Resilient Cyber Newsletter #43
CVE Near Collapse, Cyber Market Failures, The Rise of the Agentic Ecosystem (MCP/A2A) & Chinese Attribution for Critical Infrastructure Cyber Attacks
Welcome!
Welcome to another issue of the Resilient Cyber Newsletter.
It would be an understatement to say it has been a chaotic whirlwind of a week in cybersecurity. We have a lot to cover, from the near meltdown of the industry-wide Common Vulnerabilities and Exposures (CVE) program to multiple interviews with industry AppSec leaders, to the continued evolution of Agentic AI with MCP and A2A.
So, here we go!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 45,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Stop Cloud Breaches Before They Start—Get the CDR Buyer’s Guide.
As cloud adoption skyrockets, so do the risks. In fact, cloud attacks jumped 66% in just one year and legacy tools aren’t cutting it anymore.
That’s why the Cloud Detection and Response Buyer’s Guide is your essential roadmap to securing the modern cloud.
✅Protect cloud applications and workloads with industry-leading runtime protection
✅Detect known and unknown threats in real time
✅Automate response with out of the box playbooksExplore how Cortex Cloud Detection and Response (CDR) can help your team stop breaches before they happen.
Cyber Leadership & Market Dynamics
Cybersecurity is a Market Failure 📉
At least, that is the stance of many in the industry, who cite various examples of how. This is a great article by Jason Healey, Carina K., and Christine McNeill titled "Understanding Cyber Market Failures."
In the piece, they discuss:
- Information Asymmetry and Inadequacies
- Negative Externalities
- Market Power
- Public Goods
They break down each example of a cyber market failure and potential mitigations, some of which are in place, being proposed, or may be considered. This ties in with topics such as software liability and more, which was part of the recent U.S. National Cyber Strategy under the previous presidential administration.
The Intersection of Cyber and AI for Economic/Budget Resilience
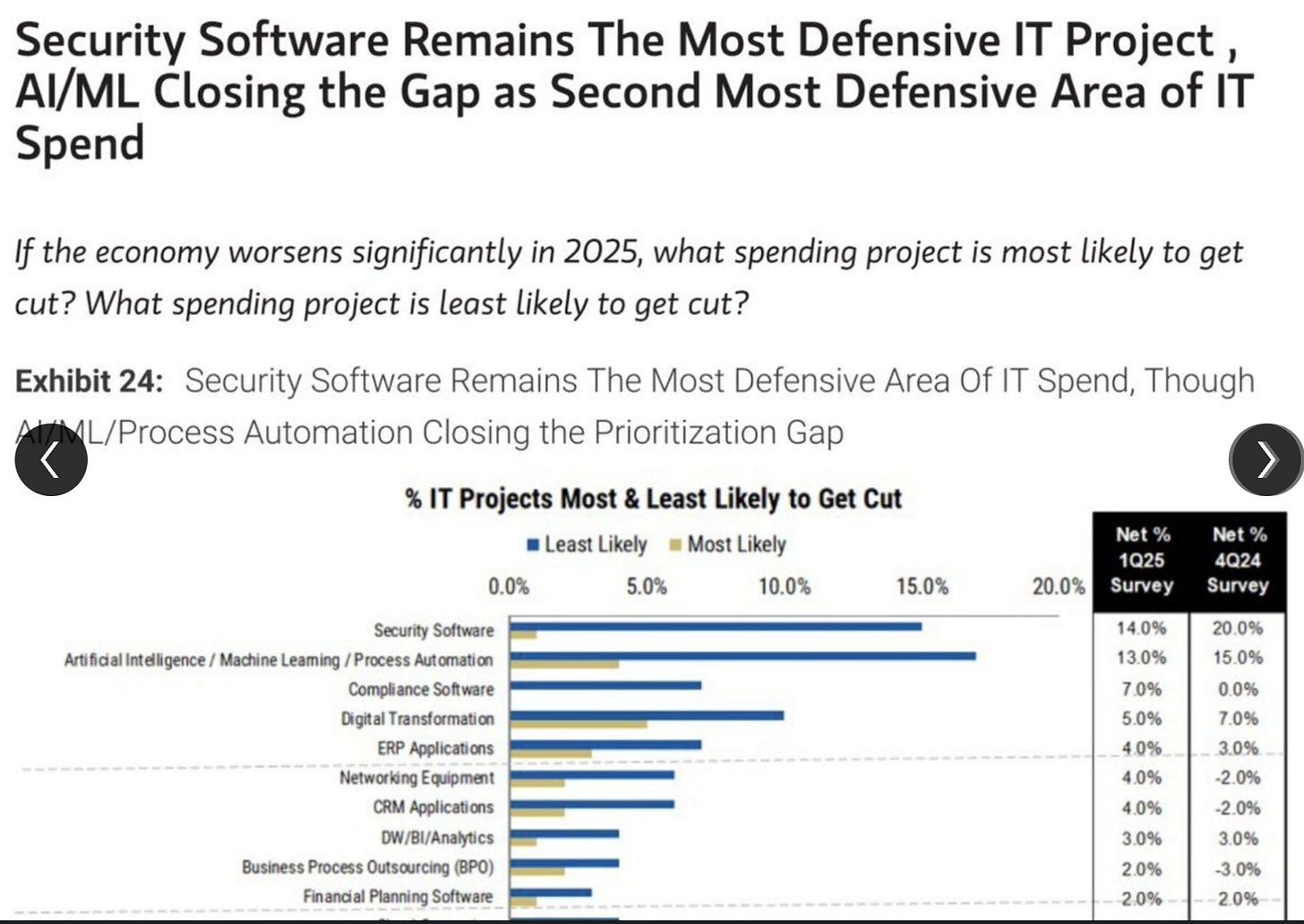
This includes, in the economic sense, when we look at potential spending cuts or projected spending. This data from Morgan Stanley's Q1 25 CIO survey shows that Security and AI are the least likely to be cut among IT projects if the economy worsens.
We also see that they account for the largest projected increase in spending. This is a signal if you're a vendor, startup, or investor. If you're a practitioner, this applies to the workforce, tooling, and organizational budgets.
This can be helpful when trying to figure out where to build as a founder or where to focus your skills and competence as a practitioner. Of course, this doesn't mean AI and Security are invincible, but they do remain resilient in the budgetary sense.
Trump Directs Pentagon to Tee Up Major Acquisition Reform
President Trump signed an Executive Order last week focused on reforming defense procurement, reviewing major defense acquisition programs, and boosting the procurement of commercial technologies, in addition to workforce changes.
Key focus areas include:
Reforming DoD acquisition processes by utilizing existing authorities to expedite acquisition
Acquisition workforce reform
Reviewing internal regulations and removing aspects that impose a burden with a focus on streamlined acquisitions
Reviewing major defense acquisition programs, including potentially canceling programs 15 behind schedule or over cost
Speaking of the EO, Shyam Sankar published a brief blog discussing it. I happened to catch a recent podcast he was on with Shawn Ryan diving into the broader Defense and Software/Technology ecosystem, its intersection with venture capital, national security, and more.
Sen. Wyden Holds Up Trump’s CISA Nominee - Citing Telecom “Cover Up”
Last year, one of, if not the largest, incidents was a massive nation-state-sponsored attack that hit the leading U.S. Telecom providers. DHS/CISA was allegedly conducting an investigation into the attack via the Cyber Safety Review Board (CSRB); however, that effort seems to have been put on hold.
Given that, Sen. Wyden recently announced he plans to hold up President Trump’s CISA nomination unless CISA releases a report on the insecurity of the U.S. telecommunications industry dating back to 2022. If claims are true, it is really disappointing that it takes these types of antics to get transparency to the American people on the security (or lack thereof) of their critical infrastructure.
The most damning aspect, if true in my opinion, is that the obstruction of transparency around cyber is coming from the nations leading Cyber agency (including under the previous President).
In Secret Meeting, China Acknowledged Role in U.S. Infrastructure Hacks
Speaking of critical infrastructure incidents, it was recently reported that in a secret meeting in December, Chinese officials acknowledged their role in a widespread series of alarming attacks on U.S. critical infrastructure.
This included U.S. ports, water utilities, airports, and other targets as part of tensions over U.S. support for Taiwan. This public attribution and acknowledgment is something pretty uncommon among competing nation-states. Apparently, the comments were “indirect and somewhat ambiguous.” Still, it made it clear to the U.S. officials in the conversations that it was both an admission and a warning to the U.S. over Taiwan.
Given cuts occurring across agencies, including CISA, and rising tensions between the U.S. and China, specifically around tariffs, it will be interesting and concerning to see if these cyberattacks against U.S. critical infrastructure continue. This is especially concerning since the majority of critical infrastructure in the U.S. has openly admitted that they haven’t met Cyber Performance Goals (CPG), as stated by CISA.
AI
The Rise of the Agent Ecosystem 🤖
On the heels of the buzz around the Model Context Protocol (MCP), Google announced Agent2Agent. This is focused on multi-agent architectures and 4 key areas:
🔷 Secure Collaboration
🔷 Task and State Management
🔷 User Experience Negotiation
🔷 Capability Discovery
But how do MCP and A2A potentially work together in these agentic environments?
This visualization from Aurimas Griciūnas did a great job of helping explain that. While A2A works among agents on the four focus areas mentioned above, MCP helps facilitate interaction with external data sources, tools, services, and more via APIs that MCP servers connect to.
It will be interesting to see how these environments evolve and how security approaches these complexities.
MCP vs. A2A: Friends or Foes
Speaking of Aurimas, he published a more comprehensive article discussing MCP and A2A and how they may complement or compete with one another. In the piece, he discusses:
What is A2A?
What is MCP?
How is A2A Complimentary to MCP and Vice Versa?
Could A2A Eat up MCP Long Term?
As he explains, the rise of open protocols such as MCP and A2A addresses some fundamental gaps in the evolving agent ecosystem, such as a lack of system state transfer and disconnected agents not sharing tools, context, and memory.
A2A as described, is:
“an open protocol that provides a standard way for agents to collaborate with each other, regardless of the underlying framework or vendor”.
Google’s announcement defines both a “client” and a “remote” agent. The client creates tasks and communicates them to the “remote” agent to perform work and return results and data. I defined the four primary capabilities of A2A in the section above with the visualization from Aurimas.
As the article explains, A2A builds on existing standards and protocols, such as HTTP, SSE, and JSON RPC, making it highly interoperable with existing architectures and IT environments rather than requiring a new set of requirements or protocols. One of the biggest appeals is that A2A is parity with OpenAI’s authentication schemes to provide robust authentication and authorization, where MCP has faced criticism in this area.
If you haven’t subscribed to Aurimas Griciūnas’s newsletter, I definitely recommend doing so, as it is full of great information about AI, and he helps easily explain complex topics.
The MCP Authorization Spec Is…a Mess for Enterprise
Spending a good bit of time the last week or so learning about MCP and security challenges from people far smarter than myself. This one is from Christian Posta, in a really excellent piece diving deep into the Model Context Protocol (MCP), specifically authorization.
These concerns are critical as we look to have pervasive agents and agentic architectures across enterprises, likely exponentially outnumbering human users. Christian provides a masterclass on OAuth and its intersection with MCP to facilitate secure authorization.
We already know that authorization, access control, and credential compromise are among the leading sources of security incidents. These problems are likely to get exacerbated by agents, along with other risks and vulnerabilities.
Securing the Model Context Protocol (MCP)
Building on the theme of A2A and MCP and their secure use, I found this article from Alex Rosenzweig of Block to be super informative. He laid out how the team at Block is building on MCP securely and their lessons learned.
Alex emphasizes two key considerations when securing MCP are:
How does the agent talk to the MCP server
How does the MCP server act as a client for the system it connects to?
Alex discusses some parallels with APIs and Agents, but the paradigm shift due to LLMs potentially performing in ways that human users wouldn’t. Alex also discusses the need to address Agent, Human and Device identity, and the ability to determine the primary identity abstraction, the agent’s identity and the device/location the agent is running from.
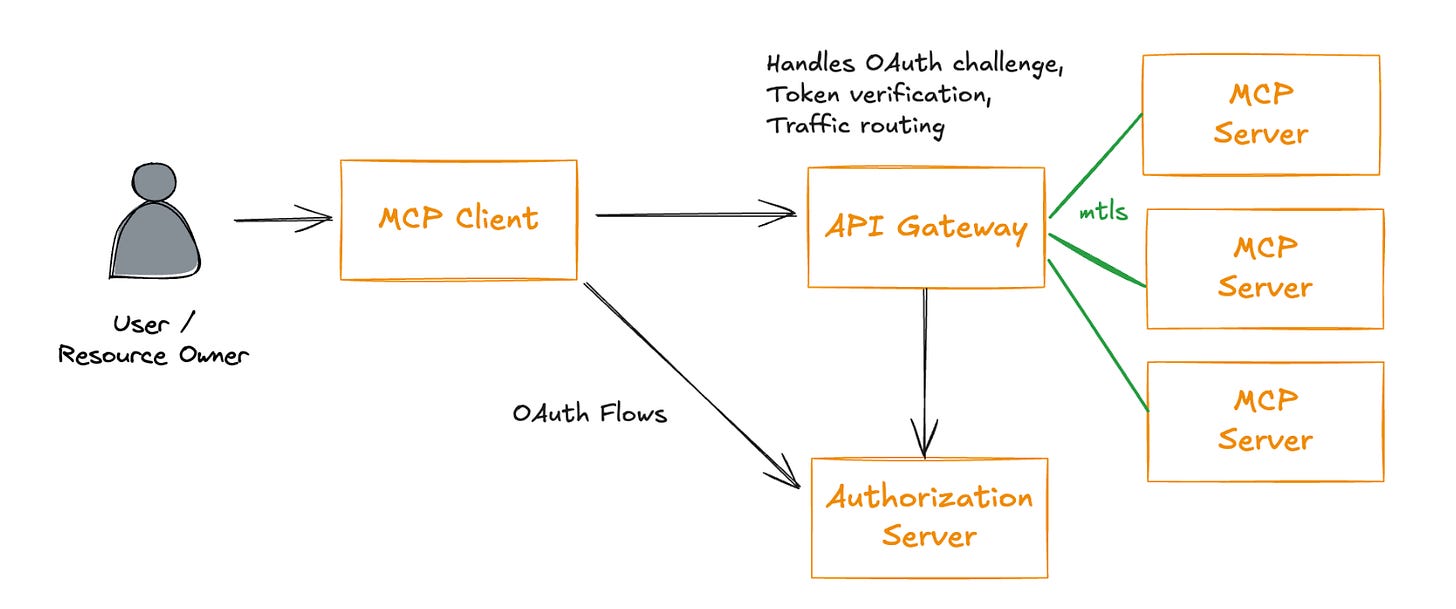
Much like it has been discussed in other articles I am sharing this week, Alex discusses that potential OAuth process for MCP, as below:
A couple of other key topics Alex covers is the need for human-in-the-loop for operational safety, depending on the task, such as writing IaC that is being deployed to production. Alex closes out his article discussing the MCP supply chain and three key tips that we already should be following from other spaces, such as open source:
Only install MCPs from trusted sources that are well maintained
Implement integrity checks and/or signing of artifacts where possible to ensure you’re executing the expected code
Implement allow lists on enterprise agents to ensure users only use pre-validated MCPs
Enterprise-Grade Security for MCP
The Model Context Protocol (MCP) is taking off rapidly 🚀.
Organizations across many industries are now exploring its use for agentic architectures and workflows. That said, rapid technological adoption without security as a key consideration is a recipe for disaster, as we know from past lessons learned. That's why it is awesome to see so many great articles, research and efforts around securing MCP already.
The latest example is a paper titled "Enterprise-Grade Security for the Model Context Protocol: Frameworks and Mitigation Strategies" by Idan Habler, PhD, and Vineeth Sai Narajala
The paper:
Discusses MCP at a high level as well as the security threat landscape for MCP
Unpack key security challenges, such as tool poisoning, data exfiltration, command and control (C2), and update mechanism compromise, among other examples
Proposes a comprehensive MCP security framework with mitigations and methodologies to secure the use of MCP
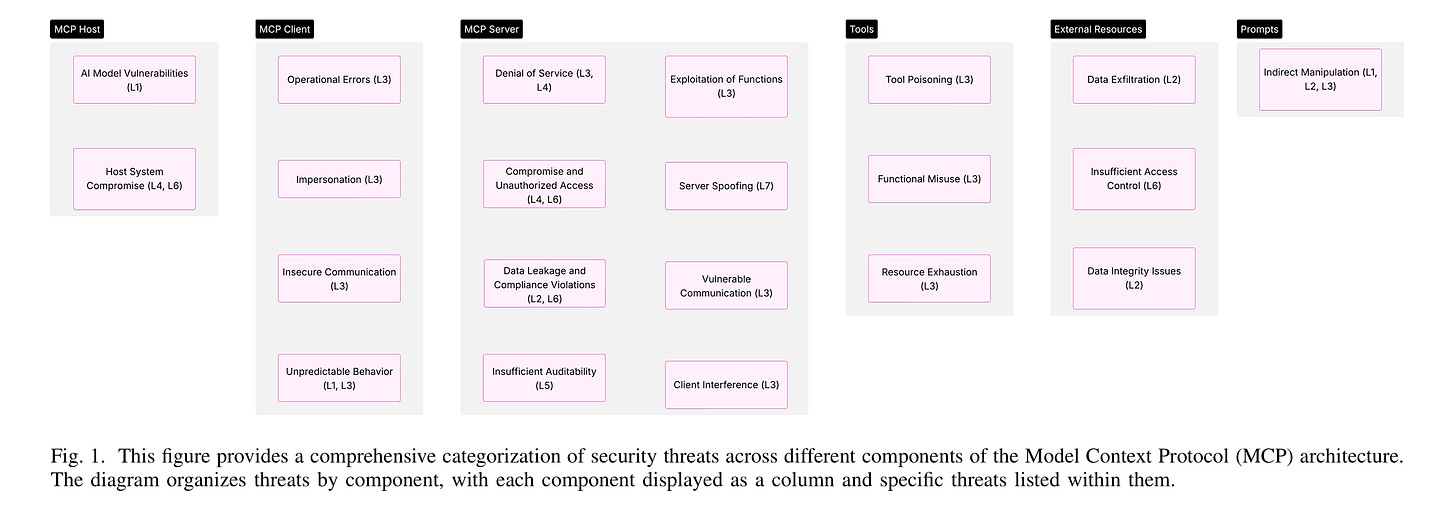
Below is a categorization of security threats to components of MCP :
This is a great and short (11 pages!) resource for those who want to better understand MCP and how it can be exploited and secured.
While not directly from the same source, I did stumble across a great dynamic visualization of “Vulnerabilities of MCP” from Rakesh Gohel on LinkedIn. In the post, Rakesh discusses each of the potential vulnerabilities.
Agentic AI Threats and Mitigations
Speaking of agents and multi-agent architectures, I recently wrote an article discussing OWASP’s Agentic AI Threats and Mitigations publication.
It covers key topics such as:
What is an “Agent”?
Agentic AI Architectures, both for single and multi-agent environments
The rise of Non-Human Identities (NHI)’s and their importance with Agentic AI
Vulnerabilities with aspects of the agentic ecosystem, such as the Model Context Protocol (MCP)
Agentic AI Patterns
Agentic AI Threat Modeling
This OWASP publication and its associated “Agentic AI Threats Taxonomy Navigator” are great resources for security practitioners looking to address agentic architectures and potential risks. I’ll be joining the OWASP team for a panel at RSA on the publication and topic, so stay tuned for more on that!
Mitigating LLM Prompt Injection
It's well known that one of the most common and problematic vulnerabilities in LLMs is the potential for prompt injection.This is cited in sources such as OWASP GenAI Security Project LLM Top 10. Google DeepMind recently released a new paper titled "Defeating Prompt Injections by Design," and Simon Willison does a great job summarizing it in this article.
It converts user commands into a sequence of steps in a Python-like programming language, checking the inputs and outputs of the steps to ensure data isn't improperly disclosed.
The research doesn't claim to solve prompt injection but can significantly decrease its probability and risk. Very interesting research here, and it will be interesting to see it be put into practice.
MCP Research Briefing by Wiz
Building on the MCP theme this week, Wiz dropped a comprehensive and awesome research brief focused on MCP, including:
MCP: New Technology, Old Risks
How to Secure Yourself Today
How to Secure Yourself Tomorrow
Takeaways
References
In typical Wiz fashion, it is full of not just great technical content but also amazing diagrams to really help those who learn and understand visually as well, such as the one below:
MCP & A2A: Security Implications and Practical Insights
Rounding out the MCP and A2A coverage this week is a piece from industry leader Caleb Sima covering both MCP & A2A and their security implications.
Caleb covers the fundamentals of MCP and its technical architecure, as well as Google’s key move introducing A2A into the ecosystem. He closes things out discussing key considerations from a security perspective as well as steps for enterprise leaders to take right now and moving forward when it comes to ensuring secure adoption and use of these new frameworks and protocols to enable agentic architectures in enterprise environments.
His key considerations include:
Access and Privileges
Shadow MCP
Standardization
And makes key recommendations around access control, governance and secure use.
AppSec, Vulnerability Management and Supply Chain Security
The CVE System Nearly Collapses
In news that rocked in the industry this week, word broke that FFRDC MITRE’s contract for the Common Vulnerability and Exposure (CVE) and Common Weaknesses and Enumerations (CWE) program was on the brink of expiration.
News largely broke across the cyber industry and ecosystem via social media, as folks such as Brian Krebs and myself began sharing the above letter from Yosry Barsoum of MITRE, who wrote to inform the CVE Board that the funding was set to expire in a day and the potential ramifications if so. Many others began joining in to raise alarms, including recent CISA Director Jen Easterly and media outlets such as CSO Online, NextGov and many others.
For those unfamiliar, the CVE ecosystem is the primary vulnerability identification system used, and is what downstream vulnerability databases, such as the NIST National Vulnerability Database (NVD) rely on. NVD of course had its own problems last year with a gap in funding and contractual support, leading to months of CVE’s not being enriched, and even to this day, a massive backlog of thousands of CVE’s which still haven’t been enriched, and many now being “deferred”, set to never be addressed by NVD.
Rightfully, the ecosystem began to panic with the latest news from MITRE on CVE as so many organizations rely on CVE’s, including vulnerability scanners, tools, researchers, security practitioners and everything in between. At the 11th hour, CISA announced that the program was being funded.
For those interested, the contract is estimated at about $58 million, which gives some insight into what it costs to run this program the entire cyber and software ecosystem relies on.
However, many are growing increasingly skeptical of the resilience and reliability of CVD, NVD and other critical entities that underpin the entire software and cyber ecosystem. In the wake of the CVE fiasco, we’ve now seen several entities announced and established to try and mitigate this risk.
This includes:
The CVE Foundation, which consists of current and former CVE Board members, who are looking to transition CVE to a non-profit foundation and eliminate a “single point of failure”
The Global CVE Allocation System (GCVE), which is described as a “new, decentralized approach to vulnerability identification and numbering, designed to improve flexibility, scalability, and autonomy for participating entities.”
The European Union Vulnerability Database, with support from ENISA.
Below is a diagram from James Berthoty
Last but not least, I hosted a discussion with my friends and fellow AppSec and Vulnerability Management enthusiasts James Berthoty, Patrick Garrity and Francesco Cipollone on the topic:
We discussed:
What happened and why this became such a big deal
What the potential downstream impacts across cyber and software would have been
Where we go from here
Resilient Cyber w/ Varun Badhwar - AI for AppSec - Beyond the Buzzwords
In this episode, I sat down with Varun Badhwar, Founder and CEO of Endor Labs, to discuss the state of AI for AppSec and move beyond the buzzwords. For those unfamiliar, I serve as the Chief Security Advisor at Endor Labs and they have been a leader for several years now in AppSec in areas such as Software Composition Analysis (SCA) and vulnerability prioritization via reachability analysis, as well as securing CI/CD environments and modern development. They’re now ensuring organizations can ride the wave of Agentic AI securely, which we dive into on the show.
We discussed the rapid adoption of AI-driven development, its implications for AppSec, and how AppSec can leverage AI to address longstanding challenges and mitigate organizational risks at scale.
Varun and I dove into a lot of great topics, such as:
The rise of GenAI and LLMs and their broad implications on Cybersecurity
The dominant use case of AI-driven development with Copilots and LLM written code, leading to a Developer productivity boost. AppSec has struggled to keep up historically, with vulnerability backlogs getting out of control. What will the future look like now?
Studies show that AI-driven development and Copilots don’t inherently produce secure code, and frontier models are primarily trained on open source software, which has vulnerabilities and other risks. What are the implications of this for AppSec?
How can AppSec and Cyber leverage AI and agentic workflows to address systemic security challenges? Developers and attackers are both early adopters of this technology.
Navigating vulnerability prioritization, dealing with insecure design decisions and addressing factors such as transitive dependencies.
The importance of integrating with developer workflows, reducing cognitive disruption and avoiding imposing a “Developer Tax” with legacy processes and tooling from security.
If you prefer audio and podcasts see below:
Please be sure to leave a review and subscribe!
State of Exploitation
Many are familiar with the reality that only a small percentage of CVEs are exploited. What that percentage is, however, seems up for debate. With the rise of the Exploit Prediction Scoring System (EPSS) and other research, the industry has woken up to the fact that most CVEs in a given year never see exploitation activity and has begun prioritizing those with known or likely exploitation.
Determining what is likely to be exploited or known to be exploited isn’t trivial, though, and really comes down to quality signals and sources. Michael Roytman of Empirical Security recently took to LinkedIn, saying that it isn’t 1-2% of CVEs in a given year that sees exploitation, but roughly 3x that, around 6%.
Being able to know what CVEs to prioritize for remediation being on exploitation activity is key and the differentiator among data sources will be the validity and quality of that data.
Resilient Cyber: Ravid Circus - Tackling the Prioritization Crisis in Cyber
In this episode, I sat down with the Co-Founder and CPO of Seemplicity, Ravid Circus, to discuss tackling the prioritization crisis in cybersecurity and how AI is changing vulnerability management.
We dove into a lot of great topics, including:
The massive challenge of not just finding and managing vulnerabilities but also remediation, with Seemplicity’s Year in Review report finding organizations face 48.6 million vulnerabilities annually and only 1.7% of them are critical. That still means hundreds of thousands to millions of vulnerabilities need to be remedied - and organizations struggle with this, even with the context of what to prioritize.
There’s a lot of excitement around AI in Cyber, including in GRC, SecOps, and, of course, AppSec and vulnerability management. How do you discern between what is hype and what can provide real outcomes?
What practical steps can teams take to bridge the gap between AI’s ability to find problems and security teams’ ability to fix them?
One of the major issues is determining who is responsible for fixing findings in the space of Remediation Operations, where Seemplicity specializes. Ravid talks about how, both technically and culturally, Seemplicity addresses this challenge of finding the fixer.
What lies ahead for Seemplicity this year with RSA and beyond
GitHub Actions Supply Chain Attack - tj-actions Breakdown by Unit 42
A recent incident focused on GitHub actions and tj-actions reminded everyone that supply chain security is still a thing. This breakdown by Palo Alto’s Unit 42 group is among the most comprehensive of the incident I’ve seen yet.
As they lay out, it was a complex, multi-layered attack involving GitHub Actions and much more.