Resilient Cyber Newsletter #66
DoW’s Cyber 2.0, State of Israeli Cyber Exits, 2025 Security Software & Services Benchmarks, Measuring the Impact of AI, RiskRubric.ai LLM Leaderboard & Open Source Malware
Welcome!
Welcome to issue #66 of the Resilient Cyber Newsletter.
We’ve got a lot of exciting news and resources to cover this week, including the Department of War’s Cyber 2.0 approach, a deep dive into the state of Israeli cybersecurity exits, where a new wave is being born, looking at the state of cybersecurity software and services spending in 2025, measuring AI’s impact on software development, an LLM leaderboard and much more.
So, let’s not waste any more time and get right down to business!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 40,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Don’t Let Inactive AI Models Linger: Cut Risk and Cost Fast
Every inactive AI model you leave behind could be a ticking time bomb—retaining access, increasing your attack surface, and racking up cloud bills.
With Cortex Cloud, you can now automatically detect and flag inactive AI models across environments—no agents or code changes required.
Get clear visibility into usage patterns, ownership, and risk posture. Know when a model was last used and streamline cleanup in seconds.
Stop paying for idle infrastructure and reduce your exposure with Cortex Cloud’s activity-based AI model insights.
Cyber Leadership & Market Dynamics
DoD Rolls Out It’s New Approach to Cybersecurity
This week Katie Arrington and the United States Department of War rolled out their long-awaited RMF overhaul, dubbed “Cyber Security Risk Management Construct”.
What I was excited to see is much of what they emphasize is what myself and like-minded folks have been advocating for quite a while when it comes to doing Cyber/Compliance correctly, including aligning with GRC Engineering principles. I have written about this extensively in an article titled “GRC is Ripe for a Revolution”.
The new DoD approach includes 10 core principles:
Automation – driving efficiency and scale
Critical Controls – identifying and tracking the controls that matter most to cybersecurity
Continuous Monitoring and ATO – enabling real-time situational awareness to achieve constant ATO posture
DevSecOps – supporting secure, agile development and deployment
Cyber Survivability – enabling operations in contested environments
Training – upskilling personnel to meet evolving challenges
Enterprise Services & Inheritance – reducing duplication and compliance burdens
Operationalization – ensuring stakeholders near real-time visibility of cybersecurity risk posture
Reciprocity – reuse assessments across systems
Cybersecurity Assessments – integrating threat-informed testing to validate security
If you’re like me, you’ll likely be relieved to see this announcement, not because it is groundbreaking per se, but because it is grounded in the same fundamental principles my team and I, at Aquia, and fellow practitioners have been advocating for when it comes to doing cybersecurity and GRC Engineering correctly.
This includes focusing on the controls that make the most impact and risk reduction, sound DevSecOps principles, a secure SDLC, automating traditional compliance assessment toil, and moving towards cyber resilience.
We look forward to helping lead this paradigm shift from the legacy approach to cybersecurity across the DoW 🫡
Hopefully, many others will be willing to adopt these principles as well to deliver improved outcomes for the warfighters and our nation 🇺🇸
Lack of Board Access: The No. 1 Factor for CISO Dissatisfaction
We hear a lot about CISO frustrations and challenges, including demands, burnout, lack of support, and more. This recent report from IANS and Artico Search found that lacking board access is the #1 frustration among CISOs for SMB firms.
The report cites CISOs being blamed when things go wrong and lacking the broader visibility and access they need to succeed in their roles. This lack of board access often means being buried in the organization, and cybersecurity does not get the visibility or support it needs to be effective. The age-old friction is pointed out by some in the report, too, when having the CISO report to the CIO or CTO, where CISOs are raising risks around new technologies and efforts, which can frustrate the CIO/CTO they report to.
State of Israeli Cyber Exits: A New Generation is Born
If you watch the cybersecurity market at all, you are inevitably aware of the massively outsized role Israel plays in cybersecurity startups, M&A, and innovation. It can be a lot to keep up with, which is why this recent report from Dorin Baniel of VC firm NightDragon is a great resource.
This is the second edition of her report, with the previous report being the first edition, which was very insightful, and the latest being just as valuable. She points out that throughout 2025, there have been 18 Israeli cyber exits announced among the 36 weeks of the year thus far, which is bi-weekly, which is incredible. That said, her report also points out the skewed perceptions that can be had due to some outliers making massive impacts on the ecosystem (e.g. Wiz).
This report covers macroeconomic drivers, the IPO market, M&A landscape, Wiz acquisition deep dive, a look at current and future unicorns and more. I definitely won’t try and cover it all here, and recommend you read the full report for the latest on the Israeli cyber ecosystem, which heavily influences the broader U.S and international cyber community as well.
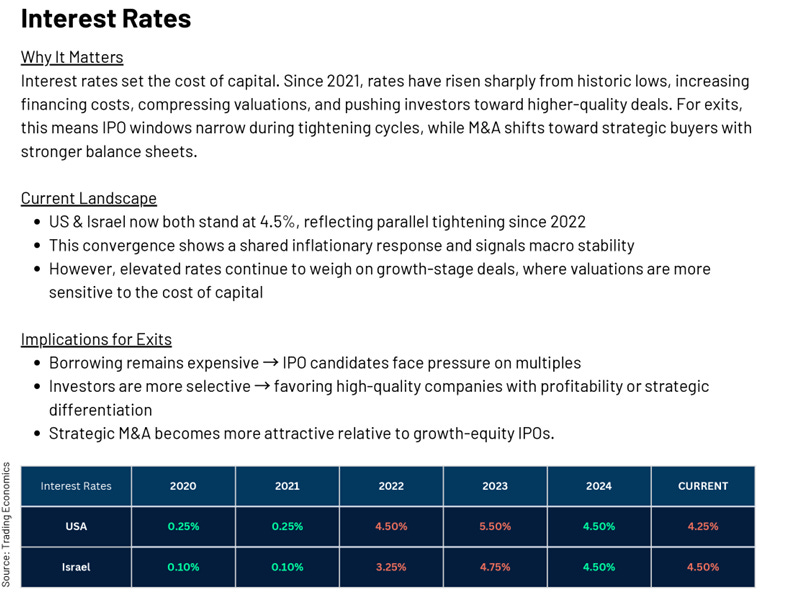
The report opens up by laying out the role of consumer price index, unemployment and interest rates when it comes to M&A, investment and spending.
As you can see, the U.S. and Israel have a lot in common when it comes to interest rates. This applies to exits and IPO activity as well, with emerging markets such as India making strong growth and being one to watch.
The report states that IPO cyber markets are quiet in general, although Netskope's announcement this week was a sign that things may be changing. In general, though, cyber outperforms the S&P 500 very well.
2025 has had a good deal of M&A and exit activity, as Dorin’s report shows below:
CyberArk and Wiz played a massive role here, accounting for a significant portion of overall capital. Not including Wiz and CyberArb, the combined value of existing assets from 2019 to 2024 was $23B. As Dorin points out, the Wiz and CyberArk exits alone exceed the combined value of ALL prior Israeli cyber exits since 2019.
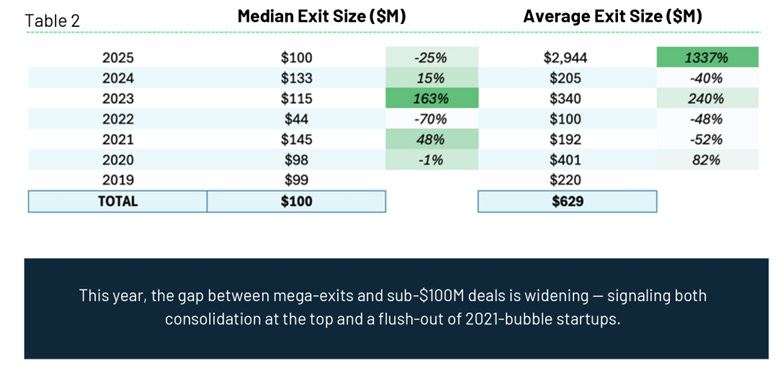
Exit sizes seem to be split, with roughly half being more than $100M, and half being below that:
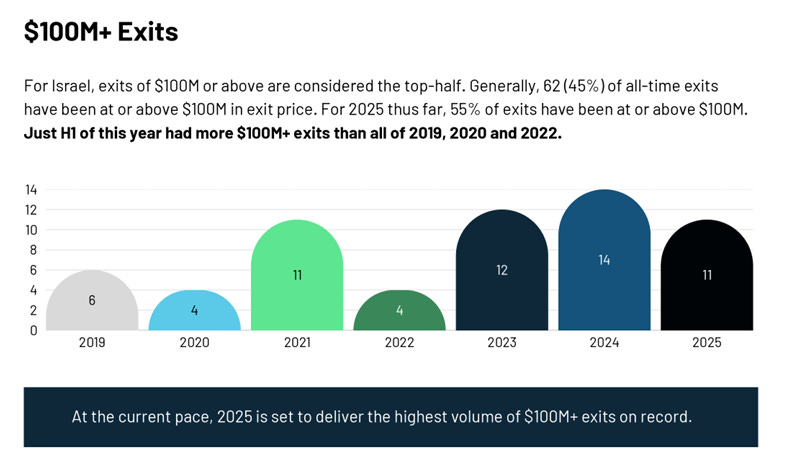
It will be interesting to see if we have 3+ more $100M cyber exits in 2025, to surpass the record in 2024:
Dorin shows the percentage and number of $100M+ exits since 2019 below:
2025 Security Software and Services Benchmark Report 📊
Like many others in our industry, I'm continually monitoring spending trends, enterprise and CISO interests, changing purchasing patterns, differences among software and services, and more.
This report from IANS and Artico Search has been a great read.
They found that approximately 30% of security budgets are focused on security software, but spending remains opaque and fuzzy.
However, vendor and tool consolidation is a fundamental factor, with 70% of CISOs stating they are either in the process of consolidating or well underway.
The platform vs. point solution argument is unfolding, with platform-based security solutions accounting for 40% of security software spend. It leaves more room for growth for industry leaders looking to chip away at point solutions, but plenty of room for those priding themselves on being best of breed.
There's also continued growth of Managed Security Service Providers (MSSPs), especially among large enterprise environments, for everything from threat detection, IR, endpoints, and network monitoring, as organizations look to outsource some security activities or, at a minimum, have a hybrid model to augment internal expertise.
I'm also curious to see how much of the security staffing budgets can become part of the TAM for AI-native security vendors looking to automate traditional toil and manual activities with the rise of Agentic AI.
Despite budget constraints, key focus areas remain SecOps, Cloud, and IAM, which isn't surprising given that identity is the primary attack vector and is muddled into declarative cloud infrastructure and development environments.
All of these require a strong foundation in SecOps to identify and respond to incidents when they occur. These are just some of the highlights from the report, which included over 600+ CISOs.
I definitely recommend checking it out for more details
Defining What “Winning” Looks Like in Cyber
We hear a lot about “winning” against adversaries in cybersecurity, but what does measuring that in practice look like? This piece from Jason Healey lays out some key considerations beyond just the number of adversaries that have been disrupted.
Jason points out that attackers are already having to shift from easier to more difficult TTPs, which is substantiated by reports from Verizon’s DBIR and Mandiant’s M-Trends. They also report a significant drop in the MTTD/MTTR in terms of detecting and removing threat actors from environments. 2011 it took 400+ days; now, these reports cite figures closer to a dozen.
Others, such as Google, report that zero-days now make up a growing majority of vulnerabilities used in the wild, from 62% in 2020 to 70% in 2023, which saw a 50% increase from 2022 to 2023. Jason also highlights that attackers must exploit newly disclosed vulnerabilities more quickly due to improved patching.
Inside the Mind of a Teen Hacker
This piece from Bloomberg provides rare insights into the mind and experiences of a teen hacker involved with the notorious “Scattered Spider” hacking group. The teen lived in Florida and had been on the run from the FBI for his involvement in the cybergang. The group's attacks include the 2023 attack on MGM Resorts International, which took down the casino's computers and cost the company over $100 million, among many other notable incidents and attacks.
The article tells how the teen went from a normal kid playing video games, to contributing to crypto theft and cybercrime, and the group’s activities spilled into reality, including kidnapping, firebombings, and sextortion. The teen met people in his video games and got involved in malicious activities with them, initially having him perform calls related to SIM swapping attacks.
The article is a fascinating look into the minds of those involved in these hacking groups and how the digital world our youth often consume can lead to real-world crimes and impacts.
AI
China’s AI Surge Exposes America’s Blind Spot: Research Security
Anyone who follows the AI and tech space knows that the U.S. and China have been locked in a race for superiority when it comes to AI, with both nations citing the importance of this transformative technology on the future of geopolitics and conflict alike.
This piece from NextGov/FCW lays out how China has now taken the lead in the world in AI research output, surpassing the U.S. and EU:
China files nearly 10x more AI patents than the U.S.
China’s output in AI research has eclipsed the combined total of the U.S., EU-27, and the UK in both volume and growth rate.
China’s AI researcher base is larger and younger than that in the U.S., suggesting a continued wave of innovation.
China has become the top AI research collaborator for the U.S., despite geopolitical tensions.
The piece goes on to discuss how China’s engagement with research institutions worldwide, including in the U.S., can serve as a secretive channel for the transfer of R&D and IP.
How AI is Reshaping Cybersecurity Careers
Everywhere we look, we’re seeing AI’s impact from investment, startups, incumbents, large enterprise environments, and more. All of this has implications for cybersecurity practitioners as well, including the rise of potentially new cyber roles and titles.
Cyber education and certification leader SANS recently shared a poster outlining some of the emerging AI-enabled security roles, what they do, and the problems they solve. It will be interesting to see if these truly catch on as standalone roles and titles or if these activities get absorbed into existing security roles and responsibilities.
The image can be difficult to read, so I recommend going to the source. There, you can zoom in and scroll around for better readability. Shoutout to Rob T. Lee and the SANS team for this thought-provoking resource.
AI Headlines List of Changes Seen by CIOs and CISOs
This piece from Signal, part of AFCEA, mentioned how at a recent gathering of Federal CIOs and CISOs, both stressed that the demand for AI and the AI field overall has been “the most notable change within their respective offices”.
The Federal technology and security executives are grappling with the rampant demand for AI while trying to ensure it is adopted securely and responsibly.
Are AI strategies destined to fail without Security-by-Design?
This article makes the case that in the rush for AI adoption, most organizations are perpetuating the bolted-on rather than built-in problem of cybersecurity.
I'm inclined to agree.
We're seeing rampant pilots and adoption of AI, LLMs, and Agents. But governance, visibility, inventory, access control, and fundamental security?
Not so much.
Everyone is hyped about the potential TAM of agentic AI, and agents are poised to outnumber human users exponentially. Yet, most organizations aren't building sound strategies and processes in parallel to enable secure Agentic AI adoption.
Measuring the Impact of AI 🔎
I was recently reading Gergely Orosz 's and Laura Tacho deep dive on The Pragmatic Engineer about "How tech companies measure the impact of AI on software development."
The line below in the image jumped out to me - because it is so true.
However, when it comes to AppSec, I feel like the security of AI-driven development is still an afterthought for much of the ecosystem. Security is a subset of quality; therefore, the question could include, Is the software actually secure?
As numerous studies have pointed out, not quite. Yet, we continue to widely adopt the AI coding paradigm, including inherently trusting the outputs, failing to use security-centric prompting, and speeding at all costs, security be damned.
We are seeing some AI-native security platforms and tools emerge to address this new development dilemma, but they are far from the norm or widely adopted. This will inevitably make for a vast, porous digital attack surface.
The whole piece from Gergely and Laura is an excellent look into how the leading tech companies are measuring the ROI of AI tools for developers (and inevitably the security implications of this adoption).
Do we need an Agent Control Plane?
The team at Astrix Security thinks so. In this article, they make a strong case for the Agent Control Plane, laying out where traditional security falls flat when it comes to securing AI agents.
This includes relying on outdated practices such as long-living credentials, poor visibility and governance of agent activity, and exacerbating long-standing industry challenges around IAM. Instead, they propose an Agent Control Plane (ACP) that leverages just-in-time credentials, real-time logging and visibility, monitoring for malicious or anomalous activity, and more.
RiskRubric.ai Launches Industry First LLM Leaderboard
RiskRubri.ai, a project of the Cloud Security Alliance, launched this week. It is a comprehensive leaderboard/report card for LLMs that provides grades across transparency, realiability, security, privacy, safety, and reputation.
The initial launch includes 150+ models with monthly updates and expert validation.
It provides extended details in addition to the grades, citing concerns such as whether models falsely portray themselves as human, adequately disclose AI status when answering questions, have protections against prompt attacks, and how they handle privacy concerns related to personal data.
This is a good resource for organizations and practitioners to keep on hand and check before using models.
AI Ushers in a Golden Age of Hacking
This piece from the Washington Post provides insights from industry leaders and researchers on AI's quickly evolving impacts on malicious activities. The folks quoted cited malicious packages, software supply chain attacks, improved phishing techniques, and more—all powered by LLMs, coding tools, and GenAI platforms.
AppSec
Open Source Malware 📈
In the past few months alone, we've seen several notable open source malicious activities and incidents. This continues to leave organizations scrambling, while attackers continue to take advantage of the opaque open source ecosystem.
This Open Source Malware Index from Sonatype shows just how problematic things are.
In Q1 of 2025 alone they saw almost 18,000 open source malware packages, a 230% increase from the prior quarter. This includes hijacked packages for crypto, fake security tooling and more. Really insightful report in terms of the open source landscape and malicious activity.
Zero Trust and Open Source Need a Convergence 🤝
In the past several weeks and months, we’ve seen a significant uptick in malicious attacks against open source, including npm.
Despite the broader industry embracing zero trust in cybersecurity, open source makes up 80% of modern codebases and applications, yet is often inherently trusted.
That needs to change, and it can be done by changing the ways we consume, validate, and govern our open source consumption.
This is an excellent piece from Varun Badhwar explaining what this intersection of open source and Zero Trust looks like in practice, and how organizations can implement zero trust principles to mitigate software supply chain risks.
This involves principles such as a default deny stance, continuous verification, least privilege (minimizing dependency bloat), and assuming breach. That said, much of this is easier said than done, especially with legacy AppSec tooling. That’s why I’m proud to collaborate with the Endor Labs team, which has a purpose-built solution for the modern software supply chain risks.
This includes:
OSS risk intelligence and scoring
Evidence-based remediation to minimize toil and noise to focus on actual exploitable and reachable risks
A flexible policy engine to enable least-permissive access control and a default deny stance for open source consumption
These capabilities are aligned with OWASP® Foundation‘s Open Source Top 10 as well.
Resilient Cyber w/ Emre Tinaztepe (Binalyze) - Forensics at the Frontline
In this episode of Resilient Cyber, I sit down with Binalyze Founder/CEO Emre Tinaztepe.
We will discuss how AI and automation are impacting the future of the SOC and the role that forensics-level data can play in incident response and recovery, as well as proactive threat hunting.
Prefer to listen?
Please be sure to leave a review, as it truly helps the show grow!
Emre and I dove into a lot of great topics, including:
The excitement around AI for security, particularly when it comes to SecOps and the SOC, and why the SOC is such a promising use case for AI
How AI can be leveraged to accelerate and improve incident response, and how Binalyze has integrated AI into its platform
The unique value of coupling digital forensics to live incident response workflows to mitigate the impact of incidents and improve security outcomes
The role of AI and LLMs when it comes to driving down metrics such as Mean-time-to-Detection/Response (MTTD/MTTR), as well as post-incident reporting and analysis
Utilizing digital forensics for proactive threat hunting, to shift security from a reactionary to a proactive posture