Resilient Cyber Newsletter #45
CISO’s Clarion Call to Industry, ProjectDiscovery Steals the Show, FedRAMP Updates, Cisco’s Open Source Security Model and Oligo Takes Apple “AirBorne”
Welcome!
Welcome to issue #45 of the Resilient Cyber Newsletter. I will be traveling to and back from RSA and on-site at RSA this week, so I will do my best to bring as many great resources as possible.
There will undoubtedly be a lot of announcements and news both during RSA and the week after the event. Below, I am sharing some of the updates as I do a bit of a brain dump, along with more to come next week.
I had an absolute blast at RSA, from doing a book signing with my friends at Endor Labs, walking the show floor, joining an OWASP panel on Agentic AI, a talk around NHI’s with the Astrix crew, and tons of random run-ins and insights with fellow practitioners and friends.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 45,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Get the Ultimate ISO 42001 Guide for AI Governance
AI has drastically changed the world we live in. What does this mean for information security professionals? More complex risks, a growing need for enhanced AI governance, and new standards to comply with all come to mind — but where do you get started?
In this guide, we’ll outline everything you need to know about the world’s first artificial intelligence framework: ISO 42001. Whether you’re a small startup or a large enterprise, this guide will equip you with the knowledge and resources to navigate the complex landscape of AI governance.
Cyber Leadership & Market Dynamics
One CISO’s Clarion Call to Industry
J.P. Morgan’s CISO Patrick Opet penned an open letter to industry last week that quickly made its rounds among cybersecurity leaders and the community. At a high level, Pat points out that SaaS sprawl is quickly enabling attackers to attack the entire ecosystem, leading to a “weakening of the global economic system.”
He lays out three key points:
Software providers must prioritize security over rushing features. Comprehensive security should be built in or enabled by default
We must modernize security architecture to optimize SaaS integration and minimize risk
Security practitioners must work collaboratively to prevent the abuse of interconnected systems
At a more granular level, Pat points out the software supply chain risks of the pervasive SaaS ecosystem and how attackers are taking advantage of it, including OAuth connections and the underlying credentials.
I have been warning about this risk for several years, even leading the Cloud Security Alliance’s publication of SaaS Governance Best Practices for Cloud Customers years ago.
Over the last several years, the problem has only gotten worse, which Pat also validates in his post. Organizations are consuming hundreds or even thousands of SaaS providers, often quickly being enabled and integrated with little oversight or governance, and no involvement by security teams.
We often hear “security is the new perimeter, " which is true. Still, that perimeter is porous and problematic as organizations haphazardly integrate with SaaS software without consideration for identity security, what data is involved, who has access, when access will be removed, what activities are authorized, or the security of the providers involved. I mean actual security, not paper credentials such as SOC2, FedRAMP, et. al.
The hype cycle of AI is exacerbating these behaviors as vendors rush to integrate AI into their products and services and race for speed to market amongst competitors. What will be interesting to see now is what other large customers join Pat’s call, especially given that most SMB’s lack the leverage or purchasing power to change the vendor's behavior.
Project Discovery Wins RSAC Innovation Sandbox 2025
Security startup ProjectDiscovery won this week's RSAC Innovation Sandbox competition. This highly visible and sought-after award often indicates a bright future for the awardees.
For those unfamiliar with ProjectDiscovery, they help detect real, exploitable vulnerabilities leveraging Nuclei to minimize false positives, keep teams from drowning in noise and toil, and create customized rules for their specific environment, findings, threats, and more.
I got a chance to chat with Andy Cao from ProjectDiscovery onsite at RSA, and I will be having him on my Resilient Cyber Show soon, so stay tuned for that!
Palo Alto to Acquire AI Startup Protect AI
This week, it was announced that Palo Alto signed an intent to acquire AI security startup Protect AI. This coincided with RSA and marked one of the largest acquisitions focused on AI by an industry cyber leader in Palo Alto Networks.
AI and AI security are playing an outsized role in fundraising, investments, and now acquisitions. Palo Alto mentions that the acquisition and addition of Protect AI will play a role in their comprehensive AI security platform, Prisma AIRS.
FedRAMP 20x - One Month in and Moving Fast
The U.S. government's cloud security program, FedRAMP, is still undergoing significant changes. One month after announcing its “FedRAMP 20x” initiative, FedRAMP recently released a blog recapping some of its activities.
Some key takeaways include:
They have authorized 29 new cloud services, 73 in 2025 alone, leading to over 400 authorized services.
Added two new 3PAOs
Responded to thousands of inbound messages, launched their community working groups, and hosted several meetings on automation, assessments, and more
Developed new and improved FedRAMP boundary guidance
Moving towards GSA’s AI goals
And much more. The FedRAMP program is indeed undergoing massive changes and looking to drive improvements. How that all will shake out and what it means for compliance security remains to be seen.
Comparing Findings from DBIR and M-Trends
I shared how Verizon’s Data Breach Investigation Report (DBIR) and Mandiant’s M-Trends report dropped last week. These are two widely cited leading reports, and I recently came across a resource someone put together combining insights from both, as seen in the table above.
One key theme from both reports was that exploitation of vulnerability is increasing, making AppSec as important as ever. I suspect in the coming years we will continue to see organizations innovate in various areas, such as using AI to improve AppSec and VulnMgt, focusing on runtime exploitability (e.g. Oligo and others) and also on Secure-by-Design principles and implementations to try and mitigate the growing risks of vulnerability exploitation.
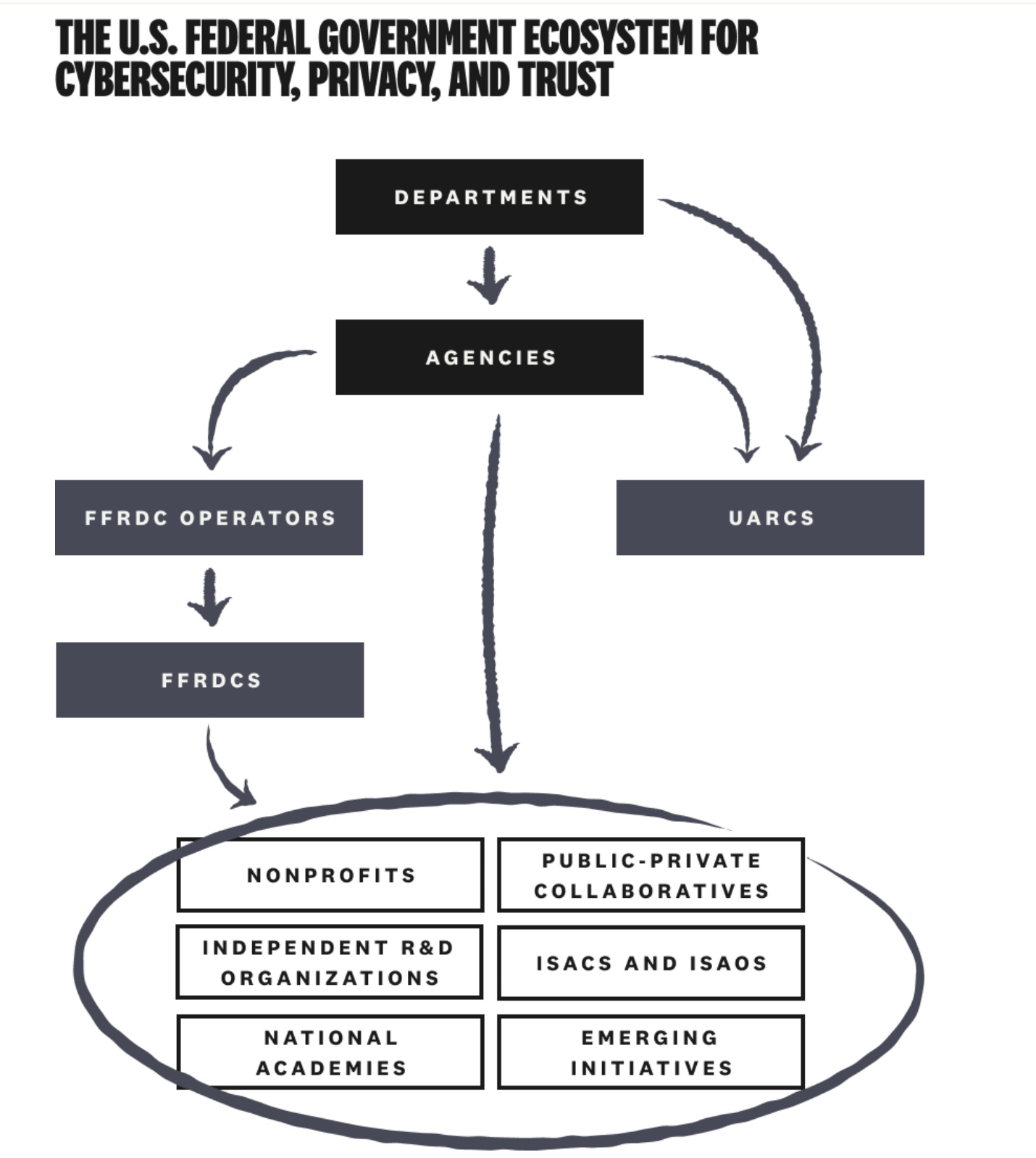
Mapping the U.S. Federal Government Ecosystem for Cybersecurity, Privacy, and Trust
Amid the CVE turmoil in recent weeks, many are now taking a closer look and even scrutinizing the U.S. federal IT and cyber ecosystem. In this well-researched piece by Cole of Strategy of Security, he deeply dives into the federally funded cyber, privacy, and trust initiatives.
Ironically, his look at who and where the money comes from is similar to what DOGE has been digging into and mapping without the cyber focus. Cole lays out how these organizations are connected, the complex interdependencies these relationships create, and how funding flows (or doesn’t) to the entities that rely on it for the various cyber activities.
AI
Cisco Foundation AI Group Releases Open Source Security Model
This purpose-built cybersecurity model combines deep domain expertise with leading open-source foundation models to help tackle security-specific tasks and use cases. Cisco mentions that despite its size, it performs as well as models 10x its size, and it is specifically trained on key fundamental security data and sources such as vulnerability databases, threat intelligence, security tooling, compliance frameworks, and guidance, among many more.
This represents a powerful tool security practitioners can add to their arsenal. It is custom-built for the world of activities we focus on, rather than broader foundation models, which are more generalist and not as focused on cybersecurity in particular.
Cisco laid out some potential use cases for SOC acceleration, threat defense, secure code reviews, compliance assessment, and more. It will be interesting to see the security community embrace and explore the art of the possible with a purpose-built model such as this.
The model is available for download from HuggingFace, and a comprehensive research paper is also available for those interested.
How MCP Servers Can Steal Your Conversation History
Security researchers and teams continue to explore the potential vulnerabilities and weaknesses associated with MCP and how it can be abused, as its adoption skyrockets.
This latest piece comes from Trail of Bits, which demonstrates a “line jumping” vulnerability in MCP and tricks it into executing malicious commands on your workstation.
This is done by injecting trigger phrases into tool descriptions to exfiltrate a user’s entire conversation history, including sensitive data such as API keys, internal project names, financial data, etc.
This great and concise write-up demonstrates some of the problems that lie ahead as MCP becomes a de facto method for extending the capabilities of LLMs and agentic architectures.
How to be a Security Person AI/ML Teams Don’t Hate
One challenge in security is that we’re often viewed as blockers, gatekeepers, the office of no, and other negative terms you’ve all inevitably heard. How do we avoid perpetuating this cycle with the latest wave of AI?
This piece from Frank Wang lays out some sound recommendations on just that. His advice includes understanding how security fits into the AI/ML lifecycle and how your organization uses AI. Are they using AI model providers, self-hosting open source models, or using specific services? These questions and many more you can and should be asking to understand how the organization uses this technology and what business outcomes they aim for through their usage.
Key focus areas of his article include:
Model development
Training and fine-tuning
Deployment
These are fundamental areas for security practitioners to familiarize themselves with. From here, I recommend diving into industry guidance and frameworks from OWASP, Cloud Security Alliance, and others to understand how you can effectively implement security in these various phases of the AI/ML lifecycle and organizational adoption.
Frank also makes the astute recommendation to facilitate their experimentation securely, rather than shut it down. This is such a critical point because in my experience, if you look to shut it down, all you do is foster shadow usage that security is unaware of and unable to secure.
Insights Around Malicious AI Usage
We often hear that AI will be a double-edged sword, arming attackers but also being a tool defenders can wield. That said, it can be challenging to gain insights into how attackers use and potentially abuse this technology for their nefarious intent. This recent piece from Anthropic is excellent, titled "Detecting and Malicious Use of Claude."
It sheds light on activities such as:
📢 Malicious social influence campaigns
🔑 Attempts to scale account credential discovery and compromise
😈 Malware development and application exploitation
It is really cool to see one of the largest model providers share these insights and actively take steps to not just share them with the community but also counter potential malicious usage of their offerings.
AppSec, Vulnerability Management, and Software Supply Chain
Oligo Discovers “AirBorne” Vulnerability Impacting Millions of Apple Devices
Runtime AppSec security leader Oligo recently disclosed a vulnerability they’ve dubbed “AirBorne,” which involves Apple’s AirPlay protocol and likely impacts millions of Apple devices.
The Oligo research team discovered a massive vulnerability, especially given the number of devices it potentially impacts and how pervasive Apple is as a product vendor. Additionally, in their detailed write-up of the vulnerability, they explain how it can lead to Zero/One-Click RCE, Sensitive Data Disclosure, ACL/User Interaction Bypass, and more, making it not just widely applicable but also highly impactful should it be exploited.
Oligo's blog lays out the technical details of the vulnerability and how they worked with Apple to follow a responsible vulnerability disclosure approach, allowing Apple to roll out patches before the vulnerability was publicly disclosed.
The Wired team also released an excellent article discussing the vulnerability and its potential reach and impact. Wired outlines how it is likely that many Apple devices will receive updates and be protected, many smart home devices do not routinely receive similar updates, and those that are AirPlay compatible likely may remain vulnerable for years to come.
The Oligo blog also demonstrates the exploit on various device types, including MacOS.
CISA Warns Threat Hunting Staff to Stop Using Censys & Virus Total
Challenges continue to flow from the Federal cybersecurity ecosystem, with a recent announcement by CISA that hundreds of staff were notified to quit using Censys and VirusTotal, two widely used security tools. Amid ongoing cuts and reductions, the agency is seeking alternative tools.
Vulnerability Enumeration Conundrum – an Open Source Perspective on CVE and CWE
OpenSSF and OWASP released a joint statement on the CVE funding crisis and the need for the open source community to work together to ensure more resilience around vulnerability identifiers and that critical software ecosystem entities such as CVE and CWE remain stable.
They also laid out how the now growing fragmentation of vulnerability identifiers and databases will just add to the complexity and challenges associated with vulnerability management, making an already nearly impossible task even worse.
The Collapse of Trust: Rethinking Cyber’s Public-Private Divide in the Wake of the NVD Crisis
We’re just weeks out from the near collapse of the CVE program, which sent shockwaves through the AppSec community. In this piece, the author lays out how the near collapse of CVE and the struggles of NVD shouldn’t be surprising and argues we’ve outsourced too much of our cyber infrastructure to the federal government, which is often underfunded, understaffed and recently, increasingly politically polarizing.
They discuss the “triple threat” undermining U.S. cyber leadership:
Brain drain at federal agencies
Politicization of cyber
Public-private partnership fatigue
The author advocate that we build a private, globally funded vulnerability infrastructure, professionalize the cyber field and that the government isn’t the answer.
While I don’t agree with all of the points being made throughout the article, they are very though provoking.