You're Vulnerable - And Malicious Actors Know It
A look at recent research from Rezilion on malicious actors targeting KEV's
Last week we took a look at a recent report from Vulnerability Management firm Qualys that demonstrated that less than 1% of all known vulnerabilities in 2022, historically throughout NVD’s CVE history a similarly small number of vulnerabilities are actually exploited. For example, in 2021 Kenna Security pointed out that just 2.6% of the 18,000 CVE’s tracked in 2019 were ever actually exploited.
One thing that I thought was cool was the President and CEO of Qualys, Sumedh Thakar commented on my article/LinkedIn post, which can be found here. He touches on the need for automated vulnerability remediation and mitigation to address the speed asymmetry between Defenders patching vulnerabilities, and Malicious Actors exploiting them.
Sumedh of course is referring to the exploitation window between how long it takes organizations to remediate vulnerabilities (if ever, note the 57.7% figure), compared to how quickly malicious actors weaponize the vulnerabilities. This is of course supported by the Rezilion research we discuss below that show malicious actors exploiting vulnerabilities that are several years old, have a patch available, and still aren’t being remediated by defenders.
Source: Qualys 2023 TRURISK Threat Report
My article last week discussed the toil that the legacy CVSS-centric approach of vulnerability management imposes on Developers and the friction it causes between Developers and Security teams and runs contrary for pushes to enable software velocity. CVSS misuse has been discussed elsewhere as well, such as in Carnegie Mellon’s Software Engineering Institute (SEI) “Towards Improving CVSS” report.
This week, we will be taking a look at a report from security researchers at Cybersecurity firm Rezilion titled “Do You Know KEV? You Should (Because Hackers Do)!”
To publish their report, Rezilion leveraged the U.S. Cybersecurity Infrastructure & Security Agency (CISA)’s Known Exploited Vulnerability (KEV) catalog.
For those unfamiliar with it, I will provide a brief recap below, but much more can be found in my article “CISA’s Take On Vulnerability Prioritization”, which covers not just KEV, but also other vulnerability resources such as the Stakeholder Specific Vulnerability Categorization (SSCV), Vulnerability Exploitability eXchange (VEX), and the Common Security Advisory Framework (CSAF). For those wanting to dive into not just KEV but those topics, please find that article here.
CISA KEV Primer
CISA has curated and published a Known Exploited Vulnerabilities (KEV) Catalog and mandated through a Binding Operational Directive (BOD) that Federal agencies remediate KEV’s and recommends that commercial organizations do the same if they are impacted by these KEV’s.
This KEV is published as a webpage but also as a CSV and JSON file. Organizations and individuals can also subscribe to the KEV catalog update bulletin which delivers email notifications when new KEV’s are added to the catalog.
The criteria for vulnerabilities to make it into the KEV catalog include that they have a Common Vulnerabilities & Enumerations (CVE) ID assigned, and are actively being exploited in the wild based on reliable evidence and that there is clear remediation guidance for the vulnerabilities, such as vendor provided patches or updates.
The CVE program is sponsored by CISA but run by the Federally Funded Research and Development (FFRDC) MITRE. The CVE program aims to identify, define and catalog publicly disclosed vulnerabilities. CVE ID’s are assigned by CVE Numbering Authorities and have three potential status,’ which are Reserved, Published and Rejected.
On the actively being exploited front, CISA’s KEV catalog does not use exploitability itself as criteria for inclusion in the catalog, but instead there is reliable evidence that the vulnerability either has attempted or successful exploitation.
For example, there may be evidence that a malicious actor tried to execute code on a target but failed or merely did so on a honeypot system, aimed at exposing malicious activity. Unlike attempted exploitation, successful exploitation means a malicious actor successfully exploited vulnerable code on a target system thus allowing them to perform unauthorized actions of some sort on the system or network.
CISA is careful to point out that Proof of Concept (PoC) exploits do not make it to the KEV catalog, given that while a researcher may have shown something could be exploited, there is no evidence that it has been, or even was attempted to be exploited in the wild.
The third criterion for KEV catalog inclusion is clear remediation guidance. This means that there are clear actions organizations can take to remediate the risk of the KEV. These could be actions such as applying vendor updates or in potential dire situations, removing the impacted product from the network entirely if there is either not an update available or the product is end-of-life and simply no longer being updated or supported.
CISA also acknowledges that in the absence of relevant updates and patches organizations often will seek to implement mitigations to prevent a vulnerability from being exploited or workarounds, which are manual changes to protect a vulnerable system from exploitation until patches are available.
Rezilion’s Findings
Now that we have an understanding of what the CISA KEV is and how vulnerabilities make it to the list, let’s take a look at Rezilion’s report.
Rezilion found that over 15 million public facing instances were susceptible to vulnerabilities from the KEV catalog. These included virtual machines, containers, services and other forms of digital environments and systems.
Their report took a look at the vulnerabilities in the CISA KEV catalog as well as activities by Advanced Persistent Threats (APT)’s (such as Nation States like Russia, Iran, China and North Korea) to exploit them.
The research was conducted using GreyNoise and resources such as Shodan to check the attack surface of public facing instances on the Internet. For those unfamiliar, GreyNoise passively collects packets from hundreds of thousands of IP’s scanning the Internet to understand exploitation attempts and Shodan is a search engine for Internet-connected devices.
Rezilion points out that the CISA KEV only represents less than 1% of the total vulnerabilities that get discovered each year and make it into the NVD with assigned CVE ID’s.
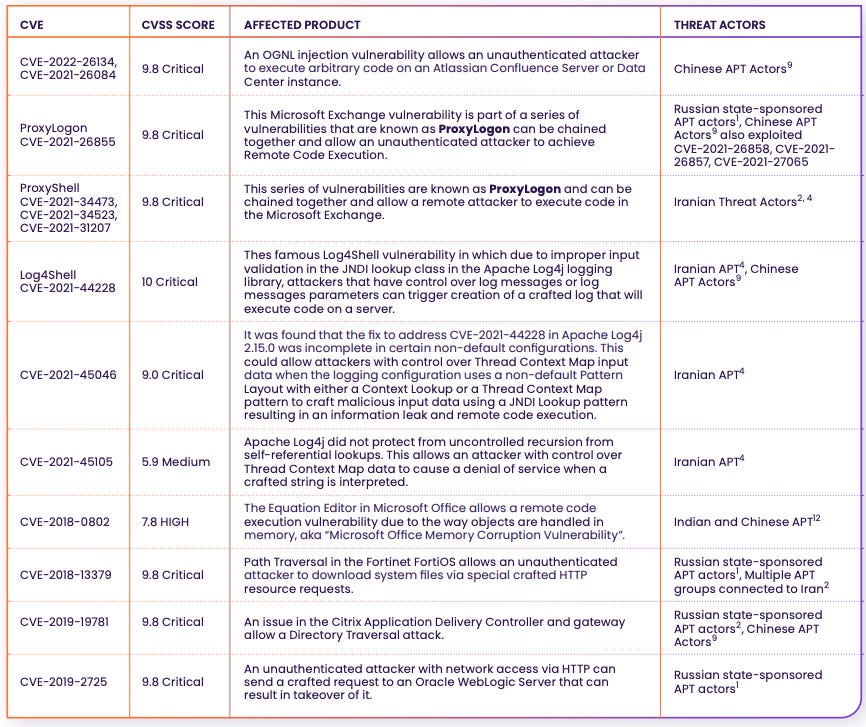
Rezilion’s report goes on to point out several examples of notable Nation State Threat Actors actively trying to exploit these known vulnerabilities, along with their CVE ID, CVSS Score and the impacted products. Below is a sample of the broader set of examples the Rezilion report highlights.
Using GreyNoise, Rezilion goes on to demonstrate that in just the last 30 days there has been over 1,000 identified attempts to exploit these known-exploited vulnerabilities.
Rezilion points out that these are the top 20 most vulnerable components or products that possess the most known exploited CVE’s. This is a complicated topic, since on one hand these may be the most known vulnerable products or components, they are also among the most widely used products in the world, garnering them outsized attention from researchers and malicious actors alike.
In this case we have a bit of an inverse of Linus’ Law, which states under enough eyeballs, all bugs are shallow, because the reality is, under enough eyeballs, all software and systems are vulnerable.
Another interesting thing to point out, but not dive into here, is the top listed vendor also is arguably one of the largest cybersecurity companies in the world now as well, boasting over $15 Billion USD in cybersecurity revenue.
Here is a great article that discusses Microsoft’s potential role as both an entity that is among the most vulnerable and exploited in the industry but also one of the largest cybersecurity providers, titled “The Microsoft paradox: Contributing to cyber threats and monetizing the cure”.
Rezilion recommends if you use these products (and just about everyone uses one or more of these), that you ensure they are patched and up-to-date.
To determine the extent to which publicly facing instances and systems are vulnerable to CVE’s from the CISA KEV catalog, Rezilion used Shodan to search for the presence of 200 CVE’s from the CISA KEV catalog.
They found over 15 million publicly access vulnerable instances, a snippet of which are displayed below
What is interesting is nearly half of these CVE’s are over 5 years old.
So we have multi-year old known exploited vulnerabilities just sitting on publicly accessible systems waiting to be compromised - what’s the worst that could happen?
One could ask why this would be, given it is so logical to think these should be patched given their exploitability, existing patch and how long they’ve been publicly known.
The reality is that many organizations are simply drowning in vulnerabilities, with no end in sight.
Another stellar recently released report from Rezilion and the Ponemon Institute (Rezilion must be up to something over there with all of these great reports) found that in a survey of over 600 IT/Security professionals, 66% said they have a backlog of more than 100,000 open vulnerabilities. The same report found that over 50% of security leaders admit they were able to patch less than 50% of their backlogged vulnerabilities.
As I shared this Rezilion study in a LinkedIn post, Yotam Perkal, Rezilion’s Director of Vulnerability Research commented and shared it, along with additional context. (Yotam will be joining us on the Resilient Cyber Podcast soon to dive into these topics, so keep an eye out for that!)
He pointed out that as the visibility into software increases (e.g. Software Transparency - ironically, the title of my book from Wiley, which you can find here), the number of vulnerabilities will only accelerate, along with noise, in terms of vulnerability data without context in terms of exploitability and real risk, but data that needs to be assessed nonetheless.
Yotam points out several other reasons the 15 million instances they identified with Shodan doesn’t tell the whole story, including:
Shodan only allowed them visibility into Internet/Public Facing instances and systems. Undoubtedly there are many more private and non-public facing systems which have CISA KEV’s present but simply couldn’t be picked up through their Shodan research. Anecdotally, I’ll say in my experience, organizations do indeed tend to prioritize hardening Internet-facing systems since the long held fallacy of the perimeter-based security model still persists strong in our industry. Despite John Kindervag’s 13 year old “No More Chewy Centers” paper, most organizations still cling heavily to their security perimeter and haven’t fully embraced or implemented a Zero Trust Architecture.
Some of the vulnerabilities in CISA’s KEV apply to non-public or Internet facing applications. For example, local privilege escalation vulnerabilities aren’t vulnerabilities that a tool like Shodan would identify, despite their existence on the system.
Rezilion took a conservative approach to the vulnerability counting. They didn’t count vulnerabilities where they couldn’t identify the specific vulnerable product versions. They also only counted non-duplicative high certainty results, despite many other findings being likely and probable.
Yotam concludes:
“Given this conservative calculation approach added to the fact that there are many CISA KEV vulnerabilities that can’t be identified with a high level of certainty (if at all) using Shodan, it is safe to assume that the actual number of vulnerable instances is much higher.”
The bottom line is that not just organizationally, but as an industry, our legacy approaches to Vulnerability Management simply aren’t scalable, efficient, effective or sustainable - we must mature.
This record growth of vulnerabilities is underway concurrent to organizations increased focus on digital transformation efforts and technology modernization with software now underpinning nearly all modern businesses and activities.
At this point most modern organizations are technology companies who happen to do “x” as their core competency to deliver value to customers and drive revenue, all of which is tied to their successful use and governance of technology.
It has long been quipped that “software is eating the world”, and it has, being tied to every aspect of society from leisurely entertainment activities and personal lives to our most critical infrastructure, government functions and national security systems.
This pervasive use of software and the complex interdependencies between not just the systems but the organizations and nations leveraging them has created a level of systemic risk that is nearly incalculable, and will impact nearly all of us in a variety of ways.
The uncomfortable truth is that the appetite and growth for software has come with a persistent and explosive state of vulnerable digital systems that are now pervasive in every aspect of our lives - and we aren’t able to keep up with the vulnerabilities, nor the malicious actors exploiting them.