A look at the Exploit Prediction Scoring System (EPSS) 3.0
The third iteration of the Exploit Prediction Scoring System helps security teams prioritize vulnerabilities through prediction.
(This article is one I originally published in CSO Online, and I am now re-publishing on the Resilient Cyber Substack)
In late 2022, we compared the Exploit Prediction Scoring System (EPSS) and the widely used Common Vulnerability Scoring System (CVSS). Now EPSS 3.0 brings a more comprehensive, efficient, and effective model to the industry looking to prioritize vulnerabilities that pose the greatest threat and offers a robust API and resource open for anyone to access and consume as part of their vulnerability management program.
While CVSS is the most widely used to assess the severity of vulnerabilities, it is inappropriately used in isolation to prioritize risk from the vulnerabilities. Many organizations, including the US Federal Government and the Department of Defense (DoD), utilize CVSS severity scores to help drive their vulnerability remediation timeline requirements.
The introduction of the EPSS, which attempts to aid vulnerability prioritization efforts by providing a numerical score of how likely a vulnerability is to be exploited over the next 30-day window, has been a boon to security practitioners and organizations looking to improve their vulnerability management activities.
Organizations are falling behind in vulnerability management
Studies have shown that organizations can only remediate between 5% and 20% of their vulnerabilities each month, leaving them in a situation where they are perpetually falling behind the number of published and emerging vulnerabilities due to their inability to remediate them all.
Organizations ultimately aim to take approaches to prioritize vulnerabilities for remediation, but they have historically been very inefficient and ineffective, all at a time when we constantly hear about the shortfall of cybersecurity talent and organizations struggling to attract and retain it. It has been found that using only a CVSS severity score to measure the risk of an individual vulnerability is equivalent to picking random vulnerabilities to fix, whereas focusing on vulnerabilities with actual exploitation proof or probability is far more effective at mitigating organizational risks.
A common vulnerability prioritization strategy called for in sources such as PCI and Federal vulnerability management guidance is to remediate vulnerabilities within a predefined set of calendar days after initial detection, based on CVSS severity scores. This often manifests in having critical and high vulnerabilities (as categorized by CVSS) prioritized for remediation within seven to 30 days of initial detection. On the surface, this seems intuitive, except for the issue that fewer than 10% of known vulnerabilities are actually ever exploited in the wild.
For example, security vendor Qualys found in their 2023 TRURISK Threat Report that despite there being 25,000 known vulnerabilities published to the NIST National Vulnerability Database (NVD) in 2022, fewer than 5% of those were ever actually known to be exploited in the wild.
Precious time wasted on vulnerabilities that pose no risk
While organizations may prioritize vulnerabilities based on CVSS severity scores, those vulnerabilities may not be known to be exploited through sources such as CISA's Known Exploited Vulnerability (KEV) list, and they may never be known to be exploited. Organizations are essentially spending precious time and resources remediating vulnerabilities that pose little to no risk while ignoring those that potentially do.
As an industry, we desperately need to focus on vulnerabilities that pose the most risk and those that are the most likely to be exploited are great places to start. That's where EPSS comes in, and the EPSS 3.0 model provides a number of improvements over previous versions.
The best way to really dig into EPSS 3.0 and the evolution of EPSS overall is with the latest whitepaper produced by the EPSS special interest group members from organizations such as Cyentia and RAND.
EPSS shows an 82% improvement over previous versions
The EPSS team claims an 82% performance improvement in EPSS 3.0 over previous versions along with covering the evolving vulnerability landscape. The NIST National Vulnerability Database (NVD) has continued to see exponential growth with a 24.3% increase in vulnerabilities in 2022 over 2021, totaling more than 25,000 vulnerabilities in a single year.
Despite the tremendous growth of vulnerabilities, organizations only have a median remediation rate of 15.5% with one-quarter of organizations remediating fewer than 7% of their open vulnerabilities per month. This creates a scenario in which organizations are perpetually drowning in increasing vulnerability backlogs, with some studies finding the average organization has a backlog of more than 100,000 vulnerabilities and climbing.
EPSS strives to help organizations prioritize vulnerabilities quickly by focusing on those with the highest probability of being exploited over the next 30 days. EPSS boasts the ability to help organizations minimize the burden of patching critical vulnerabilities with one-eighth of the effort of typical strategies using CVSS.
EPSS utilizes a variety of sources when it comes to exploits, such as Fortiguard, Alienvault OTX, the Shadow Server Foundation, and GreyNoise, all of which utilize various techniques to identify exploitation attempts in digital environments around the globe. In addition to these sources, EPSS utilizes over 1,400 features for predicting exploitation activity. These include sources such as published exploit code, public vulnerability lists, offensive security tools, and the age of the vulnerability among others.
Tests show the effectiveness of EPSS 3.0
To prove their performance improvements with EPSS 3.0, the EPSS special interest group performed testing to explore the increased effectiveness of the 3.0 model. They measured its performance improvement in predicting vulnerability exploitation over 30 days using the features discussed above and they compared performance results and metrics against previous EPSS versions such as 1 and 2, as well as CVSS v3 base scores.
One diagram that demonstrates the significant improvement is found below, which shows all CVEs, CVEs above a threshold, and those that are actually exploited. As you can see, when contrasting CVSS v3.x along with EPSS v1 and v2, EPSS 3.0 shows a significant improvement in terms of prioritizing the largest portion of exploited vulnerabilities. The blue circles represent the number of vulnerabilities needing to be remediated under the given methodology and the red circle represents actual exploitation activity. As you can see, EPSS significantly outperformed the other models by helping users remediate the largest portion of exploited vulnerabilities and minimizing wasted resources and effort on non-exploited vulnerabilities.
A strong data-driven approach to evaluating threats
While the EPSS model isn't perfect, it does present a strong data-driven approach to help organizations focus on vulnerabilities that pose the greatest threat based on probable exploitation activity. We're also seeing an evolution of other industry resources such as the longstanding Common Vulnerability Scoring System (CVSS).
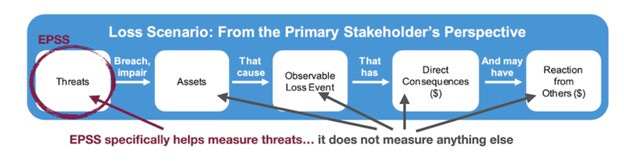
It's worth emphasizing that EPSS measures the threat associated with a published CVE, based on the probability that the CVE will actually be exploited in the wild in the next 30 days. It doesn't account for organization-specific context such as that related to assets or the business.
That said, when organizations are drowning in a backlog of hundreds of thousands of open vulnerabilities with the rate of discovered and published vulnerabilities only accelerating, starting with vulnerabilities most likely to be exploited is a great foundation. For those looking to learn more, you can dig into the EPSS FAQ page.




Great write up as usual, Chris!