Resilient Cyber Newsletter #50
2025 Rising in Cyber List, FedRAMP 20x Updates, Cyber Opportunities & Risks of Agentic AI and AppSec’s Exploitation Era
Welcome!
Welcome to another issue of the Resilient Cyber Newsletter.
A good mix of resources this week in terms of cyber market analysis and technical topics, so let’s get to it.
I hope you enjoy this week’s resources!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 45,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Hardening AD? Start with your passwords
Not all complex passwords are secure. Specops Password Policy lets you enforce true security hygiene across your Active Directory, using real-time breached password filtering, granular policy targeting via GPO, and compliance-ready enforcement for NIST, NCSC, and more.
Go beyond Microsoft’s legacy settings with custom dictionaries, passphrase support, and rules that adapt to your environment. No schema extensions. No agent sprawl.
Just precise control at scale.
If you’re hardening AD, your password policy shouldn’t be the weakest link.
Cyber Leadership & Market Dynamics
Rising in Cyber 2025 List Unveiled
Notable Capital recently unveiled their “Rising in Cyber” list, highlighting the most promising private cyber companies selected by leading CISOs and security executives and those who have been nominated by top VC firms.
Companies are categorized as Early Stage (~$35M), Mid Stage ($35M-$100M) or Late Stage ($100M+) raised.
The publication also discusses the state of the industry and provides some solid insights. This includes the dichotomy of AI, where it is dominating headlines and investments, but also making many concerned from the security angle as well.
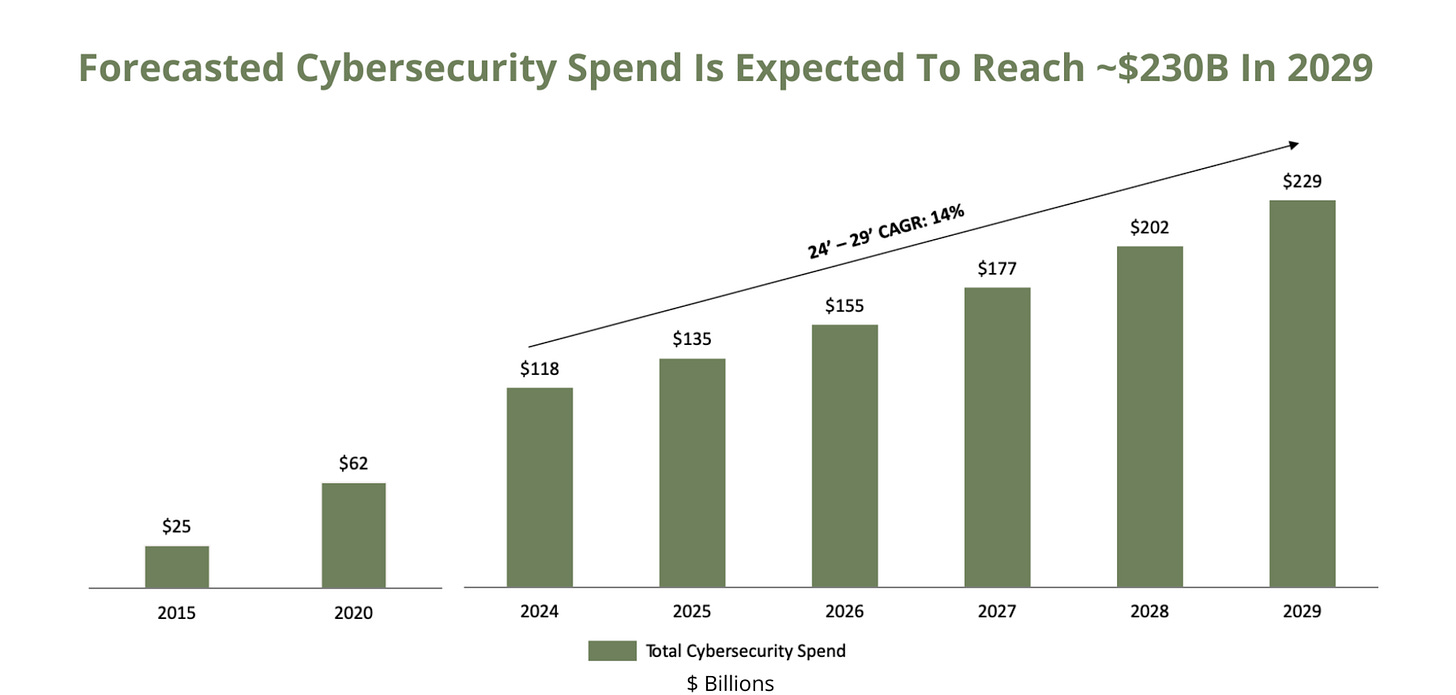
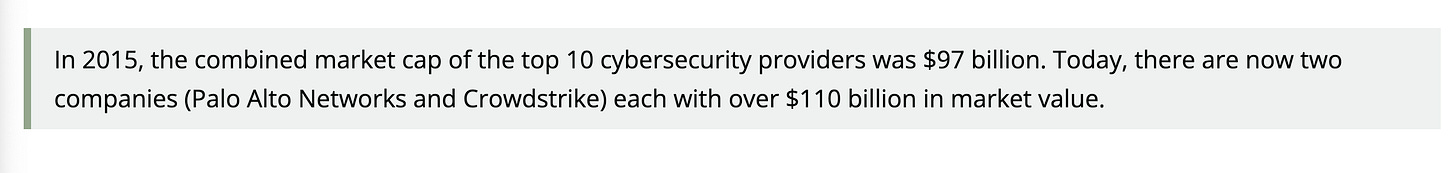
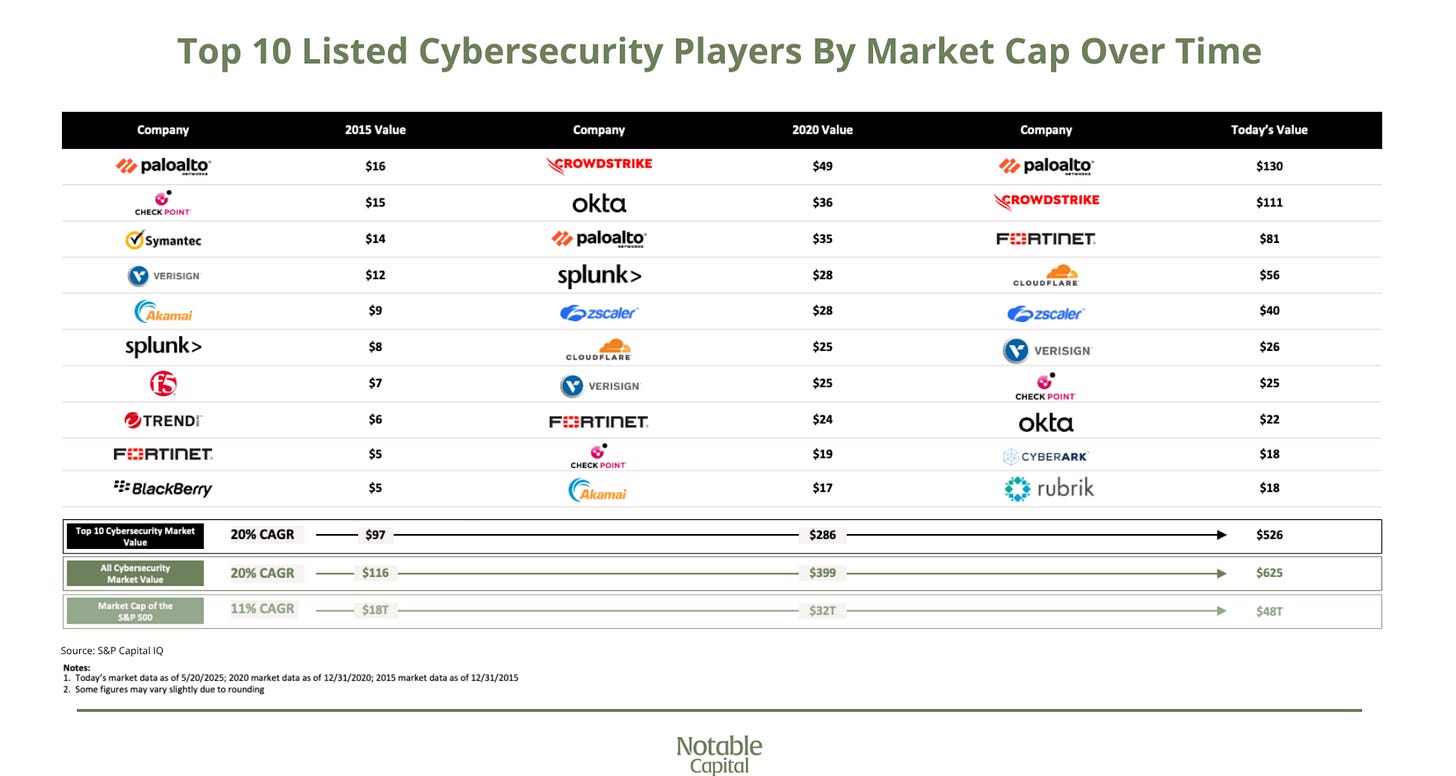
It’s amazing to see the market cap of publicly traded cyber companies exceed $625 billion, when it was just $116 billion 10 years ago, that’s a hell of a decade for cybersecurity.
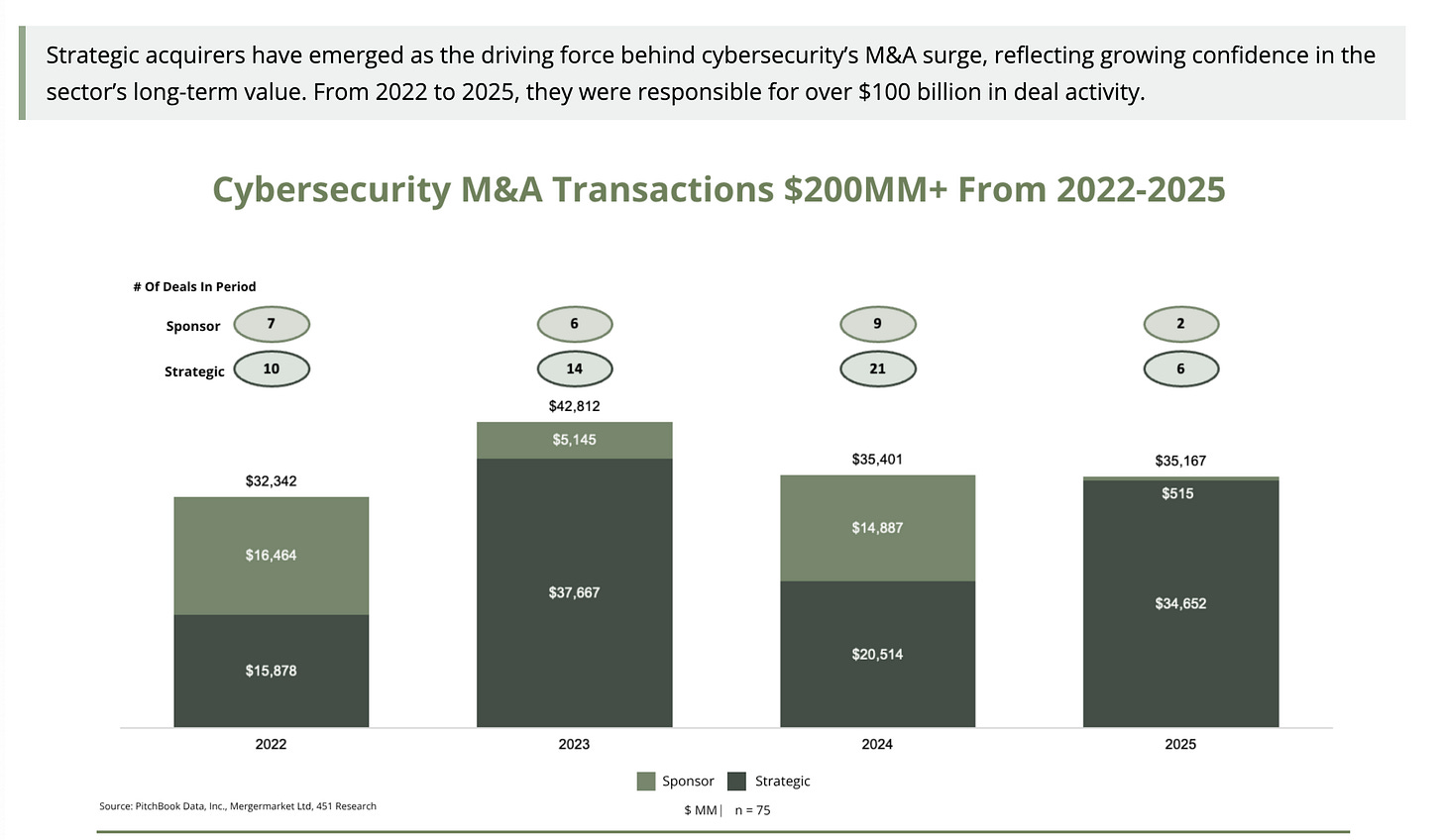
It also pointed out that 51 of the 75 cybersecurity deals over $200 million since 2022 were done by strategic acquisitions (e.g. existing players) in the ecosystem, showing the push towards consolidation, large players innovating through acquisition versus organic R&D and the overall vitality of the cyber industry as it grows.
Elastic’s CISO is even quoted as saying
“Startups are the R&D labs of the larger security companies”
The report projects cyber spending to double by 2029, reaching an annual total of $229 billion.
Notable’s report shares several key insights pulling from Morgan Stanley analysis, including that we have a complex need in cyber that’s leading to a booming market, see below:
They also provided insights into the trends and changes of the Top 10 publicly listed cyber players in terms of market cap over the last decade, and the growth is truly astounding:
They point out the role of strategic acquirers (e.g. existing companies) being a driving force behind the industry’s M&A activity, as they look to enhance their offerings, expand their market share, and consolidate competitors.
A key theme of Notable’s piece is just how critical cybersecurity is to running modern businesses, to which I agree with completely, because never every business runs on software to some extend and software plays a key role from operations to value delivery to customers.
We live in a software-driven society.
Some of they key survey findings involve budget pressures, the role of AI and agents, and the foundational role that identity plays:
One key theme throughout the Notable piece is also the potential of AI, from SecOps, to AppSec and GRC, many are looking for this promising technology to help alleviate workload challenges, automate toil, accelerate meantime-to-detection, mitigate vulnerabilities and much more. This is also evident in the massive number of startups that are both focused on AI and Cyber, as well as the premium in terms of valuation and fundraising that AI-native firms are fetching.
FedRAMP 20x - Two Months In and Taking Off
If you pay any attention to the public sector you likely have noticed the U.S. Federal Government’s cloud authorization program, FedRAMP, has been undergoing some big changes.
Some of these include contractual changes in terms of workforce and PMO size etc. but others include efforts to streamline, innovate and modernize the FedRAMP program itself, which has been dubbed as “FedRAMP 20x”, and being championed by the programs lead Pete Waterman.
FedRAMP recently shared an update on being two months in to FedRAMP 20x and some of the key changes. and progress.
This includes launch FedRAMP 20x Phase One pilots, updating key FedRAMP guidance such as the introduction of Key Security Indicators (KSI)’s aligned with NIST 800-53, as well as guidance on “Minimum Assessment Scope” which looks to narrowly define boundaries for assessment and authorization.
State of Enterprise Software 2025 Report
Silicon Valley Bank recently published their “State of Enterprise Software 2025 Report” which has a lot of great insights on the current software startup ecosystem in terms of funding, exits and more.
Some of the key metrics they cite:
43% YoY growth in US VC investments in enterprise software companies
1 in 6 deals involve AI/ML startups, showing the outsized role AI is playing
307 US VC-backed unicorns are enterprise software, which is 40% of ALL VC backed unicorns, up from 31% five years ago
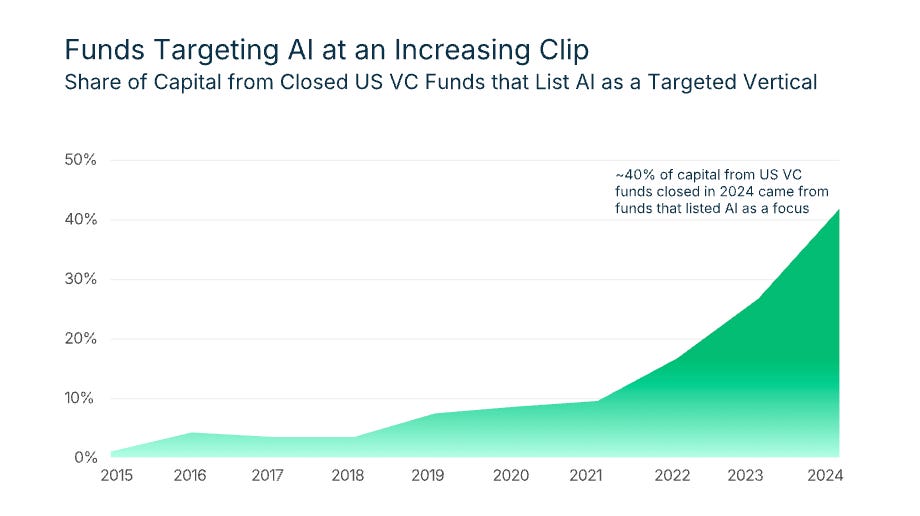
The below chart shows just how dominant of a role QAI is having right now in terms of fundraising:
This shows 40% of capital raised from US VC funds in 2024 was from funds targeting the AI vertical.
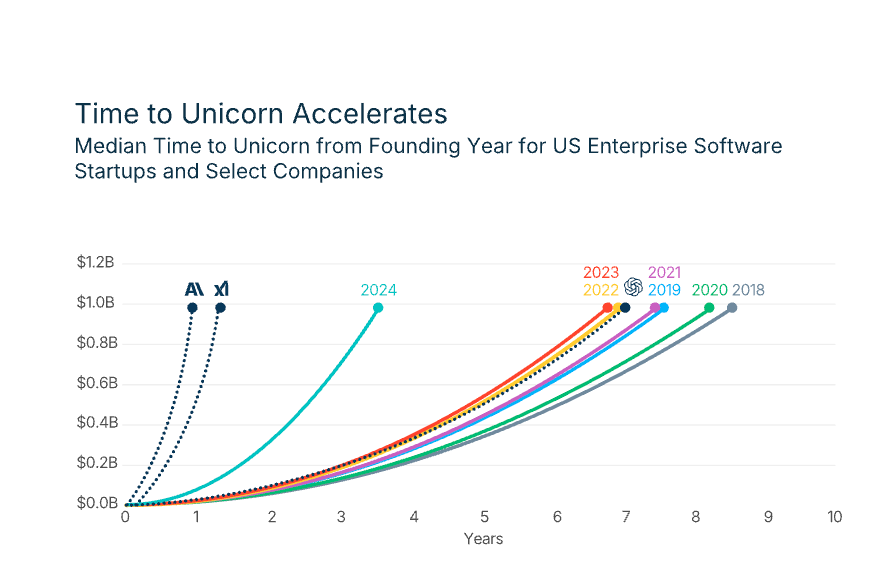
The report also demonstrated that the “time to unicorn” has accelerated:
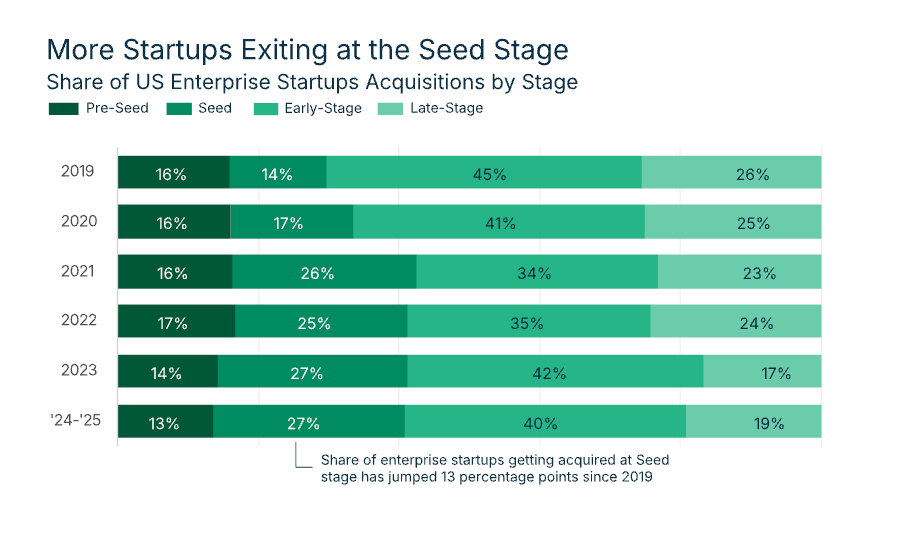
Another interesting insight is the role of seed-stage exits, with companies exiting at seed stage nearly 25% of the time, which is up 13% from 2019.
Resilient Cyber w/ Bob Ritchie - Securing Federal and Defense Digital Modernization
In this episode, I sit down with SAIC Chief Technology Officer (CTO) and longtime Federal/Defense leader Bob Ritchie to discuss his experience securing public sector digital modernization, including everything from large multi-cloud environments to zero trust, identity, and where things are headed with AI.
Bob starts discussing SAIC and his background there. He went from intern to CTO over 20 years with this public sector industry leader, including a brief stint with Capital One on the commercial side.
We covered the current state of the federal cloud community across multiple clouds (e.g., Azure, AWS, and GCP) and some of the challenges and opportunities on the security front.
We often hear phrases such as “identity is the new perimeter,” but the perimeter is porous and problematic, especially in large, disparate environments such as the Federal/Defense ecosystem. Bob touched on the current state of identity security in this ecosystem, where progress is being made and what challenges still need to be tackled.
The government is doing a big push towards Zero Trust, with the Cyber EO 14028, Federal/Defense ZT strategies, and more. But how much progress is being made on ZT, and where can we look for examples of innovation and success?
We dove into the rise of excitement and adoption of AI, GenAI, Agentic AI, and protocols such as MCP, A2A, and where the public sector community can lean into Agentic AI for use cases ranging from SecOps, AppSec, GRC, and more.
Bob explains how he balances a good business focus while staying deep in the weeds and proficient in relevant emerging technologies and nuances required as a CTO.
I’ve known Bob for several years, and you would be hard pressed to find a more competent technology leader. This is not one to miss!
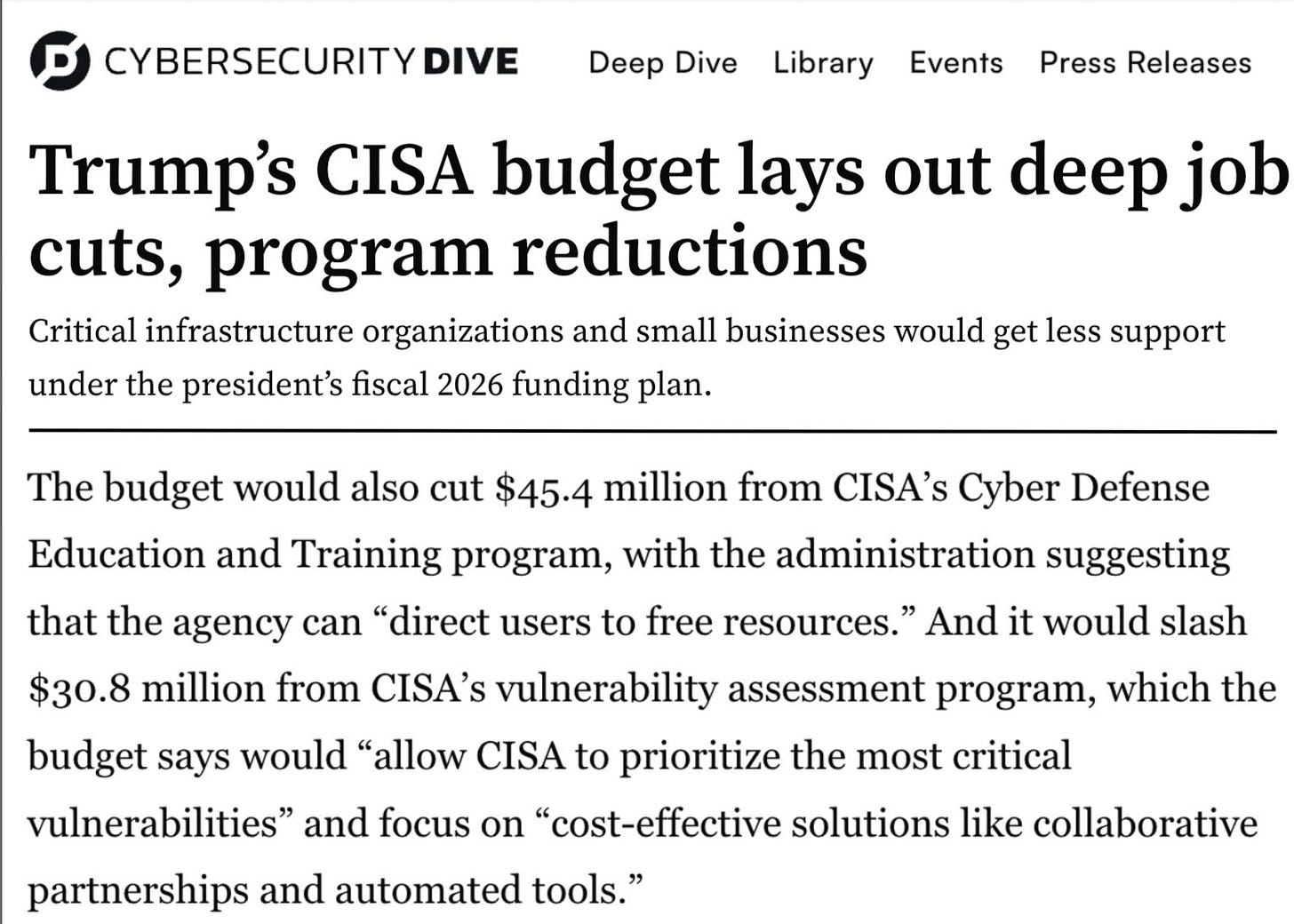
Trump’s CISA Budget Lays Out Deep Job Cuts, Program Reductions
There’s been a lot of focus on the current proposed budget, both in terms of spending and cuts. One area that got some attention is the proposed budget cuts to CISA in FY2026, which include $45.4 million cut from CISA’s Cyber Defense Education and Training Program, and a cut of $30.8 million to CISA’s vulnerability assessment program.
Some have asked what this may mean for things such as the CVE program, CISA’s Vulnrichment, CISA-alerts, CISA KEV and more which the community relies on.
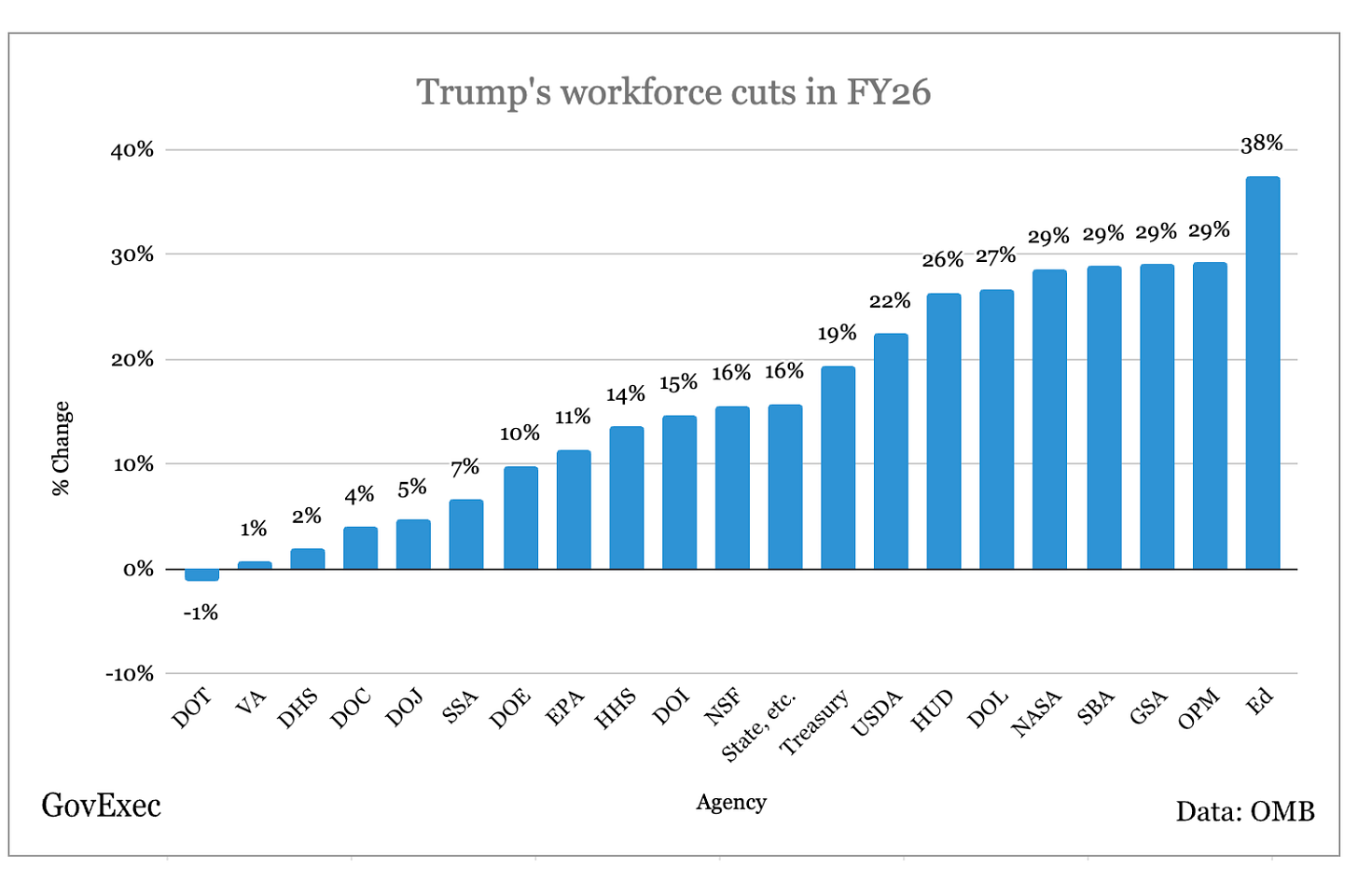
107,000 Federal Jobs Set to be Slashed Next Year
New details from the presidents projected FY2026 budget show a proposed 7% reduction to non-defense agencies next fiscal year, which is roughly 107,000 employees.
The below graph helps visualize where those cuts will occur based on agency.
AI
Cyber Opportunities and Risks of Agentic AI
As always, I've been looking for good resources on the intersection of Agentic AI and Cyber. This comprehensive piece from Haiman Wong and Tiffany Saade from R Street Institute was one of the best I found this past week.
➡️ It provides a comprehensive breakdown on AI and Agentic AI, and its rise and interest
➡️ Breaks down the potential cybersecurity benefits of Agentic AI, such as Continuous Monitoring, VulnMgt, real-time threat detection, and augmented decision support for the broader workforce
➡️ It also lays out potential cyber considerations and risks across the four layers of Agentic AI, which include Perception, Reasoning, Action, and Memory
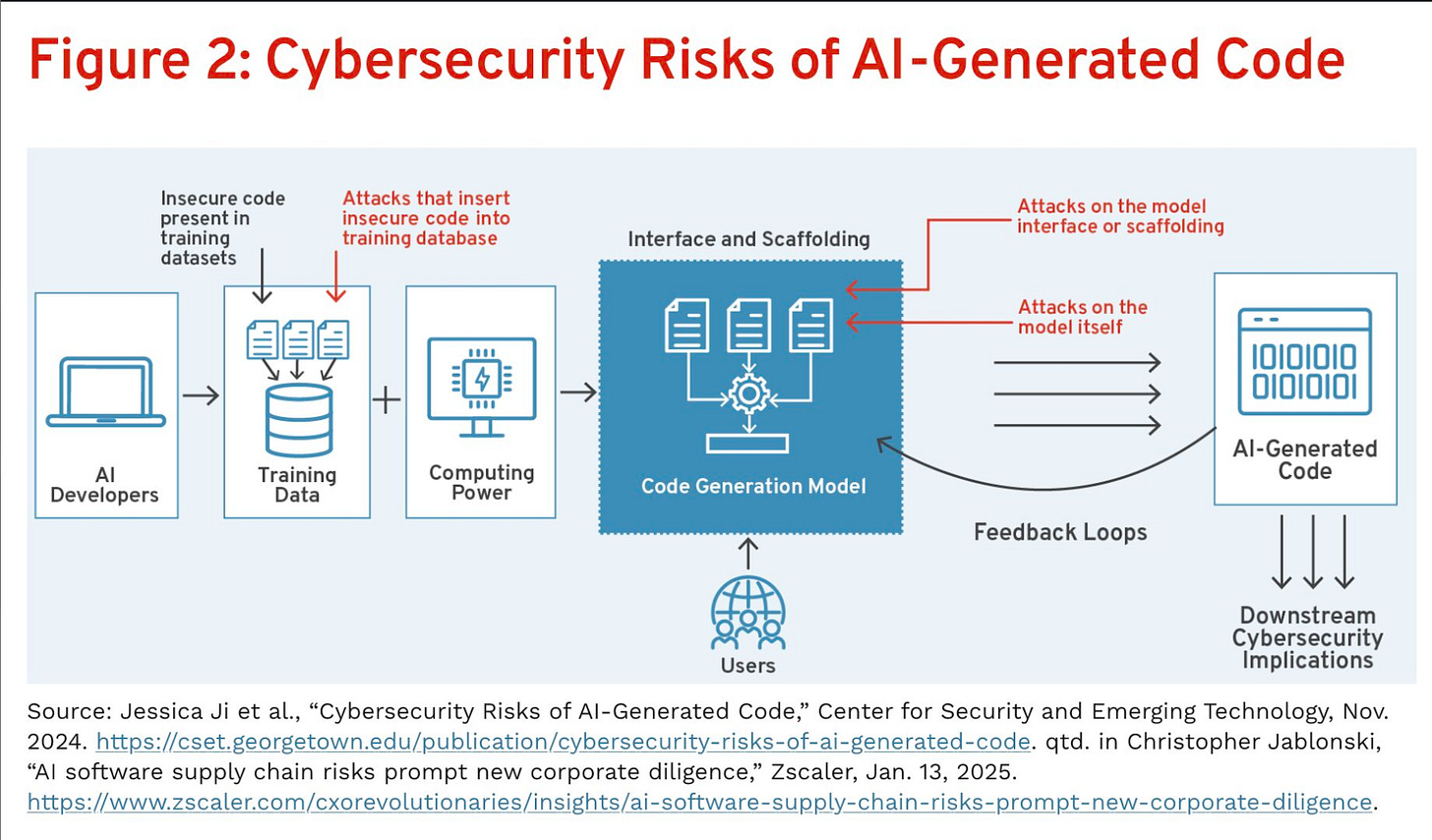
It cites good research on the cyber risks of AI-generated code, something the team and I at Endor Labs have discussed quite a bit.
➡️ It concludes by discussing the need for industry-wide policy-based approaches, technological innovative solutions, and responsible design and deployment for end users.
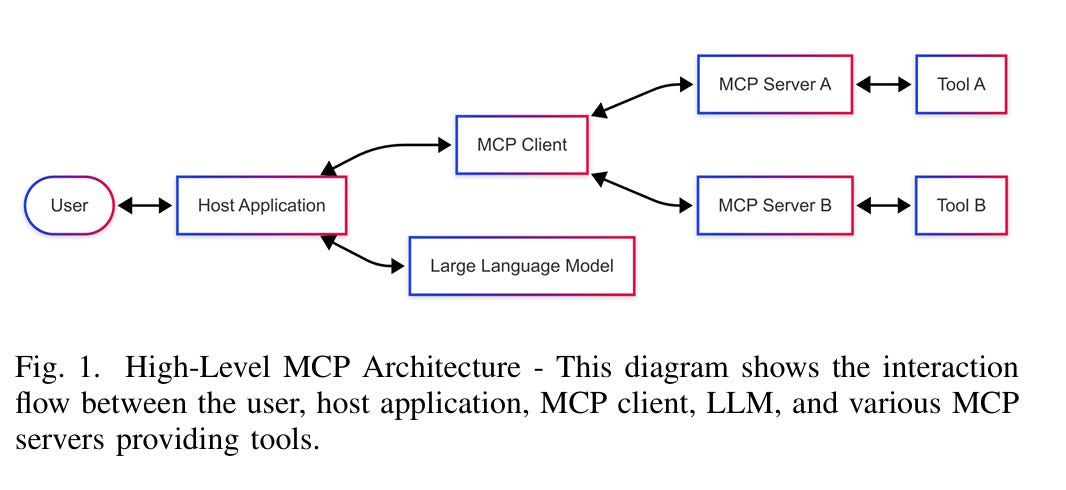
Mitigating MCP Attacks 🔓
We've seen the rapid rise in popularity of MCP to enable agentic AI
We've also seen teams like Invariant Labs and folks like Idan Habler, PhD, and Vineeth Sai Narajala lay out MCP vulnerabilities and potential attack paths.
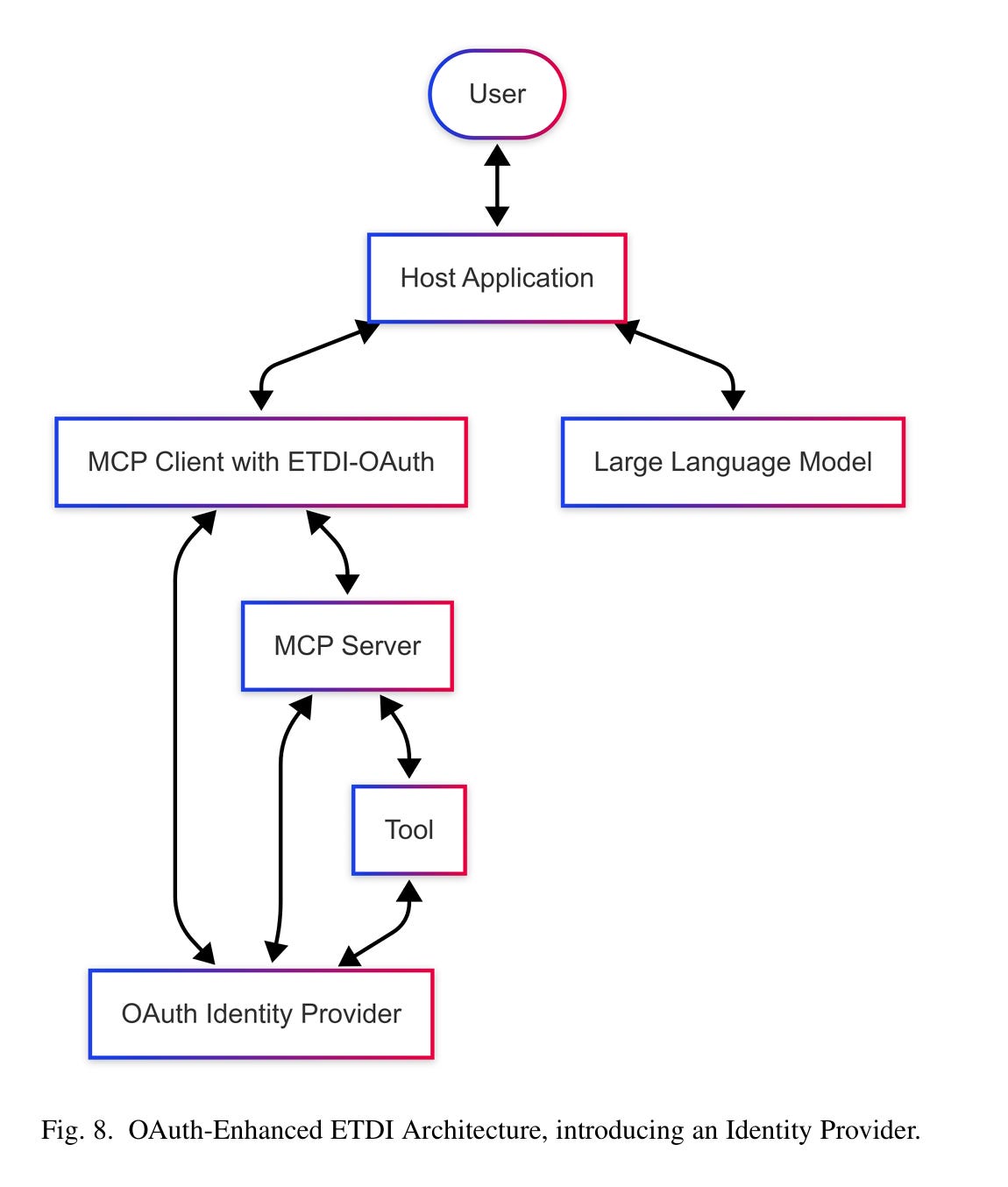
This latest paper introduces the "Enhanced Tool Definition Interface" (ETDI), a security extension to fortify the MCP.
It does so through cryptographic identity verification, immutable versioned tool definitions, and explicit permission management, leveraging OAuth 2.0 and addressing potential vulnerabilities and threats to MCP that many have pointed out.
As MCP, agents and agentic workflows become more pervasive, a secure implementation model will be necessary to ensure we don’t have a sprawling attack surface of insecure and poorly implemented MCP servers and workflows putting organizations at risk, and this paper is a great step down that path.
AppSec, Vulnerability Management and Software Supply Chain Security
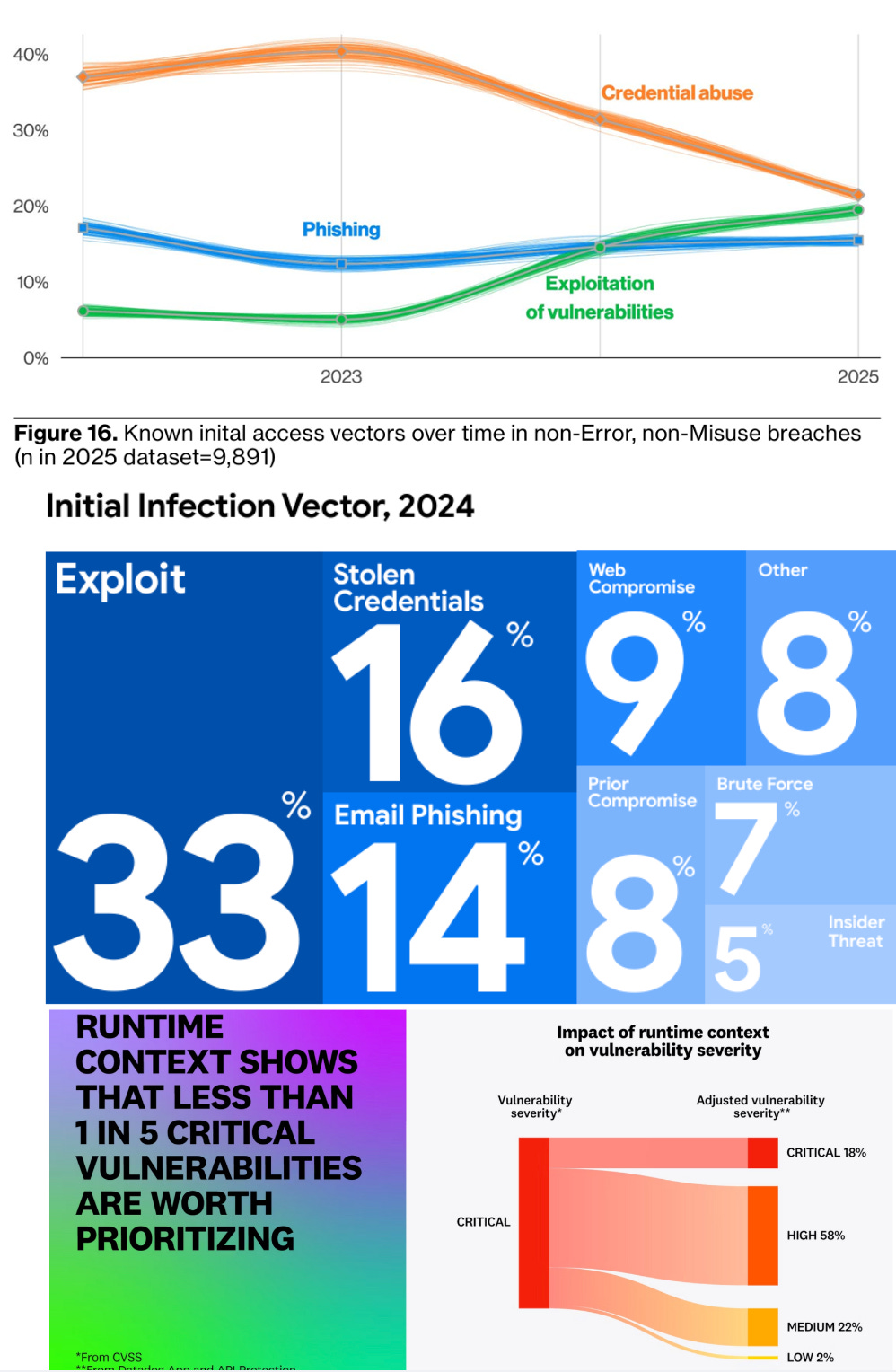
We're entering AppSec's "Exploitation Era" 📊
At least, that is the overarching theme of leading reports such as DBIR, M-Trends, and Datadog's DevSecOps report. In my latest piece with Endor Labs, I:
👿 Discuss the themes from these industry-leading reports, and the outsized role that application exploitation is playing
📈 The fact that traditional AppSec already struggled to keep pace, with vulnerability backlogs ballooning out of control, and teams clamoring for context from the noise
🤖 The role of AI-driven development and how it is only accelerating the gap and expanding the attack surface
💡 The focus of security must be to be an early adopter and innovator with AI, much like our Development and attacker peers; if we fail to do so, the existing problems and vulnerabilities are only going to be exacerbated
AI has the potential to be a force multiplier for AppSec, but it requires rethinking how we approach longstanding challenges as opportunities.
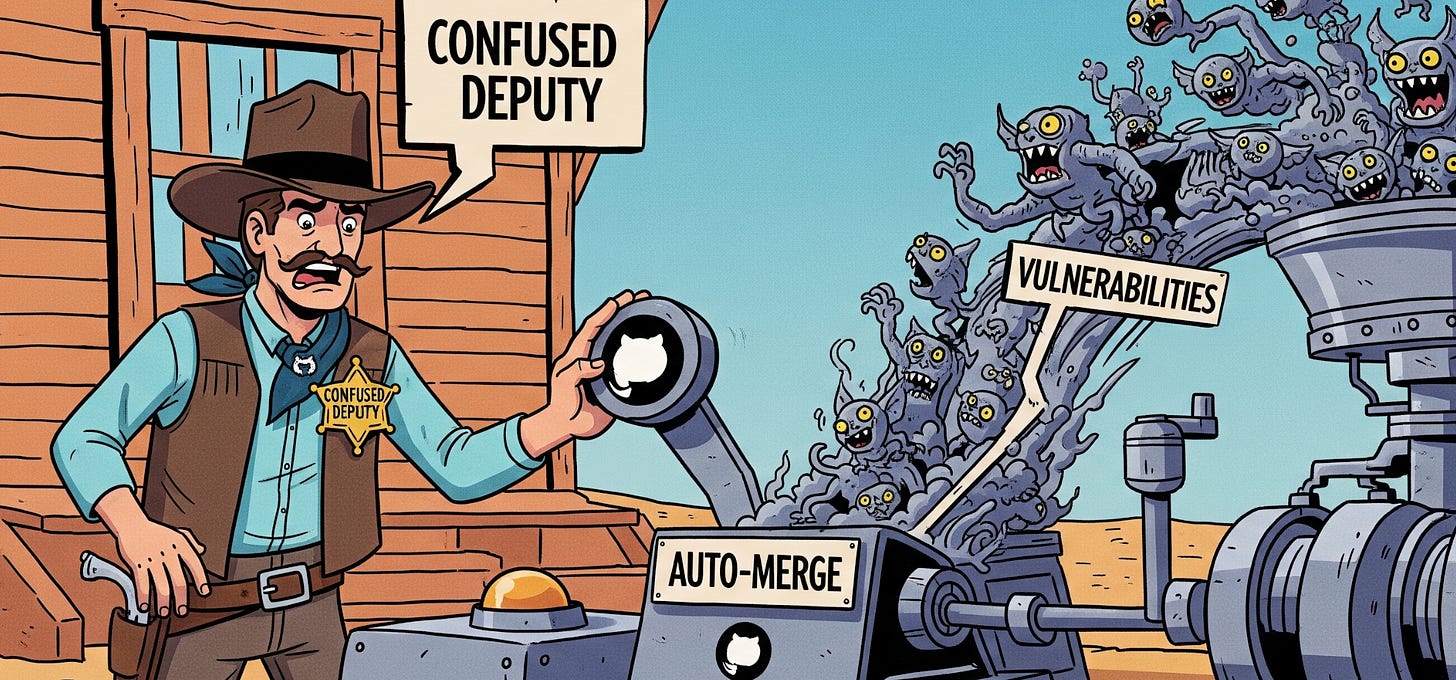
Weaponizing Dependendabot: Pwn Request at its finest
It’s always interesting to see the innovative and novel approaches both attackers and researchers come up with when it comes to exploiting systems. As shown in this piece, it isn’t just the code itself, but widely used projects and infrastructure which can play a role.
This article looks at the widely used and trusted Dependabot GitHub bot and how through “confused deputy” attacks it can be used to trick Dependabot into merging malicious code and even escalate into command injection and bypass branch protection rules.
Gartner’s Leaders’ Guide to Modern Machine IAM
By now you’ve likely seen me writing and speaking quite a bit about identity security, including Non-Human Identities (NHI)’s. Gartner recently released their “Leaders’ Guide to Modern Machine IAM”.
It lays out the state of Machine Identity and Access management and why this is a critical aspect of modern identity and access management (IAM) security. It also recognized firms such as Astrix as leaders in the space.
This marks Gartner’s first dedicated report on Machine IAM and demonstrates the continued growth of the sector and problem space, being recognized by one of the leader industry analyst firms. Several of us have been beating this drum for several years with deep dive pieces dedicated to the problem space, but I digress :)