Resilient Cyber Newsletter #6
Crowdstrike outage wreaks havoc, Wiz braves the IPO market, Unpacking Cybersecurity workforce trends and Continuing to argue about who the CISO should report to
Welcome to another issue of the Resilient Cyber Newsletter!
This week we have a lot of things to cover but undoubtedly the biggest story of the week is Crowdstrike’s faulty update that caused massive IT outages around the world. I will share some stories and resources but I also won’t belabor the point due to the fact that it has been covered by nearly every media outlet and by countless industry professionals on nearly every platform.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 6,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cybersecurity Leadership and Market Dynamics
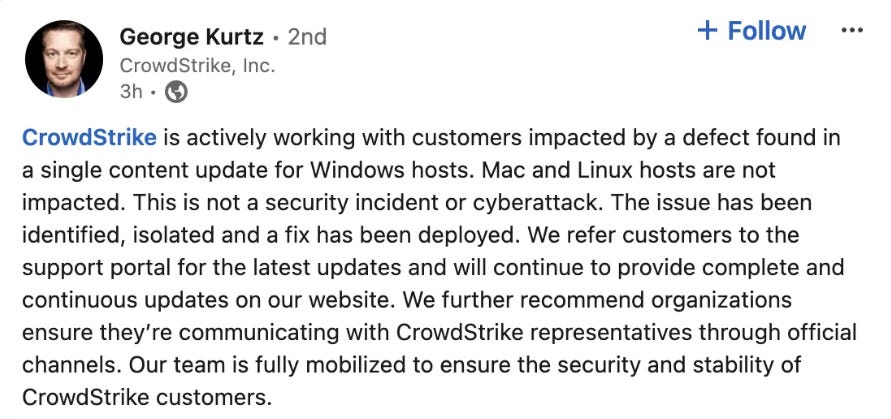
Crowdstrike Update Causes Blue Screen of Death
Towards the end of last week, a widely deployed Crowdstrike product update led to massive IT outages, impacting not just enterprise software environments but also airlines, financial institutions, medical facilities, Federal agencies and more.
The story was so big that it was covered on nearly all traditional media outlets in addition to the typical tech circuit.
Many have called it one of the largest IT outages in history.
It led to a nonstop series of public relations, communications and outreach from CEO George Kurtz and others on the Crowdstrike leadership team as well.
Crowdstrike of course is one of the largest cybersecurity companies in the world, with a massive presence due to their Endpoint Detection & Response (EDR) platform and suite of products.
The takes from the industry have wavered between armchair quarterbacks and competitors claiming what they would have done differently or better, to support from peers stating how these situations can happen to any organization, and we need to provide some grace to Crowdstrike.
From my perspective, that is true, and Crowdstrike has been incredibly transparent about the issue, what happened, and that they messed up. Crowdstrike President Michael Sentonas took to LinkedIn openly stating “Let me be clear, we got this update wrong, we will learn from this and will be better”.
I would much rather take this sort of transparency and humility from an industry leading software company than others we have seen who try and muddy the truth, blame others, or lack open transparency communications.
While the impact and outcome of this one remains to be seen, there were definitely a lot of lessons learned, organizations got exposed for lacking robust disaster recovery and continuity processes that they’ve practiced and countless business operations were disrupted.
We will continue to see how this one plays out and what comes of it.
We don’t have a cybersecurity problem, we have a software quality problem
CISA’s Director Jen Easterly took to LinkedIn, penning an article discussing how we have a software quality problem, not a cybersecurity problem. The post got massive traction with thousands of views and hundreds of shares.
Ironically, I had shared something similar in a post the day before.
In the article, Jen gives kudos to Crowdstrike CEO George Kurtz and his team for taking responsibility, apologizing and working collaboratively with CISA and others as the outage unfolded.
She also pointed out how much the industry has improved when it comes to collaboration, information sharing and response.
Most importantly though, Jen emphasized how the Crowdstrike outage is just yet another example of how highly dependent our modern society is on software, powering everything from consumer goods to critical infrastructure and national security.
She stressed how consumers of technology (all of us), need to be demanding that software and technology manufactures are prioritizing security, driving down flaws and now putting things like speed to market, features/functionality and revenue ahead of stability and security. This is in line with the CISA Secure-by-Design Pledge, which I have covered extensively previously in an article titled “A Digital Scouts Honor”.
The challenge of course, as I point out in the article is that CISA’s Secure-by-Design Pledge is a voluntary effort, and cybersecurity is a market failure, so depending on consumers to drive this change has proven unsuccessful so far. It will take either a drastic change in market dynamics, or increased regulatory pressure before we see systemic change.
Microsoft’s global sprawl comes under fire after historic outage
Despite the Crowdstrike outage not being an incident of Microsoft’s doing, it has raised further concerns about the prevalence of Microsoft and their outsized presence in the software market.
In this article on MSN/The Wall Street Journal, several U.S. Lawmakers are cited with concerns about Microsoft’s dominance.
This comes in addition to an already rough stretch for Microsoft in which they have had several highly visible incidents impacting the U.S. Federal Government, DoD, National Security and many commercial organizations and industries as well. They of course also has the damning Cybersecurity Safety Review Board (CSRB) report, citing “systemic” security failures at Microsoft and cultural gaps when it comes to security.
SolarWinds Defeats Part of SEC’s Fraud Cause
This week in a closely watched case with large potential ramifications for the future of legal cases in cyber, a Federal judge dismissed some claims against SolarWinds related to breach disclosures.
The case of course has been one the industry is paying close attention to due to the potential impact when it comes to accountability for organizations dealing with security incidents and the public claims, commentary and disclosures they make as well as specific questions regarding some of the public statements from the SolarWinds CISO.
As I have previously shared on LinkedIn, a group of industry leaders files an amicus brief, looking to aid SolarWinds push to dismiss the charges, claiming the case would be counterproductive due to the real-world demands of cybersecurity and could harm future disclosures, CISO’s and the broader cybersecurity industry. It is definitely worth a read as well!
EY Cybersecurity & Data Privacy Leader Brian Levine, who always shares great legal and regulatory content made a post discussing some key takeaways from the case as well on LinkedIn.
DarkReading also has a good article discussing some of the implications of the discussion, such as vindicating incident investigations and information sharing. However, as noted, some charges against SolarWinds and their CISO remain active, so we will have to see how that plays out.
Overseeing Cyber Risk: The Board’s Role'
We continue to see an industry wide push for board oversight of cybersecurity risks. This report from PwC dives into the Board of Directors (BoD)’s role in overseeing cyber risks and stresses that it isn’t just about preventing breaches and incidents, but also helping organizations recover (e.g. as we see with the Crowdstrike situation, albeit not a “security” incident, it is still adjacent, touching business continuity, incident response and disaster recovery).
The report discusses how nearly half of directors see cybersecurity as a significant oversight challenge and it lays out four key areas for boards to take action to support their companies and their risk management efforts.
CISO Reporting Landscape 2024
The reporting structure for CISO’s is an ever raging industry debate. While the role often reports to the CIO or other CxO’s, you’ll hear a large portion of CISO’s, Security Leaders and practitioners explain why the CISO needs to report to the CEO and/or Board.
YL Ventures, a Venture Capital (VC) firm with a strong portfolio of startups and mature security companies released their “CISO Reporting Landscape 2024” who provides insight into CISO reporting relationships across the ecosystem.
The report includes perspectives from over 50 cybersecurity executives and from various industry verticals. It also accounts for recent rules from the SEC and actions by the FTC that have and may continue to impact CISO’s and Security Leaders.
Ironically, despite all the hype around the CISO needing to report to the CEO, it seems that reporting relationships in terms of CIO vs CEO are almost even, per the report:
(Potential) Wiz Acquisition Continues to Make Waves
While the Wiz acquisition by Google still hasn’t been confirmed or finalized, it continues to make waves in the industry. This is a great post from Daniel Bartus, Partner at Felicis Ventures detailing how much of a success story the acquisition would be, not just due to the size (estimated $23 billion) but due to how quickly it happened (Wis is only 4 years old) and the rapid growth Wiz experienced, the execution of their leadership team and more.
The post breaks down the Top 20 Security Acquisitions of all time and shows just how incredible a story this would be if it goes through.
Wiz walks from $23 billion deal with Google
And just like that, all the waves the potential Wiz acquisition by Google made, are beginning to fizzle out as a story broke that Wiz is walking away from the $23 billion deal - which would of been one of the largest pure cyber acquisitions ever.
Wiz’s CEO Assaf Rappaport told employees that they are going to pursue an IP as they originally planned. Assaf was quoted as saying “Saying no to such a humbling offer is tough”. Among the concerns cited include antitrust concerns (the current staff have been known to be highly critical of large M&A activities) as well as investor concerns.
The company plans to push on for the IPO as well as aiming for $1 billion in recurring revenue.
I personally think this is a wise move by the Wiz team, as they have built an amazing vendor-agnostic security platform, innovative culture and have blown past previously set goals. I have no doubt they will hit their next targets due to the product and team they’ve built.
Closed IPO Windows
Speaking of the topic of IPO’s, VC Michael Jackson shared an excellent image of “Significant Software IPO’s” from 2014-2024. The image demonstrates just how slow and narrow the IPO activity has gotten since 2021 in particular.
That said, I wouldn’t count out unique teams like Wiz and a few others who’s IPO goals are far more likely than the broader ecosystem of companies striving for the similar goal.
Cyber Talent, Recruiting and the Workforce
The cybersecurity workforce is a constant hot topic. This includes outlandish numbers related to the number of unfilled jobs, often cited in the hundreds of thousands. These claims are also often made by credentialing/certification and education organizations who of course have an incentive to try and drive enrollment and revenue. Couple that with charlatans taking advantage of folks looking to break into cyber pitching their guidance, workshops, or mentoring all in claims of that glamorous “six figure salary” and it is a recipe for disaster.
That said, we indeed have workforce challenges, such as shortages of junior and entry level roles, ridiculous position description/requirements and some arguing that cyber isn’t an entry level role at all.
The hiring market has also changed drastically in the last few years (much like the IPO market above), with the pendulum swinging heavily in the favor of employers now, rather than employees like in peak 2021~.
I dive into this and more with Stuart Mitchell, a security talent and recruiting leader I have followed on LinkedIn for several years. Be sure to give it a listen as the latest episode of the Resilient Cyber Show!
AI
The Coalition for Secure AI (CoSAI)
Google along with others announced the founding of CoSAI, which is aimed at “investing in AI Security and leveraging Google’s Secure AI Framework”.
Other founding members includes organizations such as Amazon, Anthropic, Chainguard, Intel, Microsoft, NVIDIA, Wiz and others. The announcement mentioned the effort has been underway for the past year and is aimed at addressing the unique risks of AI.
The three initial work streams for the group include:
Software Supply Chain Security for AI Systems - it should come as no surprise they mention leveraging Google’s SLSA framework as well as the NIST Secure Software Development Framework (SSDF).
Preparing defenders for a changing cyber landscape - this is focused on developing a “defender’s framework” to address the security impact of AI use
AI Security Governance - The work stream mentions developing a taxonomy of AI risks, controls and an associated checklist and scorecard for readiness assessments associated with the security of AI products.
Leveraging AI to Identify Vulnerabilities in the Wild
Clint Gibler shared an excellent paper introducing “eyeballvul” which is pitched as a benchmark to test vulnerability detection capabilities of LLM’s at-scale. The paper evaluates the performance of LLM’s when it comes to identifying vulnerabilities in code bases
While it shows some promising potential and results, the authors also point out that there is still significant room for improvement as well.
Application Security (AppSec), Software Supply Chain and Vulnerability Management
Making Attestation Work for Software Security
There’s been a ton of discussion about software supply chain security, accountability and activities such as attestations. As we know, the U.S. Federal Government has now mandated that software manufacturers selling to the U.S. Government self-attest to following a subset of practices around secure software development from NIST’s Secure Software Development Framework (SSDF).
In this article on Lawfare, the authors discuss how to go about making attestation actually work. This includes recommendations for future attestation forms as well as pushing to make the attestations public, leaning into transparency to help address market failures in security where the consumer often is at an information asymmetry compared to suppliers due to a lack of transparency.
For a great discussion on this information asymmetry see Venture in Security’s article “Cybersecurity is not a market for lemons. It is a market for silver bullets”. However, it is worth noting that in this article the authors claim that not even the sellers truly understand the efficiency of the goods they are selling, often leading to speculative and outlandish claims.
Robust Release Processes
There has of course been a ton of discussion about the buggy update from Crowdstrike that caused one of the largest IT outages in history. Among some of the valuable discussion I found was a blog from CNCG’s TAG Security group, by Andres Vega discussing the important of robust release processes.
The article discusses key aspects of a robust release process, including:
Comprehensive testing
Integrity Verification
Staged Rollouts
Quick Rollback Mechanisms
Transparent Communication
Proper Key Management
While the industry speculation and criticism of Crowdstrike quickly got old, there are some valuable lessons learned and discussing robust release processes is part of that discussion to be had.
Accelerating Federal/Defense Software Development Cycles
The discussion on the need to securely accelerate software development cycles in the U.S. Federal and Defense space continues to evolve. Federal News Network shared a great article from my friend Bryon Kroger, diving into some key aspects of facilitating that acceleration.
Among the discussion in the article includes the need to evolve traditional ATO processes, but pointing out cATO/Ongoing Authorization is not a shortcut and actually required higher levels of maturity and rigor than traditional ATO’s.
This of course is a harsh truth for many across the DoD/Federal landscape who have used Continuous ATO (cATO) to try and sidestep doing the hard work of actually documenting their systems, associated security controls, their implementation details and following standardized processes.
For many expecting cATO to be an “easy button” when it comes to ATO’s, they will be disappointed, at least based on the currently published DoD cATO requirements and evaluation criteria. However, for mature, highly-capable and competent teams, cATO/OA can facilitate DevSecOps and agile software delivery in this highly regulated environment while still demonstrating high levels of security maturity.
Closing Thoughts
What a wild week it has been, with Crowdstrike’s buggy update causing massive headlines with one of the largest IT outages ever. The event led to a lot of armchair quarterbacking, some ambulance chasing but also a lot of healthy discussion across various professionals, backgrounds and perspectives on how to mitigate these sort of events in the future.
It can’t be emphasized enough that security is a subset of quality, organizations need robust release processes, and nothing gets businesses attention like availability disruptions (sorry cyber, Confidentiality is constantly exploited and gets no where near as much attention since it generally doesn’t impact revenue).
We continue to argue about who the CISO should report to, versus focusing on the actual influence, effectiveness and impact of those in the role.
Wiz continued to bring headlines regarding their potential acquisition by Google and we unpacked a lot of the complexities of the modern cyber workforce and talent landscape.
As always, I appreciate the support and hope the resources shared are valuable!
If you enjoy the content, be sure to subscribe and share it with a friend, as your support is greatly appreciated as well.