Resilient Cyber Newsletter #8
Cybersecurity Anti-Patterns, SEC Weakening the Cyber Posture of the U.S., the AI Security Shared Responsibility Model and 8 reasons Why Vulnerability Management Sucks
Welcome!
Welcome to #8 of the Resilient Cyber Newsletter.
This week we have BlackHat/DEFCON underway so it will no doubt be a week full of product/company announcements, feature releases, great talks and more.
I wasn’t able to attend this year as my wife is 7 months pregnant with #5 - so I am hanging back with the family, and also got to attend a Kidz Bop concert with our youngest daughter who turned 6.
All that said, I hope everyone has safe travels to BlackHat and I look forward to covering all of the great content coming out of the event.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 6,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cybersecurity Leadership and Market Dynamics
CrowdStrike Faces Lawsuit - But Limited Liability
The drama around the CrowdStrike incident continues to unfold, with it being announced that CrowdStrike is facing lawsuits from customers and investors, the Delta airlines CEO saying the incident cost them $500 Million and impacted over 5,000 flights, while CrowdStrike says it isn’t solely to blame for the outage.
Building on the topic, CSO recently published an article discussing if the CrowdStrike failure is the beginning of the end of software without guarantees pointing out the fact that the majority of software is sold “as-is”, with no promises or legal recourse for consumers.
This of course is a hot topic with the concepts of Software Liability and conversely Safe Harbor being a focus with the latest U.S. National Cybersecurity Strategy (NCS). I covered this topic in great depth previously in an article titled “Software: Liability, Safe Harbor and National Security”, as well as an interview with Chinmayi Sharma and Jim Dempsey.
You’re Doing it Wrong! Cybersecurity Anti-patterns
Cybersecurity is full of anti-patterns.
Behaviors that on the surface seem logical but often end up creating more organizational risks than they mitigate.
Whether it is chasing shiny objects (e.g. zero days, quantum, crypto, dare I say AI) rather than focusing on fundamental security practices. Thinking one “platform” will solve all of your problems, or conversely, thinking security is something you can buy (e.g. a product/tool) rather than something you practice, and more.
This is an excellent presentation from Mark Simos of Microsoft from RSA 2024, where he dives into those exact anti-patterns and the unintended impacts they have.
When it comes to security, it often isn’t attackers who are the worst enemies and culprits, it’s us.
That said, the talk also does a great job of highlighting challenging behaviors of the business that security practitioners need to wrestle with as well.
The Software Monoculture is Here to Stay
With the recent Crowdstrike incident and ties to Microsoft we’ve seen a renewed discussion around “monocultures”. It is indeed true that monocultures or vendor market dominance can present systemic risks.
That said, so can vendor/tool sprawl, a lack of standardization and a lack of organizational proficiency with backup, recovery, and resilience - something that was also on full display during the outages.
This is a great and concise piece on the topic from Andrew Plato, I particularly thought this line was on point:
“Like it or not, the software monoculture is here to stay. Standardized compute environments are preferred as they are easier to monitor, manage, and secure. The recent uproar over monoculture due to the CrowdStrike incident is a distraction. It avoids the real problem that organizations are unprepared for systemic outages and looking to blame somebody else for their problems.”
I dive into this paradigm and the dichotomy between vendor consolidation, monocultures and vendor sprawl in my article “Systemic Concentrated Cyber Risks: Discussing monocultures, systemic dependencies and digital fragility”.
Speaking of concentration risks, the Center for Cybersecurity Policy and Law published a report titled “Addressing Concentration Risk in Federal IT” which came out of a multi-stakeholder tabletop in April 2024. It was aimed at explored monoculture or concentration risk in the Federal IT ecosystem in particular.
The SEC is Weakening the Cyber Posture of the U.S.
Hard hitting piece from longtime CISO and Security Leader Ed Amoroso discussing how the latest SEC rules are actually weakening the U.S.’s cybersecurity posture.
Ed makes the case that there should be, and is, a collective concern among CISO’s when it comes to the latest SEC rules and activities. His says through interacting with 120 CISO’s as part of his organization many are concerned with the SEC rules and he points out that CISO’s largely manage the nation’s cybersecurity posture, especially since most critical infrastructure is owned and operated by the private sector. That said, I would be interested to see of those firms who actually have CISO’s, what the reporting structure looks like and more.
Ed states the SEC is causing five new/unfortunate behaviors by CISO’s which are impacting their effectiveness, rather than letting them focus on their actual function of reducing organizational risk. The behaviors he cites are:
CISOs are starting to minimize what they write down in email, workflow, or texts – and this includes requesting that less information be sent to them from their teams.
CISO’s are spending more time with their lawyers than ever - and it is related more to personal protection than organizational risk
Anyone with a prior CISO position is now being forced to play back decisions made many years ago that are being freshly scrutinized under a different set of criteria.
CISOs are being forced to file 8Ks that might otherwise have been avoided, and this generates numerous (uncomfortable) meetings with the SEC.
Many excellent present and future practitioners are considering leaving, or worse – never entering, the profession of CISO.
One peculiar aspect of this situation is that many of us security practitioners know that it isn’t the CISO who owns the risk, it is the business. Our job is typically to empower the business to make risk-informed decisions. Yet CISO’s are largely being held to account for organizational behavior related to cybersecurity rather than those who own the risk.. CEO’s, the board and the business.
Will your startup get acquired?
Many startup founders obviously seek to get acquired at some point in their founders journey. However, that dream turning into a reality is a steep climb and hard journey.
This visualization from Carta, which was shared by VC/Advisor Pramod Gosavi highlights just how small the chances of being acquired for most startups actually is.
As you can see, your best chance of being acquired is at Series B, but even then we’re taking about 3%. The chances begin to decline again moving beyond Series B and are relatively low at Pre-Seed/Seed, which makes sense given you’re just getting off the ground at that point, finding initial customers, refining early versions of a product and more.
Pramod makes a couple of key points in his post as well:
You need to plan for 3 raises minimum (e.g. Seed, Series A and Series B)
Founders need to be focused on getting to Series B, not wasting time on thinking about M&A
M&A is about de-risking, meaning GM/CEO’s won’t risk their career on Seed/Series A starts who haven’t found Product Market Fit (PMF)
The post also has good comments from others on the state of the market, dynamics at play and more, so I recommend giving it a read.
Cybersecurity Trends 2024 - Bessemer Venture Partners
While this resource was published a few months ago, it is still very relevant for the current cybersecurity landscape.
It dives into current cybersecurity trends in 2024, including in both the public and private security markets. It also discusses top 5 CISO trends, leveraging insights from Bessemer’s portfolio, which included:
Continued market consolidation
Cybercriminals exploiting AI tools
AI counterattacks for fraud and deep fakes
Growing importance of Identity and bringing together disparate capabilities
CISO’s returning to the fundamentals
This was a good read, and also insightful to see what how CISO’s view the state of the industry and threat landscape in 2024.
Decline in Cybersecurity M&A in First Half of 2024?
This article from SecurityWeek shows a steady decline in cybersecurity M&A deals since 2021 H1, with 2024 H1 hitting a low since the site stated they have started tracking the metric.
The article also demonstrates that of the 178 deals, 111 were strictly cyber companies, and the U.S. far outpaced other nations, account for 135 of the deals completed.
Despite the dip, the article does mention that the number of deals exceeding $1 Billion is already the same through 2024 as it was the entire year of 2024 combined.
What is interesting is GRC seems to be leading the way, accounting for 30 of the acquisitions. While it isn’t certain why this is, one could speculate it is due to the increased focus on Governance, regulatory compliance and scrutiny around organizational risk management.
AI
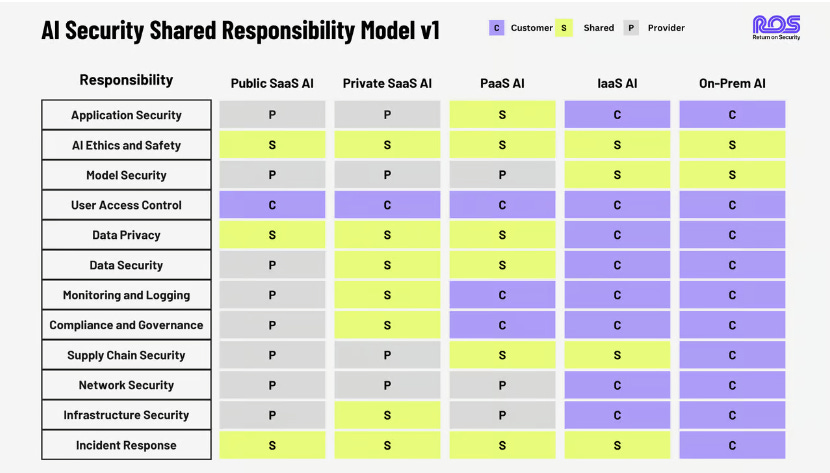
AI Security Shared Responsibility Model
The “Shared Responsibility Model” has been a fundamental (and often still misunderstood) aspect of Cloud and Cloud Security for years.
As organizations increasingly adopt as-a-Service offerings such as IaaS, PaaS and SaaS, they have had to understand where the vendors responsibility is, what the organization is responsible for and what responsibilities are shared between the two.
The same is true in AI, as organizations lean into various AI options ranging from Public SaaS AI, Private SaaS AI, IaaS/PaaS AI and On-Prem.
This is a great resource from my friend Mike Privette of “Return on Security” (if you aren’t following his page/newsletter you should be, it is full of amazing market analysis) where he breaks down what he proposes as a AI Security Shared Responsibility Model v1.
The article discusses the need for a shared responsibility model in AI and what a framework could look like. It also discusses the various AI deployment models and how to build a robust AI security stack and leverage this model in practice.
As CISO’s and Security leaders look to help their organizations securely adopt and leverage AI to drive business/mission outcomes, having a mental model like this is key to securing that use.
AppSec, Supply Chain and Vulnerability Management
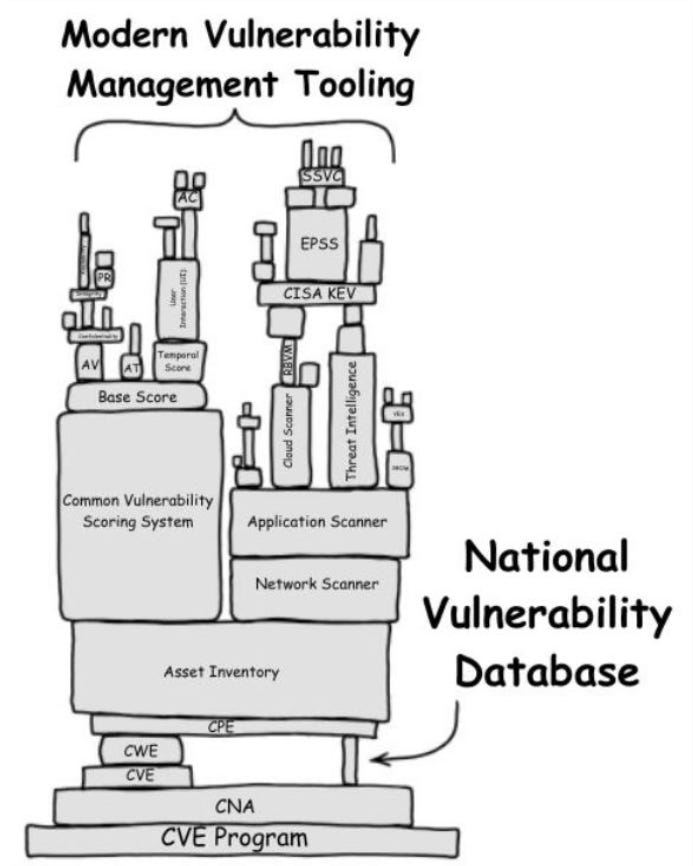
8 reasons why vulnerability management sucks
James Berthoty of Latio Tech posted this funny, but painfully true image about all of the frustration associated with Vulnerability Management.
From the struggles with vulnerability scoring and prioritization, wrestling with CVSS scoring, the addition of other schemes such as EPSS, KEV, business criticality, data sensitivity, reachability and more.
The awful behavior of security teams dumping massive vulnerability lists on developers and engineers, with little to no context, many of which are false positives. The NVD continuing to flounder, with Fortress publishing research showing the NVD will finish 2024 with 30,000 CVE’s pending analysis, all despite claims that the NVD was making changes to fix the backlog and vulnerability analysis struggles.
For a more detailed breakdown of NVD problems, you can see my article “Death Knell of the NVD?”
I’ve written how open source maintainers, are not suppliers, in my article supplier misnomer, with modern applications overwhelmingly relying on OSS components, accounting for 60-80% of modern code bases, yet open source having longstanding documented challenges such as:
Lack of funding
Aging population
No formal contractual relationship
Many FOSS maintainers citing security as a “dreadful soul withering chore”
And of course, everyone’s favorite - the reality that you can’t secure what you don’t know you have and most organizations still struggling terribly with asset inventory despite it being a CIS Critical Security Control for decades.
StrideGPT and AttackGen - AI-powered Security Tools
We see a lot of focus on securing AI, but many are also excited about how GenAI and LLM’s can be used to improve security. Matthew Adams, Head of GenAI at Citi is among those and has created a couple of awesome tools to demonstrate those use cases. Matthew created two open-source tools leveraging AI.
StrideGPT lets you utilize OpenAI, Azure, Google AI or Mistral to conduct Threat Modeling. You’re able to provide details about your application, such as the app type, data sensitivity, whether it is Internet-facing and the authentication types and generate automated threat models.
Similarly, he also created AttackGen, which lets you use the same AI providers/tools coupled with the MITRE ATT&CK framework to generate various attack scenarios against specific threat actors and their known TTP’s.
Today’s Lack of Software Visibility and the Implications
In cybersecurity it is often quipped that you can’t protect what you don’t know you have, and no where is that problem more true than in the space of software supply chain security.
Despite “software asset inventory” being a critical CIS control for years, most organizations simply have very low visibility into what software components they consume, whether it is via SaaS, Hardware, IoT, or via internal development making widespread use of open source.
This is a great blog on the topic from NetRise who touch on:
The importance of software visibility
The current state of software visibility
The implications of inadequate visibility
Steps to improve
NetRise continuously puts out great content around this problem and offers a robust solution addressing hardware, XIoT and Software component security.
Closing Thoughts
A ton of great content this week ranging from software supply chain security, cybersecurity leadership and the evolving challenges of leading effective security programs, including the dynamics between those leaders and their vendors/software suppliers.
It will be interesting to watch the conversation continue to evolve and see if software’s “third rail” - software liability will come to fruition or continue to be elusive, with software indefinitely used “as-is” with no assurances whatsoever.