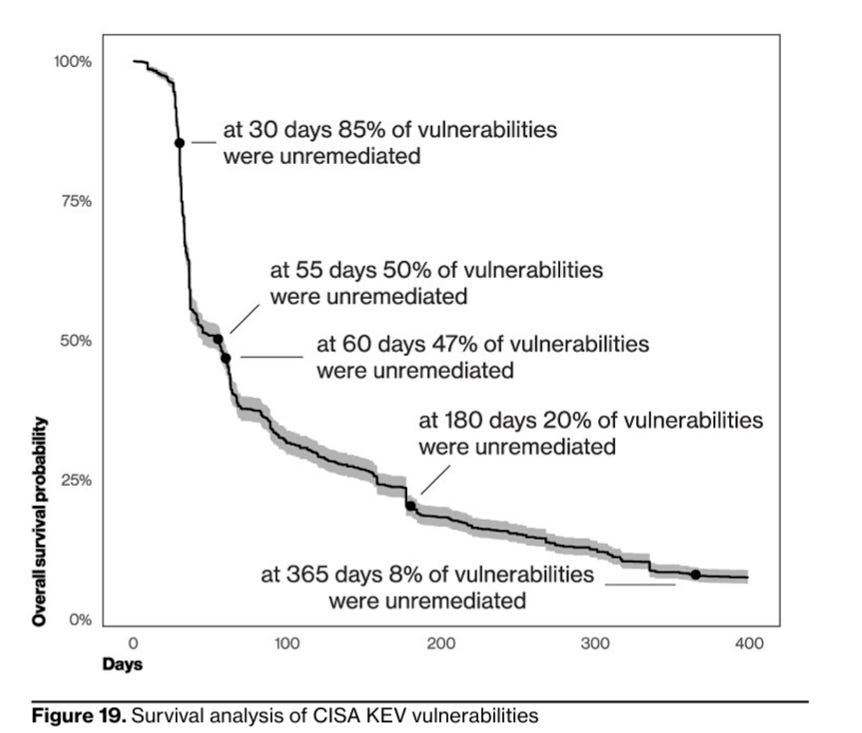
It takes organizations around 55 days to remediate 50% of vulnerabilities in the CISA KEV once a patch is available
Patching doesn’t pick up until the 30-day mark and by the end of the year nearly 10% of them are still open
They point out that longstanding practices such as 15-30-60 day patch cycles simply doesn’t keep up with the pace of threat actors exploitation activities. The DBIR also uses the word “critical” loosely, assuming they are referring to CVSS severity scores, which we know are inherently flawed and don’t represent real risks, given <10% of ALL CVE’s per year are actually ever exploited (hence KEV and EPPS and other vulnerability intelligence gaining traction).
Below is an excellent depiction of their findings around remediation of CISA KEV vulnerabilities:
They point out that while some vulnerabilities had a massively successful response in terms of scanning/identification and remediation (they used Log4j as an example) “we cannot realistically expect an industrywide response of that magnitude for every single vulnerability that comes along, be it a zero-day or not”.
This of course is something I’ve written about extensively, in articles such as:
The overarching theme in all of the articles is simple:
“Organizations are drowning in vulnerabilities and simply telling them “patch faster” won’t help”
This point is backed up explicitly by the DBIR, which states “If we can’t patch the vulnerabilities faster, it seems like the only logical conclusion is to have fewer of them to patch”.
This of course again is pointing to the need for Secure-by-Design software/products and suppliers taking more responsibility rather than externalizing the risk and burden onto consumers and customers.
Secure-by-Design Theme
Another refreshing perspective from both the report and Chris’ commentary was:
“You can’t vulnerability management yourself way out of bad vendor, we need to be looking at the vendor management processes and the testing and vetting that we’re doing there.”
This of course is a nod to the growing trend of calls we’re hearing from CISA and others for “Secure-by-Design/Default” software and products. I’ve covered CISA’s Secure-by-Design initiative extensively in other articles, for those interested. It also of course is a theme emphasized in the latest U.S. National Cybersecurity Strategy, which I covered.
The DBIR report even features CISA’s Director Jen Easterly, pointing out that we continue to fall victim to well-known, researched and reported classes of vulnerabilities being exploited. She discusses trying to encourage software developers to improve the tools, technologies and processes and eliminating systemic software quality issues at their root, and to begin demanding that technology be Secure-by-Design starting today.
For those who have been following CISA’s Secure-by-Design efforts and commentary from Director Jen Easterly, you’ll notice parallels from her commentary here to her remarks in other publications such as Foreign Affairs (Stop Passing the Buck on Cybersecurity) and at Carnegie Mellon (Unsafe at Any CPU Speed: The Designed-in Dangers of Technology and What We Can Do About It).
Within the report, they discuss how vulnerability exploitation is accounted for in their supply chain metric due to the fact that quality control failures by software suppliers disproportionately affect customers.
Sound familiar?
If you’ve read the U.S. National Cybersecurity Strategy (NCS), it should, due to language such as:
“Today, end users bear too great a burden for mitigating cyber risks”
“The most capable and best-positioned actors in cyber space (e.g. Software Suppliers) must be better stewards of the digital ecosystem”
This is language from Pillar Three of the NCS, “Shape Market Forces to Drive Security and Resilience”, which stresses placing responsibility on those within our digital ecosystem that are best positioned to reduce risk (again, software and digital product manufacturers).
It is also the section of the NCS that discusses concepts such as Software Liability and Safe Harbor.
The DBIR recommends readers go check out the latest Secure-by-Design publication from CISA and their partners.
We have one of the most cited and widely read data breach reports in the security industry emphasizing the need for the shift of paradigms to Secure-by-Design, stating: “If there was ever was a clear time to make a statement by prioritizing this elegant solution (Secure-by-Design) to a growing threat (Vulnerability Exploitation), this is it”
For those interested in Secure-by-Design, I cover the publication great depth in this article, and also have an entire chapter of my latest book dedicated to it.
Software Supply Chain Attacks
The DBIR report mentions that it introduced the expanded concept of a breach involving a third party that includes partner infrastructure being affected and direct or indirect software supply chain issues “including when an organization is affected by vulnerability in third-party software”.
The report found that 15% of breaches involve a 3rd party, including software vulnerabilities in third-party software:
That 15% represents a growth from 9% the year prior, again representing a substantial growth of 68% YoY for incidents involving 3rd parties, including their software.
They demonstrate it further, with the image below, showing the growth of the supply chain metric in breaches over the past several years, moving up and to the right:
They emphasize that to mitigate these risks and impacts, organizations to be trying to select vendors with better security track records.
I would take this further and emphasize demanding transparency from vendors, which we’re seeing emerge with efforts such as Software Bill of Materials (SBOM)’s, to see the residual risk of components embedded into products, and also in methods such as in the U.S. Federal sector with CISA’s Secure Software Self-Attestation Form, which is soon going to be required of ALL software vendors selling to the Federal government, demonstrating they are following methods such as NIST’s Secure Software Development Framework (SSDF).
In the report, they discuss not only incidents where data was compromised in a third-party data processor or custodians site (e.g. MOVEit) but also cases where the software development process itself was hijacked and malicious software updates were distributed (e.g. SolarWinds and 3CX). This ties back to my previous point about focusing on not just the software artifacts but the overall security of the development process, including its underlying infrastructure, hosting environment, methodologies and more.
The DBIR places the fault for this right at the feet of the software vendor community (and us, as consumers who choose them) too, by stating “this metric ultimately represents a failure of community resilience and recognition of how organizations depend on each other. Every time a choice is made on a partner (or software provider) by your organization, and it fails you, this metric goes up.”
This of course is inferring as customers, and as an industry, we need to bolster our due diligence around selecting the software products we consume and vendors we work with. There are longstanding practices such as security questionnaires, which are both ineffective and intolerable for both the suppliers and consumers.
Modernized effective due diligence requires increased transparency from the supplier (e.g. SBOM’s, visibility into the residual vulnerabilities of products/components, assurances around the governance and security of the software development process and more).
It also requires customers voting with their wallets and making risk-informed decisions either from insights directly from transparency of a vendor, as well as word of mouth among the community and information from a vendors security track record as well as evolving efforts such as cybersecurity incident disclosures being driven by organizations such as the SEC for publicly traded companies, which can help.
Conclusion
The Verizon DBIR is a literal trove of useful and insightful information for the security industry, bringing long awaited updated every year that practitioners, investors, analysts and more seek out.
While I only touched on a subset of the coverage this year, I strongly recommend going to give it a full read, to get the wealth of information in all the areas I didn’t directly discuss.
If there was a theme though, and it was even emphasized by the DBIR itself and their team, it’s that vulnerability exploitation is a key attack vector seeing exponential growth, coupled with software supply chain attacks and a broader systemic push for Secure-by-Design software/systems, being championed not only by government agencies such as CISA but also now by one of the most respected and read pieces of research in the entire cybersecurity industry.
We are indeed, as they say, in the Vulnerability Era.










Chris, I wasn't aware of the DBIR report. Thanks for unpacking it.
In my opinion, software supply chain attacks are probably way higher as they are harder to measure.
Thoughts?