Resilient Cyber Newsletter #39
Google & Wiz Join Forces, Collection of AI Security Resources, Autonomous SOC Framework, Agentic Radar, GitHub Supply Chain Attack & EPSS v4 Goes Live!
Welcome
Welcome to another issue of the Resilient Cyber Newsletter. This week, we have some big news on various fronts to cover.
From Google’s $32 billion acquisition of cloud security leader Wiz, my collection of AI security resources, chats with industry leaders, supply chain security attacks (and reports), and the Exploit Prediction Scoring System (EPSS) v4 going live!
Beyond Visibility: Cloud Runtime Security without Tradeoffs
Cloud security has traditionally pushed organizations into a difficult choice: deploy an agent for deep, real-time protection or rely on agentless visibility for broad coverage. Each approach has benefits, but neither alone is enough to stop modern attacks.
What if I told you that you could have both?
Cortex® Cloud eliminates tradeoffs, giving you the best of both worlds in best-in-class protection with an XDR agent and broad visibility with agentless scanning for complete cloud runtime security.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 45,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cyber Leadership & Market Dynamics
Google Seals Record-Breaking $32 billion Wiz Acquisition
In what marks tech giant Google's largest-ever acquisition, it is announced that they will acquire cloud security startup leader Wiz for a massive $32 Billion, with a B.
This deal emphasizes Google’s plans to be a cloud security leader and compete more broadly with peers such as Microsoft and Amazon in the enterprise cloud. It will also nicely complement prior acquisitions such as Mandiant and native offerings like Google’s Thread Intelligence.
This is also a huge milestone for the startup community, cloud security, and the Wiz founders, who previously rejected a Google offer worth over $20 billion in 2024 and now received the subsequent larger offer.
As noted in the above article, this does represent a shift from Wiz’s prior comments about IPO ambitions, but given the market uncertainty, an acquisition likely made more sense. Wiz recently raised $1 billion at a $12 billion valuation.
In an insane state, it is also reported that Google will offer retention bonuses worth up to $1 billion to Wiz employees, particularly to ensure continuity in leadership and talent retention.
Not all cuts are equal: Security budget choices disproportionately impact risk
Budget cuts that impact security can present unique challenges to organizations, specifically regarding potentially introducing organizational risk. One challenge for security leaders is often proving a negative or that nothing bad happened explicitly because of spending and investments in security, which is hard to do.
A recent survey of 600 CISOs in the EU, US and others showed a priority gap between boards ands security leaders, with CISO’s facing pressures to rein in spending and outsource functions and also show the business value of security initiatives.
While it is speculative and questionable how Splunk tied these survey results together, there nonetheless interesting:
The above article discusses each category and how they can create organizational risks and lead to security incidents.
White House Instructs agencies to avoid firing cybersecurity staff, email says
Amidst widespread changes to the Federal and Defense workforce in the U.S., the White House sent an email instructing agencies to avoid firing cybersecurity staff.
Greg Barbaccia, the U.S. Federal CIO sent an email including the following:
Many have speculated that widespread RIFs and workforce reshaping may have cybersecurity implications, from systems and data being accessed to the workforce itself and a loss of technical security talent.
The ramifications of much of the actions being taken still remain to be seen from the security perspective.
Cyber Industry Leaders Continue to Grow
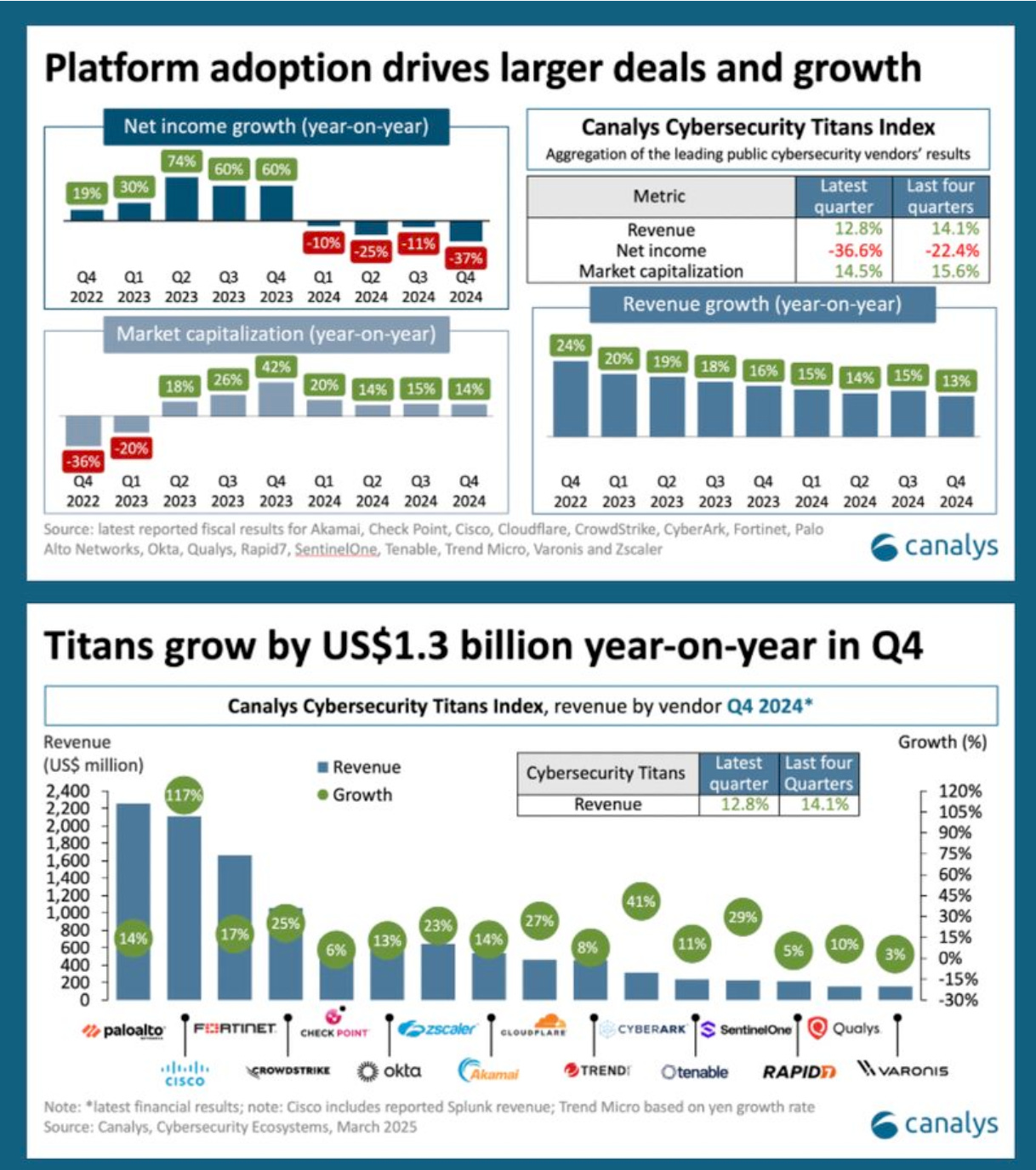
An analysis from Jay McBain, Chief Analyst of Canalys, demonstrated that the “Cybersecurity Titans Index” (a group of industry security leading vendors) grew 12.8% in Q4 2024, with a combined revenue reaching $11.9Bn.
For the full year of 2024, those same companies grew 14.1%, with a combined revenue of $43.9Bn, although in 2023, they saw 18.3% growth.
Jay speculated that platform adoption, as shown by rising ARR, high module attachment rates, and larger deals, remained a focus for this group of vendors and likely contributed to their growth in 2024.
This is amidst ongoing debates about Platform vs. Best of Breed, discussing budgetary consolidation in cyber, and the need to show ROI.
AI
Resilient Cyber’s Collection of AI Security Resources
If you're like me, you're probably spending a fair amount of time up-skilling in GenAI, LLMs, and AI Security more broadly. I've intentionally been consuming any publications, research, frameworks, and more over the last 18-24~ months around AI and AI Security
Additionally, I've intentionally sought out industry leaders who approach the topic from various perspectives. This includes Investors, Advisors, Founders, Security Leaders and more.
I've also been reading extensively about AI security in publications from organizations such as the National Institute of Standards and Technology (NIST), MITRE, OWASP® Foundation, and others.
I've consolidated that analysis and the interviews in this article here. I hope you find these resources helpful and the conversations as insightful as I did with this group of amazing folks.
I also look forward to learning and evolving in this age of AI as it redefines the future of Cybersecurity and our society more broadly.
Resilient Cyber w/ Chenxi Wang - The Intersection of AI & Cybersecurity
In this episode, we sit down with Investor, Advisor, Board Member, and Cybersecurity Leader Chenxi Wang to discuss the interaction of AI and Cybersecurity, what Agentic AI means for Services-as-a-Software, as well as security in the boardroom.
Chenxi and I covered a lot of ground, including:
When we discuss AI for Cybersecurity, it is usually divided into two categories: AI for Cybersecurity and Securing AI. Chenxi and I walk through the potential for each and which one she finds more interesting at the moment.
Chenxi believes LLMs are fundamentally changing the nature of software development, and the industry's current state seems to support that. We discussed what this means for Developers and the cybersecurity implications when LLMs and Copilots create the majority of code and applications.
LLMs and GenAI are currently being applied to various cybersecurity areas, such as SecOps, GRC, and AppSec. Chenxi and I unpack which areas AI may have the greatest impact on and the areas we see the most investment and innovation in currently.
As mentioned above, there is also the need to secure AI itself, which introduces new attack vectors, such as supply chain attacks, model poisoning, prompt injection, and more. We cover how organizations are currently dealing with these new attack vectors and the potential risks.
The biggest buzz of 2025 (and beyond) is Agentic AI or AI Agents, and their potential to disrupt traditional services work represents an outsized portion of cybersecurity spending and revenue. Chenxi envisions a future where Agentic AI and Services-as-a-Software may change what cyber services look like and how cyber activities are conducted within an organization.
If you aren’t already following Chenxi Wang on LinkedIn, I strongly recommend you do. I have a lot of connections, but she is someone when I see a post, I am sure to stop and read because she shares a TON of great insights from the boardroom, investment, cyber, startups, AI, and more.
I’m thankful to have her on the show to come chat!
Global AI Agents Market Set for Takeoff
With Agentic AI getting a TON of focus,0 it is estimated by market.us that the market will see a CAGR of 43.8% and a market size by 2033 of $139.12B. This is due to the fact that Agentic AI has the potential to be applied to many industry verticals from Healthcare, Marketing, Gaming, Software, Business and more.
Autonomous SOC Framework
SecOps and the SOC continue to be among the most targeted areas for AI use cases. This is due to various factors, such as workforce challenges, organizations trying to drive down metrics such as MTTD/MTTR, cognitive overload as organizations drown in logs and alerts, and more.
Elad Erez put together an excellent blog discussing an autonomous SOC framework and compared it to autonomous cars, as seen below:
He walks through the various levels of the proposed autonomous SOC framework, showing how we can move from partial to fully autonomous, as well as the reality check that we will likely see fully autonomous cars before we get fully autonomous SOCs.
Agentic Radar
As agents and agentic workflows get embedded into enterprises, visibility and security considerations will be crucial. This is an awesome open source tool that helps with just that.
It provides:
Workflow visualization - a graph of the agentic system’s workflow
Tool Identification - a list of all external and custom tools utilized by the system
Vulnerability Mapping - A table connecting identified tools to known vulnerabilities, providing a security overview
Even cooler, Agentic Radar maps the detected vulnerabilities to frameworks such as OWASP’s Top 10 LLM Risks and OWASP’s Agentic AI Threats and Mitigations guidance.
I suspect this will be more and more of a critical need to fully grasp the operational and security implications of agentic AI in enterprise environments and to avoid “shadow” agents, as organizations rush head first into deploying these technologies without necessarily engaging security teams early on.
AppSec, Vulnerability Management & Supply Chain Security (SSCS)
2025 Software Supply Chain Report ⛓️💥
The software supply chain landscape continues to be as porous and problematic as ever. In my latest article for Resilient Cyber, I explored ReversingLabs' 2025 "Software Supply Chain Security Report."
It covers:
📈 The current software supply chain security landscape across open source, commercial software, and attack trends
💻 The pervasive and porous nature of open source continues to be both ungoverned and overlooked by enterprise consumers while being heavily targeted by attackers 🎯
🤕 The overlooked risks associated with commercial software suppliers and the role of binary analysis.
As Saša Zdjelar says, the world may run on open source, but your business runs on commercial software.
💵 The price customers and consumers pay as organizations still prioritize speed to market and revenue over security
🚧 The continual and increasing challenges of the vulnerability ecosystem, from NIST NVD's near collapse, disparate vulnerability databases, problems with CVE data quality, and noise.
The RL team's excellent report on the software supply chain is here, and I hope you enjoy my analysis and thoughts!
GitHub Action tj-actions Attack
Software supply chain attacks continue to evolve and expand. The latest example is a malicious commit discovered in the popular tj-actions/changed-files GitHub action, which is used in over 23,000 repositories.
This is a great article from Endor Labs that breaks down what happened, what versions are impacted, the impact on GitHub repos and OSS projects, and recommended guidance for organizations to follow.
Key recommended actions include:
Searching your dependencies for impacted versions
Configuring CI scanning
Auditing GitHub logs for suspicious IP addresses
Rotating any active secrets in impacted repos
Supply Chain Security is FUBAR - A Proposal for GitHub
Following up the article from Endor Labs, James Berthoty published a really awesome article looking at not just this incident but broader systemic challenges around supply chain security (SSCS), including some gaps in the GitHub platform itself.
James specifically lays out some key things GitHub themselves could do to bolster the entire supply chain, given their outsized role as a leading Developer platform:
When a repo hits a “verified stars” or other popularity threshold, require: Signed commits, Changes must happen via pull request, no bypassing for force pushes and 2FA for all admin credentials are among key recommendations.
Create an opt-in standard for open source maintainer identity verification with: voluntary verified maintainer program, and maintainer roster change alerts
Allow maintainers to share their repo’s audit logs and security settings publicly, which includes configurable public audit logs, and public security settings overview.
Introducing EPSS Version 4
If you have followed me for any time, you know I’m a big proponent of effective vulnerability management, and have written a book on the topic with the same name. This includes factoring in metrics like known exploitation and exploitation probability into vulnerability prioritization.
The Exploit Prediction Scoring System (EPSS) does just that, providing a probability score that a vulnerability will be exploited in the next 30 days. This week we saw v4 of EPSS go live. This is an excellent post from a recent security startup, and key leaders of EPSS, discussing EPSS v4 “Introducing EPSS Version 4”.
Below, you can see how EPSS v4 performs compared to traditional methods such as Common Vulnerability Scoring System (CVSS) prioritization, such as High’s and Critical findings. To put it shortly, if you’re prioritizing vulnerabilities based on CVSS you are wasting a TON of time, given < 5% of CVE’s are exploited in a given year.
I recommend reading the blog to learn more about EPSS v4.
If you want a deeper dive on EPSS, you can read previous articles I’ve written, such as:
Weekly VulnCheck KEV
As organizations continue to optimize their vulnerability remediation and prioritization efforts, known exploited vulnerabilities (KEVs) have become a core part of prioritization. While CISA’s KEV is the most widely known and discussed, it also has some gaps, and some vendors, such as VulnCheck, provide free comparable resources for the community.
This includes their VulnCheck KEV, and this past week, Vulnerability Researcher Patrick Garrity shared a weekly VulnCheck KEV report, which may be useful for organizations looking each week to see what vulnerabilities are now being tracked as known to be exploited.