Resilient Cyber Newsletter #33
DeepSeek Disruption, (De)Regulation Drivers, CISO Spending Patterns, CVSS is Dead (to some), and Cloud Risk Exposure Impact Report
Welcome!
Welcome to another issue of the Resilient Cyber Newsletter.
We’ve got quite the roller coaster of a week underway, from China’s AI Model DeepSeek’s disruption, the new presidential administration making major policy and organizational changes, and deep dives into 2024 market analysis to reflect on and see what may lie ahead for 2025.
So, let’s get to it!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 16,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Reduce Your Phishing Triage Time by 95% with Material Security
Security teams need to balance the critical risk of modern phishing attacks against the simple fact that there are only so many hours in a day. Far too much time is wasted on manually triaging, investigating, and remediating: every minute spent chasing false positives is a minute not spent on mission-critical tasks. Trusted by companies like Lyft, Databricks, and Carta, Material Security helps strike the right balance with AI-powered detections and truly automated remediations across your productivity suite, along with flexible controls and granular settings that match your needs.
Cyber Leadership & Market Dynamics
Trump’s Commerce Pick Backs Light-Touch Regulation in Emerging Tech Policy
I recently shared how the Trump administration revoked several Biden administration Executive Orders (EO), including the AI EO, and released their own AI EO, emphasizing U.S. competitiveness and removing barriers to innovation.
This likely will be an overall theme for the next several years. Trump’s nominee to lead the Department of Commerce recently advocated for a light-touch approach to regulating emerging tech and U.S. tech policy.
Below is a quote from Lutnick at a recent confirmation hearing:
“Let's just unleash America for the benefit of America,” Lutnick said. “I think we've been too constrained for too long. That's over. It needs to be all about American ingenuity. And I think if you unleash American ingenuity, the scale by which we will outrun, outpace, outperform the rest of the world will be incredible.”
Lutnick even responded to a question about avoiding following in the EU’s tech policy footsteps (e.g., rigorous compliance-driven policy), and he confirmed he would indeed look to take a different route for the U.S.
Coincidentally, Lutnick was asked about China’s DeepSeek in the same testimony. He commented about China and IP theft from the U.S. and how it needs to be stopped, which many would then subsequently point to efforts like NIST 800-171 and CMMC for the Defense Industrial Base (DIB), which looks to ensure the DIB has security controls and measures in place to prevent the compromise of data such as IP.
Ironically, security and compliance can impede and prevent innovation and competitiveness and protect it in some scenarios.
Altitude Cyber - 2024 Cybersecurity Year in Review
Altitude Cyber recently released its 2024 Cybersecurity Year in Review, which provides some great insights into the cybersecurity space in 2024 regarding investments, ventures, M&A, and more.
The image above shows some key insights, such as YTD financing, deal counts, volume, and the top public performers in cyber for the year. I made a post pointing out that once again, we see markets DGAF when it comes to Cyber, notably due to the top performer, Fortinet, seeing several highly visible security incidents and exploited zero days in 2024, and despite that, still performing incredibly and above their peers.
Until cyber consumers' purchasing patterns change, the market will continue to behave the way it does. Security leaders would be well reminded to acknowledge that their security tools are part of their attack surface.
The report goes on to provide many great insights, such as M&A activity and financing. The year saw 280 total M&A transactions, for a total deal volume of $53.3B, and 892 total financing transactions, for a total deal volume of $13.2B.
As can be seen below, Security Consulting saw the most M&A activity by far, 2x as much as its next peer in Risk & Compliance.
Altitude also provides a great snapshot of 2024 Market Themes & Commentary
The report also covers a detailed collection of some of the top reports, articles, podcasts, and more from 2024, which are worth checking out if you haven’t already. Overall, this is an excellent resource from Altitude Cyber, and I look forward to seeing it each year.
Tenable Acquiring Vulcan Cyber
Industry vulnerability management leader Tenable announced they were acquiring Vulcan Cyber and integrating it into their platform. The deal is estimated to be approximately $150M and shows further consolidation in the vulnerability management space. It is also another nod to “platformization” as Tenable, which already boasts a broad set of capabilities, looks to expand.
CISOs Are Gaining C-Suite Swagger, but Has It Come With a Cost?
A recent survey by Splunk showed that the number of CISOs reporting to the CEO is up to 82%, compared to 47% as recently as 2023. 83% also said they regularly participate in board meetings.
Many would view that as a good thing, as CISOs have long bemoaned reporting relationships and a lack of reporting to the CEO (often to the CTO, where some say there is a conflict of interest), but 53% of those surveyed said that it has become more difficult since they took the job of CISO. Many cite challenges such as a lack of board buy-in, and the survey discusses that potentially being tied to the fact that a mere 29% of CISOs have a board with even one cyber expert. This often likely makes cyber and associated concerns a foreign concept or difficult to grasp on a board that isn’t cyber-savvy.
Budgets were cited as a challenge, too, with only 29% of CISOs surveyed saying they have the necessary budget to keep up with the threat environment. Non-CISO board members have a different experience, with 41% saying they are satisfied with cyber investment levels.
Anecdotally, Jen Easterly took to LinkedIn to tout the drastic change in CISOs reporting to the CEO, and the comments were rich, with many experienced and well-connected practitioners calling the metric into question. Many suspect the actual metric across a broader population than the survey did (600 CISOs) would likely show a much lower % of CISOs reporting to the CEO.
That said, we would need real data to substantiate that. I bring up Jen’s post, though, because she made a critical point that I agree with and have been trying to explain to many: CISOs often “manage” risk, as delegated to them by the CEO/Board, etc., but they do not “own” risk, a key distinction.
The business owns the risk. The CISO is there to empower the business to make risk-informed decisions.
How CISOs are Spending Their New Budgets
CISO spending patterns continue to be a key topic, whether peer security leaders are looking to see how their network is spending or security vendors are looking for insights on security spending and how they can align accordingly. This piece on Crunchbase provides some interesting perspectives from longtime security leader turned VC Andy Ellis.
Andy discusses how spending slowed down, stopped, or even reversed for many CISOs in 2023, but the trend started to reverse in 2024.
Pointing to another resource from YL Ventures, Andy shows what 218 CISOs said they were planning in terms of projects and investments:
It shouldn’t be surprising to see some of the items on the top of the list such as Identity, including NHIs, as well as GenAI Security. For those looking to learn more about NHIs you can find several of my recent articles below:
GenAI Security is another notable area as security leaders race to keep up with the business’s rapid adoption of AI, whether it is self-hosting models, using products with embedded AI capabilities, or using external providers offering capabilities such as GenAI and LLM’s.
Board Firings, Loyalty Tests Thin Out U.S. Government’s Cyber Bench
Axios recently ran a story highlighting some of the firings and removals of the U.S. government’s cybersecurity expertise, particularly on the Cyber Safety Review Board (CSRB) and AI Safety and Security Board.
The story touches on the fact that the CSRB was actively investigating Salt Typhoon, the largest hack the U.S. telecom sector has ever seen, and that new members of the CSRB, when they are nominated/selected, will likely need to start over or, at a minimum, take quite a bit of time to ramp up.
While cyber is typically a largely bipartisan issue, entities such as the CSRB have been unfortunately swept up in politics involving agencies such as CISA.
Sen. Wyden Raises Concerns Around Elon Musk/DOGE Access to U.S. Treasury Payment Systems
In the ongoing shakeup of the U.S. Government, including DOGE and Elon Musk, some, such as Sen. Wyden, have raised concerns that Musk personnel are getting access to highly sensitive U.S. Treasury payment systems. Sen. Wyden raised concerns about potential dangerous conflicts of interest, such as Musk’s business ties to China.
Politics aside, Sen. Wyden has been a strong advocate for cybersecurity, such as calling out MSFT's behavior and incidents that impacted U.S. agencies and national security in 2023-2024. I often find his perspective on cybersecurity to be strong, especially for Congress, which is often not cyber-savvy.
Text from Wyden’s letter is below:
While many on both sides of the political aisle agree that the Government is ripe for modernization and overhaul and has deep systemic issues, I think many would also agree that there needs to be some level of oversight of who is accessing what and why, as well as potential COI’s or national security considerations.
We will see what, if anything, comes from the concerns being raised.
The systems involved process payments for Social Security, Medicare, Tax Refunds, Payments to Federal Contractors (some in media have pointed out that the companies may compete with Musk owned or affiliated companies), and others.
AI
The Intersection of AI and Need-to-Know
I recently spoke with Sounil Yu, Co-Founder and CTO at Knostic, a security company focused on need-to-know-based access controls for LLM-based Enterprise AI.
Sounil is a recognized industry security leader and the author of the widely popular Cyber Defense Matrix. For those unfamiliar with the Cyber Defense Matrix, I did a deep dive article on it titled: “Enter the Matrix: A look at the Cyber Defense Matrix by Sounil Yu”.
Sounil and I dug into a lot of interesting topics, such as:
The latest news with DeepSeek and some of its implications regarding broader AI, cybersecurity, and the AI arms race, most notably between China and the U.S.
The different approaches to AI security and safety we’re seeing unfold between the U.S. and EU, with the former being more best-practice and guidance-driven and the latter being more rigorous and including hard requirements.
The age-old concept of need-to-know access control, the role it plays, and potentially new challenges implementing it when it comes to LLM’s
Organizations rolling out and adopting LLMs and how they can go about implementing least-permissive access control and need-to-know
Some of the different security considerations between
Some of the work Knostic is doing around LLM enterprise readiness assessments, focusing on visibility, policy enforcement, and remediation of data exposure risks
On DeepSeek and Export Controls
Anthropic’s CEO took to the web, publishing a piece discussing the importance of export controls in ensuring democratic nations such as the U.S. stay in the lead and in a dominant position when it comes to AI.
This followed the buzz around China’s DeepSeek and claims that it produced the model for a fraction of the cost of leading U.S. AI models. While those claims have come under great scrutiny, one saying stands the test of time: constraints drive ingenuity. I suspect that, to some extent, what we are watching is the power of ingenuity when constrained, in this case, by export controls on chips against China.
In the piece, Dario discusses the three dynamics of AI development, which he cites as:
Scaling Laws—State that, all things equal, scaling up the training of AI systems leads to smoother, better results on a range of cognitive tasks across the board. This is why we have seen so much investment of capital in scaling models.
Shifting the Curve—In this dynamic, Dario discusses how organizations constantly seek gains in the efficiency and effectiveness of models and their capabilities, but those cost savings are ultimately funneled back into producing smarter models. We keep pushing and pushing in pursuit of bigger and better, demonstrating an insatiable thirst for pushing the boundaries of what is possible. Previous gains and optimizations are built on by subsequent activities, and the time to surpass previous achievements continues to shrink.
Shifting the Paradigm—In this dynamic, Dario discusses major paradigm shifts, such as the pre-training focus in 2020-2023 or the more recent shift, such as the focus on reinforcement learning (RL) or chain-of-thought reasoning.
Dario goes on to suggest that DeepSeek's claims of doing what it has for $6M are inaccurate and likely false, but he does admit that due to innovations among the DeepSeek team, they produced a model with similar capabilities to its U.S. peers at a reduced cost. That said, he does speak about DeepSeek’s alleged access to potentially 50,000 Hopper Chips, which is far more compute than originally speculated and not orders of magnitude less than some of the US AI labs.
All of the discussion above led up to Dario’s primary point, which is the need to implement and enforce further export controls on chips to China to sustain the US’s advantage as an AI leader.
Dario makes the case that to achieve AGI and AI dominance, we will need millions of chips that collectively cost tens of billions of dollars and will occur in 2026-2027 and said multiple U.S. companies will have that chip capacity, and the wild card is, will China too?
Whether they do or not will determine whether we live in a unipolar or bipolar world, where both the U.S. and China are on par with AI and all the economic and national security implications that come along with that. This is why he states we need well-enforced export controls to prevent China from getting the chips to ensure we have a bipolar world where they are on par with the U.S.
I will say from my perspective, it is fascinating to watch the continued convergence of technology and national security as AI and software increasingly drive both modern nations and militaries alike.
Exposed DeepSeek Database Leaking Sensitive Data
While much has been written in the past couple of weeks about Chinese AI company DeepSeek, including their potentially massively disrupting the AI ecosystem with their incredibly cost-efficient model, questions on what data they used to train the model, impacts to the stock market and NVIDIA share price, and much more, I wanted to share a resource that is more security-focused.
This past week, cloud security leader Wiz reported that they identified a publicly accessible ClickHouse database that belonged to DeepSeek and allowed full control over database operations, including access to internal data such as chat history and secret keys.
Wiz published a blog breaking down their finding and how they were able to access the system.
Adversarial Misuse of AI
Like any other technology, we already know malicious actors will utilize AI to facilitate their goals. That said, we are still getting insight into the what and how’s in terms of details. This paper from Google Cloud provided some of that insight.
They looked at government-backed threat actor usage of Gemini to see how threat actors use AI in their operations. Some of the key findings are:
They didn’t observe any original or persistent attempts by threat actors to use prompt attacks or ML-focused threats (it’s coming)
Threat actors are experimenting with Geimini to enable their operations to boost producivity gains but haven’t developed novel capabilities yet
Gemini is being used to support several phases of the attack lifecycle
Malicious actors are using Gemini for research, content generation, translation and messaging
Gemini’s security and safety measures impede the malicious actors’ planned usage in some cases
This shouldn’t come as a surprise, as attackers always look to exploit new and novel technologies, either directly or as part of their attack campaigns.
Defenders should equally be building proficiency with AI in areas such as GRC, SecOps, AppSec and others and throughout the defensive lifecycle to be more effective and ultimately mitigate organizational risks.
The nation-state APTs widely using Gemini included usual suspects such as Iran, China, North Korea, and Russia. The google blog goes into much more detail about the types of activities, attacks, and more and is worth a read.
A Realistic Take on AI Agents in Security
We’ve seen a TON of hype around Agentic AI and the implications of AI agents, including in security. However, I found this piece from Harry Wetherald to be a good one, with a pragmatic take on AI agents.
Harry discusses how most security tools struggle with the same problem, too much noise, not enough signal and how AI has the potential to try and mitigate this systemic challenge.
Copilots vs. Autonomous Investigations
When it comes to AI and areas of excitement in security, none have perhaps seem more excitement than SecOps. This piece from Filip Stojkovski and Srinivas Mantripragada does a good job discusses potential AI Sidekicks including copilots and autonomous investigations.
The diagram below is quickly informative:
The article goes on to discuss some of the activities each model can help with, such as in Copilots case, helping with alert investigation, enrichment, blast radius insights and alert summaries. It’s easy to see how this model would be helpful but it does require you knowing what questions to ask and creating quality prompts.
On the flip side, the automated/autonomous approach doesn’t require prompt and can pre-populate insights based on autonomous activities that didn’t require human involvement. However, it also requires vendor or organizationally-defined playbooks and can even hallucinate or product incomplete results.
Both models are looking to address systemic challenges in SecOps such as alert fatigue, resource constraints, speed of investigation and the ever-present workforce challenges.
We may even see some organizations using a combination of the two, depending on the use case, scenario and maturity of the SecOps team and broader organization. It will be interesting to watch this space mature with continued investment and innovation.
AppSec, Vulnerability Management, and Software Supply Chain Security
The Evolving GRC Landscape
If you're like me, you've lived and breathed the pain of GRC and compliance frameworks throughout your career. That said, the GRC space continues to evolve and, in many ways, make progress over traditional pain points and challenges.
That's why I was excited to dig into Hyperproof's 2025 IT Risk and Compliance Benchmark Report. In my latest article on Resilient Cyber I break down some of the key findings, such as:
👩🏫 The continued push to centralize GRC teams to manage the changing regulatory landscape, requirements, and controls
✅ Organizations leaning into common control frameworks (CCF) to address the compliance framework sprawl and cross-walk controls among frameworks, alleviating toil and manual re-work
💵 Budgetary projections in the next 12 to 24 months, as organizations allocate resources to ensure they meet their compliance requirements
🤝 Roles and responsibilities: who is overseeing organizational compliance, what is or isn't being outsourced, and how organizations that have mature, repeatable programs perform better
🛠️ Use of modernized GRC tooling that is API-centric to facilitate automation, take advantage of cloud platforms, and get out of legacy, snapshot-in-time assessments and paper-based activities
A lot of great insights here, so I hope folks enjoy!
2025 Cloud Risk Exposure Impact Report
I also recently had a chance to check out the 2025 Cloud Risk Exposure Impact Report from ZEST Security.
It provided a handful of insightful findings related to cloud security, incidents and what organizations are doing to try and address the challenges, as summarized below:
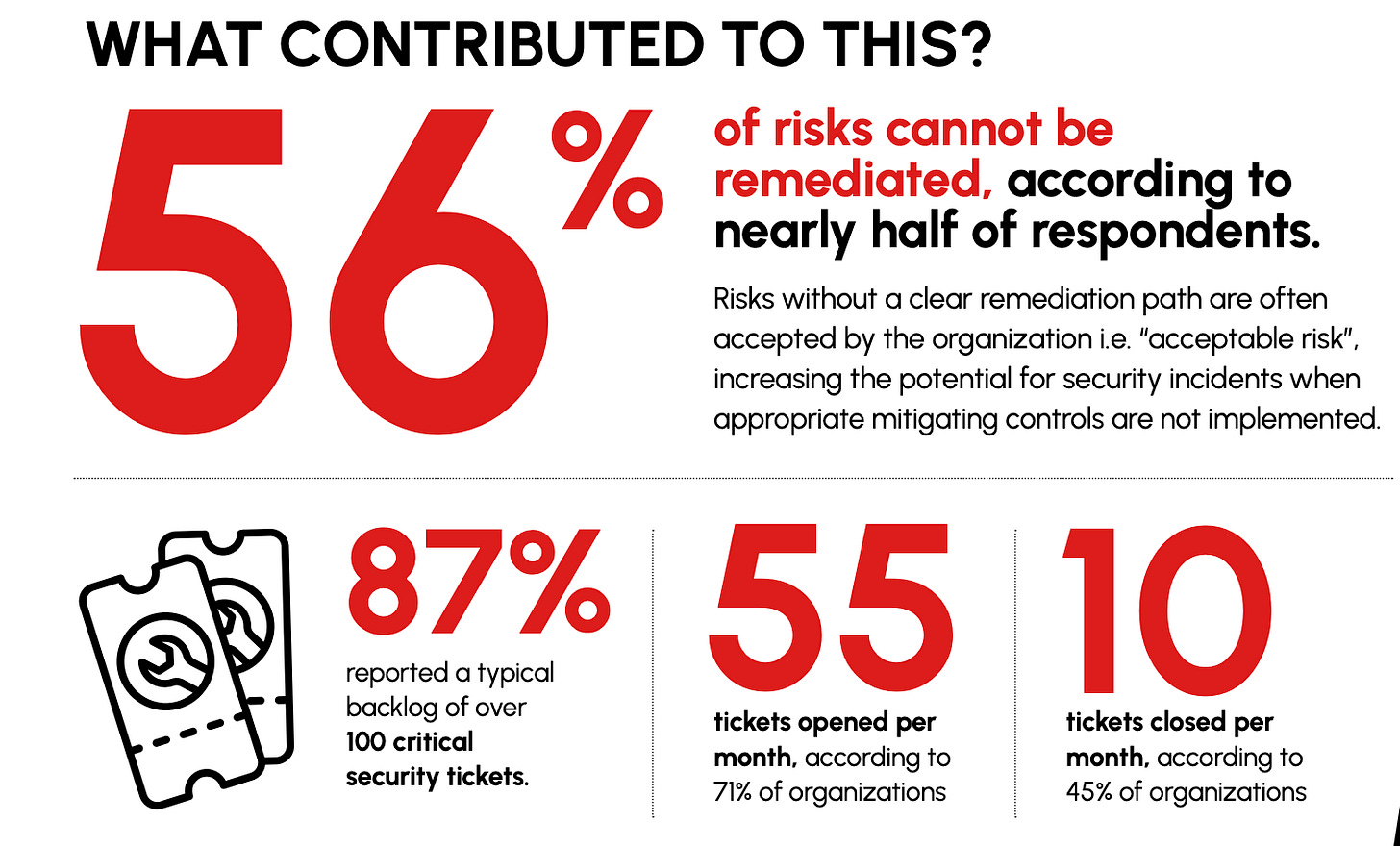
If you’re following the AppSec space, several of these shouldn’t be surprising. For example, it states 62% of organizations had incidents originating from issues the security team already identified. This is tied to the fact that organizations have vulnerability backlogs in the hundreds of thousands to millions and extensive risk registers. Organizations simply can’t keep pace with the growth of vulnerabilities, pace of development, or organizational initiatives that take priority over security.
Organizations remediation capacity and cadence is still far outpaced by that of attackers, with the report finding it takes attackers 10X less time to exploit vulnerabilities than it does for organizations to remediate them and the annual remediation costs are over $2M.
The report goes on to discuss some of the factors contributing to these challenges, such as the fact that 87% of organizations have a backlog of over 100 critical security tickets and 71% of organizations are adding at least 55 new tickets a month but 45% of organizations are only closing 10 tickets a month. You can see how it is easy for security issues and technical debt to accumulate over time, becoming a massive problem for organizations and ripe for the picking by attackers.
Attackers are getting incredibly efficient too, only needing 5 days on average to exploit (e.g. time-to-exploit (TTE)) vulnerabilities, down from 32 days the year prior. So while attackers continue to improve their efficiency, defenders continue to degrade ours.
This of course is due to factors such as the reality that attackers can focus on a single vulnerability and exploiting it, and defenders are facing down literal thousands of vulnerabilities they need to address, coupled with the organizational friction of getting teams to prioritize remediation over competing goals such as speed to market, feature velocity, and revenue.
The report provides some insight into what is actually occurring when it comes to meantime-to-remediate (MTTR), including prioritization and analytics as well as remediation efforts. Organizations particularly are struggling with remediation of container and application level risks, as well as those in Infrastructure-as-Code (IaC).
In my experience this is due to technical nuances of containers, IaC and applications and the underlying tech stacks involved, as well as organizational relationships and dynamics between teams such as Cloud, Infrastructure, AppDev, Security and the business.
The involved cost of remediation goes beyond the specific fix too, including people, labor hours, tickets, and of course addressing the vulnerability, misconfiguration or weakness itself, as well as operational costs such as business disruption. These numbers can climb exponentially too in cases such as ransomware, where financial extortion is involved.
Overall the report is a great look into the state of remediation (or lack thereof), organizational challenges causing delays in remediation, an impedance mismatch with exploitation, and the costs involved in remediation.
Be sure to check out the full report for more.
CVSS Is Dead to Us
In a bit of a damning piece by Daniel Stenberg, who maintains the hugely popular open source projects curl and libcurl, Daniel takes CVSS to task. Critiques include limitations around input factors for the CVSS calculation which produces the CVSS score, as well as Daniel criticizing how the scores are produced. He says it is really designed when you know exactly when and how a product is use and how an exploit will impact it, which isn’t the case when CVSS scores are being done generically and then just consumed downstream across the vulnerability ecosystem with no context or further refinement of scoring.
Daniel’s piece goes on to discuss a myriad of issues, such as CVSS scores being inaccurate, projects like curl not engaging the CVSS nonsense, but other entities such as CISA and their “vulnrichment” program, which adds CVSS scores to vulnerabilities, how that has and will continue to lead to false alarms and “critical” vulnerabilities, the toll it takes on project maintainers and much more.
All of this not only takes a toll on maintainers or vendors but inevitably also organizations conducting vulnerability management and dealing with awful scoring that is inaccurate but they are wasting scarce resources trying to remediate or mitigate nonetheless.
CVSS-driven remediation timelines are still required in many compliance frameworks and industries, including the DoD and Federal space where I spend a lot of my time, despite several damning critiques pointing out how inaccurate and inefficient it is.
Introduction to Cloud Vulnerability Management
There’s no denying that VulnMgt in the cloud looks much different than it did on-premise. From the growth of managed services from CSPs, the adoption of containers and Kubernetes and more.
This is a great discussion from James Berthoty of Latio Tech that covers some of the major fundamental differences with VulnMgt in the cloud where he also shares several helpful visualizations to help make his point.
We also see the rise of several new tools such as CNAPP, ADR, CSPM and the list goes on. James helps makes sense of it for those looking to better understand VulnMgt in the cloud.
North Korean Hackers Impersonated Recruiters to Steal Credentials from Over 1,500 Developer Systems
At the weird intersection of social engineering and the software supply chain, we have news that North Korean hackers continue to impersonate Recruiters and are targeting Developers. This was done by the Lazarus group, and are using social engineering tactics to extract development credentials, authentication tokens, passwords and more.
As I have written about in various articles and my book Software Transparency, Developers are a key attack vector and potential weakness in the software supply chain and their credentials can be used to access sensitive data, and contribute malicious code into products, projects, components or more and impact downstream consumers and customers of the software.
The hackers have been getting Developers to download malicious software onto their systems and in this case it involved copying legitimate applications and setting up rogue GitLab repos with backdoor versions of software packages.