Resilient Cyber Newsletter #46
CISO’s & Board Seats, 2026 White House Budget, Cyber “Hiring Crisis”, Agentic AI Threats, & The Future of CVE’s
Welcome
Welcome to another issue of the Resilient Cyber Newsletter. We’re back after RSA with a lot of great resources, including a masterclass from CrowdStrike CEO George Kurtz on CISO’s joining boards, what the 2026 White House budget is shaping up to be, myths of a cyber “hiring crisis” and where the CVE program and vulnerability management in general may be headed.
So, that said, here we go!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 45,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Who Has Access to Your Cloud Data? You Might Be Surprised
In today’s cloud, identity is everything — and it’s more complex than ever. With nonhuman identities now outnumbering people, traditional IAM struggles to keep up. Attackers know this, exploiting gaps to reach your most sensitive data. This blog explores the top identity governance challenges, real-world attack paths, and how to reduce risk by unifying security across your environment. Don't chase every permission — prioritize what matters.
Cyber Leadership & Market Dynamics
Project Discovery Wins RSAC Innovation Sandbox
As I mentioned last week, the winner of the RSAC Innovation Sandbox is ProjectDiscovery. They’re built around a widely popular and powerful vulnerability scanning tool called Nuclei.
Below, you can hear their RSAC pitch, led by Andy Cao, where he lays out the state of vulnerability management, legacy scanning tools, the need to focus on exploitability, and the robust massive open source community rallying around Nuclei and ProjectDiscovery.
The CISO’s Guide to Securing a Board Seat
Many CISOs and security leaders have aspirations of sitting on a board, serving as a board advisor, and board director. This talk from Crowdstrike CEO George Kurtz is a masterclass on the topic.
George walks through the evolution of the industry, and how cybersecurity has and is increasingly becoming a boardroom priority. This includes the increased digitization of society and businesses, rise of cyber attacks and more.
George emphasizes the diverse skillsets needed to transition to board roles, beyond just technical and cyber expertise to areas such as business and financial accumen, some of the learning resources available and the importance of proximity to the individuals and organizations seeking this sort of expertise.
If you have aspirations to serve on a board in your career, this is a great talk to catch!
White House Releases 2026 Budget Aims
The White House recently released their 2026 budget request and it is generating a lot of discussion. Like many, I watch this data from multiple perspectives, both as a tax paying citizen, but also as a CEO of a Government focused digital services company.
The proposed budget includes a $1 trillion dollar budget mark for the DoD, aligning with public comments from the President. Other agencies such as DHS are also set to see an increase in funding, while many others, not so much. Non-defense discretionary spending is set to decrease by 7.6% and it is anticipated that non-defense agencies are likely to see major cuts across the board, including a 22% cut from 2025 numbers.
NSC Official: Trump Administration Will “Change the Script” On Offensive Side
Alexei Bulazel, the senior director for cyber at the National Security Council (NSC) recent spoke at RSA and made comments about how the administration plans to wield the U.S.’s offensive cyber power.
The administration looks to be wanting to use offensive cyber to show that the constant cyber attacks and incidents on U.S. critical infrastructure and systems won’t be tolerated, especially by large nation state peers (e.g. China). This includes the largest hack ever of U.S. telecom providers last year by a group known as “Salt Typhoon”.
This may be controversial but this is a stance I agree with. We know we’re reluctant to escalate to a kinetic response when it comes to cyber attacks against U.S. systems and infrastructure, but we also can’t just sit idly while our peers and adversaries burrow in our networks, disrupt out infrastructure and impose real costs on our citizens.
The best way to get a bully to quit is to stand up to them, and if that means in the cyber domain, rather than escalating to a physical conflict, so be it.
NSA to Cut Up To 2,000 Civilian Roles
As part of larger workforce reconciliation and overhaul efforts, news broke that the NSA is projected to cut between 1,500 and 2,000 positions as part of the broader efforts to reduce the size of the U.S. Federal Government.
This works out to roughly 8% of the agencies workforce, and the deadline is anticipated to be by the end of this year, although it is said it could change and is part of the DoD’s push to reduce its budget by 8% YoY each year for the next 5 years.
There is also word that the CIA is anticipated to cut 1,200 positions and this comes after news of several high profile leaders being dismissed/replaced.
The Cybersecurity “Hiring Crisis”: Myth or Reality? A Data-Driven Perspective
We hear a TON about the cybersecurity workforce crisis. That said, how much of it is hype versus reality, and what other factors may be involved? This piece from Dr. Chase Cunningham digs into the topic.
As Chase lays out, the industry is actually flush with cash, and far from being too broke to afford cyber talent. However, the capital is disproportionately focused on startups and products, as opposed to hiring, retaining and building a robust security workforce. Chase uses RSA as an example, where there 427 new vendors, with $2.3 billion raised in just Q1 2025 alone.
As he says, this could hire 23,000 senior analysts with $100k salaries, however 92% of the vendors have ZERO full-time cyber professionals on staff based on crunchbase. Instead they have PhD’s in AI, and a large marketing/sales presence, on top of t their engineering teams. Cyber? Eh, not so much.
Chase goes on to rail against corporate delusion around JD’s, and how they have inflated unrealistic expectations for ridiculous cheap labor rates/salaries. Chase dives into the dirty secret that organizations want to replace humans with automation but don’t want to say the quiet part out loud. He points to metrics around tier-1 alerts now being fielded by AI, and the huge investment and spend in automated SOAR/SIEM tooling.
He points out an awful cycle of: more funding for tools, less for people. More breaches, more tool spending. Rinse and Repeat.
It’s a formula that is appealing to founders and investors, but for the actual cyber workforce doing the work? Not so much.
In my opinion this is grounded in a strong misunderstanding (or delusion) that security is something you buy, not something you do.
That isn’t correct, security is a process, NOT a product.
One thing I will disagree or take issue with in Chase’s piece is that we shouldn’t be looking to investors to spend on the cyber workforce. This is a misinterpretation of why venture capital even exists. Investors are investing for an ROI, and in the case of startups, for the power law (e.g. making 100x+) returns on their investment in some cases. Investors have little to nothing to gain by investing in enterprise companies to grow their cyber workforce.
The onus for spending there comes down to the enterprise. Again, the enterprise is looking for products as silver bullets for security, rather than rolling their sleeves up and doing the work of security itself.
AI
Agentic AI Threats & Mitigations 🤖
By now, it is no surprise that Agentic AI is a hot topic across the industry. We've even published some excellent guidance from the OWASP GenAI Security Project team on Agentic AI Security. That said, I found this Palo Alto Networks Unit 42 publication awesome.
They moved beyond the theoretical and created functional multi-agent applications, using leading open source agent frameworks to execute attacks and examine vulnerabilities and mitigations.
Some of the key findings:
⌨️ Prompt injection, while not always necessary, is still only of the most potent attack vectors
😈 Agentic architectures leave a lot of attack vectors and paths to consider from the LLM(s), agents, tooling, integrations, configurations, and more
🙋Credential compromise will remain key, as exposed NHIs tied to agents can be exploited for activities such as privilege escalation, lateral movement, sensitive data exposure, etc.
👉 Fundamental methods such as defense-in-depth will remain key, with robust mitigations across the involved architectures, systems, and data.
This is an excellent publication for Unit 42, and I recommend folks check it out and read it!
Model Context Protocol Security Best Practices
MCP continues to dominate discussions around AI and Agentic AI, which is why it was cool to see this authoritative page for MCP security best practices go live. The piece lays out attacks and mitigations against MCP, primary terminology, and architecture insights.
That said, it is clear the page is just being built out, so I would keep an eye out for it to have more added in time as MCP’s use and adoption matures. Below it shows normal OAuth proxy usage and then a malicious example as well.
Steve’s Chat Platform
I previously shared the book by Steve Wilson titled “The Developers Playbook for LLM Security”. Steven recently shared a companion open source project dubbed “Steve’s Chat Playground”, which lets users experiment with various chat models, personalities, guardrails and user interfaces locally and quickly.
This lets users get experience interacting with LLM chat bots and use different models, views, and guardrails all from their browser to explore how LLMs can be used maliciously or abused as well as what guardrails may be effective at mitigating LLM security risks.
The New Shadow IT: LLMs in the Wild
It is clear that GenAI and LLMs are the next technological wave, building on Cloud and SaaS before it. That said, we also seem poised to repeat the mistakes of the past when it comes to our behaviors that help foster shadow usage, rather than building deep relationships and functional partnerships with development, engineering and our business peers.
RAD Security Co-Founder Jimmy Mesta lays out how to avoid that in a recent article titled “The New Shadow IT: LLMs in the Wild”. Jimmy makes a lot of excellent points, similar to themes I tried to emphasize in an article of my own not too long ago about AI titled “Bringing Security Out of the Shadows”.
AI SBOM Generator: The First Open-Source Tool for AI Transparency
Over the last several years we’ve seen many incidents that highlighted the need for software transparency (someone even wrote a book with the same name!). The industry continues to lean into the importance of transparency, even in the AI era, with leaders such as Helen Oakley and Dmitry Raidman releasing an open source tool that helps produce AI BOM’s.
It uses the CycloneDX SBOM format and in addition to showing what components and libraries are involved, it can also show:
Where the model came from
What architecture and frameworks it uses
How and with what data it was trained on
Energy consumption and licensing
It orients around the industry-leading platform for open source models, Hugging Face.
CyberSecAI - Your Guide to Using AI For Cybersecurity
Chris Madden dropped this wealth of a resource this week titled “CyberSecAI”. It is a comprehensive guide and collection of tools for using AI for Cyber. It includes rich citations to publications and research on AI and Cyber, links to AI tools to help with CVE/CWE enrichment and analysis, deep dives into prompting and agents and much more.
I’m still working my way through this, but definitely seems like a promising resource so far!
AppSec, Vulnerability Management and Software Supply Chain Security (SSCS)
Q&A With the CVE Foundation
While the initial shock has died down about the near collapse of the CVE program, there is still a lot of ongoing discussion about the stability and resilience of our vulnerability management ecosystem.
One of the outcomes from that near collapse was the standing up of the CVE Foundation, which I have provided insights on previously. Now, a recent interview was released with Pete Allor of the CVE foundation, where he discusses the ongoing issues facing the program, why they stood up the CVE Foundation and where things may be headed in the future.
Beyond CVE: Building a Decentralized Future for Vulnerability Intelligence
Building on Josh Bressers article “Can We Trust CVE?” Chris Langton picks up discussing what the future of vulnerability intelligence could look like, if we moved away from the centralized model we have currently with CVE/NVD.
The article makes many critical points. Aside from the centralized single point of failure in terms of Governance that the NVD and CVE represents, Chris raises points around coverage gaps, temporal delays, scalability challenges and a disconnect between detection and remediation.
Chris makes the case that the real issue isn’t information/vulnerability numbering but information sharing. At it’s core, Chris makes the case that when one team discovers a vulnerability and fixes it, that the knowledge can quickly and effectively be shared with everyone else who is using that code.
He advocates for the use of the Transparency Exchange API (TEA), which would serve as a distributed, privacy-preserving network of vulnerability intelligence. TEA uses fundamental safeguards such as metadata separation, cryptographic attestation, verifiable timestamps and selective disclosure, each of which Chris defined further in his article.
The 3 key items needed to turn this vision into a reality are:
Standards adoption (e.g. SARIF, xBOM, and OCSF)
Infrastructure investment (to host and facilitate the TEA network)
Organizational participation (e.g. adoption)
Chris closes out the article discussing some challenges as well, such as regulatory alignment and data sensitivity concerns and how those could be successfully navigated.
How to Harden GitHub Actions: The Unofficial Guide
GitHub and GitHub actions have consistently become a topic of concern when discussing software supply chain attacks and have been involved in high profile incidents in recent years. Rami McCarthy and Shay Berkovich dropped this awesome guide from the team at Wiz that they put together.
As they point out this blog is a companion for GitHub’s official first-party guidance. Not only does their blog provide sound guidance, it shows how widely used GitHub Actions are, with nearly 60% of public repos using at least one GitHub Actions Workflow.
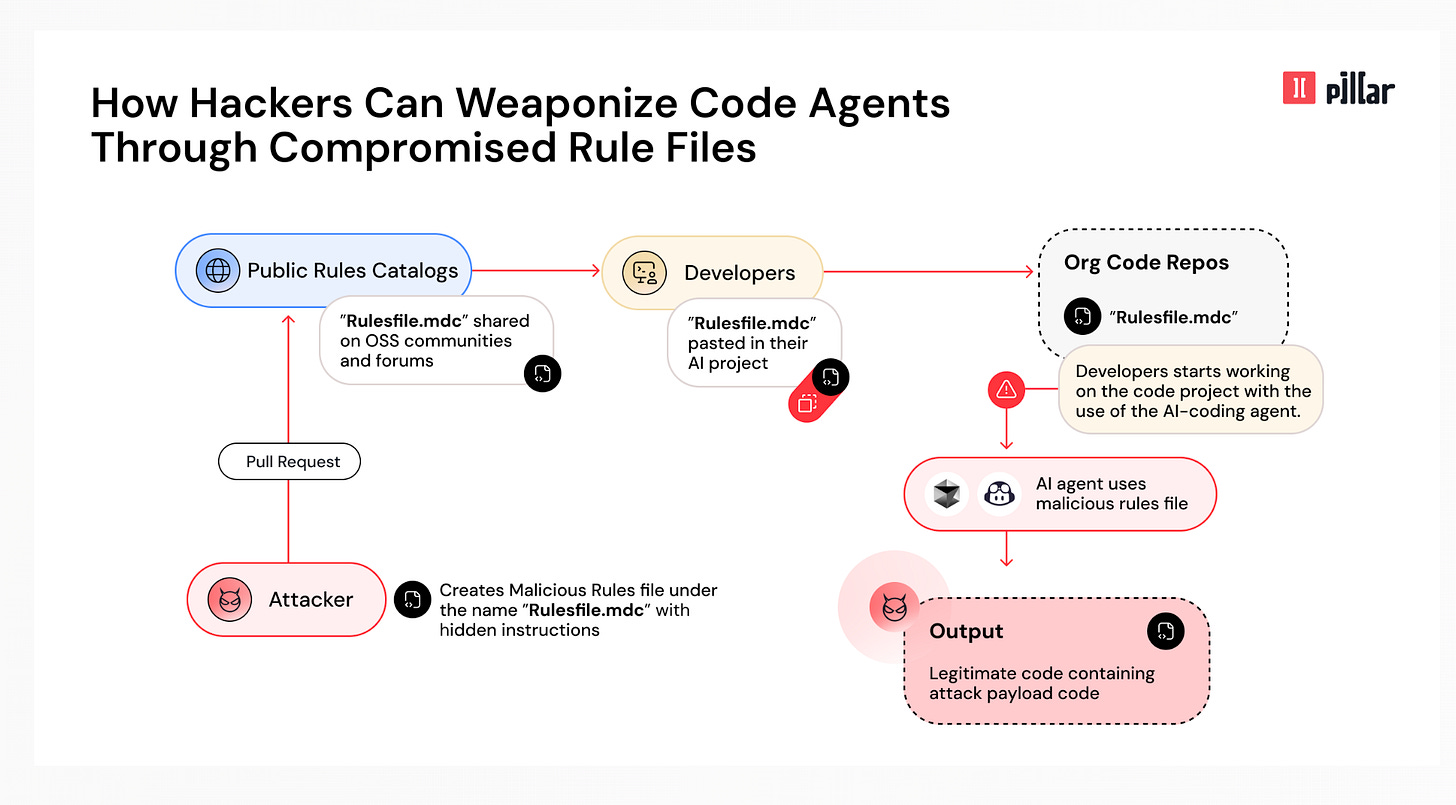
GitHub Now Provides a Warning About Hidden Unicode Text
If you’ve been following for a bit, you’ll recall I shared recently how AI security startup Pillar Security discovered by MCP can be targeted via unicode text. Researchers were able to show how attackers can hide Unicode characters in a text file and can have it be misinterpreted malicious by AI.
This was highlighted in Pillar’s research “Pillar Security: Rules File Backdoor” and “Hiding and Finding Text with Unicode Tags”.
It’s great to see an industry leading platform provider in GitHub take quick action on these findings and lead to systemic risk reduction across the ecosystem.
EPSS MCP Project
MCP continues to see a rise in use cases and implementation. The latest comes from Jerry Gamblin in the form of his EPSS MCP Project, described below:
This allows the integration of EPSS scoring into tools such as Claude Desktop and others, where developers can natively pull in EPSS exploitation probability scoring into their development workflows.