The 2025 Open Source Security Landscape
Open source continues to be pervasive, as are risks with its use being poorly governed and maintained
I have written articles covering Synopsis/Black Duck’s Open Source Security and Risk Analysis Report (OSSRA) for the past two years. I have found it to be one of the better reports on the state of open source software (OSS) security and one that is widely cited, especially regarding how pervasive OSS is in code bases and some of the challenges it brings.
This year is no different, and they just dropped their 2025 OSSRA report, so let’s look at some of the key findings.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 30,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Exploding Attack Surface
One key highlight from the report is that the size and scope of the software supply chain and attack surface continue to expand rapidly, largely led by OSS. As shown below, 97% of codebases contain OSS; on average, 70% of the entire codebase is OSS. There are 911 components per application, and 64% of those are transitive rather than direct dependencies.
What is wild is that while we know OSS is pervasive and widely used, the number of OSS files in the average application has grown threefold in the last three years alone to more than 16,000.
This emphasizes the importance of governance when it comes to understanding what OSS components your applications and organization more broadly are using, from where, what vulnerabilities and risks those components have, and establishing a process to govern the ingestion and use of those components, especially given the backdrop of continues attacks on the OSS ecosystem, to take advantage of its massive footprint, and also organizations poor governance and visibility of what they’re using.
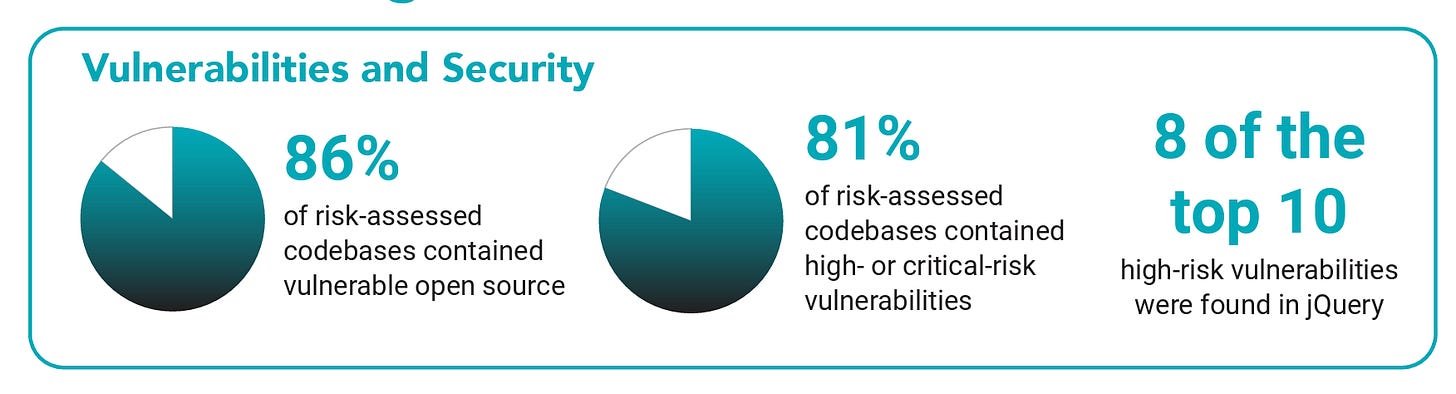
It isn’t just the OSS components that are pervasive and expanding, but in tandem, vulnerabilities and security risks also abound. They found that 86% of the codebases contain vulnerable OSS, and 81% contain high or critical vulnerabilities. While it doesn’t expand on how those severity ratings are derived, I assume it is likely CVSS base scores.
Given the massive number of components and high vulnerability counts, this further emphasizes, in my opinion, why prioritization around factors such as known exploitation, exploitability, and reachability, coupled with organizational context, is key.
It isn’t just a single vulnerability either; as we see above, it is hundreds on average and, in extreme cases, thousands. Being able to navigate which of these hundreds or thousands of vulnerabilities in your open-source components truly present risk and need to be addressed is paramount.
Software Ages Like Milk (Still)
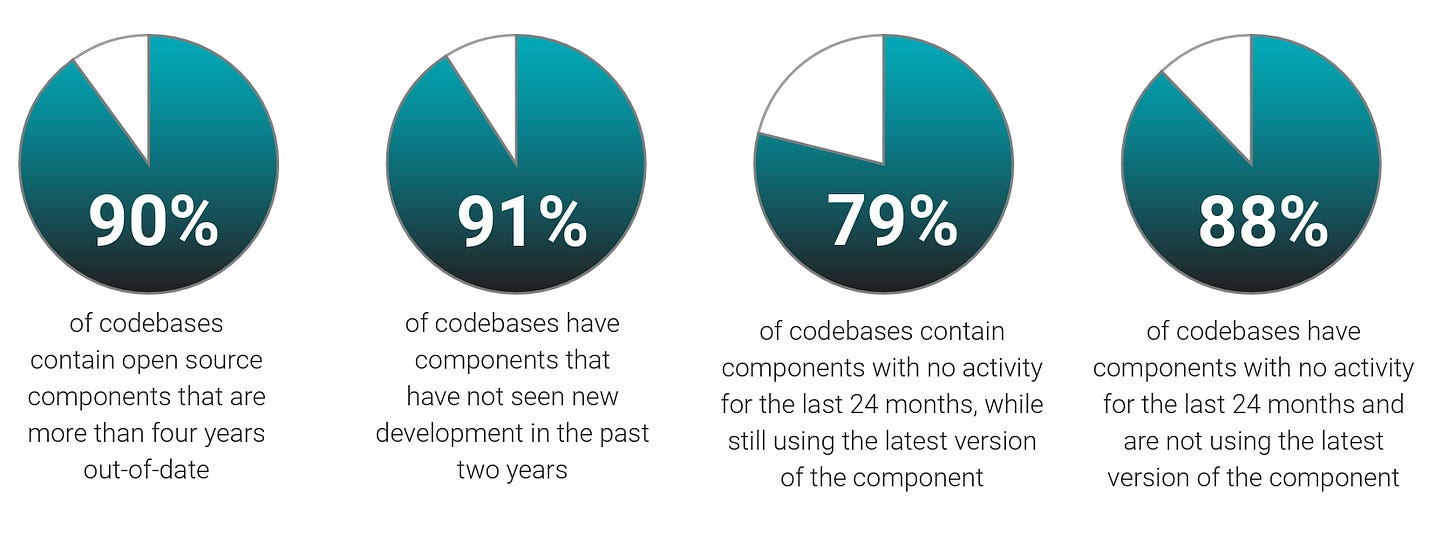
It’s often quipped that software ages like milk, which continues to be the case from the OSSRA report. As seen below, there are significant maintenance and operational risks. This includes 91% of codebases having outdated OSS components and 90% of all codebases containing components that are more than 10 versions behind the most current version.
Not only are organizations struggling with governing the overall ingestion and use of OSS, but once embedded into applications and systems, they struggle terribly to keep it maintained and updated, opening themselves to further risks around disruption, security incidents, and more.
The OSSRA goes on to discuss that it isn’t that organizations are struggling to update and maintain the components they use. Still, they often rely on components that haven’t seen new development in years.
They found that 91% of codebases have components that haven’t seen new development in years, meaning these components and their associated projects are often no longer active. They may have undiscovered vulnerabilities or unpatched security flaws.
79% of the codebases have components with no activity for 2 years and 88% have components with no activity in 2 years. They aren’t using the latest version of the component, adding additional risks.
This means that even when there is a more recent version, organizations often don’t use it, leaving them vulnerable to fixed flaws or security patches that address vulnerabilities.
Closing Thoughts
Not a long piece on this one, as the problems discussed, are well-known and have been reported in previous OSSRA reports. That said, they continue to get worse as organizations continue to take advantage of OSS while either willfully or ignorantly neglecting the fundamental aspects of governing and securing their OSS consumption.
Attackers are well aware of this by now, which is why we continue to see attacks on the open-source ecosystem to capitalize on this lack of governance and security in nearly all codebases and applications, including those in critical infrastructure and national security systems.
The tragedy of the digital commons is playing out right in front of our eyes.