Resilient Cyber Newsletter #58
PANW Acquires CyberArk, Cyber Acquisition Rumors/Trends, CISO’s in the Corner on AI, MCP’s Security Layer, GenAI Incident Response Guide & Software Under Siege
Welcome
Welcome to issue #58 of the Resilient Cyber Newsletter.
We’re in peak summer and heading into Hacker Summer Camp (e.g., Black Hat), and things are crazy.
From M&A trends and activities to big moves from the White House on AI, there are a ton of resources around Agentic AI and Cyber and AppSec reports with key insights from security teams and leaders.
So, without wasting more time, let’s get down to business!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 45,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Legacy DAM is a headache. It's time to get some relief.
For years, database activity monitoring (DAM) has been an obligation driven by checking a box rather than driving outcomes or simplifying compliance.
That's because legacy DAM solutions were built for a different era — when deploying hundreds of agents and monitoring databases in isolation was considered acceptable. The AI era demands a new approach to data security.
Varonis Next-Gen DAM secures thousands of cloud, on-prem, structured, and unstructured databases with agentless monitoring that's easy to deploy and scale. As a part of the Varonis Data Security Platform, database security is no longer the domain of DBAs and a blind spot for security teams. Instead, they have a single pane of glass view into their data — wherever it lives.
Get some DAM relief with Varonis.
Cyber Leadership & Market Dynamics
Palo Alto Set to Acquire CyberArk for $25 Billion
In news that is racing through the cyber ecosystem, Palo Alto Networks (PANW) has entered into an agreement to acquire CyberArk, a leader in IAM. This move enables PANW’s platform strategy and helps them move into the Identity Security space with it as a core capability.
This move also signals PANW’s intent to play in the Agentic AI identity security space, where agents are poised and non-human identities are poised to outpace human users, exacerbating existing identity security challenges significantly.
There will inevitably more to come on this and deep industry analysis, so stay tuned for those resources as they get published.
The Case For and Against PANW Acquiring SentinelOne
Speaking of PANW acquisitions, it is also being speculated that PANW is exploring acquiring SentinelOne. In typical fashion, my friend Cole Grolmus of Strategy of Security is on top of it, with an article discussing both the case FOR and AGAINST this move by PANW.
I won’t go deep on this one, given the CyberArk news it remains to be seen if PANW makes this move, but if you’re curious the implications be sure to give this piece a read.
Security is Splitting: Three Acquisitions, Three Different Realities
Apparently M&A season is in full swing, as Frank Wang tackles three potential acquisitions in a recent piece as well, discussing how each one is unique and signals different things to the market.
Frank discusses the three acquisitions below:
Cursor > Resourcely
PANW > SentinelOne (Rumored, per the article I shared above)
DataDog > Upwind (Rumored)
Each move has different motivations and signals. Cursor acquiring Resourcely demonstrates the move of building security directly into DevEx and Dev workflows. PANW, of course, is their desire to expand their platform play. DataDog and Upwind, again, are platform pushes but also align with the broader industry trend of moving towards Runtime security and trends such as Cloud Detection/Application Detection and Response (ADR).
Prophet Security Announces Its $30M Series A
Kamal Shah and the Prophet Security team recently shared that they have finalized their $30M Series A financing, with the round led by Accel and Bain Capital Ventures, among others.
The team is driving towards an Agentic AI SOC Platform and looking to address longstanding SOC challenges, such as:
Slashing investigation times
Reducing alert fatigue
Allowing analysts to focus on strategic work versus toil
They represent one of the promising disrupting firms leaning into AI and Agents, and their potential to revolutionize the SecOps space.
I actually had Grant Oviatt from the Prophet Security team on in the past, who discussed transforming SecOps with AI SOC Analysts, and you can check out that full conversation below:
U.S. Navy Goes All-in on Containers
The Department of Navy CIO (DON CIO) recently released a memo titled “Containerization Technology Usage” which aims to drive adoption and use of containers across the Navy.
It specifically states:
“POLICY: Effective Immediately, all software development activities transitioning to the cloud and/or upgrades that are hosted in a cloud as outlined above must utilize containerization technology to the greatest extent practical".
This is a big opportunity when it comes to cybersecurity companies focused on securing container-based technologies and workloads.
AI
Winning the AI Race 🚀 - America’s AI Action Plan
Last week The White House unveiled the U.S. AI Action Plan. It's aimed at ensuring U.S. dominance in the race around AI. It is a great example of the intersection of technology, cybersecurity, AI, and geopolitics.
I spent some time this weekend delving into the plan and analyzing its major implications, both technologically and politically.
This includes the race for AI dominance, largely between China and the U.S.
Nuances around commercial and open source models, energy demands, and workforce implications
Venture capital, investments, startups, and resource allocation
AI's intersection with Cybersecurity, both from a governance and regulatory perspective, as well as the dual-edged nature of AI, both needing to be secured and having promising potential to address systemic cybersecurity challenges, both offensively and defensively.
Software and technology increasingly underpin everything from critical infrastructure, consumer goods, geopolitics, and national security
Shadow AI, Scope Creep, and the CISO in the Corner
We continue to see rampant AI adoption across enterprise environments, and like previous technological waves before it, Cyber is challenged with keeping pace, being viewed as an enabler rather than a blocker to the business and simply governing the consumption and use of new technologies, products, and services.
This piece from Saanya Ojha serves as a field report from CISOs on the state of enterprise AI adoption and the challenges CISOs face.
In the article, she frames CISOs as the “adult chaperones at the no-holds-barred enterprise AI party”. She lays out three key things for security leaders to do or keep in mind:
Governance must assume AI is already in use
Scope creep is inevitable; plan for it
Experimentation is the goal, not the threat
AI amplifies old risks more than it invents new ones
Policies are only as good as their enforcement
She highlights that AI governance isn’t a new discipline but is much faster, messier, and has higher stakes than previous challenges. Therefore, ensuring the security fundamentals are more important than ever to enable secure enterprise AI adoption.
We Built the Security Layer MCP Always Needed
The Model Context Protocol (MCP) continues to generate excitement, as it helps give LLMs arms and legs, supports semi- or fully autonomous workflows, facilitates tool integrations, and more.
That said, various folks have raised issues with the MCP specification around IAM and ways to abuse MCP, such as embedding prompt injections in the MCP tool descriptions. Attacks include data exfiltration and code execution, among others.
That’s why this open-source tool from Trail of Bits (in beta release) is so awesome. “mcp-context-protector” functions as a security wrapper for LLM apps using MCP.
The tool sits between LLMs and downstream servers and can perform security checks on messages before they enter an LLMs context window. The key security features the team highlights as part of the mcp-context-protector tool include:
Trust-on-first-use server pinning
LLM guardrail scanning of tool responses
Sanitizing ANSI control sequences
The LLM Guardrail allows for integration with other toolkits such as LLamaFirewall from Meta, or NeMo Guardrails from NVIDIA. Then if unsafe content or prompt injections are detected, responses get placed into a quarantine:
That said, they also admit to some challenges, such as the need for manual configuration review and alert fatigue associated with reviewing quarantined alerts that the tool may flag.
GenAI Incident Response Guide 📕
The recent U.S. AI Action Plan published by The White House called for updating incident response plans and measures to account for AI-related threats. And, in typical OWASP GenAI Security Project fashion, the crew just dropped OWASP® Foundation's "GenAI Incident Response Guide 1.0"
It's a comprehensive guide, covering:
Defining AI incidents, including real-world examples, and distinguishing between AI and Cyber incidents
Preparing for AI Incident Response, including Risk Assessment and Management, AI system inventory, detecting and reporting AI incidents, and responding
Event-specific guidance, such as attacks on AI systems, supply chains, and third-party model providers
This is a great resource for organizations looking to modernize their IR plans and processes to account for emerging AI threats and risks.
Resilient Cyber w/ Christian Posta MCP, Agents & IAM in the age of LLMs
In this episode, we sit down with Christian Posta, the Field CTO at Solo.io and an industry author and leader on topics such as Microservices, AI, and IAM.
We will explore the rise of Agentic AI and its supporting protocols, such as MCP and A2A, and the broader challenges and considerations of Identity security in the age of LLMs.
We discussed:
The topic of Agentic Identity and the rise of protocols such as MCP
The original MCP specification, gaps it had and why they were concerning
Despite improvements to the MCP spec, continued challenges and risks for organizations to consider
How the widespread adoption of Agents and Agentic Workflows and their associated protocols will change the attack landscape
AppSec, Vulnerability Management, and Supply Chain Security
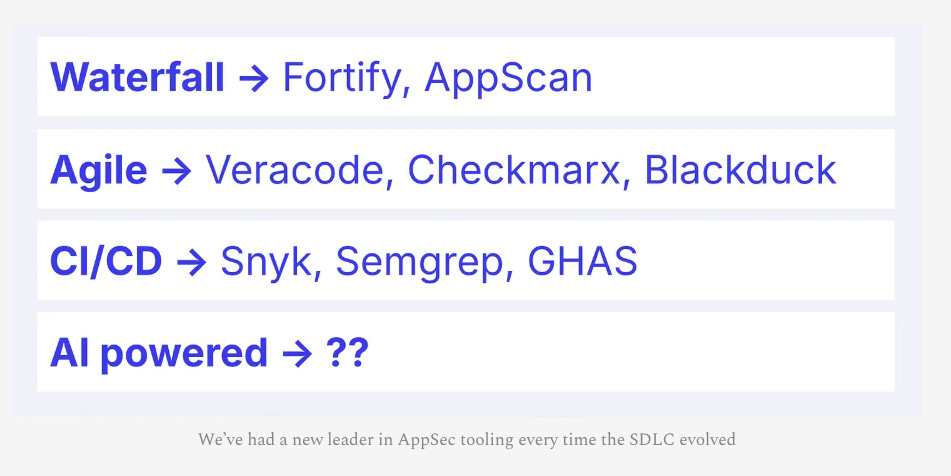
The SDLC is Changing and So Will AppSec (Again)
We know that we’re seeing AI-driven development fundamentally reshape software development, from coding agents, copilots, LLM’s and more. These changes inevitably will have downstream ramifications for AppSec.
Sandesh Mysore Anand of Boring AppSec makes that case in a recent article.
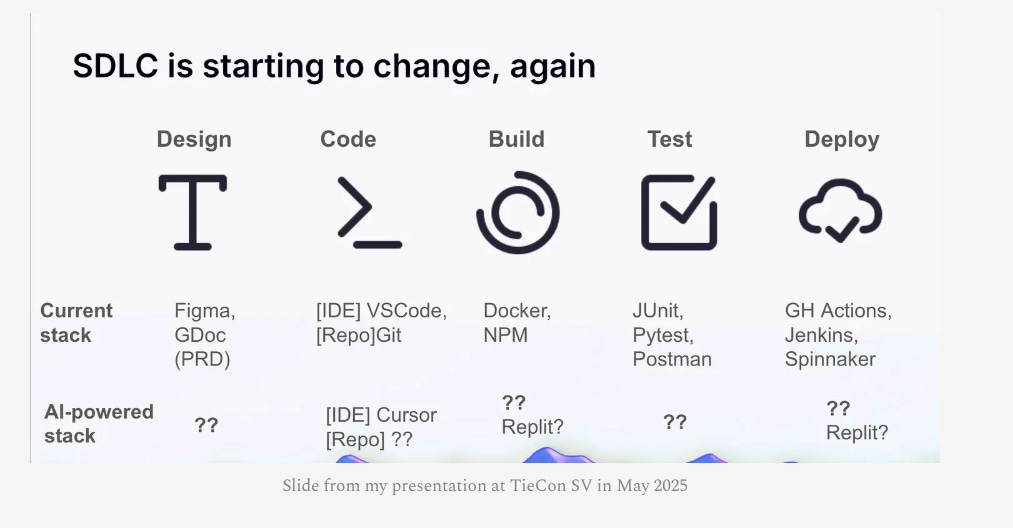
As he discusses, each aspect of the SDLC is changing from Design through Deployment, with new AI-powered technology stacks coming into play. Sandesh gave a topic focused on this at TiE Silicon Valley:
Sandesh doesn’t pretend to have all of the answers of what AppSec looks like in the future, but says these two questions must be answered:
How should we manage prompts?
What should automated code and prompt review look like?
Each of these questions come with their own nuances and considerations as well. Such as how prompts get stored and versioned, or what a testing cadence for prompts looks like.
This is a thought provoking piece for the changes to AppSec as part of the changes to upstream software development with AI-driven development taking major hold across the industry.
Software Under Seige 2025
What are the blind spots in software security? This is a good report from the Contrast Security team diving into those exact topics. It covers topics relevant for security teams and CISO’s, such as
Attack Volume and Breakdowns
The Growth of Software Vulnerabilities
Disadvantages of Defenders due to the increasing speed of attackers compared to organizations ability to patch
The report discusses how AI-driven development is only exacerbating existing AppSec challenges, and the average application is exposed to 81 confirmed viable attacks monthly, and over 10,000 probes/attack attempts that don’t succeed. This is all while the average number of vulnerabilities continues to grow per application.
The report emphasizes the importance of runtime data, and aligns with the broader industry shift towards Application Detection and Response (ADR), especially among many growing frustrated with how poorly DevSecOps has been implemented and the toil it has caused Developers.
There’s a lot of great insights in this report, and I plan to give it a deeper review and possibly a write up soon.