Software Supply Chain Attack Types
Understanding the variety of malicious activity options in the software supply chain
The modern software supply chain is incredibly complex, making it difficult to understand the variety of attack methods threat actors can use. Discussing the variety of attacks and using examples can be helpful. In this article we will discuss some resources that help organize the variety of attack types and touch on some example scenarios and activities that may be involved.
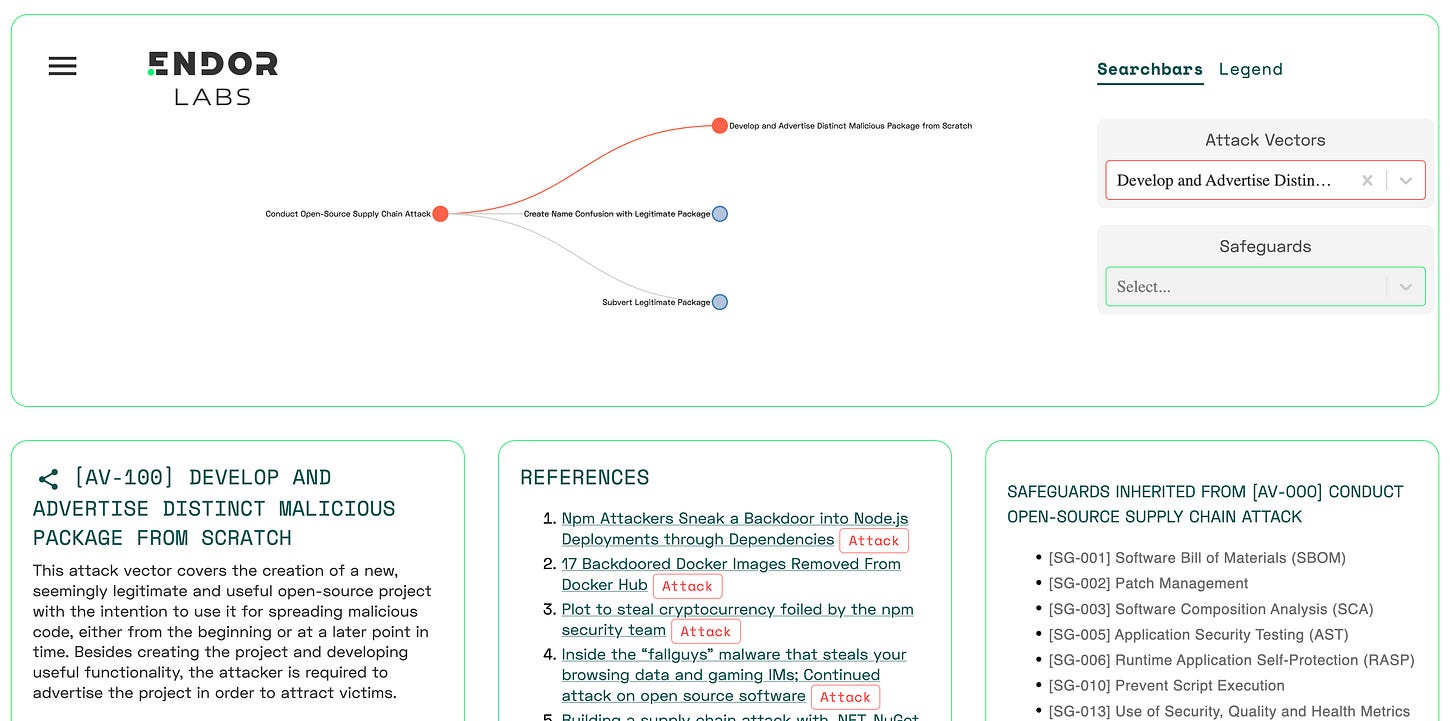
A couple of notable resources include the recently published “Taxonomy of Attacks on Open-Source Software Supply Chains”. This research publication covers 107 attack vectors across 94 real-world incidents and maps them to 33 mitigating safeguards. It involved user surveys of 17 domain experts and 34 software developers. It is an incredibly rich resource and read, but also dense in detail, which may be appealing depending on your role and interest.
A great tool to use to help visualize the variety of attack vectors and correlating safeguards is the “Risk Explorer” which builds on work from SAP Security Research and was recently announced and shared by Endor Labs, which you can play with for free, here.
Another excellent read on the topic is the paper released by folks from In-Q-Tel titled “For Good Measure Counting Broken Links: A Quant’s View of Software Supply Chain Security”. This whitepaper discusses the rapid increase in software supply chain attacks as well as applies some categorization to help organize them.
While these are some great resources on the topic, for the purpose of this article we will use CNCF’s catalog of software supply chain compromises also includes an index defining the several types of attacks that can occur. We will be discussing those attack types to have a shared lexicon of some of the primary attack vectors in the software supply chain. The index of attack types includes:
Dev Tooling
Negligence
Publishing Infrastructure
Source Code
Trust and Signing
Malicious Maintainer
Attack Chaining
It is worth noting that several of the attack types map to existing frameworks such as MITRE’s ATT&CK which has sections dedicated to Supply Chain Compromise, including software dependencies, development tooling and the software supply chain itself.
Developer Tooling
Developer tooling attacks are a compromise of the tools utilized to facilitate software development. This may be the developers end device, software development toolkits (SDK)’s, and toolchains. MITRE recommends utilizing integrity checking mechanisms such as has validation and scanning downloads for malicious signatures. If a malicious actor can compromise dev tooling, they are able to introduce potentially malicious code from the onset of the SDLC and tarnish all subsequent application development activities and consumers. This also puts the safeguards and posture of the developers endpoint and associated development environments in the crosshairs and emphasizes the need for organizations to secure them appropriately.
Negligence
Negligence is a failure to adhere to best practices, which is common, given there are so many applications security best practices to be cognizant of and we live in an increasingly complex digital ecosystem. Something as simple as neglecting to verify the dependency name can have a major impact on an organization. Malicious actors have increasingly been utilizing an attack method known as “Typo Squatting,” which takes advantage of lack of attention to detail of dependency names. Attackers typically will target a popular framework or library, add their malicious code under a similar name as the original library and then wait for unsuspecting victims to download and utilize it in their applications. In this case, the attack shifts from a push oriented approach to a pull, where the unsuspecting victim pulls malicious code into their infrastructure and organization. Given the well known problems with dependency management, often referred to as “dependency hell” it is easy to see how easily it could be to begin using a compromised dependency, especially if you have a first party dependency with a malicious transitive dependency associated with it.
Publishing Infrastructure
Publishing infrastructure has become increasingly critical as organizations now commonly utilize Continuous Integration/Continuous Delivery (CI/CD) pipelines and platforms to deliver software artifacts. One mitigation technique includes code signing, which helps ensure the integrity of the published code. However, as we have seen in cases such as SolarWinds, a compromise of the CI/CD infrastructure itself can allow malicious actors to legitimately sign software artifacts which presents them as trusted to downstream consumers. This attack method can be devastating and nefarious and it emphasizes why the publishing infrastructure must be secured like production environments are and aligns with emerging frameworks such as SLSA which we will touch on in upcoming chapters. Other notable resources focusing on the CI/CD include the OWASP Top 10 CI/CD Security Risks project, which originated from folks at Cider Security, which has now been acquired by Palo Alto.
Source Code
Source code attacks involve the compromise of a source code repository either directly from a developer or through the compromise of a developer's credentials. The 2022 Verizon Data Breach Investigation Report (DBIR) found that credential compromise was involved in over 80% of data breaches. This includes situations impacting source code or source code repositories. Malicious actors targeting source code and repositories will often try and introduce vulnerabilities or back doors into the source in order to later exploit them or impact downstream consumers.
Trust and Signing
Integrity is critical to trust in the software supply chain. This is typically facilitated by activities such as digital signing and attestations. Signing code gives downstream consumers a level of assurance regarding the provenance of code and its integrity. That said, compromising signing can and has been done to enact software supply chain attacks. Therefore, fundamental security concepts such as defense-in-depth remain key. Defense-in-Depth is a longstanding cybersecurity practice of utilizing multi-layered defenses so that no single vulnerability or weakness leads to an entire system or organizational compromise.
Malicious actors need to exploit several layers of defenses and security measures to achieve their objectives, rather than a single vulnerability or weakness. In the example above, only using digital signing is insufficient and can be exploited. This is among the attack types listed in the CNCF index and cited by MITRE in their supply chain compromise section of the ATT&CK framework. Potential threats include activities such as theft or private keys, misplaced trust, abusing certificate issuance among others, as cited by NIST in their “Security Considerations for Code Signing” whitepaper. Mitigation techniques involve activities such as establishing trusted users, separation of roles, strong cryptography and protecting signing keys and associated systems.
We would be remiss if we didn’t discuss emerging alternatives to make signing easier among the developer community and software supply chain, such as Sigstore, which has seen widespread adoption and alleviates some of the traditional pain points and challenges associated with signing.
Malicious Maintainer
Given the complexity of the software supply chain and the often-voluntary nature of maintainer activity, not all threats originate from outside of a project either. The malicious maintainer attack vector is among the threats listed in the CNCF index and it involves a maintainer, or someone posing as one, deliberately injecting malicious software or vulnerabilities into the supply chain or source code. This can occur due to a maintainer deciding to act maliciously, or their account or credentials being compromised by an external entity. You may also have malicious actors who pose as trusted contributors and maintainers, with the intent to wait until a later date to inject malicious code into the project or codebase. Motivations for these sorts of attacks range from hacktivists to those posing as involved maintainers, only to abuse their permissions and access to nefarious purposes.
Attack Chaining
Lastly, attacks and vulnerabilities don’t only occur in isolation. Malicious actors may chain together several vulnerabilities and attack vectors to carry out their activities and desired intent. Looking at some of the attack types mentioned above, a hypothetical scenario could involve a malicious actor posing as an interested contributor or maintainer only to abuse their access, insert malicious code, abuse signing and so on. Stringing together several attack vectors can have a devastating impact when done correctly. It can also be necessary, depending on the security posture of the target.
Conclusion
It should go without saying that this list is not exhaustive of the attack vectors and techniques to compromise the software supply chain and impact software consumers. As pointed out, one whitepaper cites over 100 attack techniques. That said, utilizing the CNCF catalog provides a concise reference to start to understand the variety of ways a malicious actor can attack the software supply chain. As organizations and the industry continue to pursue best-practices, implement safeguards and find ways to thwart attackers, malicious actors will continue to get more innovative and creative in their nefarious behaviors, leading to new types of attacks as well.