Resilient Cyber Newsletter #74
Economics Hits Cyber, U.S. Cyber Strategy Coming, American Dynamism, PANW Enters Observability, AI-Driven Cyber Espionage, Vibe Coded Vulnerabilities & Entering the AI SAST Era
Welcome
Welcome to issue #74 of the Resilient Cyber Newsletter!
While we may be heading into the Thanksgiving and the broader holiday season, things certainly aren’t slowing down. We have news this week providing insights into cyber budgets and spending patterns, rumors of the forthcoming U.S. Cyber Strategy with an offensive focus, M&A moves by industry leaders such as PANW and innovative disruptors such as Endor Labs in AppSec driving the future of SAST with AI.
So, let’s get to it!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 40,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Reduce Risk Exposure with Automated Compliance Monitoring
In a world where cyber threats evolve faster than manual audits, visibility and automation are key to reducing risk. That’s why we’re seeing GRC engineering rise, to replace snapshots, spreadsheets and manual toil with automation, integration and acceleration.
Drata empowers security and compliance teams to continuously monitor and prove compliance across frameworks like SOC 2, ISO 27001, and HIPAA—without slowing business operations.
Their platform integrates with your existing tech stack to surface real-time risk insights, streamline evidence collection, and eliminate the manual overhead of compliance readiness.
Whether you’re protecting your organization’s reputation or building trust with customers and stakeholders, Drata helps you stay audit-ready and resilient—continuously.
Take control of your compliance posture today.
Cyber Leadership & Market Dynamics
Uncertain Economy Takes Toll on Cybersecurity Teams
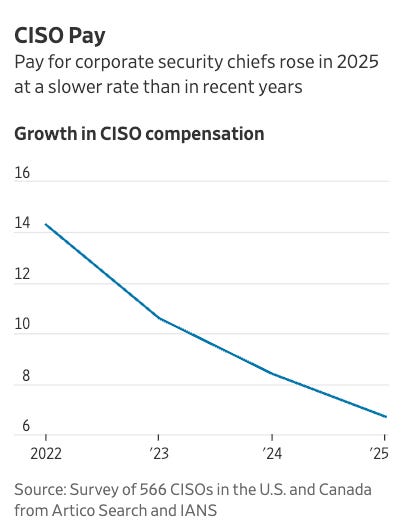
While security is often framed as being resilient to economic headwinds or recession-proof, the truth is much more nuanced. This article from WSJ highlights how everyone from CISOs to ICs in cyber is facing tighter budgets, slower wage growth, and stalled hiring plans amid broader economic uncertainty.
The piece discusses how corporate cyber budgets grew an average of 4% this year, which is a five-year low, based on insights from a survey by Artico Search and IANS, the latter of which I’m a faculty member.
They gathered these insights from 550 CISOs and security leaders, which revealed a slowing of growth in hiring, along with a decline in CISO base salary gains from 5.7% last year to 4.8% this year.
The article rightly points out that, despite stagnant budgets and compensation, CISOs are being asked to take on more than ever, and do more with less, especially amid the rapid adoption and growth of AI across enterprises.
Palo Alto Networks (PANW) Acquires Chronosphere - Targeting Observability
As part of its broader AI strategy, PANW has announced it is acquiring Chronosphere, which focuses on visibility. PANW’s CEO mentioned that the move will help them transition from passive monitoring to a groundbreaking autonomous remediation platform.
Not only does this position PANW as moving beyond just Cyber, both in technical capabilities and buyer personas, but also in budgets and total addressable market (TAM). The strategy and focus on remediation and autonomy also align with broader trends in Cybersecurity that are evolving alongside the AI adoption curve.
New U.S. Cyber Strategy To Go on the Offensive
Numerous rumors are circulating about the forthcoming U.S. Cybersecurity Strategy, based on public comments from representatives, including the U.S. National Cyber Director, Sean Cairncross.
Much of the hype revolves around the fact that it will place a significant emphasis on offensive cyber operations, imposing a cost on adversaries and introducing consequences, which represents a shift from the historical focus on defensive cyber.
Sean made comments at an event recently where he stated:
“The United States has not done a terrific job of sending a signal to our adversaries that this behavior is not consequence-free.”
Other key focus areas anticipated include bolstering partnerships with industry, streamlining the regulatory environment, and freeing up resources to focus on U.S. priorities sector by sector.
Awesome Annual Security Reports
If you’ve been following Resilient Cyber or me for any time, you know I’m a big fan of security reports, as they provide insightful trends, analysis, and more for cyber practitioners, investors, founders, and other stakeholders in our ecosystem.
That’s why this repo from Jacob Wilson, “Awesome Annual Security Reports,” is, well, awesome. It includes hundreds of security reports, some survey-based, some analytical, and other methodologies, covering everything from Cloud to App Security, Ransomware, data breaches, and AI.
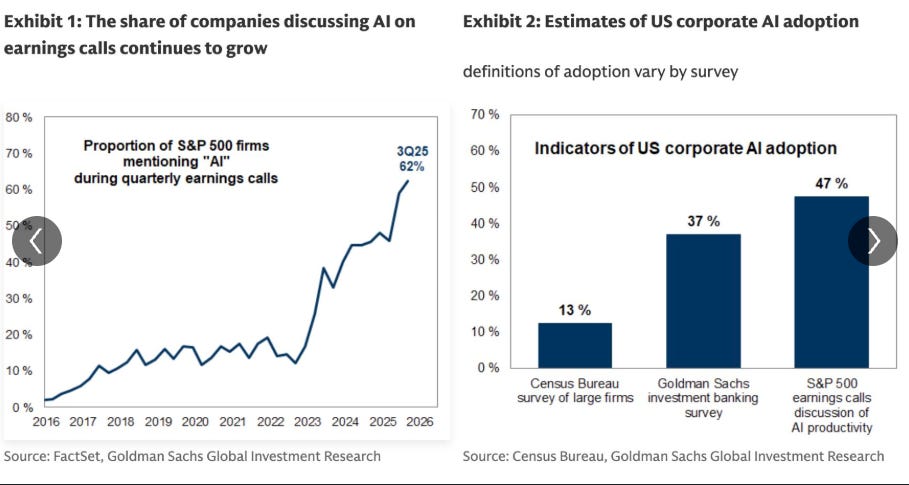
AI Adoption Insights
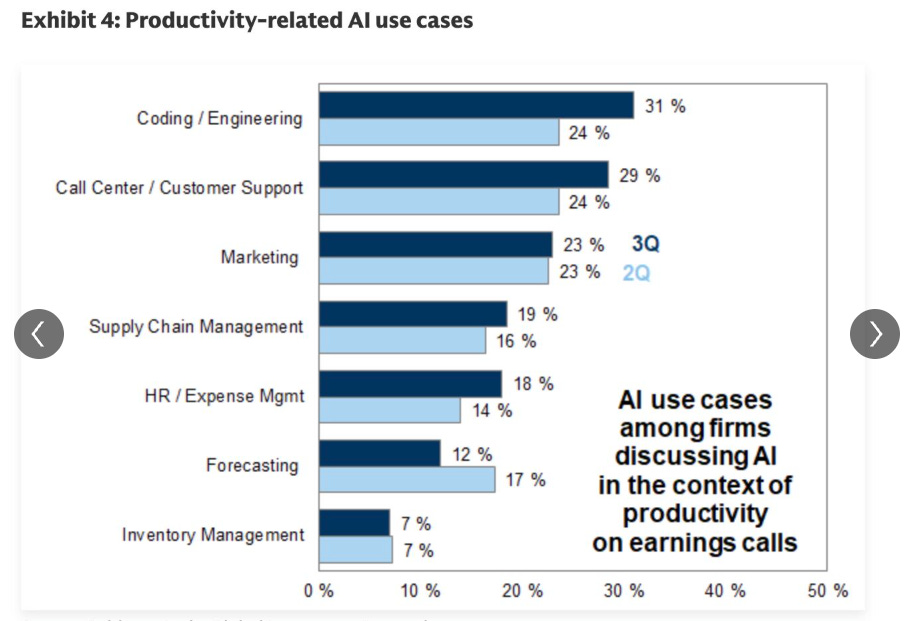
Ed Sim recently took to LinkedIn to share some insights from Goldman Sachs regarding AI adoption. It shows key metrics, such as the proportion of S&P 500 firms mentioning “AI” during earnings calls, along with how firms define adoption.
Coding and engineering are still dominating the productivity-related AI use cases, with widespread adoption at roughly a third of SP500 firms:
That said, as Ed points out, while everyone is talking about adoption, most still haven’t quantified the actual impact of AI on things such as profitability:
Cloudflare Joins the Outage Festivities
Following several recent outages from major providers such as AWS and Azure, Cloudflare recently experienced an outage that affected services from prominent vendors, including X, ChatGPT, and others.
Cloudflare is often invisible to users but underpins many of the most widely visited sites and services online. On Tuesday, news broke that several major sites and services went offline, leaving tens of thousands of users unable to access them.
EU Plans to Ease Rules for Big Tech
News is circulating that the EU Commission is introducing sweeping changes to Europe’s “digital rulebook”, with some expressing frustration that it will weaken privacy protections. In contrast, others are glad to see the EU back off on what they feel is a cumbersome regulatory approach that hinders the EU’s innovation and economy.
It would also delay the implementation of strict AI regulations until late 2027.
This is an interesting move from an entity that prides itself on being a regulatory rather than economic superpower. This reminded me of an episode of the a16z podcast I had recently listened to with guest David Sacks, who is the U.S.’s AI and Crypto Czar, where the group joked that the key to succeeding is basically doing the opposite of whatever the EU does, given the EU seems intent on regulating rather than innovating, and not concerned with the economic or national security implications their regulations have.
This is an excellent conversation that doesn’t just focus on the U.S. vs. China, or the EU but on the state of AI more broadly, with David and the hosts covering everything from regulation, to adoption, model capabilities, and more.
Speaking of the reference to the EU’s preference to regulate, and ignoring the consequences it will face as a result, I recently read an excellent piece from Azeem Azhar titled “How Europe Outsourced Its Future to Fear”, where it breaks down the EU’s general cautionary approach to everything such as energy and technology, including AI, all to the EUs own detriment in terms of prosperity and relevance.
There’s an irony here too, given I host a cyber blog/newsletter, and many in the cyber community have been clamoring for the U.S. to be more like the EU, for the unspoken reason that they know compliance is what primarily drives security spending, so it is in their own self-interest, often dressed as altruism and safety.
American Dynamism - There’s Never Been A Better Time to Build a Defense Company
It’s no secret that I’m incredibly passionate about cybersecurity and its intersection with national security. From my time on Active Duty in the USAF, to now being the Cofounder and CEO of a public sector and defense focused digital services company in Aquia.
Which is why, speaking of a16z , I also enjoyed another recent episode they did where they sat down and discussed Why Silicon Valley Turned Against Defense (and how that is now changing.
It was was a wide ranging discussion covering politics, culture, venture capital, technology and more, oriented around national security. I enjoyed the conversation, and I suspect many others will too.
AI
Anthropic Disrupts the First Reported AI-Orchestrated Cyber Espionage Campaign
If there was one story that dominated the cyber ecosystem and socials this past week, this is it. Anthropic released a report detailing how they disrupted the first reported AI-orchestrated cyber espionage campaign.
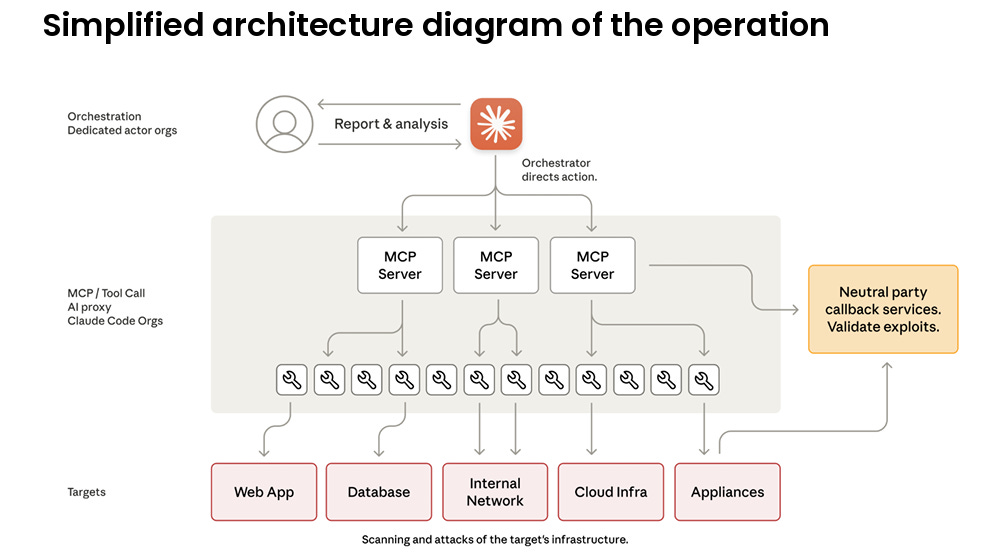
This builds on their prior threat intelligence report in September, where they discussed how a malicious actor was able to use their platform to implement attacks against tens of victim firms. This latest release primarily garnered attention due to its autonomous nature, with the report stating that it targeted 30~ entities and the attacker was able to use Claude and agents to autonomously carry out 80-90% of their attack activities through the full attack lifecycle, from reconnaissance through exfiltration.
As seen below, the activity involves orchestration, agents, MCP servers, the use of open source hacking tools and more.
The full report is well worth a read.
It has been a polarizing report, with many cyber leaders taking to social media platforms and blogs to proclaim that we’re in a new era of cyber, where attackers autonomously exploit victims using AI. Others have claimed it was a marketing effort by Anthropic to boast, while VCs have claimed this is why they have invested in their various portfolio companies. The truth is that all of these perspectives and angles have flavors of truth to them, and we are indeed entering a new era.
I’ll be sharing various resources throughout this week's newsletter, highlighting the different perspectives and takes on this event.
Three Buddy Problem Take on Anthropic Report
In the vein of sharing perspectives I found interesting on Antropic, one of them was from the “Three Buddy Problem” show, which I follow and is hosted by Ryan Naraine, Costin Raiu, and Juan Andres Guerrero-Saade.
They dove into the report, critiques, what may be driving it, and its implications for the industry, among other aspects. Juan, in particular, had some spicy takes I enjoyed.
AI for Offense is Here. Defenders Aren’t Ready
A bit of a different perspective from the three folks above, Anshuman Bhartiya, who I have been following for sometime when it comes to AI and AppSec penned a piece discussing the incident and the signs it shows related to attackers use of AI. He discusses how defenders simply aren’t ready for this scale of autonomous attacks and defenders critically need to modernize and adopt AI similarly to their attacker counterparts.
One great example is a tool he built himself called “SecureVibes”, that leverages traditional SAST along with AI to identify vulnerabilities in Vibe Coded applications.
Fully Scaled Agents
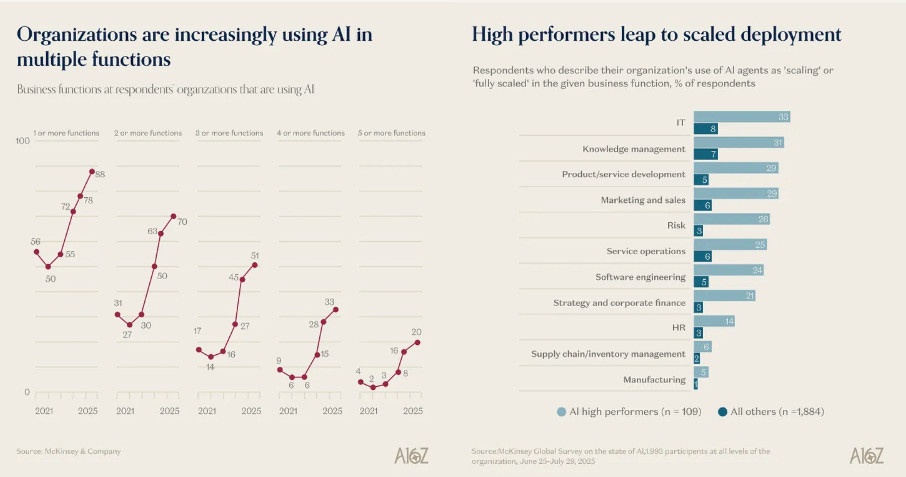
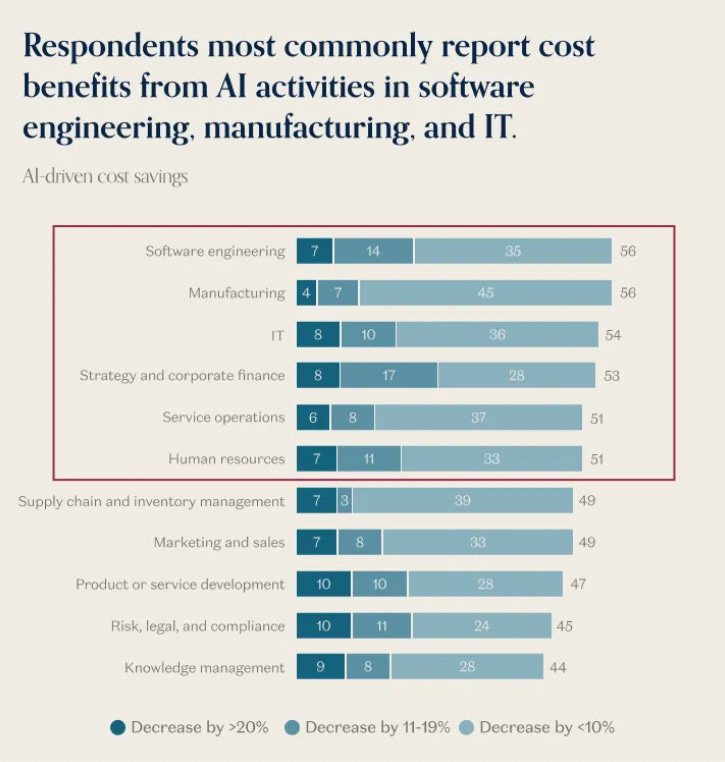
a16z recently shared their “charts of the week”, and among them are insights showing that organizations are increasingly using AI for multiple business functions, as well as where cost savings are showing up the most, with software engineering and IT among those leading the pack.
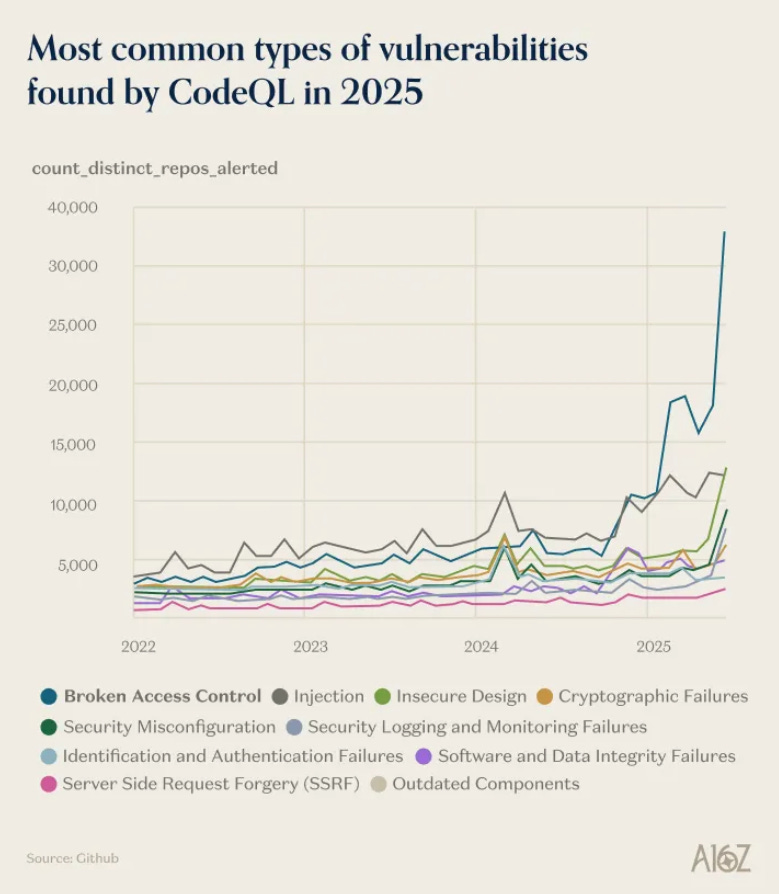
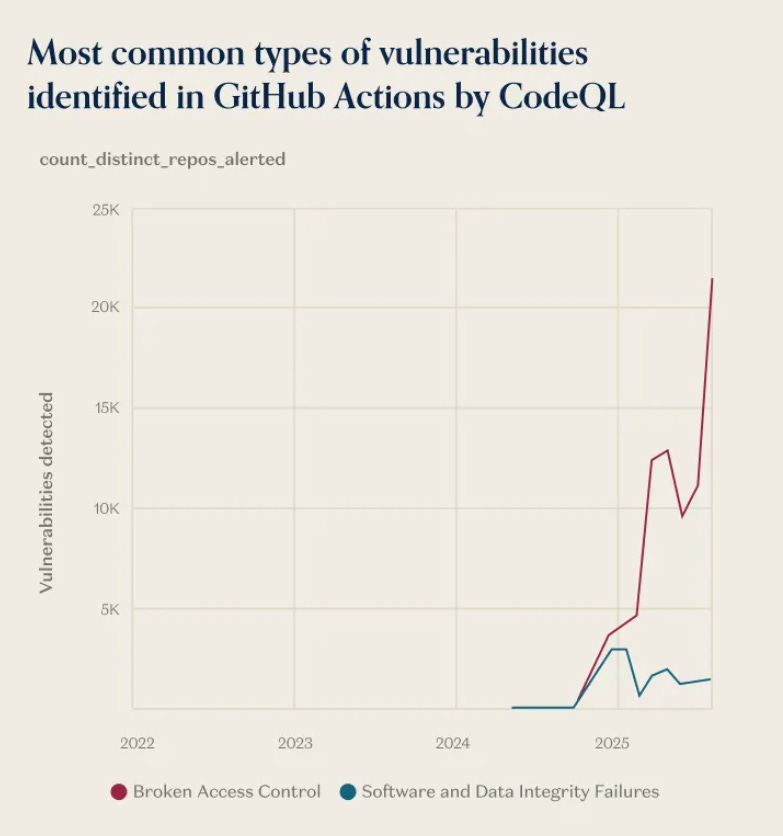
They also shared a couple of graphs shining light on the vulnerability management ecosystem, which I found awesome to see, and their findings align with the latest OWASP Top 10, demonstrating why risks such as Broken Access Control (BAC) dominate the top spot.
Interestingly enough, they attribute it to vibe coding/AI-generated code, which is precisely why we’re seeing a lot of excitement around AI-SAST. Many look to combine SAST and LLMs to address non-rule-based findings and account for unique business contexts, data flows, and more.
He’s Been Right About AI for 40 Years. Now He Thinks Everyone Is Wrong
In an interesting article from WSJ, it discusses how AI pioneer Yan LeCun may be leaving Meta as he thinks the entire industry is over hyped on LLMs and the future of AI. LeCun seems poised to leave Meta to work on “world models”, which he thinks are more critical to advance AI than LLMs. This is a view shared by others, such as other AI leader Fei-Fei Li , who recently had a piece on the a16z blog titled “From Words to Worlds: Spatial Intelligence is AI’s Next Frontier”.
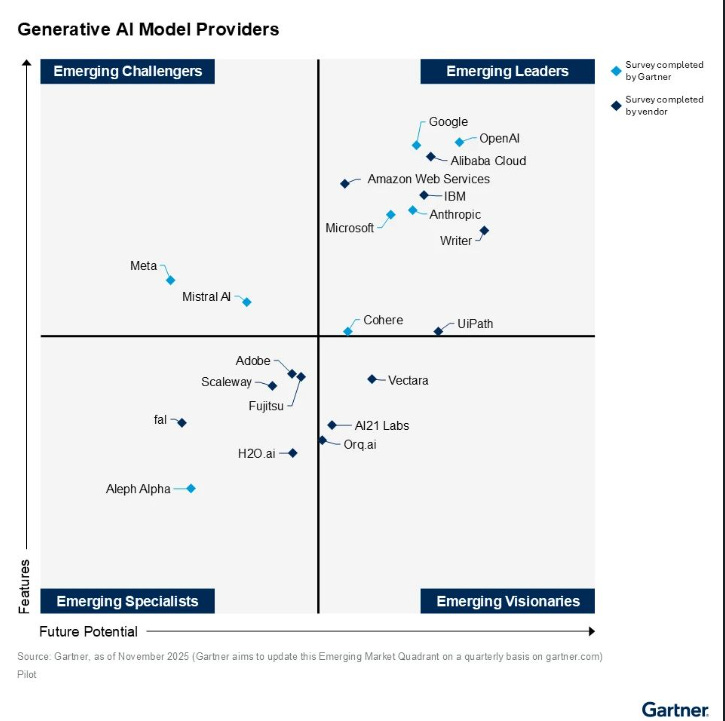
Gartner Provides Emerging GenAI Model Provider Magic Quadrant (MQ)
Now, I know most folks take Gartner’s MQ’s with a grain of salt but given this is the first MQ they provided for Emerging AI Model Providers and what I found most interesting is just how far behind Meta is given the massive investments and hires they have made to try and position themselves in the market. They’re also the primary vendor focusing on open source models, which is much different than OpenAI and Anthropic, who albeit have some mix of open source models, largely are commercial GenAI providers.
AppSec
Endor Labs Launches AI SAST That “Thinks Like a Security Engineer”
You’ve inevitably seen me share content from Endor Labs and I’ve been the Chief Security Advisor with the team for quite a while now. They originally caught my attention early due to their amazing leadership in Varun who helped pioneer the CSPM category but also their novel approach to SCA, which involved a emphasis on reachability analysis, exploitability, known exploitation and more, and tackling challenges around open source and software supply chain security.
One of the longstanding challenges of SAST historically has been that it has had high false positive (FP) rates, leading to frustrations by security and developers alike. However, I recently shared research that demonstrated how you can combine traditional SAST with AI to drastically reduce FPs and also detect complex business logic and architecture flaws, which is what Endor Labs is now doing in practice with this new launch.
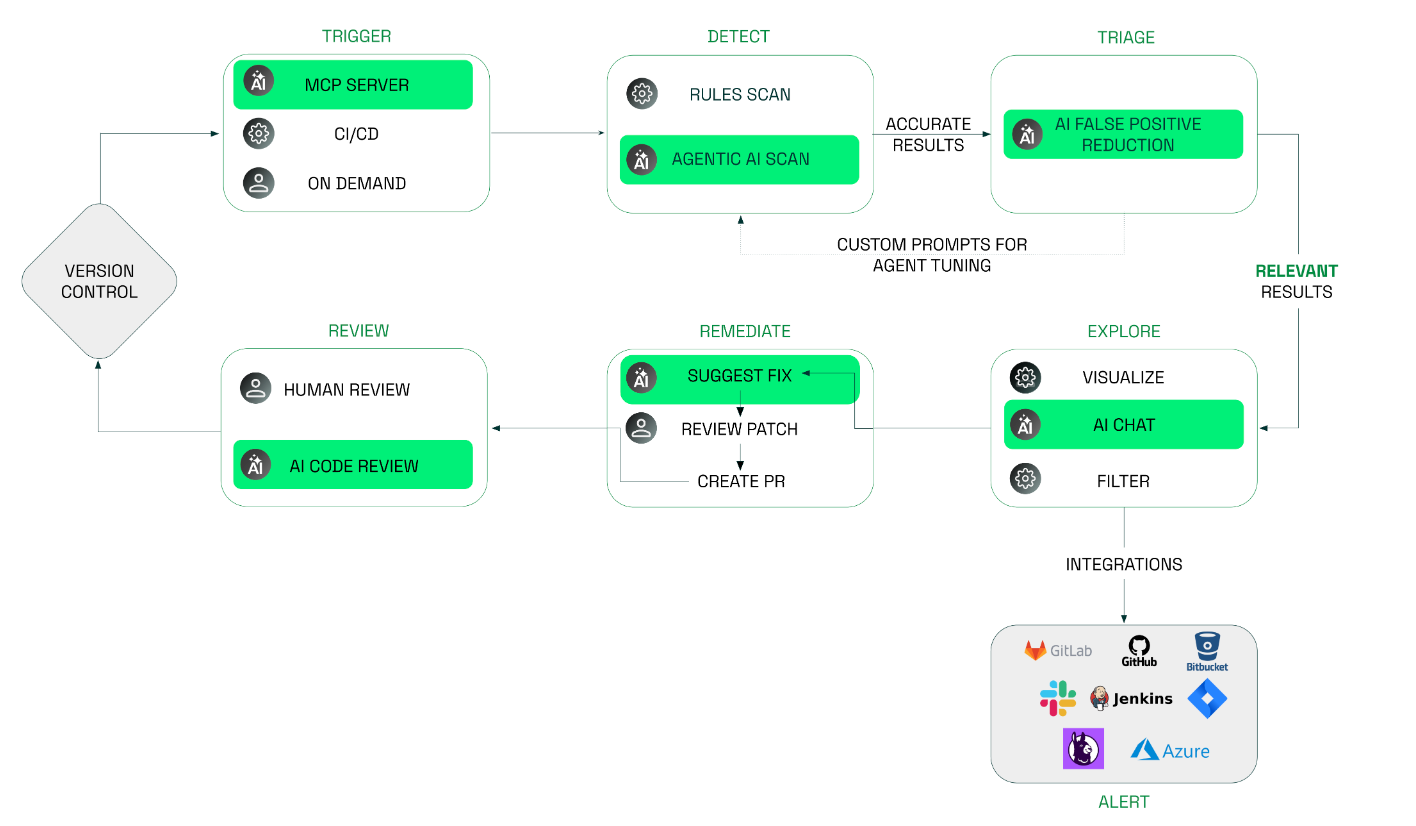
Their approach is multi-model, leveraging the best of SAST and rule based approach to detect known patterns but also AI reasoning to understand intent and context that traditional rule-based SAST has missed.
Even more cool, they leverage a multi-agent architecture, with agents scope for specific tasks such as detection, triage and remediation in tandem, and they work with Endor’s AI Security Code Review agents which look at PR’s to assess security posture and security implications of changes. You can see a notional architecture below:
Hats off to the team for their continued innovation and AppSec leadership!
2025 Exposure Management Index 📊
The vulnerability management space continues to evolve, with some organizations moving towards continuous threat exposure management (CTEM), aiming to optimize their approach to mitigating vulnerabilities and risks.
Most reports focus on large enterprise environments, despite our knowledge that SMBs struggle with expertise, resources, and other challenges, with many operating below the “cybersecurity poverty line.”
That’s why I found Intruder‘s 2025 Exposure Management Index interesting.
It looks at 3,000 real-world SMBs and trends related to vulnerabilities and risks.
I broke it down in a recent blog, including:
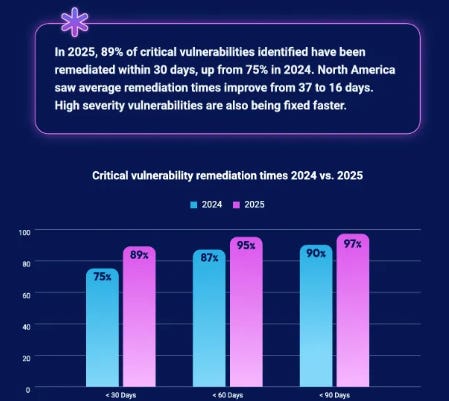
- Teams are making progress on critical vulnerabilities, but lower severities, such as high, continue to grow
- Attackers targeting “vintage” vulnerabilities, or well-known CVEs that simply aren’t remediated and are sitting in vulnerability backlots ripe for exploitation
- The lack of market forces is leading to regulation stepping in, especially in the EU, and the effect it is having on forcing teams to prioritize vulnerability remediations truly
- How SMBs are outperforming their enterprise counterparts in some cases, due to the challenges that scale and complexity bring to large enterprises regarding exposure management
- What were some of the top vulnerabilities of the year in terms of presence and exploitation?
Unsurprisingly, the list includes several “security” vendors, as they continue to expose customers with little to no consequences.
VulnCheck Canary Intelligence
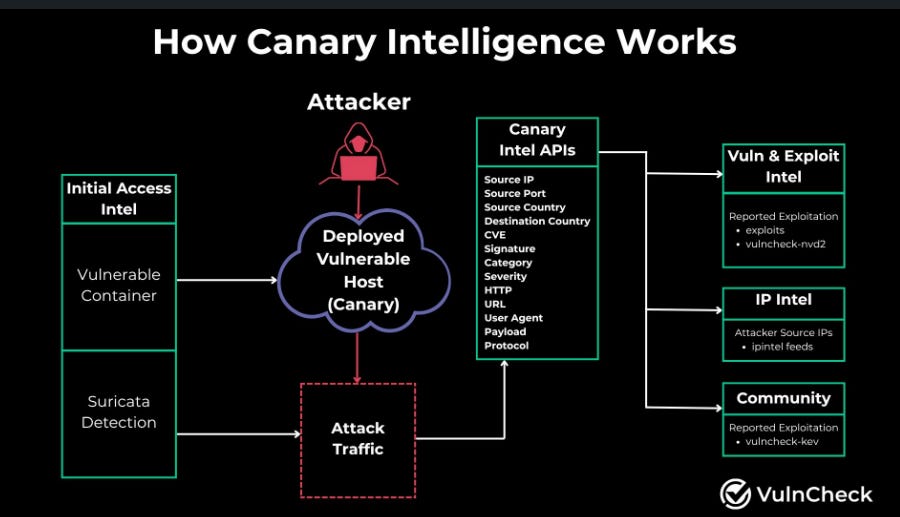
One recent feature launch that caught my attention was VulnCheck’s “Canary Intelligence”. When it comes to vulnerability management, most organizations are now looking to lean into vulnerability intelligence to prioritize known or likely exploited vulnerabilities (e.g. KEV, EPSS etc.)
VulnCheck’s offering is neat in the sense that it is capturing real-world exploitation as it happens and making it available to customers to help drive prioritization. It uses a global network of intentionally vulnerable systems to capture these insights.
Amazon Discovers APT Exploiting Cisco and Citrix Zero-Days
Amazon’s CISO recently took to the AWS Security Blog to detail how the firm identified advanced APT’s exploiting previously undisclosed zero-days in Cisco and Citrix products. This continues the trend of malicious actors targeting identity, VPN and access products to compromise organizations.
It was discovered via AWS’s “MadPot” service, which is a honeypot service and several exploitation attempts of Citrix Bleed Two Vulnerabilities (e.g. CVE-2025-5777) among others. The amazon blog goes into detail regarding the discovery and activities.
OpenAI’s New Model Just Got Much Better At Writing More Secure Code
A big part of the discussion in AppSec lately has been around the security of code models produce. That’s why I found this piece on Forbes discussing a recent research effort from Veracode interesting.
Veracode conducted a study of 100 LLMs across 80 code completion tasks, and scenarios where it could be completed without and with vulnerabilities and weaknesses and they found that “in 72% of tasks, OpenAI’s GPT-5 Mini model wrote code that didn’t contain any vulnerabilities” up from nearly 60% for previous models from the same tests earlier in the year.
This is insightful because something I have been discussing quite a bit and researchers have been digging into is the security of the code that leading LLMs produce, both with security-specific prompts and without. Model selection will play a significant role in subsequent security of code generated.