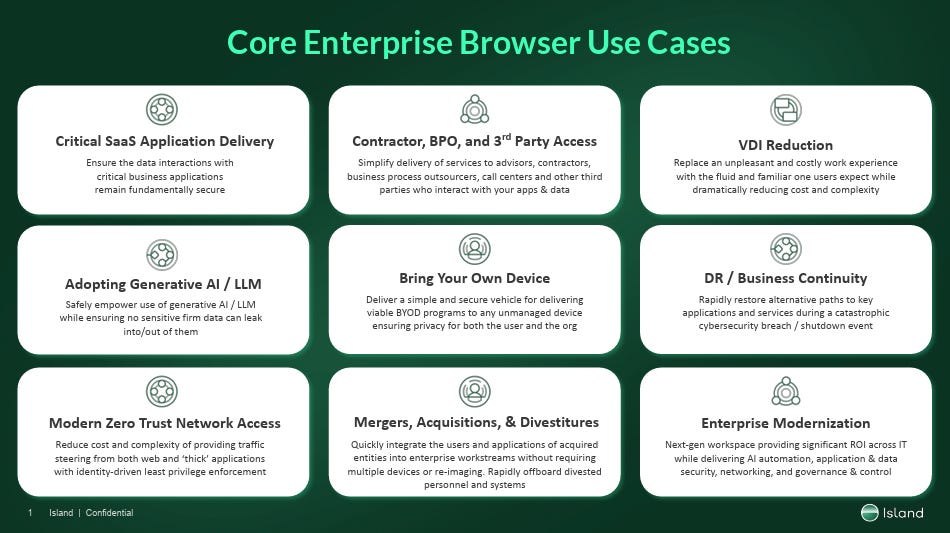
The Rise of the Enterprise Browser
Anyone and everyone who uses the web is familiar with the browser. It is as ubiquitous as the Internet itself, and its use is widespread. That said, many fail to draw a line between the concept of a consumer browser and one purpose-built for the enterprise.
In this piece, I will examine some of the key distinctions, specifically focusing on Island’s Enterprise Browser and its unique security capabilities compared to widely used consumer browsers such as Chrome and Edge.
By the end, you’ll likely be surprised just how versatile enterprise browsers are, why we need them when it comes to protecting corporate activities and reducing risk of data loss, and how a purpose-built enterprise browser not only has security advantages, but also the potential to help consolidate complicated security tech stacks for easier security governance and even cost savings.
What difference does it make?
First, you may be asking, what difference does it make?
Can’t we use common, widespread browsers such as Chrome, Edge, and Safari? You could, if you want to continue to allow unmitigated organizational risks.
It’s often quipped that “humans are the weakest link”, and while I disagree with that phrase, there is no denying that humans do generally introduce risk. From browsing the web, including untrusted sites, the opportunity to click on malicious links, exposing organizational data, and more. Ironically, we’re also entering a period where it isn’t just humans using browsers, but increasingly by AI agents via autonomous, agentic workflows as well.
Common attack vectors, such as phishing, remain among the most prevalent browser-based threats, alongside credential compromise, as malicious actors seek to exploit an individual’s credentials to access sensitive data, move laterally within environments, and perform other malicious actions.
We’ve also seen an uptick in malicious browser extensions, ransomware, and infostealers delivered via the browser, as well as unmanaged device risks, which have become increasingly commonplace, especially since 2021, with the rise of remote working and/or BYoD.
Employees, consultants, business partners, and others now use the browser as their primary mechanism for interacting with systems and data, much of which is sensitive, regulated, or valuable to the enterprise, and is essentially the primary target of malicious actors.
Enterprise users are accessing hundreds to thousands of SaaS applications, many of which are ungoverned or unsanctioned by organizational policy. They encounter phishing and malware, add potentially malicious extensions, share organizational data, and more, all via general-purpose consumer browsers that are not purpose-built for enterprise security.
This lack of secure design and implementation leads to the proliferation of numerous security tools and mechanisms, which further adds complexity, as discussed below.
Complexity is the Enemy of Security
Cybersecurity industry legend Bruce Schneier is often credited with the phrase:
“The worst enemy of security is complexity.”
And, it would be nearly impossible to argue that modern IT environments are anything but complex. This includes cybersecurity, where most security leaders and teams are drowning in security tool sprawl.
While estimates vary, some cite the number of security tools/products as between 70 and 90, while others say it is 130 or more, depending on the organization. This is a massive amount of security tools for any organization and team to manage, especially if they want to do it correctly in terms of fully implementing, tuning, optimizing, and configuring each bespoke security tool to drive down organizational risks.
Ironically, not only are many security tools operating as “shelfware”, with organizations not fully using their capabilities and capacity, but they also serve as an additional part of the attack surface, with malicious attackers now routinely targeting vulnerabilities in security products, especially given most of them have elevated permissions, access and the ability to understand the organizations most sensitive data and vulnerabilities. This is a topic I have written about extensively in an article titled “Your Security Tools May Be Making You Insecure”.
Many of these exact tools can be attributed to the lack of a secure enterprise browser, with organizations needing individual security tools to address factors such as critical SaaS and application access, BYOD and external contractor access, the protection of regulated data, safe browsing, zero-trust security, and now the use of GenAI.
Each gap can often be traced back to risks associated with consumer browser usage by organizational employees or external entities, such as contractors or third parties with access to enterprise data.
Additionally, many traditional security tools aren’t equipped to address modern cyber risks that reside in or through the browser. From extensive SaaS usage, much of which is ungoverned and unsanctioned, a lack of visibility at the network layer, and the rise of malicious extensions, traditional tooling falls short. We continue to see malicious actors targeting browser extensions as well, with many extensions having excessive permissions, inherent vulnerabilities, and a lack of user awareness regarding the granting of permissions to extensions.
These problems are being exacerbated with the rapid AI adoption wave the industry is experiencing, as well, much of which is accessed via the browser to external AI service providers. In fact, IBM’s latest 2025 Cost of a Data Breach Report focused heavily on the lack of AI oversight, finding 63% of organizations lack AI governance policies, and 20% of organizations surveyed cited experiencing a breach due to shadow AI, with shadow AI adding on average $200,000-$670,000 in costs to incidents compared to those that didn’t involve shadow AI.
Bringing security to the browser brings Secure-by-Design to reality, rather than just theory, and represents a paradigm shift from bolt-on products focused on the endpoint or network.
Is the browser you work on designed for work?
What if you no longer had to surround the browser with a whole stack of agents, proxies, and gateways, because the browser you used for work was actually designed for work?
This is Island, the Enterprise Browser. It naturally embeds your core security, IT, data controls, and productivity needs right into the workspace itself. Intelligent data boundaries keep data where it belongs, by design. Orgs have full visibility into everything happening at work. And users enjoy a fast, smooth, and even more productive browser experience.
Which is why many of the banks, hospitals, hotel chains, and airlines you can think of already run on Island. It may be one small change. But sometimes changing one thing, changes everything.
Enter the Enterprise Browser
We have extensively discussed the risks associated with consumer browser use in enterprise environments, as well as the complexity that arises from not having a purpose-built enterprise browser. It’s not that consumer browsers are bad; it’s just that they are built for a different purpose.
Now, let’s discuss some of the benefits of having an enterprise browser, including both security and efficiency, as well as potential cost savings.
There are several fundamental aspects of security and risk which get directly addressed by the use of an enterprise browser. For example, they can deliver inherent trust of the device, whether it is a corporate-owned and issued asset or a BYoD environment. From integration with corporate IDPs to continuous device posture assessment to policy-driven file system restrictions that prevent saving or printing data locally, and an enterprise browsing experience creates a secure enclave within which business apps and data remain safe.
Users’ tenancy is defined within the browser. It can be as granular as within separate tabs, truly allowing for the implementation of identity-driven zero trust at the browser and usage levels, as well as between corporate and personal usage within sites and web activities.
Additionally, sensitive data within and outside the browser can be encrypted, including cookies and cache, which often contain sensitive information or can be maliciously used in attack chain scenarios.
As we have discussed, the browser functions as the gateway between enterprise users, your organizational data, and the world.
Purpose-built enterprise browsers help meet the specific requirements of enterprises. From facilitating safe & secure browsing, meeting end-user privacy requirements, and ensuring secure configurations, all without compromising user experience or productivity, they avoid the need for users to work around security; instead, they work securely.
A great example, and the sponsor of this post, whose platform I have been incredibly impressed with, is Island. Island provides an industry-leading enterprise browser with robust capabilities to help tackle a diverse set of security challenges, all from a single platform.
Island allows for tenancy to be defined in the browser, or even in separate tabs, as I discussed above, enabling the segmentation of personal versus corporate web browsing and usage. This construct is known as an application boundary, which ensures that users can freely utilize personal resources without the risk of corporate data being compromised. This also eliminates the need for implicit trust in the underlying device, facilitating BYoD cultures, while not implicitly trusting even corporate-owned assets, which aligns with the principles of Zero Trust.
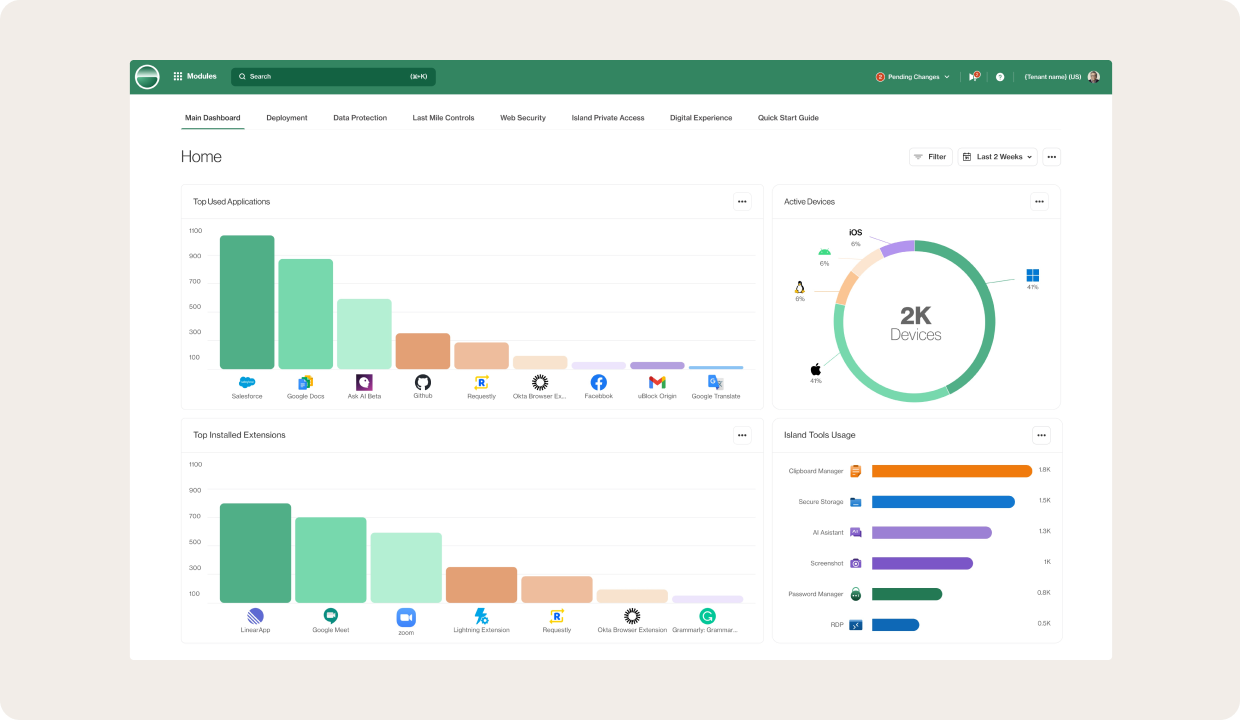
This is taken even further with the ability to control file downloads and usage based not only on group memberships or permissions, but also on context-based access control, such as geolocation, device posture, network, and more. You can also monitor top-used applications, installed extensions, active devices, and even tool usage.
It encrypts everything within and outside the browser, including cookies, cache, and sensitive user data related to their activities. Organizations can also create custom profiles within Island for users, which can be tied to organizational Identity Providers (IdP), or personal emails, and even facilitate temporary users or profiles, for cases such as contractors or short-term staff.
We also know users are routinely encountering malicious files, which Island can automatically scan for any potential malware before allowing users to save them either locally or to sanctioned organizational cloud storage environments. It can also ensure nothing lands on disks or local machines, such as when a user clicks on a phishing attack, malware, or unknown executable while browsing.
It isn’t just files that are malicious, either. As I discussed earlier, the rise of malicious extensions presents challenges, including a lack of user awareness around excessive permissions, inherent vulnerabilities, and even intentionally malicious extensions or those that have been compromised. Enterprise browsers, such as Island, can perform activities like extension risk scoring, extension management, and browser and workflow protections to mitigate the risks associated with browser extensions.
That said, as anyone who has been in security for some time knows, if we’re too restrictive, we either see users work around us, rather than with us, or face issues with adoption and collaboration. This is why Island allows organizations to define what types of files, content, and other elements can be used and under what circumstances. In fact, an organization can “say yes” to a variety of things they’d otherwise need to say no to, such as personal email, personal AI usage, etc.
Additionally, we may be concerned with insider threats or the exposure of sensitive data such as customer data, intellectual property, PII or regulated data, which is why I found it really promising that Island can also restrict where files can be saved, such as allowing them to be stored in corporate environments, but not downloaded locally, mitigating the risk of exfiltration or exposure, both from insider threats, but also potentially malicious actors who may have compromised a developer’s endpoint, which is a prevalent attack vector.
But scanning and restricting the download of files and data isn’t enough. Another common tactic is to take snippets or screenshots of sensitive data to store locally or obtain copies of it. This is why Island also prevents the movement of snipping or screenshots to the local system or to non-business websites, such as personal Gmail.
Speaking of regulated data, organizations may be dealing with frameworks such as HIPAA or CMMC, among others, which is why Island allows for sensitive data types to be redacted on the fly at the presentation layer, both obscuring them from the user and mitigating sensitive or regulated data risks for the organization.
One key concern among enterprise users is fears of an invasion of privacy or excessive oversight, which is why Island allows for limiting the monitoring of personal usage and sites into respective tabs to protect end-users’ privacy when warranted, while still protecting the organization’s data and adhering to security requirements, leading to both improved security outcomes and user experiences, which is key to broad adoption and usage.
That said, there are always exceptions to rules or policies, which is why Island also supports the ability to route requests to access sensitive data, run scripts, access unauthorized sites and more to organizational administrators, so they can be reviewed and approved as required, making organizational policies more than just static documents in a shared drive, but actionable extensions of the security requirements of an organizations, right through the browser.
We also know that organizations are undergoing significant transformations with the rise of AI, LLMs, and Agents. Many are now rushing to develop AI governance policies for approved usage, which is why Island supports the governance of specific LLMs and coding assistants based on organizational AI governance policies, making AI governance more actionable. Data protection guardrails can be enforced to ensure sensitive business data never leaks into public LLMs or restricted data is redacted from AI responses.
We’ve also observed a trend in specific cyber categories, such as AppSec, which focuses on runtime context and visibility. This shouldn’t be limited to internal development and applications, but should also be extended to user browsing. This is why Island supports a broad set of integrations, including leading IdPs, SIEM vendors, and more, providing detailed analytics that can be used for digital forensics and incident response by providing key insights such as a timeline of activities, user actions, site visits, keystrokes, and screenshots.
Extensions Have Their Place
An enterprise browser vendor like Island can offer both a full browser and an extension deployment option to meet organizations where they are in their security and deployment journeys. A full-featured enterprise browser delivers maximum protection, especially on unmanaged devices — providing IT and security teams with a seamless environment purpose-built for work.
It allows deep policy enforcement, full session telemetry, and protection that extends from the device to the app and user layer. However, not every enterprise is ready to replace its default browser entirely. For some, the path to adoption may require starting small—deploying an extension to existing browsers like Chrome or Edge to gain visibility or limited control before expanding to a full enterprise browser deployment.
Providing both options creates a natural adoption curve that fits diverse enterprise needs and infrastructures. The extension serves as a lightweight, low-friction entry point that integrates into current workflows while demonstrating the value of deeper control. Once organizations experience the benefits and identify use cases that demand more robust capabilities—such as handling sensitive data, application isolation, or advanced identity controls—they can seamlessly transition to the full enterprise browser.
In short, by offering both a full browser and an extension, a vendor like Island can maximize flexibility, accelerate adoption, and ensure its technology adapts to the organization’s pace rather than forcing a disruptive “all or nothing” approach. Any vendor should be able to demonstrate such a versatile approach; otherwise, it will not be comprehensive enough.
Closing Thoughts
Whether it is remote work, endpoint protection, software development, the software supply chain, SaaS consumption, GenAI usage, or other similar activities, nearly all modern enterprise activities occur through the web browser.
However, as I outlined in this article, there is a significant difference between enterprise browsing and an enterprise browser. The former is the front door to all sorts of potential attack vectors and organizational risks. At the same time, the latter is a purpose-built platform that offers cost savings, consolidates security tools, and serves as the front line of defense for the modern risk landscape.
Organizations are increasingly aware of the reality that commercial browsers, which weren’t designed for enterprise-grade security, pose a vulnerability in their security posture. This is why we are seeing the rise of the Enterprise Browser.