The Rise Of Application Security Posture Management (ASPM) Platforms
The culmination of the convergence of ASPM, DevSecOps and Vulnerability Management
This report on application security posture management (ASPM) is a piece I have collaborated on with Francis Odum, the author of “The Software Analyst” newsletter.
We take a deep dive on the AppSec ecosystem, rise of the Application Security Posture Management (ASPM) category, key drivers, innovative solutions and where we’re headed in the industry.
So dive in and enjoy it!
Welcome to Resilient Cyber!
If you’re interested in FREE content around AppSec, DevSecOps, Software Supply Chain and more, be sure to hit the “Subscribe” button below.
Join 5,000+ other readers ensuring a more secure digital ecosystem.
If you’re interested in Vulnerability Management, you can check out my new book “Effective Vulnerability Management: Managing Risk in the Vulnerable Digital Ecosystem” on Amazon. It is focused on infusing efficiency into risk mitigation practices by optimizing resource use with the latest best practices in vulnerability management.
Key Summary
Software development has grown complex, leading to significant challenges in maintaining application security. With teams from development to operations handling different aspects and numerous testing tools in play, getting a full picture of an application's security status is tough. This situation makes it difficult to effectively assess, prioritize, and fix security issues.
Businesses can’t manage twice the number of tools as they have security personnel, each of which are triggering thousands of alerts when they’re deployed. As applications become more complex, and with different security tools spanning multiple groups, visibility into the overall security posture of applications becomes vastly more difficult to obtain. This complicates efforts to assess, measure, prioritize and respond to application risks.
Legacy security tooling provided immense amounts of low-fidelity findings that lacked context and caused significant toil on development teams, taxing their productivity and causing security teams to waste time on findings that posed no significant risk.
Historically, security testing and operational monitoring have worked separately. Developers conducting security tests through methods like SAST, DAST, and IAST often operate isolated from operations and cloud security teams who monitor applications for security breaches or misconfigurations or focus on infrastructure as opposed to applications and code. This separation leads to duplicated efforts and makes unified risk management hard.
You can find Francis’ and I’s walkthrough discussion of the article and analysis here too:
Introduction
Traditional VM has evolved and increasingly intersects with ASPM due to changes in the threat landscape and application development practices. The convergence is driven by the need to manage vulnerabilities more comprehensively across applications rather than just focusing on infrastructure or operational environments managed by the operations teams.
Traditional VM often focuses on managing known vulnerabilities that have been cataloged in databases such as the NIST National Vulnerability Database (NVD). The reliance on CVEs (Common Vulnerabilities and Exposures) listed in the NVD means that vulnerability management can be reactive, addressing risks only after they have been formally identified and documented. This approach can miss newer or emerging threats that haven't yet been captured in the CVE system, potentially leaving organizations exposed to zero-day attacks or rapidly evolving exploits.
The best vendors address these gaps by incorporating a threat intelligence capability that goes beyond the conventional CVE list. The platform's threat intelligence can identify and assess risks that are not yet documented in the NVD. This proactive approach allows organizations to detect and respond to threats earlier in their lifecycle, potentially before they are exploited in the wild.
The convergence of VM and ASPM, as facilitated by platforms like ArmorCode, means that vulnerability management becomes a more integral part of the overall application security strategy. It's not just about patching known vulnerabilities but about understanding the security posture of applications in a dynamic environment. This integration helps organizations prioritize their security efforts more effectively, not just those already known and cataloged.
The Evolution of DevSecOps & Modern Software Development Process
Historically silos have existed between various technology teams supporting organizations uses of hardware and software to deliver business value and support ongoing operations. These teams have included Development, Operations and Security. The industry initially rallied around DevOps, along with iterative software development methodologies, most prominently captured in the “Agile Manifesto.”
However, over time, security practitioners among others began to raise concerns that security was being left out of the evolution of software development and DevOps, leading to the term and trend towards DevSecOps. DevOps purists of course will argue that security has always been part of DevOps, as a subset of quality, and while in theory that is valid, years, and even decades now, of insecure products, exploitation, incidents and data breaches impacting hundreds of millions and even billions of individuals personal data, along with corporate data raises doubts.
NIST defines “DevSecOps helps ensure that security is addressed as part of all DevOps practices by integrating security practices and automatically generating security and compliance artifacts throughout the process.” Specific benefits are cited, such as:
Reduces vulnerabilities, malicious code, and other security issues
Mitigates the potential impact of vulnerability exploitation throughout the application lifecycle
Addresses the root causes of vulnerabilities to prevent recurrences
Reduces friction between the development, operation, and security teams
While DevSecOps is not a tool, or technology and instead is a methodology of integrating security throughout the SDLC, it often does include integrating security tooling via technologies such as Continuous Integration/Continuous Deployment (CI/CD) pipelines. This often includes tools such as Static and Dynamic Application Security Testing (SAST/DAST), Secrets Management, Infrastructure-as-Code (IaC) scanning, container scanning and more. The integration of these tools accompany a push to “shift security left”, which is another mantra and industry shift associated with DevSecOps. This emphasizes moving security left in the SDLC to try and identify and remediate vulnerabilities prior to reaching runtime production environments.
Tools in the space have continued to evolve to cover various functional categories and environments, often seeking to provide coverage from “code to cloud”, representing a push to provide security coverage from the underlying cloud hosting environment (IaaS, PaaS and SaaS) to the applications at runtime hosted in those environments. This evolution has helped usher in a new category increasingly being referred to as Application Security Posture Management (ASPM) in addition to the building of comprehensive platforms often called Cloud Native Application Protection Platforms (CNAPP).
Additionally, security has begun to see a shift towards “as-Code”, aligning with the growth of cloud and modern infrastructure practices such as Infrastructure-as-Code (IaC), which is a declarative way to define and deploy cloud-native infrastructure. This allows infrastructure to be treated as software and utilize techniques such as version control, rollbacks and manage configuration drift. Security has slowly begun to adopt this paradigm shift, with techniques such as Compliance-as-Code looking to mitigate configuration deviations and risks as well as implement guardrails to mitigate risk either prior to the deployment of infrastructure and systems as well as remediation risks as they materialize. This includes items such as secure storage, encryption, access control and much more.
We’re also starting to see the adoption of compliance artifacts in codified language, with the evangelism for adoption of approaches such as NIST’s Open Security Control Assessment Language (OSCAL), which helps take typical legacy static documents for compliance that often exist in word and PDF format and shift them into a codified format, bringing them closer to the nature of modern cloud environments, and in-line with the push for “as-Code” management.
Despite all the innovations around DevSecOps in terms of people, process and technologies, many challenges still remain. This includes security often introducing friction onto development and engineering peers due to noisy scanning tools with low fidelity findings and a lack of context enrichment that drowns development teams in vast vulnerability backlogs. Rather than achieving guardrails, security teams often instead implementing gates. Security often implements “security gates” with the tools, with subjective path to production and deployment criteria leading to bottlenecks and delays in code deployments and leading to resentment and frustration from development peers. This outcome ironically often bolsters silos between Security and Development teams, one of the key things that the push for DevSecOps sought to break down.
Vulnerability Management
As the landscape of digital products and software has grown, organizations struggle to keep pace with the growing number of vulnerabilities in the ecosystem. The NIST National Vulnerability Database (NVD), which is the most widely recognized and used vulnerability database in existence, continues to set records YoY for the number of known vulnerabilities, captured as Common Vulnerabilities and Exposures (CVE’s) that it reports. Along with that, and due to the fact that no single vulnerability database can be all encompassing, we’ve also seen the growth of various other vulnerability databases, such as the OSV (Open Source Vulnerabilities), the OSS Index developed by Sonatype and the GitHub Security Advisory Database, each of which brings unique findings often not captured in the NVD.
As one of the authors here wrote in an article titled “Sitting on a Digital Haystack of Needles” - it is often known that “defenders have to be right all the time, attackers only need to be right once”, and it is getting increasingly easy for them to be right, as the number of known vulnerabilities, just using CVE’s as a source, continues to grow extensively YoY. This is emphasized by the metrics and image below from vulnerability Researcher Jerry Gamblin
For Example:
2023 YTD CVE Stats:
Total Number of CVEs: 28,261
Average CVEs Per Day: 84.61
Average CVSS Score: 7.13
YOY Growth: 20.10% or +4,730 CVEs (23,531 CVEs YTD 2022)
Historic Solutions
Organizations traditionally utilize tools such as vulnerability scanners to identify vulnerabilities in their environments, the impacted systems, severity of vulnerabilities and track metrics such as trends over time to demonstrate improvements in reducing risks associated with vulnerabilities both in isolation and in aggregate.
Historically these tools focused on items such as endpoints and servers but with the evolution of cloud, IaC, open source adoption and more, the types of tools used to scan for vulnerabilities has seen tremendous growth. These tools now include Static and Dynamic Application Security Testing (SAST/DAST), Infrastructure-as-Code (IaC) scanning, container scanning, software composition analysis, secrets scanning, virus and malware scanning, Kubernetes and of course runtime scanning tools in addition to those that scan source code or during the build and deployment of software.
These scanning tools have helped highlight vulnerabilities from the myriad of potential sources in modern cloud-native environments, and they’ve also facilitated industry trends, such as the push to “shift security left”, which represents identifying vulnerabilities earlier in the software development lifecycle (SDLC) prior to their introduction to production runtime environments where they can be exploited by malicious actors. The push to shift left also helps theoretically address vulnerabilities earlier in the SDLC when they are cheaper and easier to fix, although the latter claim has become hotly debated for a variety of reasons.
The Explosion In Vulnerabilities & Alerts
One byproduct of the increased use and variety of vulnerability scanning tools is the increased identification of vulnerabilities. On one hand this is great, given organizations likely wouldn’t have visibility and awareness of the vulnerabilities otherwise. However, this also assumes that the organization are in a position to actually remediate the identified vulnerabilities and has enough context to appropriately prioritize the identified vulnerabilities.
Not only do organizations suffer with finite resources due to challenges such as attracting and retaining technical talent, especially in cybersecurity, they also are dealing with just an overall explosion in the number of vulnerabilities.
Research from organizations such as Cyentia Institute (image below) demonstrate organizations are only able to remediate about 10% of new vulnerabilities per month, while vulnerability management leaders such as Qualys show that exploitation windows generally outpace organizations ability to patch.
Others, such as Qualys, have demonstrated that malicious actors easily outpace defenders when it comes to weaponizing vulnerabilities and maximizing exploitation windows contrasted against defenders’ meantime-to-remediation (MTTR).
While defenders often hyper-focus on the latest vulnerabilities, their inability to keep pace with the rapid identification and inventory of known vulnerabilities leads to extensive vulnerability backlogs.
Aged & Vintage Vulnerabilities Growing
These vulnerability backlogs often include aged, or “vintage” vulnerabilities, as they are called. In research from security vendor Rezilion titled “Vintage Vulnerabilities Never Go Out of Fashion”, they were able to find over 4.5 million internet-facing devices with known vulnerabilities that were identified between 2010-2020, many of which had known exploitation activity in the last 30 days at the time of the research. This demonstrates that the ecosystem is rife with vintage vulnerabilities that have accumulated as security tech debt in vulnerability backlogs and sits ripe for exploitation by malicious actors across the open internet.
Prioritizing & Managing Vulnerabilities
Further complicating the matter is that longstanding vulnerability prioritization schemes are based on metrics such as base Common Vulnerability Scoring System (CVSS) severity levels (e.g. Low, Moderate, High, and Critical).
This is despite findings demonstrating that less than 5% of known vulnerabilities (e.g. CVE’s) are actually ever exploited in the wild. While innovative new sources of vulnerability intelligence such as CISA’s Known Exploited Vulnerability (KEV) catalog and the Exploit Prediction Scoring System (EPSS) help prioritize known exploitation or exploitation probability, many organizations have yet to adopt these resources at scale and even then, addition context such as reachability, business criticality, compensating controls and more are needed to truly prioritize vulnerabilities.
This is why research from organizations such as Rezilion and Ponemon have demonstrated that the average organization has vulnerability backlogs numbering in the hundreds of thousands and even millions, as organizations simply lack the capacity to keep pace with remediating vulnerabilities faster than they are identified, documented, and added to existing backlogs.
The Rise of Application Security Posture Management (ASPM)
Defining ASPM
Application Security Posture Management (ASPM) has emerged as a solutions for organizations to secure their applications. Gartner forecasts that by 2026, over 40% of these organizations will use ASPM to quickly find and fix security vulnerabilities. ASPM integrates various efforts and tools into one system, managing security across the software development lifecycle (SDLC) from coding to deployment. This not only improves visibility but also helps manage vulnerabilities and enforce security controls more accurately.
James Berthoty from Latio Tech Pulse has a good definition of this topic that summarizes everything. He defines it as everything needed to scan and remediate your application for vulnerabilities. It provides security scanning across your SDLC pipeline, ingests results, and builds remediation workflows.
James defines it in an easy
“ASPM tells the story of how your code reaches production. It states that this person pushed this code to be compiled into this binary with these libraries onto this docker image deployed in this cluster on this cloud. These vulnerabilities would be fixed by changing this line of code. It tells teams exactly what lines of code to change, how to fix them, and the number of vulnerabilities that would be remediated if that change was applied. This has the additional benefit for provenance from the software supply chain perspective.
All of which allow for rich workflows with full flexibility that are easy to apply. If a new vuln shows up, slack the developer, they can choose to create a ticket or fix it now, security can ping them again if not resolved within 30 days. They integrate with other tools, pulls in vulnerabilities from other platforms, but enriches the findings with greater application context.”
The Evolution of ASOC To ASPM
For context, ASPM evolved from Application Security Orchestration and Correlation (ASOC), broadening its scope to offer a more integrated and comprehensive solution for managing application security. With its extensive coverage and advanced features for fixing, prioritizing, and sorting security issues, ASPM is increasingly becoming an essential part of modern security strategies.
Additionally, ASPM makes it easier to apply security policies tailored to each application's specific risks and compliance needs. This approach simplifies identifying and fixing vulnerabilities and allows for a detailed risk management process, considering the varied security requirements of an organization’s application portfolio. The advent of ASPM promises to improve the handling of the numerous alerts generated by security tools. Without ASPM, these alerts could overwhelm teams, possibly leading to ignored critical vulnerabilities. ASPM systems prioritize and sort these alerts based on set policies, ensuring urgent issues are quickly and effectively addressed without disrupting development or operations.
At its core, ASPM aims to enhance control over applications' security posture. It uses data from various sources, correlating and analyzing it to give a clear view of security threats and vulnerabilities. This not only makes fixing issues easier but also helps enforce security policies more strategically across all applications. ASPM also integrates security findings with workflow tools, providing practical ways to tackle vulnerabilities and boost security.
Vendor Spotlight
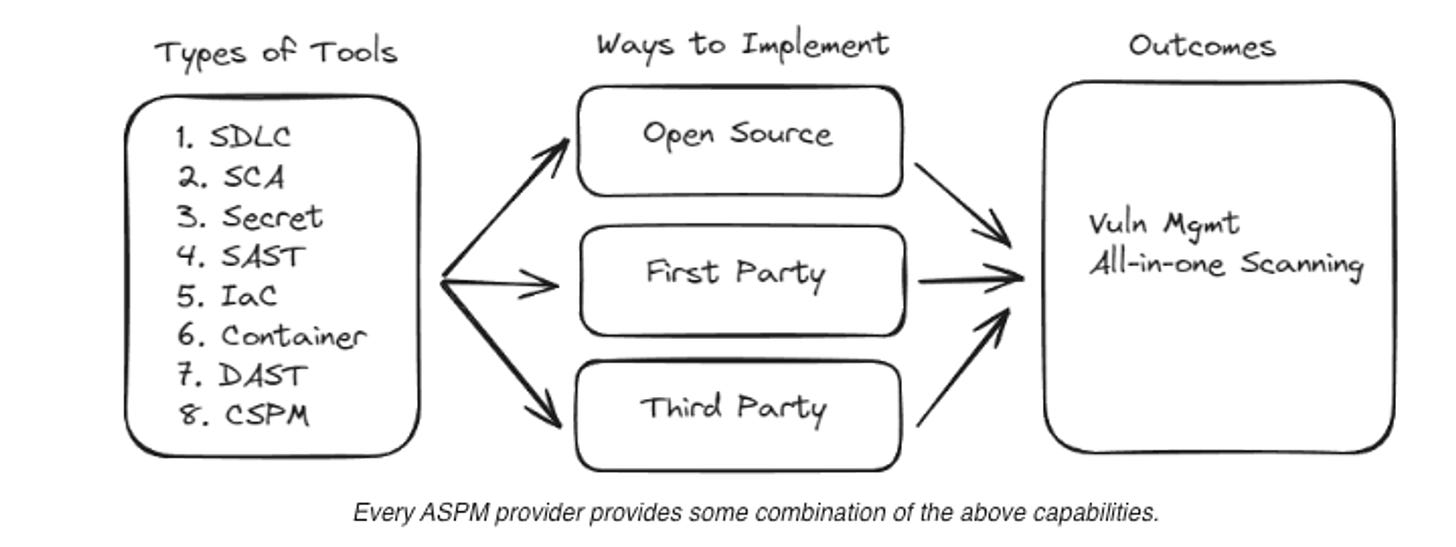
Two Categories of ASPM Solutions
ASPM Orchestrator & Aggregator Platforms: We have vendors that propose an aggregation, correlation, and prioritization platform without any scanning capability, instead relying on ingesting third-party scanners’ output. Some ASPM tools are designed to rely on the output from other AppSec platforms, ingesting it for analysis and prioritization based on the riskiness of the issues raised. Their vendors tend to stress their ability to gauge risk as the key value they add to the equation, not to mention the fact that they enable customers to continue using their existing AppSec tools.
Full ASPM Built-In Providers With Scanners (Proprietary or Open-source): On the other hand are companies such as Cycode, which offer all the building blocks to scan the disparate parts of an app as well as the downstream prerequisites of an ASPM platform - through its ConnectorX third-party security tool connector.
ASPM Orchestrator & Aggregator Platforms
We have vendors that propose an aggregation, correlation, and prioritization platform without any scanning capability, instead relying on ingesting third-party scanners’ output. Some ASPM tools are designed to rely on the output from other AppSec platforms, ingesting it for analysis and prioritization based on the riskiness of the issues raised. Their vendors tend to stress their abilities in gauging risk as the key value they add to the equation, not to mention the fact that they enable customers to continue using their existing AppSec tools.
ArmorCode
ArmorCode helps organizations shift from chasing vulnerabilities to reducing risk. The AI-powered ArmorCode Application Security Posture Management (ASPM) Platform integrates with 230+ scanners to create a unified understanding of risk of an organization's application portfolio, leverages intelligent risk scoring to prioritize the most critical risks, and orchestrates security workflows with developers to remediate issues efficiently and at enterprise scale.
Distinct from conventional scanners, ArmorCode’s ASPM platform delivers unified governance that streamlines Application Security Posture, Risk Based Vulnerability Management, Software Supply Chain Security, DevSecOps, and Risk and Compliance. This approach enables organizations to integrate and manage data from over 230 security tools—ranging from threat modelling to pen testing, including cloud, container, and infrastructure security—without vendor lock-in.
ArmorCode is focused on helping organizations reduce risk, cut the complexity from their AppSec and vulnerability management programs, and effectively burn down their critical security tech debt. ArmorCode’s AI-powered ASPM Platform integrates with all of an organization’s scanners while remaining independent from them to ensure that they can build a robust AppSec and Vulnerability Management program with best-of-breed tooling.
Based on our analysis, there are four core ways that ArmorCode distinguishes itself:
Ecosystem and Integration of Tools Approach
ArmorCode’s platform does not limit organizations to any particular scanning tool or collection of scanners, but rather they provide a comprehensive platform that integrates with most any security tools and data sources. This approach allows ArmorCode to offer a unified ASPM solution that brings together data across SAST, DAST, IAST, pen testing, cloud, container security, and more. The platform supports over 230+ different security tools and they add about 5-10 new integrations each month. ArmorCode’s ecosystem approach ensures that organizations can leverage best-of-breed tools without being locked into a specific vendor’s scanner suite. This flexibility is crucial for adapting to the evolving security landscape and integrating new technologies as they emerge, such as AI-based security tools.
Vulnerability Prioritization and Risk Scoring Engine
Earlier in our report, we discussed the growing number of alerts and vulnerabilities that security teams have to deal with on a daily basis. For Vulnerability Management, ArmorCode adopts a risk-based approach. We observed ArmorCode excels in correlating the deluge of data that comes from multiple integrated tools from code, CI/CD and cloud infrastructure tools. They are able to apply their risk scoring engine to prioritize risks based on technical severity and business context. Further making it interesting is that their method goes beyond standard CVSS scoring by considering factors such as exploitability, the business criticality of the affected system, and external exposure. By aligning technical vulnerabilities with business impact, ArmorCode helps organizations with the context required to focus on the most significant threats thereby limiting severe consequences.
They help customers visualize and report on all this information through real time, out-of-the-box and custom dashboards that include information on vulnerability statistics and trends, SLA compliance, and IT ticket status over time, as some examples. This method addresses the challenges associated with managing multiple different vulnerability prioritization and remediation tools.
Automation & AI-Powered Correlation
ArmorCode is building out more solutions to create more automation capabilities into its platform, leveraging AI to enhance the correlation of findings across different types of scanning tools to identify the root cause of issues and help speed up remediation of the backlog of tasks faced by security teams. This AI-driven automation enables alert management to provide deep insights into security vulnerabilities, enabling faster and more accurate decision-making. ArmorCode’s automation capabilities will go further as to include the orchestration of ticket creation, escalation, and notifications, thereby reducing the manual effort required from security teams. On their roadmap, they plan to bring AI into prioritization and remediation capabilities, in addition to correlation.
Scale with Big Fortune 500 Companies
ArmorCode’s ability to operate at scale is evidenced by its adoption by numerous large enterprises, over 25% of which are Fortune 500 companies. The platform has processed over 6 billion findings, demonstrating its capability to handle extensive data volumes typical of large organizations.
The scalability of ArmorCode’s platform is evidenced by the fact that a large Fortune 500 organization [Which companies do we wanna list publicly?] uses their solution across 15,000 developers. This showcases ArmorCode's capacity to manage and process large volumes of data and secure complex software development environments at a massive scale. The platform’s success with large clients across various industries underscores its effectiveness in meeting the rigorous demands of large-scale operations and complex security requirements.
On the other end of the spectrum, ArmorCode also has customers with just a couple of hundred developers and 3 to 4 scanners, showing that it can be the right fit for ASPM needs across a range of company sizes and maturity.
Summary
Overall, we believe ArmorCode offers a scalable and modular ASPM platform that integrates AppSec, Risk-Based Vulnerability Management, Software Supply Chain Security, DevSecOps and Compliance, with a proven ability to add new modules as new technologies evolve. Some of ArmorCode’s competition are customers already using open-source tools to merge and integrate all of their multiple tools. Many of their legacy competitors include Snyk, Veracode and Checkmarx. Some of their niche competitors include Ox (PBOM), Apiiro (strong scanning capabilities) and Cycode. They distinguish themselves by focusing on the breadth and depth of their integrations, risk-scoring prioritization engine, automation and the scale at which they are able to reduce risk and complexity for some of the largest organizations.
Many companies within the AppSec industry focus on providing their SCA, code scanning or cloud security infrastructure scanners and their own governance layer, however, ArmorCode has taken a different approach by building an independent platform that acts as a management layer across many of the scanners that their customers are already using. By offering a non-scanner, platform-centric solution that broadly integrates across the security tool ecosystem, ArmorCode provides a unified view that significantly enhances visibility and control over application security posture, setting itself apart from competitors.
ASPM Providers With Proprietary Scanners
ASPM Providers With Native Proprietary Scanners: On the other hand are companies such as Cycode, which offer all the building blocks to scan the disparate parts of an app as well as the downstream prerequisites of an ASPM platform - through its ConnectorX third-party security tool connector.
Cycode
Cycode is a vendor with a fully built-in ASPM solution that incorporates all of its scanners. Cycode was founded in 2019 by three prominent engineers in cybersecurity: Lior Levy, Ronen Slavin, and Ronen Slavin. Cycode provides a full ASPM solution that help organizations deliver safe code faster. Their platform offers native scanning from code to cloud, and integration with third-party security tools with their ConnectorX platform.
Proprietary Capabilities
Cycode differentiates itself by offering a 'complete' ASPM solution that encompasses natively-built security scanning across various stages of the software development lifecycle (SDLC), from code to cloud. This includes capabilities for secrets management, SCA (Software Composition Analysis), SAST (Static Application Security Testing), secret detection, ci/cd security, container security, and more. Cycode’s platform includes both proprietary technologies and the ability to integrate with other security tools, providing flexibility for organizations. Another interesting platform capability of their product capability is that they don’t leverage open-source tools and everything is proprietarily built from grounds-up.
Risk Intelligence Graph
A unique platform capability feature of Cycode’s platform is the Risk Intelligence Graph, which uses AI to offer insights based on natural language queries. This allows security teams to quickly identify and address specific vulnerabilities tied to developers, container images, and other aspects, making the security processes more intuitive and efficient. This helps organizations prioritize their risk down to the critical 1% of vulnerabilities that actually matter → risk scoring, proximity to PII, exposed/internet facing, API discoverability, etc.). At the core of their solution ensures helping organizations adhere to and be proactive in terms of managing their compliance requirements.
Cycode emphasizes the remediation and developer experience by integrating their solutions directly into developers' workflows, including IDEs and command-line interfaces, which helps in accelerating the remediation process and promoting secure coding practices without disrupting development cycles. Overall, Cycode focuses on being a comprehensive provider in the ASPM market, leveraging both proprietary and third-party tools to offer flexible and effective security solutions.
ASPM Providers Leveraging Open-Source Scanners & AST
OX Security's approach to ACTIVE Application Security Posture Management (ASPM) emphasizes the CI/CD pipeline. They have pioneered the concept of PBOM (Pipeline Bill of Materials), where a signed knowledge graph, also called PBOM, is created for each pipeline build. This graph acts as a dynamic Bill of Materials (BOM) that documents the software's lineage throughout its development lifecycle. Essentially, it's a continuously updated map that contains all the elements typically included in an SBOM, in addition to a comprehensive record of the infrastructure the software has traversed, such as pipeline branches, builds, pull requests, tickets, and known issues. OX Security's platform and CI/CD workflow automation specifically enhances the traceability and visibility of all components throughout the build and pipeline phases. Furthermore, OX Security excels in application detection and response capabilities, which enable them to determine the reachability of vulnerabilities by analyzing runtime behaviors and deducing their implications at the code level.
They meticulously analyze code repositories and pipeline configurations to detect security vulnerabilities and configuration errors. Employing a range of tools like static analysis, SAST, secrets scans, container scans, and IaC scans that identify risks or misconfigurations during the build process. After these security assessments, OX Security assigns a benchmarking application risk score based on code scans, secrets management, packages, and pipeline integrity, providing a robust measure of the application's security posture. Ox security, Apiiro and a number of other vendors have successfully created ASPM platforms that cover the full range of code to the cloud.
Leading Vendors Worth Highlighting
Snyk was the first major provider who could offer SCA, SAST, IaC, and Container all in a single platform - and that proved to be exponentially more valuable than buying four separate tools, and then a fifth to orchestrate everything. That said, while it is beneficial to utilize a platform-based approach, there may be tradeoffs with best of breed point/category tooling which can offer enhanced features and functionality that some centralized platforms may not
Endor Labs has emerged as a modernized SCA platform that provides insights into known exploitation, exploitability, and reachability. It also leveraged AI and key risk insights to help developers make risk-informed decisions around OSS consumption and natively integrates into developer workflows to minimize toil and security taxes on productivity. We know the use of OSS has seen exponential growth but so have supply chain concerns, and Endor Labs exists at their intersection to enable secure OSS usage.
VulnCheck - Another notable standout is 2024 RSA Innovation Sandbox participant VulnCheck. As we have discussed throughout the article, the list of known vulnerabilities is growing exponentially and organizations are drowning in noise trying to properly prioritize and add context. VulnCheck brings innovative visibility and context into the vulnerability ecosystem and aids prioritization and risk mitigation prior to exploitation. Additionally, they have went above and beyond CISA’s KEV and have a VulnCheck KEV which expands on known exploited vulnerabilities, offering insight that all organizations should be focused on.
Avalor - A company who positions itself as a “Data Fabric For Security” was recently acquired by one of the largest cybersecurity companies, ZScaler for $350M. As we know, security is increasingly becoming a data problem, and Avalor looks to help tackle the problem by extracting data from customers security solutions, normalize the data and help highlight the highest-risk issues using context such as environment details, reachability, exploitability and more. This is a massive area of cybersecurity ripe for disruption due to the ever expanding attack surface and need for context among the noise of vulnerabilities to focus on real risks. You can learn more about the Security Data Fabric in an excellent article from Darwin Salazar in an issue of his Cybersecurity Pulse newsletter titled “The Security Data Fabric Shift Explained: Why ZScaler Paid $350M for Avalor and What it Means for the Security Industry”.
Challenges Adopting ASPM solutions
However, adopting ASPM comes with challenges. The ASPM solutions market is still developing, with many new vendors. ASPM tools need to process large amounts of data across the SDLC, a capability that's still being tested at scale. Successful ASPM also depends on wide-ranging integration capabilities to fit smoothly into existing development and operational workflows, enhancing rather than complicating the developer experience and security stance.
In summary, as the digital and security landscapes evolve, ASPM stands out as a key approach to managing application security risks more efficiently and effectively. By connecting different security efforts and offering a unified view of application security, ASPM simplifies managing application security. Looking ahead, ASPM's role in enhancing the resilience and security of software applications in a connected world is set to be significant. The future of software security represents a convergence of application security tools, vulnerability management, and cloud security solutions wrapped up in ASPM platforms.











I find this article to be very insightful regarding the rise of ASPM, however, I believe that an important player in this domain has not been given due consideration - Palo Alto Networks.
Not only do they have the full "Code to Cloud" capabilities and beyond (AKA "to SOC") but they are also broadly recognized as market leaders in every Cyber Security related domain capabilities.
When it comes to ASPM specifically, Palo Alto clearly demonstrates best in class approach with its IaC, Secret scanners, SCA, CI/CD and more.
In conclusion, while your article provides a valuable overview of the ASPM landscape, I believe it is essential to recognize Palo Alto Networks for its significant contributions and leadership in this area. I encourage readers to delve deeper into Palo Alto's offerings to fully appreciate the breadth and depth of their ASPM solutions.