Resilient Cyber Newsletter #21
Cyber Developer Tax, New OWASP AI Guides, Open Source LLM Vulnerability Scanners, and "Shift Left" is Losing its Shine
Welcome!
Welcome to issue #21 of the Resilient Cyber Newsletter. I’m excited to share a lot of great resources this week ranging from Cyber market news, AI research and studies as well as analysis of the latest AppSec trends.
So let’s dive in!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 7,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Quickstart Template for Cloud Incident Response
Discover the measures needed to respond to incidents in your cloud environments with this resource from Wiz. With a Cloud-Specific focus, this template will serve as a foundation for optimal effectiveness, allowing teams to customize their approach to incident response.
Learn how to build a roadmap that covers all these key areas:
Threat containment
Communications
Legal
Business continuity and disaster recovery (BCDR)
Attack scenarios
Post-incident reviews
Cyber Leadership & Market Dynamics
Cybersecurity Developer Tax
Cybersecurity is like a Tax 💰
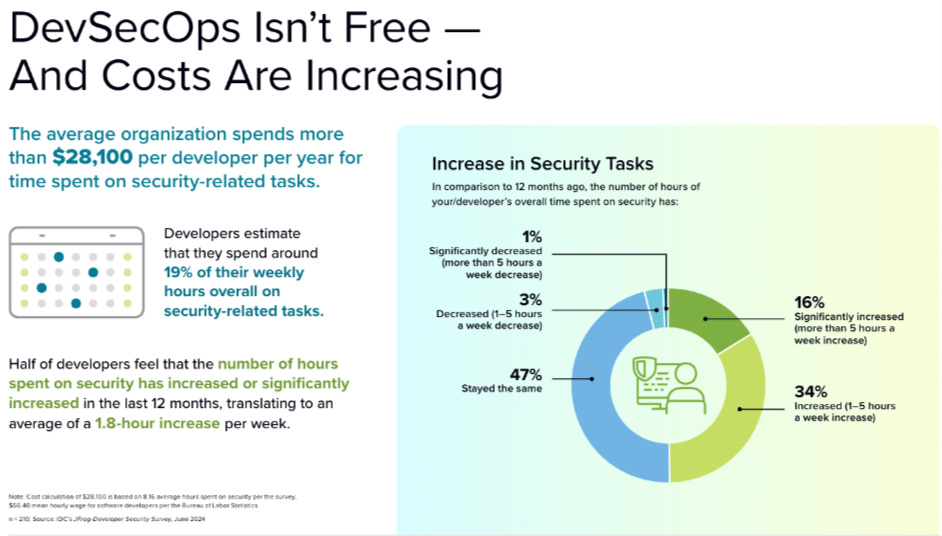
As much as we may try and frame it otherwise, the reality is that implementing security is similar to paying a tax. A cost of doing business, securely. This report from IDC by Katie Norton and Jim Mercer is insightful, showing the business impact of Developer time spent on "DevSecOps".
- They show the average organizations spends more than $28,100 𝗣𝗘𝗥 𝗱𝗲𝘃𝗲𝗹𝗼𝗽𝗲𝗿 per year for security tasks.
- Developer estimate 𝟭𝟵% of their weekly hours are spent on security-related tasks.
- Developers estimate the number of hours spent on security has increased by nearly 𝟮 𝗵𝗼𝘂𝗿𝘀 per week in the past year
These sort of insights highlight several key needs:
- Security absolutely 𝗠𝗨𝗦𝗧 be making use of innovative modern tooling that cuts down the noise and toil (aka the Developer Tax)
- This security burden is literally taking a toll on Developers, with them spending several hours 𝗢𝗨𝗧𝗦𝗜𝗗𝗘 of working hours dealing with security issues, increasing burnout, dissatisfaction and turnover. Knowing security isn't free, the question becomes, who is going to pay for it?
Are customers willing to pay 20% more?
As businesses see the increased cost of security, coupled with data showing incidents, breaches and so on have limited actual impact on revenue, and share price - do we run the risk of losing buy in for security, without regulatory forces driving it to fruition?
Federal Zero Trust Data Security Guide
The U.S. Federal ecosystem has been on a Zero Trust journey the last several years. Starting with the Cyber Executive Order (Cyber EO) and building on it with efforts such as the Federal Zero Trust Strategy and CISA Zero Trust Maturity Model.
This week they published the Federal Zero Trust Data Security Guide, published by the Zero Trust Data Security Working Group, which ties to OMB Memo M-22-09. It covers data security issues that are relevant to the implementation of ZT requirements.
The guide has key sections and chapters, such as:
Connecting the Dots Between Zero Trust and Data
Defining the Data, including activities such as defining data assets, beginning a data catalog and inventory and defining roles and responsibilities
Securing the Data, including activities such as data security controls, ICAM, monitoring and dealing with third-party risks
Risk Appetite and Risk Tolerance - A Practice Approach
We often hear about the concepts of Risk Tolerance and/or Risk Appetite in Cybersecurity. However, they are often broadly defined and even more so, difficult for organizations to go about implementing in any formal way.
This article from the always insightful Phil Venables discusses the concepts as well as key definitions from industry frameworks and organizations such as ISO, ISACA and COSO.
Phil discusses key steps such as defining the enterprise risk management framework and develop an agreed upon risk taxonomy. From there you begin to actually establish risk limits and thresholds. These may be financial losses, vulnerability resolution SLO’s or specific business resilience goals such as RTO/RPO’s. There are of course policy deviations, which Phil touches on as well.
Inside a Firewall Vendor’s 5 Year War with the Chinese Hackers Hijacking Its Devices
This is a really fascinating piece from Wired discussing how security vendor Sophos has been dealing with a multi-year battle of being targeted by Chinese malicious actors looking to compromise their devices and products.
The piece further shines a light on the fact that security products are part of the attack surface, and often an enticing one for attackers given they generally have privileged access, and can undermine an organizations defenses.
A quote from the article states:
“For more than five years, the UK cybersecurity firm Sophos engaged in a cat-and-mouse game with one loosely connected team of adversaries who targeted its firewalls. The company went so far as to track down and monitor the specific devices on which the hackers were testing their intrusion techniques, surveil the hackers at work, and ultimately trace that focused, years-long exploitation effort to a single network of vulnerability researchers in Chengdu, China.”
Wiz Eyeing Dazz Acquisition in Deal Worth Hundreds of Millions
This week news broke that industry cloud security leader Wiz may be eyeing an acquisition of Dazz. Dazz positions themselves as a unified remediation platform “providing visibility across all detection tools and environments, including code, cloud, application and infrastructure” with an emphasis on driving down meantime-to-remediation (MTTR).
This also further heats up discussions around Application Security Posture Management (ASPM), which has been a hot topic in the AppSec space as organizations look to improve VulnMgt in the era of modern cloud-native Applications. I wrote an extensive ASPM piece earlier this year titled “The Rise of Application Security Posture Management (ASPM) Platforms”, which I co-authored with Francis Odum of The Software Analyst publication on Substack.
There are also ties between Wiz and Dazz in the sense that both teams have founders with a past at Microsoft. Wiz’s CEO Assaf Rappaport was a lead for Microsoft’s Cloud Security Group and Dazz’s founder Bahat previously was the Deputy CEO of Microsoft’s R&D Center.
AI
OWASP Expands Guidance, Announcing Several New Publications
By now it should come as no surprise I’m a fan of OWASP when it comes to their AI Security publications and guidance.
In the past I’ve covered their efforts such as
This past week they announced several new key publications, including:
The Guide for Preparing and Responding to Deepfake Events - which addresses the threats of deepfakes and key ways organizations can prepare to deal with deepfake events.
The AI Security Center of Excellence Guide - much like the early days of Cloud, organizations are hustling to keep pace with the rapidly evolving technology of AI, GenAI and LLM’s. Some are beginning to consider standing up AI Centers of Excellence, to consolidate expertise, guidance, governance and more. This guide walks you through how to do just that.
The AI Security Solution landscape Guide - this publication helps readers understand the quickly expanding AI security vendor, product and solutions marketplace, looking at key use cases from LLM security to agentic AI security products.
The last guide in the list also provides a good overview of different models of GenAI use, from consumption to self-hosting as well as LLMOps.
Open-Source LLM Vulnerability Scanners
There is a lot of excitement about the potential for LLM’s and GenAI to improve cyber, including vulnerability scanning.
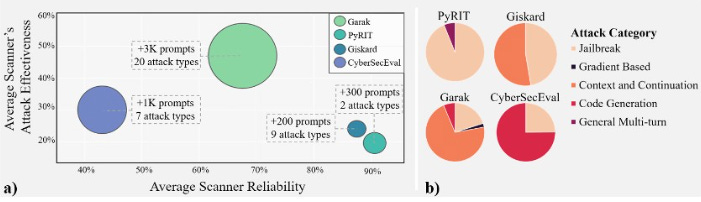
This is an interesting first of its kind report looking at Open Source LLM’s and their effectiveness related to various attack categories and vulnerability scanning.
It looks at four tools: PyRIT, Giskard, Garak and CyberSecEval
Utilizing hundreds of thousands of prompts across various attack types, such as Jailbreaks, Code Generation, Context and Continuation and more
Uses red-teaming processes to simulate adversarial attacks and potential LLM vulnerabilities
Provides recommendations for matching red-team scanners to organizational needs and use cases
It will be really interesting to watch both the tools and their use evolve, as well as the unique ways to exploit GenAI and LLM’s embedded in nearly all software and products as we move forward.
AI and Security
Many of us continue to be excited about the potential for AI and its intersection with Cyber. This includes Vijaya Kaza, who serves as the Chief Security Officer & Head of Engineering for Trust and Safety at Airbnb.
She recently took to LinkedIn to write a great article about the intersection of AI and Security, and the role AI may play in addressing longstanding cyber challenges. In this piece she discusses the potential of AI to address longstanding issues in cyber such as AppSec, VulnMgt, and third-party risks. These as she mentions have dedicated budgets and are well-defined market categories with large TAM’s.
She also discusses why securing AI is an important but smaller niche, and discusses how several aspects of AI has built-in security now, from existing infrastructure providers to internal software development.
Hands on LLM’s: Language Understanding and Generation
If you're like me, you've been learning a good bit about LLM's, Gen AI and AI more broadly.
That said, it generally is about different model deployment scenarios, key risks/considerations as well as diving into different security frameworks and guides from OWASP® Foundation, MITRE, National Institute of Standards and Technology (NIST) and others.
This book "Hands-On Large Language Models: Language Understanding and Generation" is definitely a bit more technical.
It goes into:
Understanding LLM's and key concepts such as tokens, embeddings and the underpinnings of LLM's and their architecture
Using Pre-Trained models and dealing with text classification, clustering, prompt engineering and RAG
Training and Fine-Tuning LLM's, including creating text embedding models, fine tuning models and driving tailored outputs and use cases
This is definitely a much deeper dive and is helping me understand the technical aspects of LLM's and GenAI beyond frameworks and high-level concepts around security.
AppSec, Vulnerability Management and Software Supply Chain Security
Resilient Cyber w/ Tyler Shields and James Berthoty - Is “Shift Left” Losing its Shine?
In this episode of Resilient Cyber I will be chatting with industry leaders Tyler Shields and James Berthoty on the topic of "Shift Left".
This includes the origins and early days of the shift left movement, as well as some of the current challenges, complaints and if the shift left movement is losing its shine.
We dive into a lot of topics such as:
Tyler and Jame’s high-level thoughts on shift left and where it may have went wrong or run into challenges
Tyler’s thoughts on the evolution of shift left over the last several decades from some of his early Pen Testing roles and working with early legacy applications before the age of Cloud, DevOps and Microservices
James’ perspective, having started in Cyber in the age of Cloud and how his entire career has come at shift left from a bit of a different perspective
The role that Vendors, VC’s and products play and why the industry only seems to come at this from the tool perspective
Where we think the industry is headed with similar efforts such as Secure-by-Design/Default and its potential as well as possible challenges
Comparing Static and Runtime Reachability
Reachability Analysis has become a hot topic in the AppSec space, with many vendors pointing out how critical it is to help drive down noise from tools, such as Software Composition Analysis (SCA) and help Developers focus on vulnerabilities that are actually reachable, and therefore pose real risks.
This is particularly true when we look at organizations struggling to keep up with exponentially expanding vulnerability backlogs, CVE’s growing by double digits in the NIST NVD YoY and Developers getting burnt out from Security “shifting left” and drowning them in noise.
This is an excellent piece from James Berthoty of Latio Tech who dives into reachability and compares Static vs. Runtime Reachability and some key differences.
Data Normalization Challenges and Mitigations in SBOM Processing
Software Bill of Materials (SBOM)’s continue to get attention in the conversation around software supply chain security. That said, not all of the attention has been good, as some question the current state and value of SBOM’s as well as challenges around data quality.
This paper from MITRE discusses some of the data normalization challenges with SBOM’s, and how to mitigate those challenges with a core focus on FDA policy and medical devices.