Resilient Cyber Newsletter #7
Report on U.S. Cyber Posture, American Company Cybersecurity Leadership Crisis, Building a GenAI Platform and Concentrated Global Cyber Risks
Welcome to another issue of the Resilient Cyber Newsletter!
We have a lot of great topics to discuss this week, ranging from Cybersecurity Leadership (or lack thereof), Building GenAI Platforms, Platform Security Engineering Teams and AppSec - so let’s give in.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 6,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cybersecurity Leadership & Market Dynamics
2024 Report on the Cyber Posture of the U.S. 🇺🇸
The Office of the National Cyber Director, The White House recently published the FIRST ever Report on the "Cybersecurity Posture of the United States".
This is a comprehensive report, tying to efforts like the previously published U.S. National Cybersecurity Strategy (NCS) and NCS Implementation Plan (NCSIP). It emphasizes the fundamental transformation that is underway for U.S. Cybersecurity across critical areas.
Key trends such as risks to critical infrastructure, ransomware, supply chain exploitation, commercial spyware and AI
Actions taken by the U.S. Government and partners over the past year across areas identified in the NCS
The Strategic Environment, top trends of 2023 and current efforts underway ranging from the cybersecurity workforce, critical infrastructure, incident preparedness and response and enhancing security and resilience across the globe.
For those paying attention to the big strides and efforts being taken by the U.S. Government the past several years, including the Cyber EO, National Cyber Strategy, push for Secure-by-Design and driving systemic market changes, this is a MUST read 📖
The Cybersecurity Leadership Crisis Dooming America’s Companies
Bob Zukis publishes a damning piece in Forbes criticizing a lack of Cybersecurity leadership among American companies (I would argue this is globally applicable).
Bob argues recent incidents such as Crowdstrike and UnitedHealth highlight both the fragility of America’s digital business systems as well as their lack of security governance, oversight and leadership at the board and executive level.
The case is made that “cyber resiliency can only be built and sustained when there is effective boardroom cybersecurity leadership”. Bob states incidents like Crowdstrike are eye-opening to current business and boardroom leaders because many of them lack expertise in complex digital business systems, despite their organizations reliance on software and technology.
Bob is the founder of the Digital Directors Network (DDN), which focuses on evangelism and education for cybersecurity in the boardroom. They provide a certification called “Qualified Technology Executive (QTE)”, which I’ve obtained, and they also host courses such as one titled “A Cybersecurity Incident Materiality Tabletop”, which I’ve attended.
I largely agree with Bob’s assessment about both the lack of and importance of cybersecurity experience/expertise and involvement at the board level. That said, as I have written about extensively, cybersecurity is also largely a market failure, and without a change in market dynamics and/or regulatory consequences, companies will continue to prioritize competing interests such as speed to market, revenue, market share and more above security, including at the board level.
Boards and CISO’s - Learning from the Crowdstrike Incident
A good read on Medium from Bill Burns discussing what Boards, CISO’s and Security/Technology leaders can learn from the Crowdstrike incident.
The article emphasizes the importance of Premortems, or exercises you carry out before problems occur, to be best prepared. It highlights key activities such as allowing security leaders the opportunity to learn from practice, address systemic risks and acknowledging that all technology fails at some point.
There are specific examples for conducting the premortems as well as links to additional resource, templates and more.
AI
The Periodic Table of AI Security
The team at the OWASP AI Exchange continue to impress, this time producing a concise and excellent table demonstrating various threats to AI and the associated controls to mitigate those threats.
The document is organized by asset, impact and attack surface and also has hyperlinks to the AI Exchange with detailed information about the information and topics.
Below is an example of how the table is laid out.
Building Guardrails for Large Language Models (LLM)’s
The excitement around GenAI and LLM’s continues to grow. Rapid adoption of both commercial and open source solutions and the expansion of potential use cases has taken the industry by storm.
That said, GenAI and LLM’s aren’t without their risks and considerations. This is an incredibly well written and citation rich write up discussing “Building Guardrails for LLM’s”.
It looks at three different open source solutions (e.g. Llama Guard, Nvidia NeMo, and Guardrails AI) and their potential use, applicability and limitations.
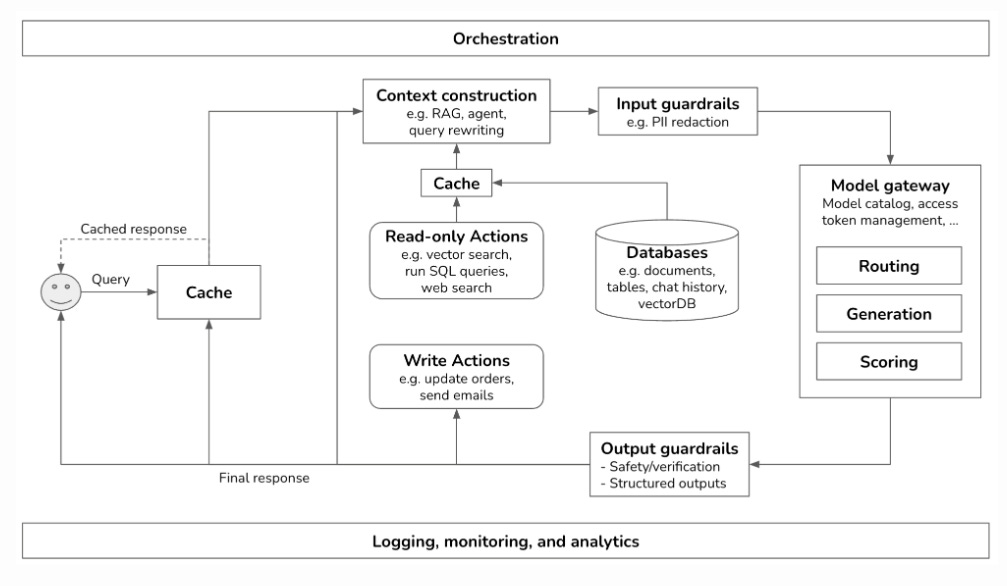
Building a Generative AI (GenAI) Platform
GenAI continues to be one of the hottest aspects of AI, with many organizations standing up GenAI applications and infrastructures. That said, many may not know what the general aspects of a GenAI platform look like under the hood.
This is an excellent article from Chip Huyen, discussing just that.
Chip’s article is incredibly detailed, documenting various aspects of the architecture, how they function and the value they provide to GenAI applications running on top of the platforms.
The topics range from enhancing context, putting in guardrails, reducing latency and AI pipeline orchestration.
Very detailed and well-written piece that is insightful for security practitioners looking to gain an understanding of the nuts and bolts of GenAI platforms and their functionality.
With Open Source AI, Don’t Forget the Lessons of Open Source Software (OSS)
We now see a lot of excitement about the advancement of AI, including the open source community, and on platforms like HuggingFace. This is a good blog from the folks at CISA discussing how when we discuss open source AI (which is term drawing debates, in terms of what actually qualifies as OSS, since there are models, weights, training data etc.) to not forget our lessons of securing OSS.
CISA discusses some of the longstanding aspects of open source and how open source AI can learn those lessons, and also lean into some resources and efforts from CISA.
These include the Principles for Package Repository Security framework as well as making artifacts traceable (e.g. provenance) and also ensuring model development includes diverse viewpoints.
Application Security, Software Supply Chain and Vulnerability Management
JFrog Security Research Discovers and Reports a Potentially MASSIVE Supply Chain Attack
The JFrog Security Research team published a blog discussing how they identified a GitHub token in a public Docker Hub repository that provided access to the entire Python infrastructure.
This could of been used to inject malicious python packages, compromising the entire Python ecosystem. JFrog reports this to the PyPI security team and the token was revoked in less than 20 minutes, which is a testament to the responsiveness of the PyPI security team as well.
The report lays out how this could of went drastically differently, leading to tens of millions of machines compromised worldwide if it had been discovered by a malicious actor and could of impact all of the Python, PyPI, and Python Software Foundation repositories and millions around the world who rely on them.
They point out that the token was only found in the Binary, within a Docker container in a compiled Python file, and the matching source code didn’t contain the same token, due to the process the Developer followed.
This demonstrates the need to scan for secrets in not just source code, but also compiled binaries.
It also of course demonstrates that old-style GitHub tokens as they call them need to be replaced with modern GitHub Privileged Access Tokens (PAT)’s after 2021 due to changes made by the GitHub team and the addition of checksums.
Lastly, they stress that tokens should only provide access to the resources required by the application using them, which we know is the concept of least-permissive access control, a longstanding security best practice but applied to access tokens in this case.
This is an example of what could of been a massive software supply chain attack had it not beed identified and remediated.
Who know what other similar tokens may be floating around the ecosystem, already exploited, or yet to be discovered.
What is an Open Source Program Office (OSPO) and How to Start One?
There has been a lot of interest lately in OSPO’s, to help enable governance and improved security around the consumption and use of open source. This includes OSPO’s being cited in The Federal Governments FY26 Cybersecurity budget priorities, where agencies are directed to begin to pursue standing up OSPO’s as part of software supply chain efforts.
I had a chance to facilitate a talk by Russ Eling of OSS Consultants as part of Endor Labs LeanAppSec. Russ has a wealth of background on standing up and running OSPO’s at-scale, and put on a great talk about how others can do the same.
Security Platform Engineering
We've seen the rise of Platform Engineering. These platforms have specific security needs, often looking to systemically address security issues for the enterprise in a standardized way.
I've been fortunate enough to be a part of a few Platform (PaaS) teams across the DoD and Federal landscape (often called Software Factories), with my focus being security each time.
For those focused on the U.S. Federal space, there is a “Federal Platform Engineering Community of Practice (CoP)”.
This is a great article from Kane Narraway discussing:
What are security platform engineering teams?
What do they work on?
How do you develop this function?
When should you staff a team?
This is such an excellent topic, and there is a lot of nuance to it.
Knowing what to build vs. buy, what problems need to be addressed at-scale, easing toil and burden for developers building on the platform, addressing organizational governance and compliance requirements and more.
Securing Cloud Infrastructure, IaC, Misconfigurations and Guardrails
We continue to see cloud misconfigurations as a leading cause of cloud data breaches. The complexity of modern cloud environments with the hundreds of services, countless potential configurations, ability to expose sensitive data and access and more.
I had a chance to interview Travis McPeak on the Resilient Cyber Show and dive into this topic. Travis helped grow and scale Netflix’s cloud infrastructure and is now the founder of Resourcely, where they focus on enabling secure cloud environments with guardrails and blueprints.
This is a great talk to learn more about the complexities of cloud infrastructure and ways to optimize securing them.
A Case for Modern SOC’s versus Consolidation
Platforms vs. Best of Breed Products continue to be a hot topic in the industry, across many different niches, including the SOC. This is a great comprehensive article from my friend Francis Odum at The Software Analyst Newsletter, which does into the topic.
It discusses while there are valid needs for consolidation in areas of cyber such as SASE, IDAM etc. the SOC has some unique considerations.
Francis lays out the pros and cons of a consolidated SOC vs Best-of-Breed SOC, weighing factors such as the modern security architecture, risks, thread landscape, push for a data-centric security paradigm and more.
Even if you don’t work in the SOC space, this is a great read to better understand the modern challenges of security operations, and some of the approaches, whether it is large industry leading platforms or innovative disruptors and the unique capabilities they provide.
3 Key API Security Risks and Mitigations
API Security remains a hot topic and is only growing as trends like cloud adoption, microservices and more continue.
This is a good article from Carnegie Mellon’s Software Engineering Institute (SEI) discussing 3 key API security risks and their associated mitigations.
The article discusses how API’s are built, through the use of API Endpoints and Microservice Architectures. It then goes on to discuss the three key risks they call out, which are:
Third-Party Software Integrations
Cascading Failures
Increased Network Surface
This is a solid read unpacking the complexities of building and working with API’s and laying out some of the risks associated with their use.
Department of the Air Force (DAF) API Reference Architecture
On the topic of API’s, the DAF released their API Reference Architecture.
This is an insightful read for those supporting the DoD and USAF, as well as those looking to see how the DoD is approaching API’s as an enabler for a digital military force. It discusses the DAF’s API-first approach and the need to help facilitate DAF digital operations within the USAF, with industry and with international partners.
It was published by USAF CTO Jay Bonci, who is incredibly sharp and technical.
The publication lays out seven key principles, assumptions as well as the desired outcome for warfighters.
Concentrated Global Cyber Risks
In the wake of the Crowdstrike incident I have been seeing a lot of great resources about concentrated cyber risks and monocultures (e.g. dominance by single or small groups of vendors).
One report I came across was from SecurityScorecard, ironically preceding this incident but very timely, it is titled “Redefining Resilience: Concentrated Cyber Risk in a Global Economy”.
One glaring takeaway from the recent Crowdstrike incident is just how severe our cybersecurity risk concentrations are.
In a world where vendor leaders are seeking market share, dominance and "platformization" - there's a correlation to dependencies and systemic risks for consumers and society.
I've been digging into an excellent report from SecurityScorecard titled "Redefining Resilience: Concentrated Cyber Risk in a Global Economy" and the findings are alarming.
150 companies account for 90% of the technology products and services across the global attack surface 🌍
41% of those companies had evidence of at least one compromised device in the past year
Insanely, just 15 companies account of 62% of ALL products and services 🤯
The report is rich is additional data, such as the cost to remediate third-party breaches being 40% higher than internal cybersecurity breaches and 75% of third-party breaches targeting software and technology supply chain vendors.
As we see tightening security budgets and a push for "tool consolidation", these dependencies, single points of failure, lack of resilience and systemic risks will only be exacerbated.
Monocultures and resilience don't go hand in hand ❌
I published a much more comprehensive article on this topic this week titled “Systemic Concentrated Cyber Risks: Discussing Monocultures, Systemic Dependencies and Digital Fragility” for those who want to really examine the topic in-depth.
More Data Created in the last 3 years than ALL of history
As we look at the push for new security paradigms with data-centric security models, this report from Blackstone insightful. They reported that there has been explosive data growth, with more data being created in the last 3 years than in ALL of history combined. This seems to be underpinned by trends such a social media, cloud, streaming and now AI, which is only going to accelerate things.
We’re also of course seeing similar trends in the acceleration of code with AI-driven software development and Co-Pilots. That said, what remains to be seen is if that code will actually be sure, or will have inherent vulnerabilities, drastically expanding the attack surface.
I covered this in an article titled “Snyk Report on AI Code Generation Exposes Risks, Developers’ False Sense of Security” where I discuss how AI-generated code is still rife with vulnerabilities, and also leads to a false sense of security among developers, inherently trusting the code it generates without scanning or reviewing its security posture.
We know Developers are primarily incentivized and judged based on productivity, so this trend shows no signs of slowing down either.
Federal Government Releases FedRAMP Modernization Guidance
The Office of Management and Budget (OMB) released a memo detailing the path to modernizing the FedRAMP program.
For those unfamiliar, the FedRAMP program is used to assess and authorize Cloud Service Providers (CSP)’s and their associated offerings and services for use among Federal agencies.
The memo now supersedes the original memo that established FedRAMP and helps lay out a new vision, scope and governance structure for the widely used program.
The memo also lays out several strategic goals and responsibilities, including:
Rapidly increasing the size of the FedRAMP Marketplace by evolving and offering additional FedRAMp authorization paths
Streamlining the process through automation
It also lays the groundwork to accelerate the process by aspects such as presuming adequacy of authorizations granted by one agency, so others don’t have to do re-work and looking to enable reciprocity with other existing industry compliance frameworks.
Overall this is a positive and promising future for FedRAMP, but as with anything with Government, we will have to wait and see the actual effectiveness of execution on this vision.
A Visual Exploration of Exploitation in the Wild (Inaugural Study of EPSS Data and Performance)
Cyentia and FIRST recently published their inaugural study of EPSS Data and Performance, titled “A Visual Exploitation of Exploitation in the Wild”.
For those unfamiliar with EPSS, it is a probabilistic scoring system used to predict how likely a given CVE/vulnerability is to be exploited in the next 30 days. It’s a great resource to help organization prioritize vulnerabilities likely to be exploited, rather than trying to address all vulnerabilities, because there are simply too many.
I have covered it in previous articles such as:
This report from Cyentia/FIRST is a wealth of insights into the state of vulnerability management, including:
The growth of vulnerabilities being discovered and published, as well as exploited
Exploitation activity over time
Exploitation patterns
How EPSS performs compared to CVSS, KEV and other approaches
As the authors note, EPSS isn’t perfect, and will never be 100% accurate, neither will any other vulnerability prioritization scheme. That said, it is a critical resource that should be used in any modern vulnerability management program and is something I’ve written extensively about in my book “Effective Vulnerability Management”
I highly recommend giving this EPSS study a read, and I will very likely be publishing an article discussing its findings in the near future.
Below are some great visualizations from the study.