Resilient Cyber Newsletter #28
CISO Compensation & Budgets, Israeli Cyber Startup Exit Landscape, U.S. Seed Landscape, Top 2024 Cyber Startups, Agentic Predictions and the State of ASPM
Welcome!
Welcome to the final issue of the Resilient Cyber Newsletter for 2024.
What a year it has been as we launched the newsletter this year, hit 28 issues with this latest release, covered many great topics and resources, and reached nearly 500,000 people through the Resilient Cyber Newsletter and deep articles, analysis, and standalone pieces I publish here.
As we close the year, there are many insightful topics to cover, from market analysis, M&A, fundraising, security leadership AppSec, and more - so let’s get to it!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 8,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cyber Leadership & Market Dynamics
2024 CISO Compensation & Budget Benchmark Survey
IANS and Artico released their 2024 “Compensation & Budget Benchmark Survey,” which provides many interesting insights.
While it discusses CISO and Security leader compensation, it also provides insight into the structure of cybersecurity teams based on an organization’s size and scale.
The image below shows the makeup of a typical security organization and the specific niche roles that become filled as the organization grows in size.
This is useful for security leaders within organizations to see how they compare to their peers in terms of team sizes and senior cyber roles for managing various aspects of cyber (e.g., AppSec, IAM, GRC, etc.). It is also useful for vendors who may be interested in how security teams are typically structured and who may be responsible for what as they look to sell into enterprises of various sizes and scopes.
It is worth noting that GRC is the role that gets filled the quickest, alongside SecOps, as security leaders need to grapple with not only the operational concerns of running a digital enterprise but also with the myriad of compliance requirements and frameworks for different industries, data types and more.
This further emphasizes the importance of compliance for organizations. It often functions as a real business enabler and ensures a fundamental level of security controls, despite security practitioners often bemoaning GRC with phrases such as “compliance doesn’t equal security.”
I posted about this research on LinkedIn, and it attracted a lot of great discussion from various cyber and tech practitioners and leaders on team dynamics, budgets, and more; you can check that out here. Also, Matt Chiodi at Cloud Security Today interviewed Steve from Artico Search about the publication, which can be found here.
Israeli Cyber Startup Exit Landscape
If you’ve spent any time studying the cybersecurity market from the perspective of vendors and companies, you know that Israel is a massive contributor to the ecosystem. Many of our industry’s leading cybersecurity vendors and tools were founded by Israelis, and some of the most historical companies in cyber can be traced back to Israel.
We won’t discuss why in this post, but I recommend checking out Ross Haleliuk’s article “Why Israel may become the winner in the global cybersecurity market, and what can make it fail” or the book “The Battle for Your Computer: Israel and the Growth of the Global Cyber-Security Industry” which examines Israel’s role in the cyber ecosystem. I advise and collaborate with cybersecurity innovators, thought leaders, and disruptors. Many live in or are from Israel, and Israel’s contributions to the cybersecurity ecosystem are incredible.
Venture Capital (VC) firm Nightdragon recently published an awesome report titled “Israeli Cyber Startup Exit Landscape,” which looked at M&A, IPO, and Cyber Unicorns from 2019-now, providing excellent insights regarding the exit landscape and what played into it, from funding rounds, funding sizes, exit values and much more.
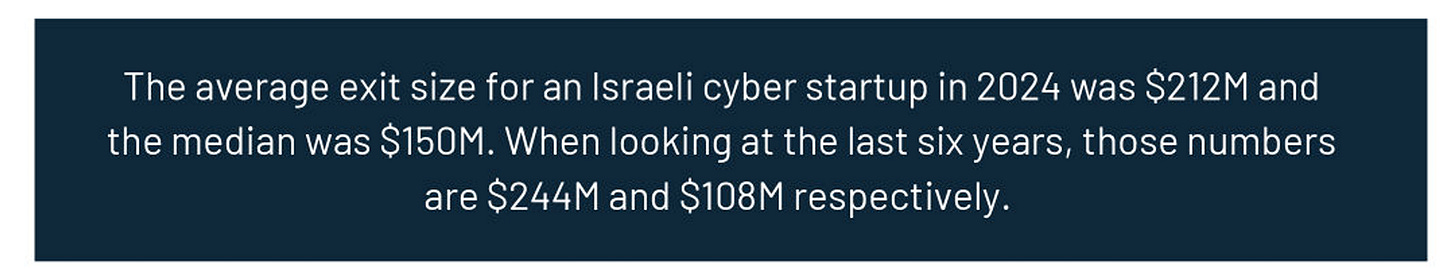
In the report, Dorin showed that 67% of exits in 2024 were at or above $100M, which is higher than any year prior through 2019. This includes 2021, which, as you can see, was a bit of an outlier, partly due to circumstances such as ZIRP, COVID, a boon to remote work, and more.
She goes on to provide excellent insights, such as the exit sizes, below:
Another interesting trend, as seen below, is that while most of all exits typically occur during Seed and sometimes Series A, exits above $100M occur earlier, at Seed/A, as opposed to A/B or even C, which was the previous norm. This means companies are not only exiting earlier but doing so with sizable exits as they quickly start, raise capital, find market fit, and get acquired.
That said, there is nuance there, and not all companies perform equally.
As seen above, while there is a -29% decrease in the time it takes to exit at $100M+, companies who exit below $100M are taking 21% longer, however she does point out that some outliers contribute to these metrics, both on those taking longer, and those happening faster. As Dorin points out, the average Israeli exit takes 3-4 years.
She goes on to point out much more, such as the amount of capital raised, relationships to exit timelines, and many other interesting insights, so I recommend diving into the actual report for more detail.
Additionally, the report discusses IPOs, which is much more applicable to more mature organizations, so be sure to check that out as well.
Below is a quick summary of the report:
On a similar front, it was recently reported that Israeli high-tech raised $9.58 billion in 2024, despite economic uncertainty and war. The figures were led by organizations such as Wiz and Cyera, among others. This represents a 38% increase in capital raised and a 13% increase in the number of rounds compared to 2023.
It was stated that Cyber companies also dominated fundraising, representing 38% of the total funds raised, with 76 fundraising rounds specifically for cyber. Additionally, a report from PwC pointed out that Israeli tech exits surged 78% in 2024, being led by cyber and AI.
While this doesn’t directly represent the U.S. Cyber exit landscape, Israeli startups represent a strong pillar of the broader cybersecurity startup ecosystem and this is an excellent analysis and side for the industry as a whole as well.
U.S. Seed Stage Landscape 2024
Peter Walker, Head of Insights at Carta, recently shared some great metrics about the U.S. Seed Stage Landscape for 2024. I’ve shared several of Peter’s visualizations and breakdowns before, and if you aren’t following him on LinkedIn and you’re interested in market dynamics, funding, venture capital, investments, and more - you are missing out!
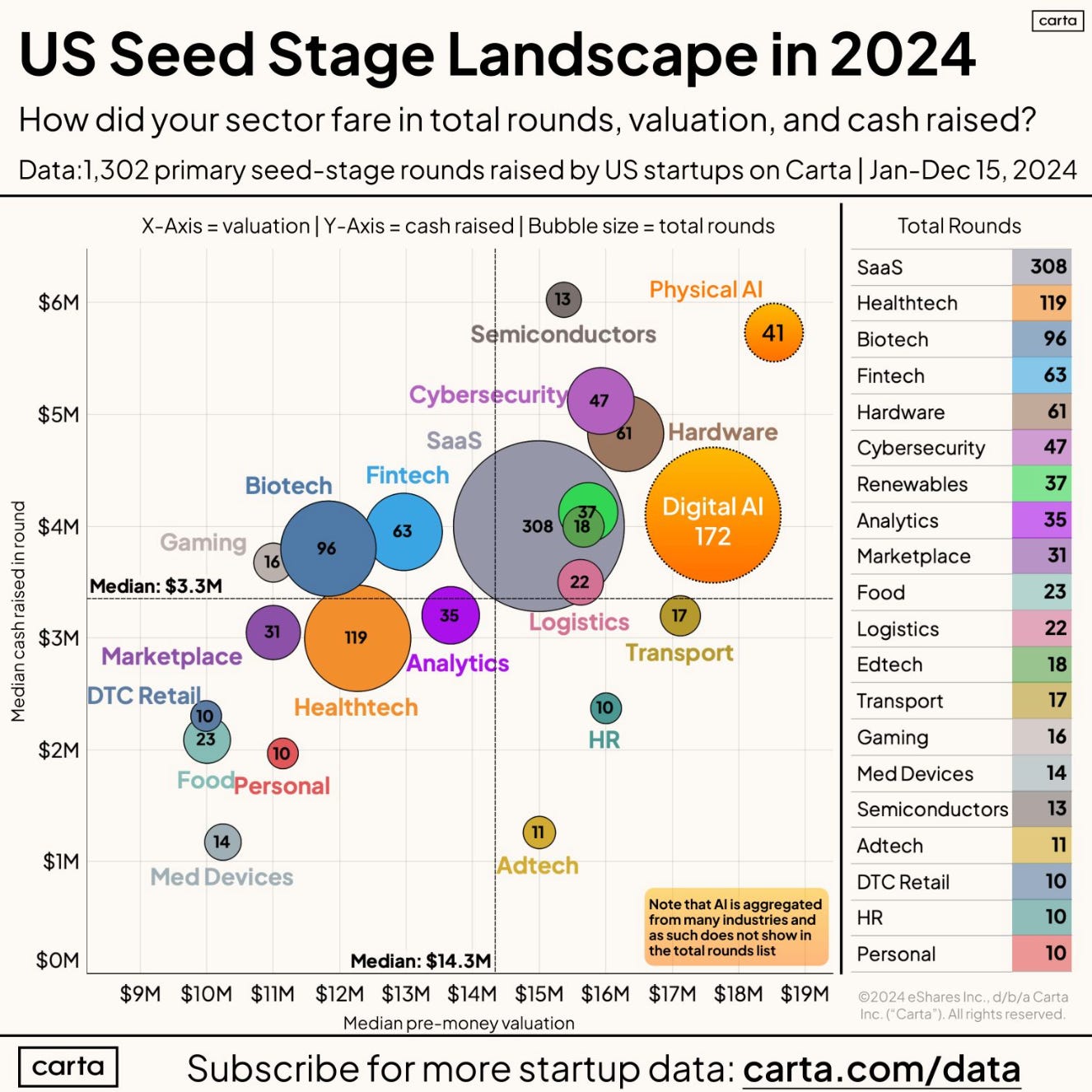
This chart depicts the median cash raised in rounds and the median pre-money valuation. The size of the bubble represents the number of rounds.
As you can see, cybersecurity performed quite well, with 47 rounds in total. It was also strong regarding cash raised and pre-money valuations.
AI has also played a massive role in fundraising and startups this year. The bubbles for digital and physical AI are aggregated across other categories, including cyber, so “Digital AI” inevitably includes cybersecurity firms.
This aligns with metrics we’ve seen from others, such as Mike Privette’s Return on Security and the general market sense where many firms we see coming out of stealth, announcing Seed rounds, and more are often tied to AI in some way, and tackling some intersection of Cyber <> AI, whether that is looking to secure AI and organizational use of AI, or looking to leverage AI to tackle systemic cyber challenges, such as the SOC, AppSec and GRC.
Startups Are Getting Older
Building on the above insights from Peter, he also shared a post detailing how the average age of startups is climbing.
As he points out, if IPOs aren’t an option until 12~ years, if at all, employees will not see liquidity situations for quite a while. The same is true for founders, who must accept they’re in for a decade-long ~ journey. This also impacts investors since most venture funds are set up around a 10-year window.
All this has nuance too, though, as I pointed out in the piece from NightDragon’s Dorin, demonstrating the average Cyber startup exits 3-4 years into their journey (at least Israeli-centric ones), but that again has nuance, as the Israeli cyber startup ecosystem is unique and not identical to its U.S. Cyber startup counterpart.
2025 NDAA Cyber Provisions
It’s that time of year again when the National Defense Authorization Act (NDAA) is passed, and folks dig into the specifics of this comprehensive and far-reaching defense bill. This year, as usual, it includes several cyber-specific provisions, such as:
Addresses a $3Bn shortfall to replace Chinese-made telecommunications equipment that poses threats to national security
Require the DoD to conduct broad assessments of the cybersecurity of internal mobile devices used by service members
Watered down measures to establish a U.S. Cybersecurity Force as a standalone military branch
Requires the NSA to establish an AI Cybersecurity Center within 90d
And much more, be sure to check out the highlights in the article above.
CISA’s Uncertain Future Under Trump’s Second Term
There continues to be much speculation about the future holders of CISA under Trump’s second term. This article does a great job discussing that, along with commentary from practitioners and experts in my network, such as Casey Ellis.
Overall, we’re likely to see CISA play less of a role in election security and “misinformation” and a shift in focus towards nation-states, offensive cyber, and more. We will also likely see less regulation-driven activity, such as SEC and CISO liability and antitrust efforts, and more of a focus on national security and securing critical infrastructure.
I’m a big fan of CISA’s work, including KEV, Secure-by-Design, Vulnerability Alerts, and more. In 2024, I participated as a CISA Cyber Innovation Fellow (CIF). I hope we continue to see them work on these sorts of efforts into 2025.
Into 2025 - DoD’s 2024 Cyber Year-End Review
The DoD made a lot of progress in 2024 on efforts they deemed critical to cybersecurity. From advancing the CMMC program, publishing further guidance and progress on their Zero Trust Goals, moving forward on Replicator, which aims to bring thousands of innovative capabilities into the hands of DoD mission owners to help keep pace with nations such as China, address cyber for Operational Technology (OT) environments and more.
Top 10 Cyber Companies Founded in 2024 - By Headcount
In 2024, startups had a busy year. As we head into 2025, the excitement seems to be growing, especially regarding administration changes and potential market ramifications, such as economic growth and deregulation.
This post from Richard Stiennon captures what he defines as the top 10 Cyber companies founded in 2024 by headcount. However, it comes with a major caveat: It can take several years to identify new companies as they emerge from stealth, find product-market fit, and more.
AI
AI Vulnerability Scoring System (AIVSS)
We all know and love (I’m joking) the Common Vulnerability Scoring System (CVSS). Do we need something like CVSS for AI systems? Perhaps, that is at least the thought of folks who have created AIVSS.
I have previously shared this in another issue of Resilient Cyber, but they recently released an updated AIVSS. It looks at the unique risks of AI systems, specifically LLM’s and cloud-based AI services.
They created the AIVSS because vulnerability scoring systems that account for unique aspects of AI systems, such as adversarial attacks, model degradation, ethical concerns, the AI lifecycle, and more, are lacking.
25 Agent Predictions for 2025
As we approach 2025, prediction season is upon us, as it is every year as we roll into the new year. While many predictions are largely noise, I find some helpful, especially from trusted voices in the industry.
The podcast/show “The AI Daily Brief,” which I began following in early 2024, is among one of the best resources I have found for staying on top of AI news, and the host has a strong understanding of the space and relevant trends.
As a close-out to the year, he hosted a two-part series with another industry leader discussing “25 Agent Predictions for 2025.” Given the heavy focus on Agentic AI heading into 2025, this was timely. They didn’t just present the predictions but also had an open dialogue about each one, which was valuable. You can check it out below!
Building Effective AI Agents
By now, we all have come to accept that Agentic AI is all the buzz. It is the topic of discussion everywhere we turn, among VC’s, startups, tech outlets and more. But how do you go about actually building effective AI agents?
AI leader Anthropic released an article discussing exactly that, and thankfully they open with one key question - do you even need AI agents? The reality is that not all organizations or more specifically situations will warrant the use of AI agents.
However, many industries, sectors and organizations are finding compelling use cases for the potential of Agentic AI. This is a great blog discussing how to get started if you’re among them.
Their leading recommendation is to find the simplest solution possible and only increase complexity when necessary. As a security practitioner this of course is appealing to me, as we know complexity is often the enemy of security, and complex systems fail in complex ways - a concept from resilience thinking.
The blog discusses some of the leading agent frameworks, such as LangGraph, Amazon’s Bedrock AI Agent Framework and others, but also mentions that the use of these frameworks often adds abstraction, and again, potential complexity, so warrant consideration.
They go on to discuss common patterns for agentic systems such as the augmented LLM, Prompt Chaining, Routing, and Orchestrator Workers among other patterns, each of which they provide diagrams for, to help visualize their workflow and function.
Below are examples of Prompt Chaining, and Orchestrator-Workers, in that order.
They also discuss the role of agents in detail, and when to use them, and again provide a great simple diagram to help visualize their functionality.
Each of these potential patterns and workflows can be used in isolation, combined or modified depending on the use cases involved.
This is a really excellent blog to get a foundational understanding of Agentic AI patterns, workflows and the role of agents. It also provide fundamental thinking of when to potentially use the different patterns and how.
I hope leaders like Anthropic keep putting out this sort of information to help organizations in their infancy with AI and Agentic workflows make sense of it all and start off on a solid footing.
Top AI Stories of 2024
To say it was a busy year in the space in and around AI would be putting it lightly. We had a lot going from new models, expanding use cases/applications, pricing discussions, the buzz around Agentic AI, Service-as-a-Software, and more. This recap from Andrew Ng does an excellent job discussing some of the key AI stories from 2024.
AppSec, Vulnerability Management and Supply Chain Security
From SOAR to AI-Driven Security: Do We Need a New Name for the Future of Automation at DefCamp 2024
We continue to see SecOps be a key target for GenAI and LLM’s. I recently shared my interview with Filip Stojkovski and several of his articles around SecOps and AI. He also recently gave a talk at DefCamp 2024, diving into the potential future of SecOps with AI, which can be found below.
The State of Application Security Posture Management (ASPM) 2025
One of the terms that caught hold in 2025 within AppSec was ASPM. This is due to a variety of factors, such as a continuing complexity in the vulnerability management space, organizations drowning in vulnerability backlogs, security tool sprawl, platform vs. point solution battles and much more. For a deeper dive on ASP, I recommend checking out my article from earlier this year titled “The Rise of ASPM Platforms: The culmination of the convergence of ASPM, DevSecOps and Vulnerability Management”.
While folks define the term differently, it is clear that it is here to stay for now in terms of categories. One of the leading vendors in the space, Cycode, recently released their “State of ASPM 2025” report, which has some interested insights.
The report opens with an astounding metric of over 90 billion lines of code (LoC) being generated in 2024, driven in part by GenAI and undoubtedly the rise of copilots. This trend will continue as well, as they cite Gartner predicting that by 2026 80% of enterprises will embed AI deeply into their operations, which of course means increased development velocity and volume.
This will continue to contribute to the challenges we see unfolding now, which have contributed to the rise of ASPM’s, which is security tool sprawl, exponential vulnerability backlog growth and alert fatigue as organizations try and keep pace and address real risks.
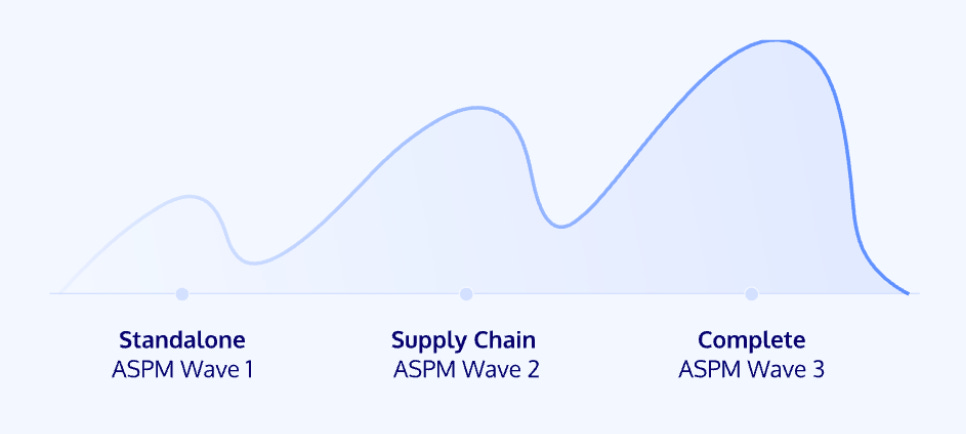
Cycode lays out three waves of ASPM, as seen below:
They state the first wave was focused on aggregation of findings and data from various security tools, the second focusing on supply chain threats (e.g. Log4j), and the third, where we are now, looking to bring it all together, with rich context, while accounting for complex operating environments of cloud, code and more.
The report goes on to take a deep dive into several systemic challenges, such as the exacerbation of attack surface via GenAI, tool sprawl, runaway code volume and security budgets.
This is a well done report and I definitely recommend giving it a read.
2024 Cloud Security Highlights
Nick Frichette recently published his 2024 Cloud Security Highlights which includes a ton of great cloud security talks from industry leaders this year, as well as comprehensive research and deep dives on cloud-specific threat vectors and risks.
This is part of his repository “Hacking the Cloud” which services as a comprehensive repository of offensive and defense security knowledge for cloud-native technologies and is worth checking out!