The Evolving GRC Landscape
A Look at HyperProofs 2025 IT Risk and Compliance Benchmark Report
Anyone who has followed me for some time knows I’m a big proponent of GRC for effectively managing organizational risks.
While phrases such as “compliance doesn’t equal security” are thrown around without context, the reality is that compliance drives organizational investments in cybersecurity more than any other single factor in security.
Compliance does equal security, albeit not the elimination of risk.
Compliance is the floor, not the ceiling when it comes to sound security, but without it, we would be in free fall.
That’s why I’m excited to recap Hyperproof’s new 2025 IT Risk and Compliance Benchmark Report, which provides a comprehensive look at the evolving GRC landscape.
So, let’s check it out!
Key Findings
91% of respondents have a centralized team to manage GRC
60% of respondents who manage risk ad-hoc or when a negative event happens experienced a data breach in 2024
63% said their GRC budgets will increase in the next 12 to 24 months
52% report that their teams spend between 30-50% of their time on manual tasks
55% say they use a common controls framework to streamline GRC processes
Maturing the GRC Function
As the GRC space has evolved, so have organizations' teams and approaches to handle GRC.
Earlier in 2024, Hyperproof created an in-depth, actionable GRC Maturity Model that aligns with respondents' steps to mature their GRC programs in the last year. The GRC Maturity Model is a vendor-agnostic, practical roadmap for organizations to improve their GRC business process so they can enter new markets and successfully navigate the rapidly changing regulatory and legal space.
The themes in this model align with respondents' methods to mature their GRC programs — a notable finding from the report.
Respondents use four strategies to mature their GRC programs:
Centralizing GRC Efforts Under a Single Team
I mentioned above that 91% of organizations reported having a centralized team to manage their GRC activities.
This makes sense on various fronts. Not only is it difficult for multiple disparate teams to ensure an organization effectively implements GRC requirements, but it can also lead to significant inefficiencies as organizations look to crosswalk controls across the various compliance frameworks they adhere to (more on that later).
Centralizing the GRC function helps both strategically and tactically. It empowers one group to lead GRC for the organization and helps tactically reduce inefficiencies and discrepancies among controls and frameworks or when dealing with auditors and assessors.
As discussed above, the centralization of GRC within the enterprise under a single team seems to be a trend across over 90% of organizations.
Leveraging a Common Controls Framework (CCF)
Another strategy used by organizations that have matured or are looking to mature their GRC function is leveraging a common control framework (CCF).
For those who have worked in GRC, like me, the list of potentially applicable compliance frameworks is exhausting: FedRAMP, HIPAA, HITRUST, SOC2, ISO standards, etc.
It’s so problematic that in 2024, we saw the U.S. Office of the National Cyber Director (ONCD) release an RFI to push for “Regulatory Harmonization” to try and help the ecosystem rationalize the overwhelming and confusing compliance landscape that continues to grow.
By leveraging a CCF, organizations can cross-walk the various security controls they have in place under one framework to others, mitigating redundancy, rework, and wasted resources.
Hyperproof’s report found that most organizations are leveraging CCFs to deal with various cyber and compliance controls that differ by region, nation, and more.
Conducting Quarterly Risk Assessments
Only 8% of respondents conduct risk assessments annually, a huge reduction from 45% in the previous year’s survey. This year, most respondents (59%) conduct quarterly risk assessments. One reason for this shift is the continued adoption of risk management technology, reducing the burden of conducting these assessments. Companies have realized the value of having real-time visibility of their risk postures.
Adopting Comprehensive Risk Management Programs with People, Processes and Technology
People, processes, and technology are the paradigm of cybersecurity. 58% of all respondents recognize that IT risk management requires integrated efforts across roles and teams.
However, it found that while 38% of organizations have matured to the point of having an integrated approach to risk management, many are either functioning in a reactive mode to negative events, entirely reliant on third parties such as MSSPs, or handling IT risks in siloed departments rather than taking a comprehensive approach of integration and collaboration.
Framework Adoption Trends
The report also provides insights into framework adoption trends and how organizations optimize their GRC activities.
For example, 72% of the organizations reported using software to monitor security controls and provide streamlined reporting. This makes sense, especially as more organizations continue to adopt cloud-native technologies that provide robust APIs, automation, and integration opportunities for reporting and visibility.
I previously discussed the myriad of compliance frameworks and requirements organizations grapple with, and the chart below from Hyperproof makes that point very well.
I don’t know about you, but my head hurts just looking at that chart, and I live and work in cybersecurity. Imagine our development, engineering, and business peers.
While ISO may be leading the pack, many of these frameworks and requirements aren’t optional, especially depending on the organization's region and the data types it interacts with. This further emphasizes why organizations are adopting software and platforms to help them effectively manage the overwhelming number of compliance frameworks and requirements they are dealing with.
Something else I found interesting was the rapid adoption of NIST’s AI Risk Management Framework (RMF). While NIST RMF and NIST 800-37 have been around for quite a while and are high on the list of adopted IT risk management frameworks, the NIST AI RMF is relatively new, and it shows how quickly organizations are adopting it to keep pace with the rapid business adoption and integration of AI.
The report also stresses that organizations are adopting AI frameworks such as NIST AI RMF due to AI risks and in reaction to the regulatory landscape, most notably the EU AI Act, in which 59% of respondents said they had implemented AI-related controls in reaction and preparation.
This shows how powerful a forcing function regulatory requirements are and contradicts the commonly used trope that “compliance doesn’t equal security.”
Compliance is inarguably one of the strongest drivers for adopting risk management and governance measures within organizations. The report makes this point, which we will discuss below as well.
Hyperproof’s report also demonstrates the correlation between investments in GRC —especially for those using an integrated, automated approach to managing GRC and the number of breaches experienced by respondents. The report found that 60% of those who manage IT risks in an ad-hoc fashion experience a breach, compared to 41% of those who take an integrated and automated approach to IT risk management.
While there were signs of further adoption of software and automation to streamline compliance efforts, over half of the respondents admitted that their teams spend 30-50% of their time with manual administrative tasks.
This is alarming in an IT landscape of APIs, cloud, CI/CD pipelines, microservices, and automation. This involves wasting organizational resources and the potential for oversights in control testing and validation. It also stresses the need for organizations to adopt cloud-native automation platforms to help with compliance automation. I’ve often quipped that GRC missed the bus on DevOps, and the widespread prevalence of manual, tedious work drives this point home.
Despite signs of adopting modern risk management software, almost half of the respondents admitted to still using forms, questionnaires, and spreadsheets to manage third-party risk, so manual activities and static documentation are still prevalent.
We know this isn’t sufficient in an environment where code changes in hours and threats are dynamic and constantly evolving. When contrasted with legacy static GRC documentation, there's an impedance mismatch.
One bright light among the findings related to legacy manual activities is that the GRC ecosystem is increasingly looking to AI as a potential force multiplier for everything from reviewing documentation, recommending relevant controls, conducting research, and even writing policies.
Given the technology's strong performance on language-specific activities (e.g., policies, processes, control statements, etc.), this is unsurprising and hopefully can accelerate GRC activities and outcomes.
The same group also said they are implementing various measures to monitor and govern AI risks, such as manual monitoring, tooling, policy and process revisions, and more.
So, the use of AI is a double-edged sword. It can help, but it comes with its own unique risks.
Third-Party Risk
Supply chain risk management (SCRM) continued to be a hot topic among those surveyed. Positive trends show that organizations continue to realize the risks from their suppliers and the broader third-party ecosystem.
94% of organizations reported aligning their stakeholders with their SCRM policies and processes. Respondents have even increased their risk assessments of suppliers, jumping from 61% the previous year to 79% this year.
They have also begun integrating more rigorous contract language and clauses with third parties to meet their SCRM objectives and working with external suppliers and providers as part of their incident response and recovery activities.
This is great to hear, as we see organizations continue to be impacted by security incidents involving third parties such as MSPs, CSPs, software vendors, and others. The survey confirmed this is a significant problem, too, with 55% of organizations stating they experienced supply chain disruptions due to cyber issues and 46% even stating they had a data or privacy breach from third-party vendors that impacted their data.
GRC Investments and Budgets
We should examine their investments because organizations continue to see GRC as a critical function that helps with compliance, risk management, and overall governance. The report provides just that, so let’s take a look.
One noteworthy phrase is that organizations view GRC and security as safeguards from risks and regulatory penalties and key enablers of growth and market expansion. I have discussed this in other articles, such as “Compliance Does Equal Security—Just Not the Elimination of Risk.”
It is incredibly common for customers, prospects, and partners to ask if your organization has SOC2, FedRAMP authorization, or other compliance designations and credentials as a signal of trust. This occurs in nearly every procurement and purchase interaction, demonstrating that compliance genuinely facilitates business growth and expansion and provides ROI.
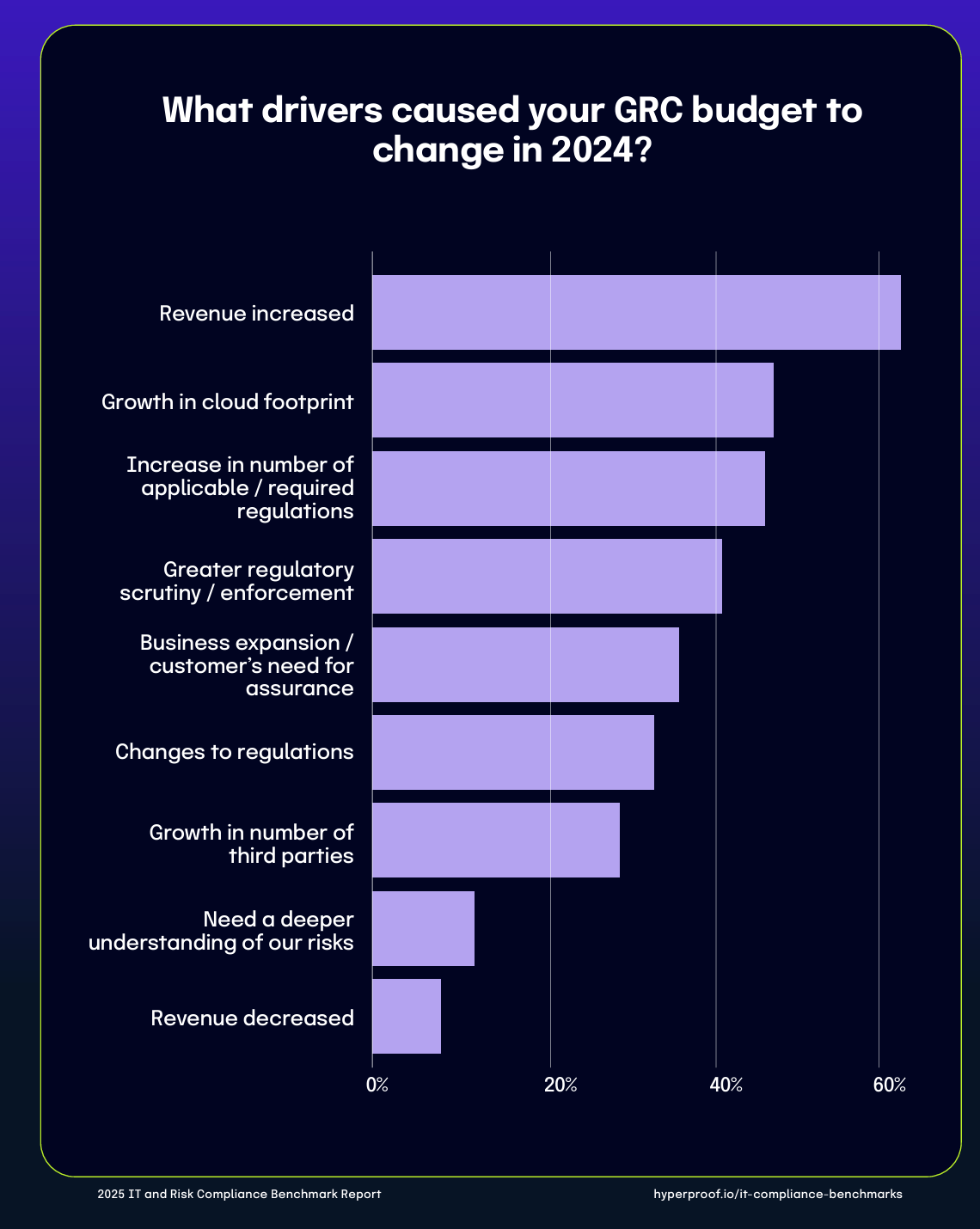
The respondents' insights about budgets support this. For example, 77% stated their GRC budget increased, while only 6% saw it decrease (the rest remained stable). This is also a natural outcome of an organization’s growth; as the survey states, as organizations grow in revenue, cloud footprints, industries, and general business expansion, their GRC budget sees a correlating growth.
Knowing that budgets are growing and how they are being allocated is useful. The survey demonstrates that organizations are distributing their GRC budget investments fairly evenly across staff, tooling, managed service providers, and external professional services, all supporting their broader GRC objectives and audits they must undergo for the various compliance frameworks.
Roles and Responsibilities in GRC
Another interesting area the report highlights is who is responsible for GRC among the various types, sizes, and sectors of organizations involved in the survey.
One promising trend they highlight is the push towards shared responsibility among GRC, with responsibilities being distributed across roles within an organization rather than the CISO or security leader bearing the burden alone.
That said, while GRC is becoming more collaborative with a diverse mix of business stakeholders, its ultimate oversight and championing still comes from the C-suite, at least for 43% of the organizations surveyed.
This emphasizes the need for the C-suite, still often the CISO, or equivalent for mid-sized and small organizations to go out and gain buy-in and support for compliance goals and ensure effective risk management and governance across the organization through a combination of tools and technologies but also effective policies and processes and arguably most importantly, relationships and rapport.
As a sign of compliance's continued complexity and importance, 72% of those surveyed anticipate their compliance team growing. In comparison, 27% said it would stay the same, and only 1% expected their compliance team size to shrink.
This growth consensus seems pervasive regardless of industry, with similar responses from organizations in technology, banking, financial services, healthcare, etc.
This shows that GRC teams will remain fundamental to security and overall organizational risk management. Organizations are investing in their GRC teams to address existing regulatory commitments and support new requirements as the business grows and expands and the regulatory landscape evolves.