Exposure Management Metrics
A look at Intruder's 2025 Exposure Management Index - with insights from 3,000 real-world organizations
The vulnerability management world continues to evolve, including a shift towards what is commonly referred to as Continuous Threat Exposure Management (CTEM). For those not familiar with exposure management in cybersecurity, it’s essentially the process of continuously identifying, assessing, and mitigating risks associated with organizational assets. For more of a deep dive on CTEM, you can find my piece “Vulnerability Management Evolves to CTEM”.
However, moving beyond the concept of exposure management, it is incredibly helpful to examine real-world metrics from organizations to understand the current state of exposure management and its implications for organizational risks.
That’s precisely why I’m excited to dig into Intruder’s “2025 Exposure Management Index” in this blog, which includes insights from 3,000 real-world SMB organizations.
2025 Exposure Management Index
Intruder opens their report, acknowledging a problem that plagues the industry: the concept of the cybersecurity poverty line. This is because SMBs, which often have fewer resources and less security expertise than large corporations, still face similar threats and risks. Wendy Nather initially coined the phrase, and the topic is one I’ve written about before, with my friend Ross Haleliuk, in a piece titled “Lifting the world out of cybersecurity poverty”.
There’s a considerable amount of research, reports, and studies on how large enterprise environments handle vulnerabilities, threats, and exposures; however, there is a lack of information when it comes to SMBs. This is why I found the Intruder report insightful, as it addresses this topic for an underserved community in cybersecurity.
Vulnerability Detection & Response Trends
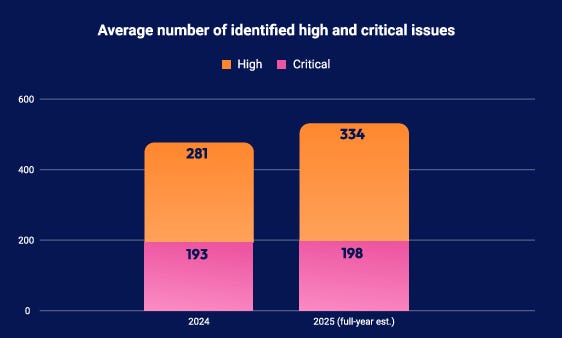
Interestingly, the Intruder team found that while Critical vulnerabilities are staying fairly consistent with 2024, we’re seeing a 20% growth in the number of High findings organizations are wrestling with.
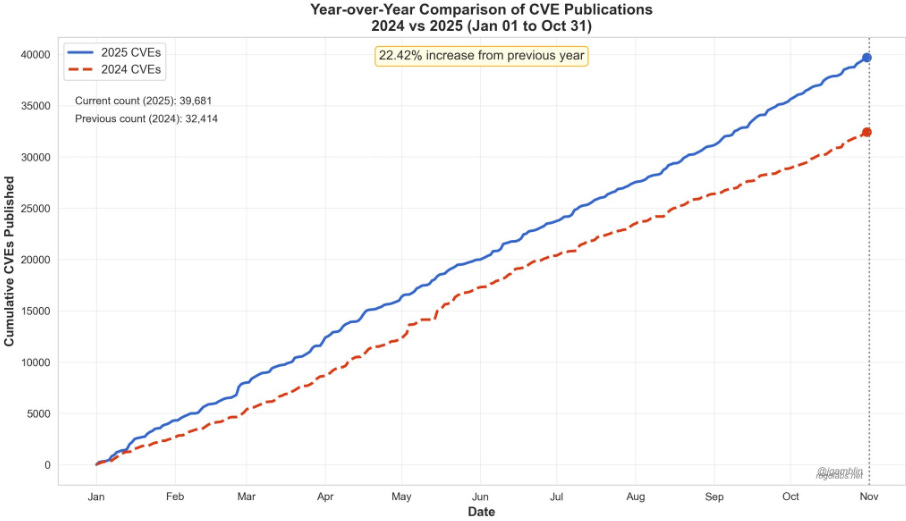
In fact, one of my favorite Vulnerability Researchers, Jerry Gamblin, recently shared an update of CVEs thus far in 2025, and we’re seeing a roughly 23% YoY growth rate overall from 2024 > 2025, with 130 new CVEs per day.
Intruder’s report rightly points out that this means the threat environment is growing increasingly challenging for organizations, and it’s putting more pressure on teams who are already struggling to get ahead, especially among SMBs who often lack the financial and cybersecurity resources to tackle the existing volume of vulnerabilities, let alone a 20%+ increase. Safe to say, most cybersecurity teams, especially those at SMBs, haven’t received 20% more funding or headcount in 2025, and in fact, many are being asked to do more with less.
Vintage Vulnerabilities Are in Vogue
Another excellent point the Intruder report highlights is that vintage vulnerabilities (e.g., “old” CVEs) are in style, and malicious actors are leveraging AI capabilities to weaponize them and create new zero-day exploits.
I previously shared how researchers are using AI and LLMs to create proof-of-concept exploits in as little as 15 minutes, with minimal financial commitment. Malicious actors are also using AI to accelerate their exploit development. Given that organizations have massive vulnerability backlogs, often numbering in the hundreds of thousands to millions, with “old” CVEs that have been published for some time, these stale CVEs represent low-hanging fruit for attackers to target.
Attackers are well aware that organizations, especially SMBs, have remediation capacity that can’t keep pace with the constant wave of new CVEs, so vulnerabilities pile up in backlogs until they get fixed someday, if ever.
Intruder also highlighted the fact that exposed infrastructure, such as VPNs, firewalls, and identity providers, is increasingly becoming enticing targets for attackers, as they often have broad internal access, allowing for potential lateral movement, are Internet-facing, and are usually associated with elevated privileges. If you take a look at CISA’s “Emergency Directives” for 2025, you will find that it is littered with vendors of these products being associated with real-world incidents and attacks.
There ARE improvements
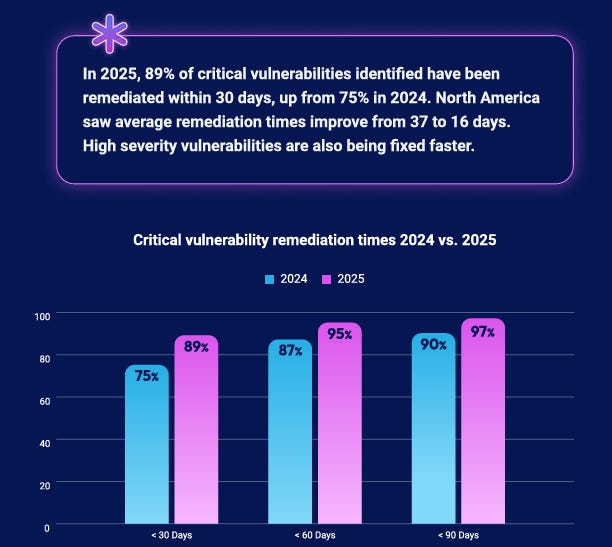
Sometimes in cybersecurity, it can feel defeating, a bit like Sisyphus pushing a rock up a hill, only for it to roll back down again. It is worth highlighting when we do make strides of improvement, and Intruder points that out, showing that in 2025, 89% of critical vulnerabilities were remediated within 30 days, an increase from 75% in 2024.
This shows that cybersecurity may be getting more support internally from executives and leaders, making adherence to SLAs around vulnerability remediation more realistic, as well as teams using technology and automation to accelerate remediation timelines.
One challenge here though may be that when most organizations say “critical”, they mean based on the Common Vulnerability Scoring System (CVSS) base scores, which don’t take into account factors such as known exploitation, exploitation probability, reachability, business criticality and more, which should be used for improved ROI in terms of focusing on remediating real risks rather than noise, especially given < 1% of CVEs in a given year are ever known to be actually exploited in the wild.
In the Absence of Market Forces, Regulation Steps In
A constant issue in cybersecurity is the lack of market incentives for vendors and organizations to prioritize security truly. This often leads to calls for regulation, and some even call the state of cybersecurity a byproduct of a market failure.
While the U.S. is currently undergoing heavy efforts to deregulate, the EU is taking a more different approach, often seen as leading the way in becoming a regulatory superpower (for better or worse). We’ve seen the introduction of frameworks such as DORA, NIS2, and CRA, which have rigorous requirements around cybersecurity and software.
Intruder points out how there are early signs of regulatory impact in Europe, including organizations in the EU having fewer critical vulnerabilities than their U.S. counterparts.
There are also some fascinating aspects that Intruder highlights here. For example, they cite that EU firms experience, on average, 100 fewer critical vulnerabilities than North American firms, but nearly twice as many high-severity issues, which continue to grow.
One must wonder if it is a play on vulnerability severity ratings and categorization, with vendors arbitrarily rating vulnerabilities lower to avoid some of the compliance burden, or if vendors are truly producing products with fewer critical findings for EU customers, albeit many more high-severity findings.
Another aspect that must be truthfully acknowledged is that the EU often has a delay compared to North America when it comes to specific products or versions of products, as they are delayed or withheld from the EU market due to the rigorous compliance requirements, perhaps trading innovation for safety.
Complexity Conundrums
Remember how I mentioned that SMBs often have fewer resources and less cyber expertise than their enterprise counterparts? As it turns out, they still outperform some of their larger, more complex enterprise peers, which may suggest that the complexity of larger organizations leads to less agility and a reduced ability to respond dynamically to remediate vulnerabilities.
This one seems counterintuitive on the surface, until you ask anyone who has worked in large complex enterprise environments, and you realize the challenges of remediation operations (RemOps) in enterprises—from exponentially more communication channels, increased competing interests and priorities, complicated tech stacks, overlapping tool sprawl, and more. Metcalfe’s Law is a perfect example of this.
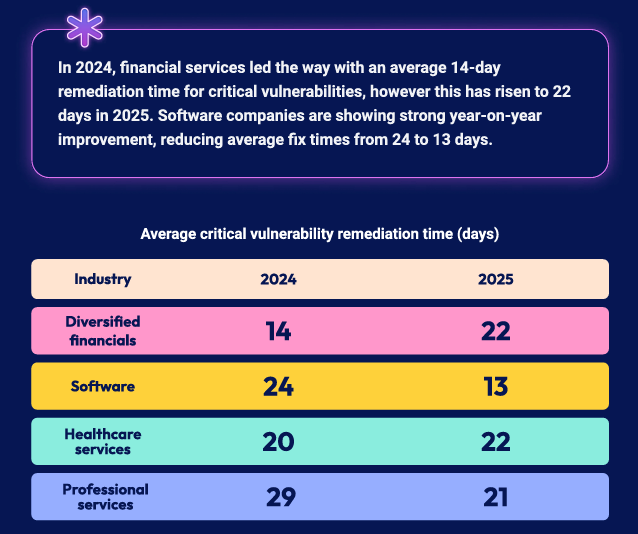
There’s also diversified remediation performance across sectors, with the software industry leading the way, taking 13 days to remediate critical vulnerabilities, while other sectors, such as financial, healthcare, and professional services, trail behind.
Intruder’s report highlights key factors, such as market pressure from buyers who seek security maturity, including compliance certifications, penetration testing, and other measures, as well as mature vulnerability management practices, which are part of their buying process.
Those in the SaaS (Software-as-a-Service) industry have unique architectural advantages that allow for streamlined remediation activities, unlike those with on-premise, hybrid, and legacy infrastructures, which are less well-suited for automation.
Vulnerabilities of the Year
One aspect of the Intruder State of Exposure Management report I found really cool was their focus on what they dubbed as “Vulnerabilities of the Year”. As I mentioned earlier, not all vulnerabilities are equal, and some have a significantly larger impact due to known exploitation, widespread adoption of impacted software or products, and other factors, which makes them more relevant to defenders.
Intruder highlights factors that make vulnerabilities more relevant, such as:
Prevalence across environments
Likelihood of exploitation
Real-world impact
With that said, the top 5 vulnerabilities Intruder’s report highlights are:
ToolShell (CVE-2025-53770)
Palo Alto Auth Bypass (CVE-2025-0108)
Apache mod_rewrite RCE (CVE-2024-38475)
Fortinet Perimeter Vulnerabilities (CVE-2024-55591 & CVE-2025-32756)
Apache Tomcat RCE (CVE-2025-24813)
These vulnerabilities share common themes, including being widely adopted by vendors and open-source solutions (e.g., Microsoft & Apache), as well as Security Vendors (e.g., Fortinet & Palo Alto).
This demonstrates that they are prevalent, given they are products of industry leaders, and have the potential for real-world impact, especially in the context of the security vendors involved, given security products often have characteristics such as elevated privilege, sensitive data and access, and the ability to see and move laterally across environments.
I highlighted these concerns around vulnerable security tools being exploited by malicious actors in an article titled “Your Security Tools May Be Making You Insecure”.
Closing Thoughts
The Intruder’s State of Exposure Management Report provides key insights, especially for SMBs, regarding the prevalence of vulnerabilities, improvements, and deficiencies in remediation operations. It also highlights where and how organizations should leverage their strained resources to focus on the most pressing organizational risks.
These actionable insights aim to help SMBs make more efficient use of their resources and leverage solutions like Intruder, which enable them to evaluate their attack surface and effectively prioritize remediation activities to mitigate risks before they impact organizations.