Trust is key to any relationship, which is even more true in cybersecurity.
Trust assures organizations of the security of the vendors they engage with, the products they use, the business interactions they participate in, and more.
And, as they say, it is built in years and lost in seconds.
But what is the state of trust across the cybersecurity ecosystem? It can be hard to say.
That’s why I’m excited to dig into Vanta’s second annual State of Trust Report, which involves 2,500 IT and business leaders from the U.S. and abroad.
Key Findings
Before we discuss some of the specific findings and their implications for cybersecurity, let’s take a look at a snapshot of some of the reports key findings.
Several things are clear:
Businesses are viewing cybersecurity threats and risks at an all-time high, which isn’t surprising, as we see organizations continuing to pursue digital transformations and software powering most modern organizations and business interactions.
Supply chain incidents and attacks continue to ripple across the ecosystem, with nearly half of organizations stating their vendors have experienced a data breach, leading to nearly 7 hours a week being spent on reviewing vendor risk as part of supply chain and third-party risk management efforts
Manual legacy compliance processes and toil continue to eat into time that could be spent on more productive tasks. They take up nearly a quarter of the year, with 11 weeks spent on compliance tasks. I tried to highlight this problem in a recent article titled “GRC is Ripe for a Revolution: A look at why Governance, Risk, and Compliance lives in the dark ages and how it can be fixed.”
Compliance continues to be a strong signal of trust among customers, investors, and suppliers. It is one of the easiest and most public ways for organizations to communicate their cybersecurity commitments and provide evidence of the implementation of sound security practices.
State of Trust
Now that we’ve reviewed a high-level summary of key findings, let’s examine the report in more detail, focusing on the findings and their implications for the cyber ecosystem.
The report states that Cyber is the leading risk cited by businesses, with over 55% of organizations saying that cyber risks have never been higher, and half of the organizations stating they are detecting and responding to threats weekly. Couple that with nearly half of organizations dealing with incidents tied to their supply chain, and it is easy to see why trust is as paramount as ever in the cyber ecosystem.
Mitigating security risks requires dedicated investments, both financially and in terms of expertise and resources. While security budgets have climbed historically, many security leaders state in the report that they feel investments are not where they should be, with, on average, only 11% of a company’s IT budget being focused on security, and leaders stating it should be closer to 17%.
Another logical finding from the report is that as the organization’s size and complexity grow, so do its current and ideal security budget percentages. The larger an organization is, the more complex its architecture is, the more expansive its business interactions are, the broader its supply chain becomes, and the more cumbersome its compliance and regulatory requirements grow.
The AI “x” Factor
It’s clear that AI is and will forever change the state of cybersecurity and technology more broadly. Businesses are rapidly adopting AI, from self-hosting open-source LLMs to consuming AI SaaS-based services and integrating GenAI, LLMs, and AI capabilities into new and existing products and services.
The risks and concerns around AI are also notable, with organizations like the Cloud Security Alliance, OWASP, NIST, and others providing guidance, best practices, and recommendations to mitigate AI-related risks.
Thankfully, these concerns don’t seem to fall on deaf ears, as the survey showed that 62% of businesses plan to invest in AI security within the next year. That said, future investments don’t address current risks, and the survey found only 37% of organizations currently conduct AI risk assessments. This means adoption is rampant, but governance and security? Not so much, at least yet.
Regarding trust, safeguarding customer data is at the top of the list, with customers, consumers, and partners wanting to ensure their data is protected by those with access to it.
AI complicates this paradigm. The survey showed that only 25% of those training AI with customer data require the customer to opt in, and 75% do not even offer an option for customers to opt out, leaving customers little to no choice regarding having AI trained on their data.
Considering that nearly half of organizations have had an incident tied to a supplier or third party highlights the potential ramifications for data loss and exposure related to AI across the supply chain.
Compliance Analogs in a Digital Era
As I have written about previously, despite the technology industry moving towards DevOps, Agile, CI/CD, Containers, Automation, and Cloud, compliance largely lives in the analog era.
It is toiling away with static documentation, snapshot-in-time assessments, and cumbersome manual processes, failing to keep pace with the modern software development landscape or the environments and organizations it is supposed to provide trust assurances.
Vanta’s report highlights this problem, stating the compliance burden has never been higher, with organizations spending 11 working weeks in 2024 on compliance tasks, up a week from the prior year and hitting nearly 7 hours a given week throughout the year.
This isn’t surprising, as we see the rise of compliance from the framework sprawl of HIPAA, HITRUST, SOC2, FedRAMP, NIST, and DORA. The list goes on as the number of compliance frameworks and requirements grows, and organizations face increasing scrutiny from oversight organizations such as the SEC and comparable examples in the EU, in particular.
While many are holding their breath for regulatory harmonization, the reality is that the compliance landscape is only growing more, not less, complex and cumbersome. Put simply, the old ways of doing things manually aren’t scaling, and organizations need to lean into automation and purpose-built compliance platforms to streamline the toil and provide efficiencies and improved compliance and security outcomes.
This isn’t just speculative, either. The report found that 6 out of 10 organizations say automating the manual work of compliance is a priority, and many cite saving hours a week through automation of activities such as collecting documents and artifacts, updating regulators, answering security questionnaires, and more.
While these figures seem promising, there is still work to be done in getting business buy-in for compliance automation. 72% of IT decision-makers cited the potential for efficiencies and cost savings through compliance automation. In comparison, only 57% of business decision-makers said the same, highlighting a disconnect, likely from the IT staff living and dealing with the problem directly.
This means there is an opportunity for IT and Security leaders to evangelize the role of compliance modernization and automation with their business peers and build buy-in and resource commitments to help organizations achieve efficiency goals.
Supply Chain Complexity and Weak Links
The software supply chain is something that is top of mind for most organizations and is something I tried to highlight in my book “Software Transparency: Supply Chain Security in an Era of a Software-Driven Society.”
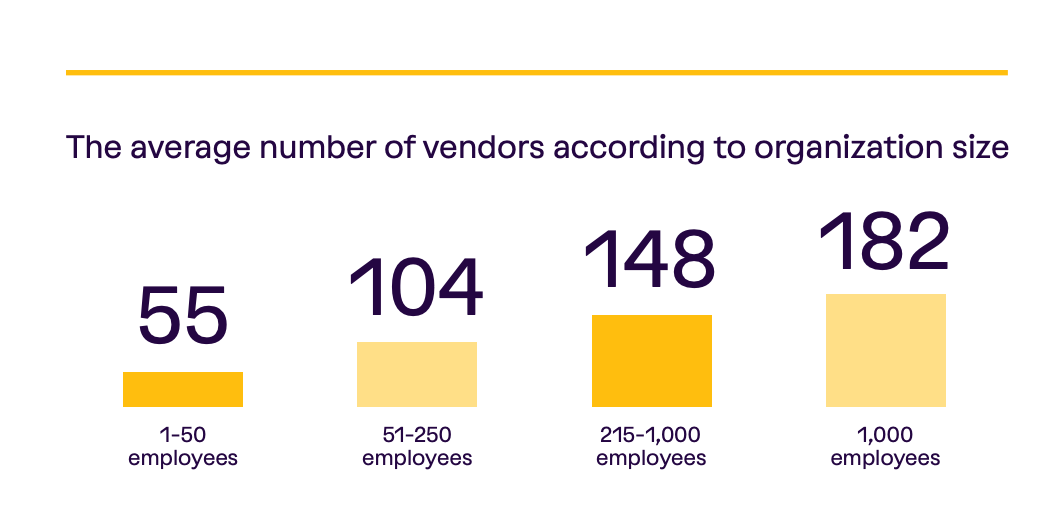
These supply chains continue to grow in complexity, with Vanta’s report finding that their third-party risk grows exponentially as organizations grow, not linearly. For example, organizations with over 1,000 employees have nearly 200 vendors to manage.
Going back to the metric discussed earlier, nearly half of an organization's vendors have had a data breach since they began working together or using their products. This means organizations aren’t only having to manage and govern hundreds of vendors. Still, they also need to deal with the fallout and ramifications of potentially tens to hundreds of security incidents tied to external vendors on a regular basis.
Organizations are taking steps to mitigate vendor and third-party risk by conducting security reviews, and half have even admitted they have terminated a vendor relationship due to a security concern. This emphasizes the importance of trust among organizations across the supply chain and the need to provide that trust and assurance to your customers and partners.
It also painfully points out the significant amount of time and energy needed to review the security of vendors and products the organization consumes, again pointing to the need for automation and compliance modernization.
Security is a Business Imperative
The metric above demonstrates that security concerns can lead to customer and revenue loss. Sound security is good for business and indeed makes security the business enabler we often like to think of it as.
More and more organizations are looking to compliance and assurances around security practices as a key signal to demonstrate trust, leading to positive business outcomes such as improved reputation, customer trust, and reduced financial risks.
One of the final major findings and takeaways from the report is that while organizations and security teams seem to be comfortable measuring their security programs impact in terms of compliance and audit outcomes or risk reductions, they are struggling to do so when it comes to business metrics such as return on security investment (ROSI) or customer revenue and retention, both of which are key to not just calling security a business enabler, but actually demonstrating it.
Again, this emphasizes the need for robust, capable compliance platforms that can not just automate and streamline compliance processes and burdens but directly demonstrate that value to executive and business peers across the organization, which can help facilitate the security budget increases that security leaders aim for.
To learn more about Vanta and how Vanta can help with your business needs, connect with a team member.
Closing Thoughts
While we in security like to bemoan the fact that “compliance doesn’t equal security,” compliance does, in fact, equal security and is one of the most dominant signals sought out by customers and regulators alike to demonstrate sound security practices and foster trust.
Trust is the currency that the entire cybersecurity ecosystem runs on, and establishing and maintaining it require dedicated commitments to regulatory requirements and, more than ever, modern, robust platforms to help demonstrate those commitments.