Resilient Cyber Newsletter #9
Black Hat, Microsoft Bonuses, AI and OffSec, GRC Engineering & The State of Exploitation
Welcome!
This past week was Black Hat/DEFCON so of course a lot of exciting announcements, product releases and more coming out of the event. I will be sure to be blending in some of that comment into this weeks newsletter.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 6,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cybersecurity Leadership and Market Dynamics
Black Hat Innovators and Investors Summit
One of the things I was bummed about most when it comes to missing this years Black Hat is missing the dedicated summit they had for innovators, investors and startups. The summit included a who’s who of security leaders and impact makers.
Darwin Salazar over at the Cybersecurity Pulse produced a quick summary of the event that I really enjoyed and I am anxiously waiting (and hoping) that the summit will be recorded so I can catch those sessions.
Microsoft Binding Bonuses & Promotions to Security Performance
In the fall out of several high-profile and highly visible security incidents, including a damning Cybersecurity Safety Review Board (CSRB) report citing “systemic” gaps in their security culture, Microsoft continues to take steps to try and undo the negative publicity.
This includes announcing that they are binding employee bonuses and promotions to security performance. This is part of a previously announced “Secure Future” initiative by Microsoft and the CEO Satya Nadella.
A new recent memo emphasizes the CEO’s guidance to the entire company which was “when faced with a trade off, employees should choose security above all else”. This of course is inspiring on its face because we know competing priorities such as speed to market, revenue, product features/releases and more all generally come ahead of security, and are how employees and companies both are incentivized, rather than based on how secure something is.
That said, it will remain to be seen how practical the approach is, and how the outcomes and security of Microsoft products changes (or doesn’t) under this new edict and if the behavior behind the scenes matches the public rhetoric.
Should the CSRB take on Crowdstrike?
Some have begin to ask if the Cyber Safety Review Board (CSRB) should focus on Crowdstrike given the recent outage. The opinions seem to be mixed on this, with some saying it was a defective update and Crowdstrike has responded well to the incident, all things considered, while others have said it is a call for resilience and accountability, with former National Cyber Director Chris Inglis saying the event is in the same category as SolarWinds.
I’m not sure I agree with him there, while the incident did have a massive widespread impact, it was also not caused by malicious actors and associated security deficiencies, which is the focus of the CSRB.
That said, Chris did mention it carries important lessons about not just digital resilience but also legal liability for software providers, which as I have pointed out in recent articles is considered a “third rail” topic in cybersecurity, and one that is complex.
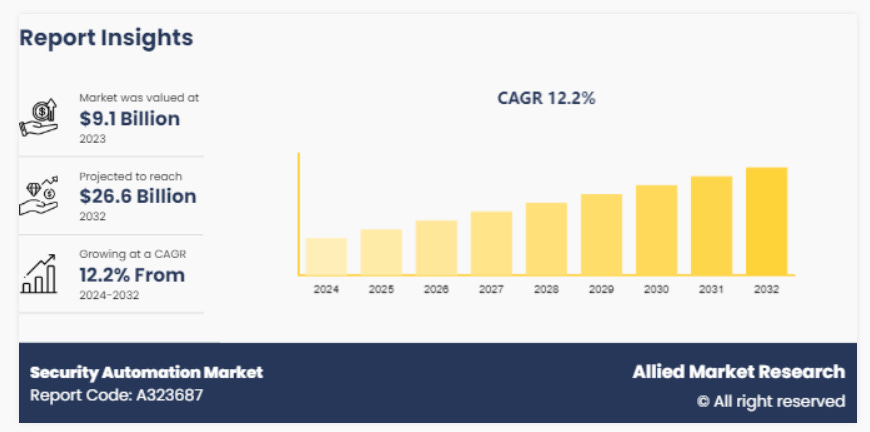
Security Automation Market Potential
One of the most promising areas of cybersecurity is the potential for automation. Taking traditional manual activities and processes and streamlining them to keep pace with development, engineering, the business and of course the threat landscape.
I found this report from Allied Market Research insightful, as it shows the potential growth and opportunity in the Security Automation Market.
As demonstrated above, the market is already sizable and projected to grow significant in the coming years.
AI
Using AI for Offensive Security
There’s been a lot of interest in the potential use cases of AI in cybersecurity. That includes in activities such as vulnerability identification/discovery, SOC/SIEM analysis and triage, and many more.
It also includes activities such as Pen Testing, Purple Teaming, Red Teaming and overall Offensive Security. The Cloud Security Alliance (CSA) recently released a comprehensive paper from their CSA AI Technology and Risk Working Group titled “Using AI for Offensive Security”.
It covers:
Current challenges within OffSec
Overview of LLM’s and AI Agents
The potential role of AI in the five security phases of reconnaissance, scanning, vulnerability analysis, exploitation and reporting
How threat actors are currently using AI
Current limitations of AI in OffSec
It is definitely a good read for those interested in the potential impact AI, GenAI and LLM’s may have in OffSec.
Knostic Wins Black Hat Startup Spotlight Competition
Much like RSA with its “Innovation Sandbox”, Black Hat hosts a special event focused on highlighting some of the most promising startups in the ecosystem.
This years top 4 finalists were:
DryRun Security
Knostic
LeakSignal
RAD Security
While I’m bummed RAD didn’t win, since I’m an advisor on the RAD team, I am excited for the winner, Knostic. Knostic focuses on LLM over-sharing and implementing need-to-know controls and right sizing access for LLM’s when it comes to organizational data.
Knostic is led by folks such as Gadi Evron who was the former CISO-in-Resident of Team8 and industry leader Sounil Yu, author of foundational book in cybersecurity (IMO) titled the “Cyber Defense Matrix”
I’m a big fan of Sounil’s thought leadership in our industry and have long-cited his work and publications.
It looks like he was excited just a bit to win as well :)
I have covered Sounil’s work in the past, such as his Cyber Defense Matrix book in my article “Enter the Matrix” as well as his D.I.E. Triad (Distributed, Immutable and Ephemeral) in an article where I apply it to your career, titled “The D.I.E. Triad - Applied to your Career (and Life)”.
Microsoft AI offerings now authorized at FedRAMP High
Microsoft recently announced their OpenAI GPT-4 is now available to agencies requiring FedRAMP High Authorization, meaning it is able to be used for FedRAMP High data.
While on one hand this is an exciting opportunity for the U.S. Federal community to lean into innovative GenAI/LLM capabilities, it is also an interesting one, given the Federal ecosystem is yet to really mature its governance and security around GenAI, LLM and AI usage, including with regards to data. Couple that with concerns around Microsoft’s security, with some even calling it a threat to national security, several highly visible security incidents and of course the Cyber Safety Review Board (CSRB) which cited “systemic” issued at Microsoft with its security culture.
AppSec, Software Supply Chain Security and Vulnerability Management
Compliance (GRC) Engineering is Promising
Everyone knows the pain of compliance. Legacy approaches, manual toil, static documentation, checklist mentalities and more.
Frank Wang penned a piece discussing why he thinks GRC Engineering is promising. He cites the GRC Engineering Manifesto.
It is created by a group of GRC innovators, who I know well and I have chatted with quite a bit. I am also a member in their Slack community to keep up with their efforts.
Frank lays out several examples from the group in his article and explains why he agrees that Engineering needs to move more into the GRC space to disrupt traditional legacy methodologies and approaches.
This is a topic I have discussed extensively in articles and publicly.
Qualys Publishes their 2024 Midyear Threat Landscape Review
We know it is tough to keep up with the most relevant trends and analysis when it comes to vulnerability management. One report I really enjoy is that from Qualys, particularly Saeed Abbasi who leads their Threat Research Unit.
He recently published their 2024 Midyear Threat Landscape Review and it has some great insights as always.
For those looking for a tl;dr, you can find that below, but I strongly recommend taking the time to read the full report as well.
As expected, the overwhelming majority of vulnerabilities this year are not being exploited, and therefore pose little actual risk o the organization. This again emphasizes the need for focusing on vulnerabilities that are known to be exploited (e.g. CISA KEV), along with those with high potential to be exploited (e.g. EPSS), along with a focus on organizational context, business criticality, reachability and more. Otherwise, we’re burying teams in noise, wasting resources and failing to mitigate organizational risks.
Also, we see that malicious actors are increasingly targeting older CVE’s, again emphasizing that we can often get caught up in the hype of the latest zero day, but attackers are taking advantage of massive vulnerability backlogs and targeting older CVE’s ripe for the picking.
Lastly, they point out that prioritization of vulnerabilities should account for public facing applications and remote services, which often serve as an initial entry point and facilitate lateral movement.
This emphasizes the need to focus on zero trust methodologies such as network segmentation, least-permissive access and a default-deny posture to limit the blast radius of exploitation.
Design Questions in the Software Liability Debate
I posted in last weeks newsletter how the recent Crowdstrike incident has spurred renewed interest around the concept of software liability, something the latest U.S. National Cyber Strategy (NCS) also highlighted.
That said, the concept of software liability is often called cybersecurity’s “third rail”, and avoided due to the complexity and controversy surrounding the topic.
This comprehensive piece from The Atlantic Council dives into the topic, discussing key topics such as:
The need for software liability
Potential methods and frameworks
What can make one liable, who can be liable and how it could actually be enforced
Challenges to implementing any sort of software liability scheme
State of Exploitation 1H-2024
While there is always interest in vulnerabilities and trends, one focus getting increased attention among the noise is exploitation. That is, vulnerabilities that have actually been weaponized and are getting exploitation activity by malicious actors.
Vulnerability Researcher Patrick Garrity at VulnCheck published a report laying out the state of vulnerability exploitation for 1H 2024. What I found interesting here is the categorization of the products and even more so open source software, which is often left out of the broader discussion around vulnerability exploitation.
Some key highlights from the analysis are below:












Great issue, as always! Thanks for including me in this week's!