Sitting On a Haystack of Digital Needles
A look at the growing and complex vulnerability landscape as we close out 2023
It’s often quipped that “defenders have to be right all the time, attackers only need to be right once”.
This is an unfortunate paradigm because as it stands right now, they aren’t looking for a needle in a haystack, we’re standing atop a digital haystack of needles when it comes to vulnerabilities.
As we close out, I wanted to take look at the vulnerability landscape.
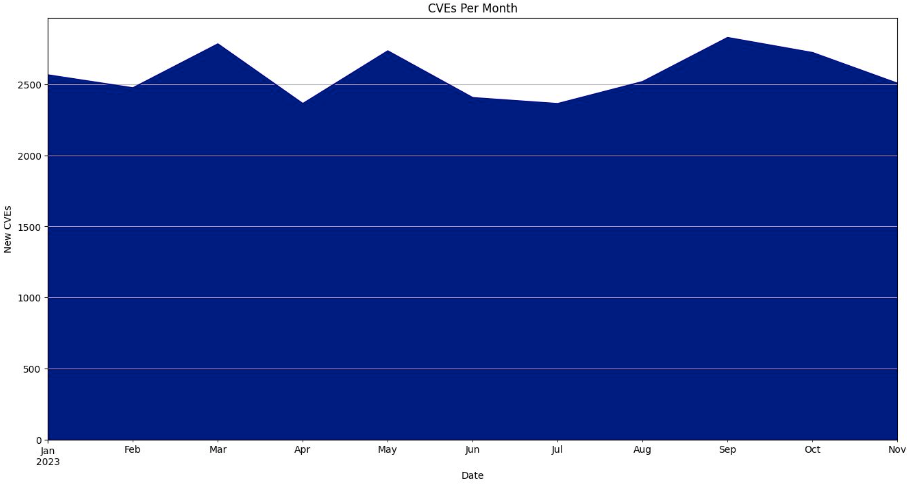
Jerry Gamblin, the always informative vulnerability researcher recently pointed out on LinkedIn that for the first time ever we have hit over 30,000 CVE’s published in a single year.
Additionally, Jerry pointed out some other interesting CVE metrics:
2023 YTD CVE Stats:
Total Number of CVEs: 28,261
Average CVEs Per Day: 84.61
Average CVSS Score: 7.13
YOY Growth: 20.10% or +4,730 CVEs (23,531 CVEs YTD 2022)
There are a lot of factors that go into these figures, such as:
The growth of software across every aspect of society
Increased attention from malicious actors
Increased attention from vulnerability researchers and cyber practitioners
And the list goes on
That said, there’s no denying one reality:
Software vulnerabilities continue to experience exponential growth that far outpaces our ability to deal with them
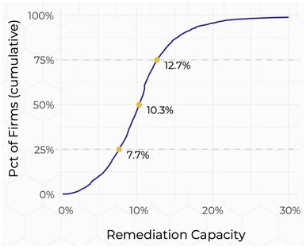
This is supported by research from organizations such as Cyentia, who found that on average, organizations only have the capacity to close roughly 10% of vulnerabilities in their assets in a given month:
This of course means vulnerability backlogs grow exponentially, leading to tremendous security technical debt, that goes on unmediated, accumulating, just waiting to be exploited by malicious actors. This is supported by research from folks such as Yotam Perkal, Rezilion and Ponemon, who found that on average, organizations had a backlog of 1.1 MILLION individual vulnerabilities.
The only thing that can come to mind in this scenario is someone trying to scoop water out of a sinking ship.
The key takeaways is vulnerabilities continue to be discovered, disclosed, and reported beyond our capacity to remediate them, leading to enormous vulnerability backlogs and security technical debt.
Malicious actors know this, and are taking advantage of it to exploit organizations of all shapes, sizes and industries.
Secure-by-Design: Breaking an Endless Hamster Wheel of Exhaustion
There has been a tremendous push for systemic changes, moving to a paradigm of “Secure-by-Design/Default” software and products, especially being championed by CISA and its leadership.
CISA has published two editions of its “Secure-by-Design” publication and have now begun publish specific tactical guidance for certain concepts as well.
I previously covered the Secure-by-Design publication in an article titled “Secure-by-Design (and Demand): A Look at the new CISA Secure-by-Design publication”.
It’s also a concept advocated for in the new National Cybersecurity Strategy, which advocates for shifting the balance and burden of insecure products and software onto suppliers and vendors, rather than consumers and customers and even revived the hotly debated topic of “software liability”.
I covered the 2023 National Cyber Strategy in this article.
The public recognition that the current paradigm is broken was further reiterated by a top CISA official Eric Goldstein recently in a CyberScoop article, where he stated:
“To say that our solution to cybersecurity is at least in part, patch faster, fix faster, that is a failed model,” Goldstein said at an event held by the nonprofit International Information System Security Certification Consortium. “It is a model that does not account for the capability and the acceleration of the adversaries who we’re up against.”
Mr. Goldstein specifically pointed out that the paradigm is particularly challenging for entities such as school districts, utility providers and small businesses, who simply don’t have the capacity, resources or expertise to succeed against modern malicious actors day after day.
He goes on to point out that the current paradigm is a “systemic cost transference from technology providers who make decisions to design products a certain way to customers, who then have to bear the burden to patch, to mitigate, to respond” and that most organizations simply can’t bear that burden.
These comments of course align with the NCS Section 3, public comments from others such as CISA Director Jen Easterly, and the CISA publications themselves I mentioned above.
As it stands now, organizations are on an endless hamster wheel of identify, remediate, report - ad nauseam and most are simply unable to keep up, a trend that will only accelerate due to factors we discussed above, such as growing software pervasiveness and increased attention from both vulnerability researchers and malicious actors alike.
It’s a Sisyphean task that is both exhausting and impossible but also one they can’t neglect, for if they stop pushing the rock (remediating vulnerabilities), it simply rolls them over and squashes them (malicious attacker exploitation)
Just this morning, Bob Lord, a Senior Technical Advisor at CISA took to LinkedIn to point out how broken the current system is. He used the example of a company recently getting breached, the fall out and news coverage, all of which focused on how the victim company didn’t patch fast enough etc. with little to no coverage or inquiries around the impacted product and its associated software supplier, such as how they produce secure products, handle eliminating classes of defects and so on - pointing out how we typically victim shame organizations who get breached while paying little to no attention to the actual product suppliers and their role.
While most security practitioners agree with and dream of a world where Secure-by-Design/Default is the de-facto operating model for technology providers, the reality is that it is not one that will be voluntarily embraced.
As much as we begrudgingly hate to admit it, security has a cost, often one that comes into conflict with other priorities such as speed to market, revenue/profit, feature backlogs, and more.
This is why cybersecurity is a market failure, it is simply both more cost affordable and less painful to externalize the cost onto customers and consumers than to make the requisite investments in security through an entire software/product development lifecycle and to take ownership for security outcomes, as advocated by the U.S. National Cyber Strategy/CISA.
That said, as software now drives everything from consumer good to critical infrastructure and national security systems, we all know collectively bear this cost, as a society, and with the increase of cyber physical systems, it is one that will increasingly blur into safety concerns as well.
Cybersecurity can, and does, impact our educational institutions, medical facilities, personal homes, family privacy, utility providers and national security.
However, until, if ever, regulatory forces change this current market failure, we will continue to get what we tolerate, which is incredibly vulnerable and insecure products and software, pervading every aspect of our society.
Building security into the SDLC is not a new concept, in fact, it is one that has been advocated for by security practitioners for over 50 years, tracing origins back to “The Ware Report”, which I unpack in articles “Cybersecurity First Principles & Shouting Into the Void” and “The Elusive Built-in not Bolted On”.
The concept of software liability, which is hotly debated was also re-introduced into the public discourse in Section 3 of the National Cyber Strategy. However, there is a lot to unpack on the topic, and it will be aggressively debated between Government and industry, in terms of how it will work, what examples can be leveraged, and what provisions for “safe harbor” will be put in place to protect technology providers who do take the proper precautions to produce secure products and technologies.
This is critical, as we know no software/product is infallible, and efforts for “vulnerability free software” (something that was originally in language for the 2023 NDAA but thankfully got stripped) are both naive and dangerous, likely to complete stifle innovation and impact economic prosperity and national security, the two of which are inextricably related, much to the dismay of some in silicon valley.
While I can’t predict the future, it’s said the best way to predict the future is to study the past, and this past year has been a tumultuous one, of cyber incidents, data breaches, exponential vulnerability growth and increased cyber activity between nation states as Cybersecurity continues to get codified as a fifth pillar of warfare.
As it stands now, we’re heading into 2024 sitting on top of a pile of digital needles in a haystack, and attackers continue to demonstrate they have no difficulties finding them, and will likely get even more proficient with the advent and evolution of AI.