Prevention is Ideal but Detection and Response is a Must: Introducing Wiz Defend
A look at Wiz Defend and Cloud Detection and Response (CDR)
The widely used NIST Cybersecurity Framework (CSF) involves activities such as Identify and Protect, which are key to securing digital environments and preventing incidents. However, as the saying in cybersecurity goes, it is not a matter of “if” an incident occurs but “when.” That’s why the additional functions of Detect, Respond, and Recover are key.
That said, when we often look at the cloud security landscape, there is a big emphasis on the ability to identify and protect environments, looking to prevent incidents, with activities such as Cloud Security Posture Management (CSPM), vulnerability scanning, identifying misconfigurations and other activities often associated with shifting security “left” in the SDLC.
And for good reason, we know ideally we want to identify misconfigurations and vulnerabilities before they reach production and can be exploited. However, that simply isn’t always possible, due to factors such as the number of potential misconfigurations, vulnerabilities, the role of zero days, and more.
In fact, CISA’s latest report titled “2023 Top Routinely Exploited Vulnerabilities” found that the majority of the most frequently exploited vulnerabilities were initially exploited as a zero-day, meaning they are vulnerabilities that were unknown to the vendor at the time of their exploitation. This further emphasizes the importance of having robust tooling and capabilities to detect and respond to security incidents when they occur in your cloud environments.
That’s why it is exciting to see the industry leader in cloud security, Wiz, add to their already impressive Cloud Native Application Protection Platform (CNAPP) with the announcement of Wiz Defend, which we will take a look at in this article.
Where it all began
Over two years ago, Wiz began its push into the threat detection space, with their early initial Cloud Detection and Response (CDR) offering. However, through engaging with customers they learned from SecOps teams in particular that they needed to expand their capabilities and help rethink and optimize workflows for detection when it came to cloud-native environments.
Wiz’s push into Cloud Detection and Response continued with its acquisition of Gem in early 2024. This team brought decades of experience in incident response, investigations, and dealing with thousands of high-profile breaches. Gem was able to help Wiz pursue its goal of building and delivering a SecOps-first experience to respond to cloud attacks.
At the time of the acquisition, Wiz’s CEO Assaf Rappaport stated the move was aimed at “reinventing threat detection in the cloud” and it seems that they have done just that with the release of Wiz Defend. The move was also aimed at another industry trend, which is that of consolidation, looking to address the ever-growing challenge of cybersecurity tool sprawl.
As I have discussed in previous articles, the cybersecurity tool sprawl problem only seems to be getting worse, with surveys showing the average CISO and Security organization has 70-90 or even up to 130 security tools, and also stated they expect the security stack to grow even further.
This sprawl has become unmanageable for organizations, sapping scarce budgets, leading to cognitive overload for security teams, expanding the attack surface, since tools can also be vulnerable and most importantly, potentially adding more risk than they mitigate due to the previously mentioned problems.
Cloud Detection and Response is aimed at bringing Security Operations (SecOps) into the fold when it comes to cloud security. SecOps teams often utilize legacy tools that lack deep visibility and context of cloud environments or fail to account for the full SDLC, from code development to production workloads in the cloud (e.g. Code to Cloud). Additionally, Gem’s acquisition focused on continuously analyzing cloud activity in real-time to enable SecOps teams to address evolving and dynamic threats that aren’t captured when looking at static configurations, code, and repositories.
Perhaps most importantly, Gem’s founders and Wiz have emphasized a smooth integration of Gem’s capabilities into the Wiz platform, re-building the capabilities into Wiz from the ground up rather than stitching them together which often leads to poor user experience and insufficient organizational outcomes.
Wiz Defend
Wiz Defend introduces what they call the “cloud security operating model”, accounting for not just common cloud security targets such as Developers, Code, CI/CD, and vulnerabilities, but also runtime environments and organizational teams such as Security Operations (SecOps) and Incident Response (IR).
Wiz Code helps secure every stage of the SDLC focusing on improving visibility and preventing risks in code, pipelines, registries, and images. Wiz Cloud rallies around security posture, bringing an agentless approach to visibility and reduced attack surface.
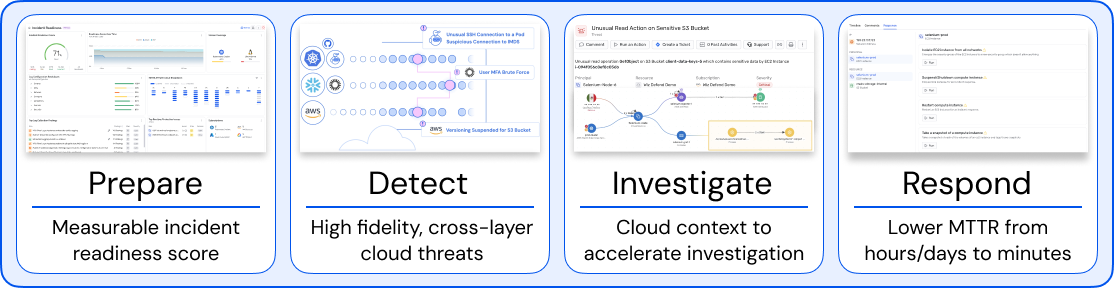
To round out the cloud security operating model, Wiz Defend focuses on cloud events and uses a lightweight eBPF-based sensor that looks to protect organizations from incidents and malicious activity as it unfolds, functioning as a last line of defense to both mitigate the impact of malicious activity, as well as provide critical insights needed for incident response, digital forensics, investigations, and recovery.
Wiz Defend empowers organizations to optimize their Cloud Detection and Response through a lifecycle of activities aligned with potentially malicious activity and incidents. This includes a focus on incident response readiness, by allowing organizations to assess their IR readiness contrasted against the popular MITRE ATT&CK Cloud Matrix. MITRE ATT&CK Cloud involves various phases of an attack lifecycle such as Initial Access, Execution, Credential Access, Exfiltration, and Impact, along with the specific techniques associated with each phase.
Defend enables SecOps teams to respond immediately and minimize the business impact of threats using their AI-based containment recommendations and one-click actions at both the control plane and process levels. Again going back to the SecOps focus, it also allows the creation of playbooks integrating with existing SOAR solutions and automating the collection of both workload and runtime forensic data.
Users can also get key readiness insights in critical areas such as log configurations, top findings, and more across multi-cloud environments and the 4Cs of Cloud Native (e.g. Cloud, Cluster, Container, and Code).
Prior to Wiz Defend, getting this sort of context around incident readiness, especially across multiple CSPs and hosting environments from a single platform has been elusive.
Breaking Down Silos and Context
The push for DevSecOps was theoretically supposed to break down silos that have long existed between Developers, Security, and Operations (e.g. DevSecOps). However, despite organizational efforts to bolster relationships between these teams, the reality is that these teams and personas often have to use different tooling to get visibility into activities and environments they are concerned with.
The same goes for teams within Security, as AppSec and SecOps tool stacks look different, often due to the vendor community building around aspects of those personas and the systems, environment, and findings they are concerned with. AppSec tooling often focuses on code repositories, CI/CD pipelines, and developer workflows. SecOps on the other hand is generally focused on runtime environments, where threats manifest impacting an organization's production workloads.
Wiz’s addition of Wiz Defend to their CNAPP product brings a unique full-lifecycle view from code, the underlying cloud environment, and production environments. This offers not only the opportunity to break down silos between teams and offer a single platform that appeals to each and all of these security personas but also the opportunity to bring unique context that breaks through the noise and toil that historically drowns organizations from security.
We know organizational vulnerability backlogs have ballooned, to hundreds of thousands and even millions in large complex environments. This is partly due to the incredible double-digit year-over-year (YoY) growth of CVEs, as seen below. I discussed this extensively in my article “Vulnerability Exploitation in the Wild”.
Source: Cyentia Institute: A Visual Exploration of Exploits in the Wild
The vulnerabilities continue to proliferate faster than teams can remediate them, driving a critical need for context, or in short, focusing on the vulnerabilities that matter. Wiz’s ability to piece together context from Wiz Code, Cloud, and Defend offers that, by allowing you to see not just vulnerabilities in code, and underlying cloud environments but couple it with cloud events and sensors providing real-time threat insights.
While “shift-left” has been a noble endeavor and logically makes sense when it comes to identifying and remediating vulnerabilities before they reach production, the reality is that there are often simply too many for organizations to address without grinding developer velocity to a halt.
Also as discussed above with CISA’s 2023 Most Exploited Vulnerabilities, zero days are most often at play, so we’re realizing runtime context is critical - which is why Wiz Defend is so timely, with its use of eBPF sensors to provide context, facilitating what is now being called Cloud Detection and Response (CDR) or Application Detection and Response (ADR) by the community.
The key distinction here is that while CDR/ADR vendors are available, they require standalone products to cover the SDLC and “left” in the developer workflow or security stack. Wiz’s platform brings you all of it, in one, again leaning into the mantra of consolidation, cost savings, and most critically for security - context.
This context is brought to bear via not just Wiz Code and Cloud but also Wiz Defend’s deep insights and visibility into incident readiness. Not only readiness but investigation and forensics as well. It’s often quipped “Defenders think in lists, attackers think in graphs”. Wiz has long been successful and known for their innovative graph-based approach to their platform, and the same is being implemented now for Wiz Defend, with capabilities such as “Investigation Graphs”, as seen below, which can show you the origination of malicious activity, it’s the source (e.g. IP), your resources it initially interacted with, the activities performed and ultimately the impact to your organization. All of which can then be summarized into detailed investigative reports with Wiz AskAI.
Wiz Defend couples not just their security graph and cloud-native signals data lake but the addition of Wiz Sensor to enable a powerful detection engine, contextualized triage, and containment and response capability for SecOps practitioners. This can be used proactively for activities such as Threat Hunting but arguably most importantly, triage-wise for post-incident activity, such as containment to limit the blast radius to the organization, and to thoroughly conduct forensics across impacted workloads and environments.
Metrics That Matter
When it comes to SecOps, metrics that matter are important. While common cloud security tools may provide insights into findings relevant to developer workflows, code, and the SDLC such as dependencies, vulnerabilities, and more, Wiz Defend brings all of those developer-centric metrics to bear with Wiz Code and Cloud but couples it with key metrics for SecOps professionals as well.
This includes identifying threats by severity, as well as rules associated with various threats ranging from secret exposure, exposed storage buckets, insecure network configurations, and real-time suspicious activity associated with running production workloads.
Wiz Defend users can bolster their incident readiness score, both individually across CSPs and in aggregate across their entire cloud footprint. They can examine their meantime-to-remediation (MTTR) over time, a critical metric demonstrating how quickly organizations address threats and overall impact to their organization.
Wiz Defend users can not only curate custom threat rules based on their organization, sector, risk profile, and threat intelligence but they can lean into Wiz-curated threat rules. These are provided out of the box, building on Wiz’s industry-leading Cloud Threat Landscape, which is a comprehensive threat intelligence database of cloud security incidents, threat actors, tools, techniques, and procedures (TTP).
Reinventing Threat Detection and Response in the Cloud
As mentioned at the opening of this article, Wiz set out to reinvent threat detection and response in the cloud through their acquisition of Gem. Now they’ve done just that with a ground-up integration of cloud-native threat detection and response capabilities into an already industry-leading cloud and code security CNAPP product.
This includes a comprehensive approach to help organizations prepare for incident response readiness, detect both known and unknown threats such as zero days, and lastly, be able to investigate and respond to incidents when they do occur. All of this is facilitated with unparalleled visibility and context from the first line of code through workloads running in production environments, bringing SecOps practitioners long-needed capabilities when it comes to cloud detection and response.
Excited to learn more about Cloud Detection and Response (CDR)?
Grab a FREE copy of this Practical Guide to CDR from Wiz!
Cloud Detection and Response (CDR) tools are purpose-built to help organizations detect, investigate, and respond to threats in cloud environments, but traditional security tools (like SIEM and EDR) fall short in addressing the complexities and scale of cloud infrastructure.
CDR solutions are designed to handle cloud-native threats by providing complete detection coverage, context, and automated responses, making it a necessary tool for any SecOps team.
This practical guide covers:
· Introduction to CDR
· Why SecOps teams need CDR
· Why traditional SecOps tools fall short
· How CDR Benefits the business
· How CDR fits into the SOC workflow
· Core capabilities of CDR solutions