Resilient Cyber Newsletter #42
White Collar Recesssion, Sec-Gemini, CISO Mindmap 2025, MCP and the Future of AI Tooling & CISO Tradecraft
Welcome
Welcome to Issue #42 of the Resilient Cyber Newsletter.
It’s been quite a week, with actions around tariffs, market reactions, the continued buzz of MCP for Agentic AI tooling, and pre-RSA hype.
That said, let’s get to it!
Secure your cloud workspace before, during and after a breach
Your Google Workspace or Microsoft 365 platform is where your company works, communicates, and collaborates — it’s your business’s critical infrastructure. Protecting it with a patchwork of native security and point solutions leaves gaps – the biggest being visibility after an attacker has made it inside.
Material Security is purpose-built to protect the entire cloud workspace – email, data, and accounts. With deep integration and powerful automations, Material prevents and detects a wider range of threats, responds to active attacks faster, and secures data and accounts even after a breach. All within a platform that fits seamlessly into existing workflows–making your security team’s jobs easier, and protecting your users without slowing them down. See Material in action today!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 45,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cyber Leadership & Market Dynamics
White Collar Recession?
By now, you’ve seen the headlines about tariffs and the market reactions across major media outlets. Like others, I have been digging into the topic, understanding what the potential implications are for my company, the industry I work in, the broader economy, and, of course, my family.
That is why I was really glad I stumbled across Citrini Research’s Substack and this collaboration between them and The Last Bear Standing, economic-focused Substacks, both of which I now subscribe to.
In this joint piece between the authors, they discuss the Haves vs. Have Nots: Exploring a Wealth-Effect Driven Slowdown. On one hand some have written off the stock market reaction as not being relevant, and in a recent interview, Treasury Secretary Scott Bessent even quipped the stock market metrics, to some extent, are a “MAG-7 problem, not a MAGA problem.”’
However, as Citrini and Last Bear Standing point out in this article, we may be witnessing a government policy-driven recession due to increasing concentration and wealth, but more notably, the fact that the top 10% of earners now account for half of all spending.
They point out that tariffs are likely to have more of an impact on low and middle-income consumers than on high-income households. How this ties into the software industry and potentially cybersecurity is when they begin to discuss the potential for an “AI-Powered Recession”, explaining that the rise of LLMs hangs over white-collar employees like a Sword of Damocles.
This means that with the economic impacts now reverberating throughout the economy and the Trump administration being more focused on populist narratives and potentially blue-collar workers, there is a path where organizations increasingly lean into LLMs and AI even if it is just “good enough” for now if it offers cost savings and the ability to trim manual human labor from knowledge workers which of course can be incredibly capital intensive.
They cross-link to an article titled “The White-Collar Recession 2025”, showing findings such as:
The nation’s largest law firms cut entry-level hiring by nearly 25% over previous years
Ad agencies and creative roles are seeing a push toward AI
Vanguard reported that hiring for positions making > $96k is at a decade-low
What this increased exposure to AI ramifications means for Cybersecurity still remains to be seen. While we’re certainly among that community of knowledge workers in the economy, and startups, investors, and industry leaders are rapidly exploring the potential for AI across AppSec, SecOps, GRC, and more, we are not to a point yet where many are willing to entirely outsource decision-making, for example, to AI.
Due to its non-deterministic nature, ability to hallucinate and other challenges, AI is still in its infancy in terms of widespread adoption in Cybersecurity, specifically without a human-in-the-loop, to take actions on data and decisions.
That said, with the rise of Agentic AI and autonomy for agents, this may change in the future as models improve and organizations’ risk tolerances, potentially adjusting to the new reality both technologically and economically.
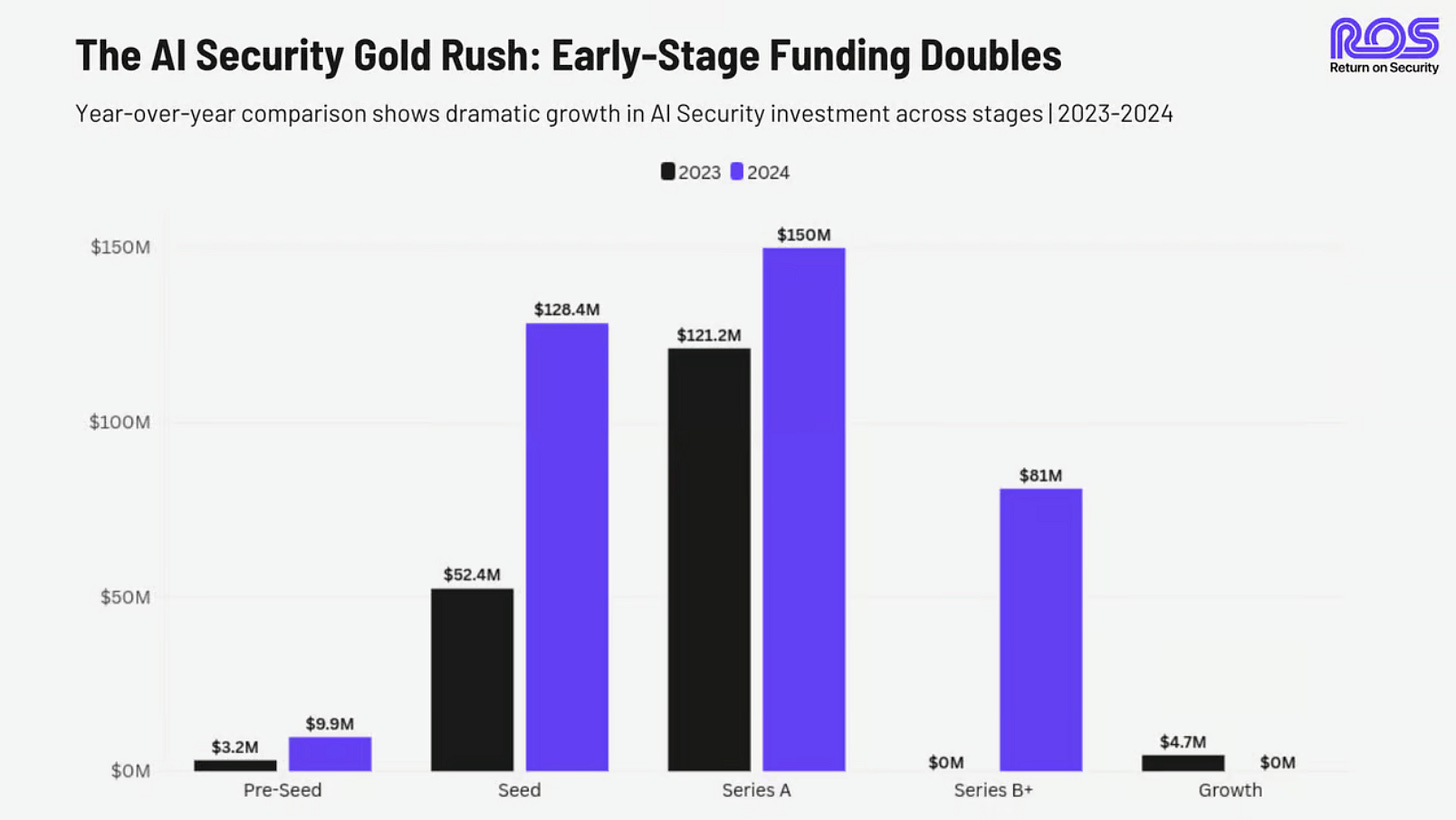
What we do know is that AI is driving a significant impact on company startup valuations, funding rounds, and investments made within the Cybersecurity ecosystem. Thus, it is clear where the focus is for the future of the cybersecurity ecosystem, which heavily involves the potential of AI.
This can be seen in the image below from my friend Mike Privette at Return on Security and his “State of the Cybersecurity Market in 2024”:
Tensions and Opportunities for Cyber Founders 🤼
There are many things to consider when founding a cybersecurity company. From what to focus on, the founding team, the type of customers to pursue, and much more. Jason Chan and Ross Haleliuk of Venture in Security put together an awesome article discussing some of those key considerations:
Time to value vs. moat, meaning focusing on how quickly and easily customers can utilize your technology while also building a remarkable user experience that becomes your differentiation among competitors
Speaking of differentiation, focusing on this vs. speed to market. As they say, many architectures and integrations look similar these days, with the pervasiveness of the cloud, for example, but what differentiates things is the user experience and the outcomes organizations can achieve with your product
Platform vs. Best of Breed, which is a bit of a false dichotomy, as ever, the platform starts as a point product that grows either through organic development or M&A additions- Will you look to create a new category or build in an existing market?
On one hand, greenfield is nice but requires big investments around the market and customer education, where building in an existing market can mean more competition and the ability to build on the momentum of earlier competitors. They break down many other key points founders and startups should consider, including compliance, sales strategies, and more. They also argue that cybersecurity as a market is still in the “Stone Age.”
Great read for those looking to make the leap into founding a company and those earlier on the journey.
Feinberg Initiates Pentagon’s Implementation of DOGE-Influenced Regulatory Review
As I have discussed in past issues, one of the key focus areas for the current Trump administration is decreasing the “regulatory burden,” which includes issuing an Executive Order (EO) with this focus.
Deputy Secretary of Defense Stephen Feinburg recently issued a new memorandum directing the Pentagon to implement the EO to pare back Federal agency regulations.
This article from Defense Scoop sheds light on what that may impact, including potentially the highly polarizing Cybersecurity Maturity Model Certification (CMMC) compliance program. Some argue the program is key to protecting the DoD and Defense Industrial Base (DIB), while others argue that it will harm small businesses and impose significant costs to the firms that can afford it least among the DIB.
AI Raises a Big Question, But Legacy Industries Have Already Answered It
There are a lot of interesting implications for the software industry when it comes to investment, revenue, and profits due to the rise of AI. This article takes a look at the three predominant business models:
You own the solution, using the vendor’s tools to do so
You can outsource the solution to another party
You can do something in between, operating alongside someone else to solve problems
Historically, the most profitable software companies have let customers own their data while providing software tools to facilitate various workflows. With the rise of AI and agents, platforms can innovate faster, create further separation between those who create and maintain data and those who rely on it, and make service companies more efficient and effective.
The article states companies now need to decide to either build core platforms or outsource undifferentiated services.
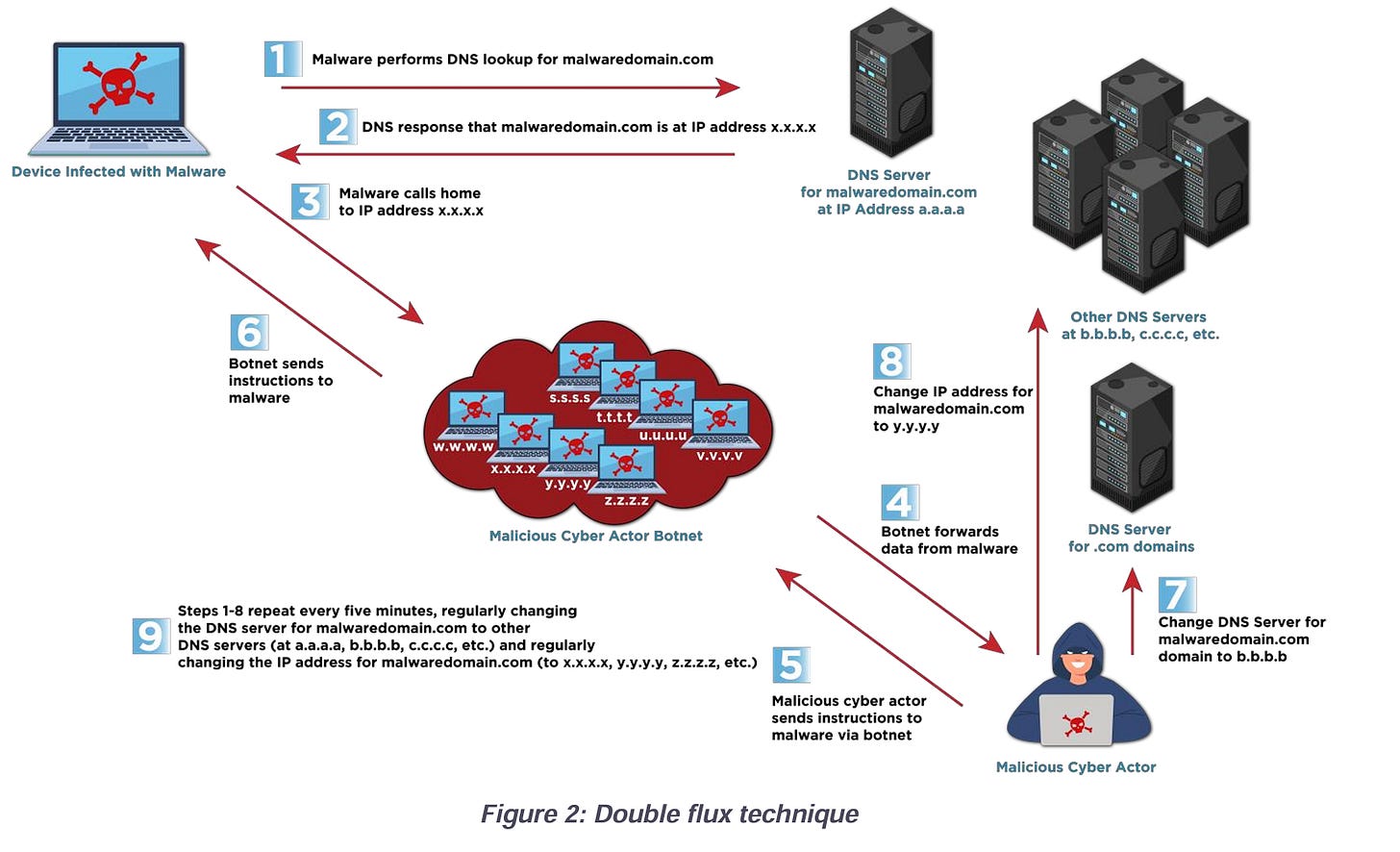
NSA & CISA Issue Fast Flux National Security Cyber Advisory
This past week, the NSA, CISA, and other international cyber partners issued a Cybersecurity Advisory focused on “Fast Flux,” calling it a national security threat targeting ISPs and Cyber Service Providers.
This involves malicious cyber actors using techniques to obfuscate their locations and malicious servers by rapidly changing DNS records and creating resilient, highly available C2 infrastructure to conceal their activities.
The advisory highlights single and double “flux” techniques, each aimed at concealing their IP address and location, making activities such as incident response and threat hunting increasingly difficult.
How LLMs Finally Solve the “Black Box” Problem for Security Products
One of the longstanding challenges in security is that many of the products in the ecosystem are considered “black boxes,” or essentially something that we, as customers, have little visibility and understanding of under the hood.
Harry Wetherald writes an interesting piece on the role that LLMs can potentially play in solving this problem related to security Products. Harry makes the case that a single call to an LLM definitely lacks full clarity since LLMs are probabilistic by nature and non-deterministic, but when we shift toward agents. This will involve tens of calls to LLMs coupled with chain-of-thought reasoning, the ability to follow the logic of why actions were taken, and the context based on the data involved coupled with the prompts fed to the LLMs.
I understand Harry's perspective and somewhat agree with it. However, I think it will get challenging when agents across large enterprise environments quickly outnumber us and organizations struggle to understand what agents are active in the enterprise and what systems and data they’re interacting with, let alone why they carry out the actions they have.
This is why I suspect we will see some security vendors capitalize on the rise of Agentic AI with products focused on governance, visibility, and securing the agents and their interactions.
AI
Google Announces Sec-Gemini v1
We’ve heard a ton about LLMs and use cases for increased development productivity and AI-driven development. We know attackers leverage AI to be more effective at everything from reconnaissance to exploitation.
But defenders should also leverage this revolutionary technology. That’s why it’s really cool to see Google announce Sec-Gemini v1 this week. It's a purpose-built model combining Gemini's capabilities with security intelligence and tooling.
This includes insights into threat intelligence and OSV for vulnerabilities and exploitation insights. It’s exciting to see this angle of LLM’s get more focus and to think about the potential this can unlock for defenders in the future!
Why SOCs are Turning to AI Agents
SecOps and the SOC continue to be primary areas where the industry hopes for the potential of AI, LLMs, and Agents. In this piece, Filipstojkovski breaks down why the SOC is looking to turn to AI agents.
Steps AI agents can and will help with include:
Alert deduplication
Alert classification by use case
Alert grouping by asset
IoC enrichment
Machine and Account Enrichment
He also discusses the different types of agents and their role in modernizing the SOC with AI.
While there is a lot of promise for AI agents in the SOC, there are also plenty of of challenges ahead too, which Filip lays out, such as:
Transparency, explainability, and trust
Data quality, blind spots, and bias
Edge cases and configuration complexities
How to Use GenAI in Cybersecurity Operations
The exploration of GenAI and LLMs for Cyber continues to unfold across countless cyber niches, such as GRC, AppSec, SecOps, and more. This concise piece from Rafeeq Rehman summarizes some key areas in which GenAI can help in cyber operations.
CISO MindMap 2025: What do InfoSec Professionals Really Do?
Regarding Refeeq, I meant to share his latest version of the CISO Mindmap. I’ve been able to help contribute to it in the past, along with many other security leaders I highly respect.
Trying to concisely capture what CISOs do is no easy task, especially as their responsibilities continue to grow without an end in sight. The mindmap below attempts to do that, covering various key areas, responsibilities, and tasks within those domains.
Refeeq’s blog, which discusses the mindmap, walks through key areas seeing growth, such as the need to secure GenAI due to the rapid enterprise adoption we have seen in this area. It also makes some fundamental recommendations to get started, such as standards and governance, inventory, responsible use, and more.
GenAI Security 🤖
Like everyone else, I’m upskilling in AI security. That’s why I’m really enjoying this awesome new book from Ken Huang, CISSP. As I’ve mentioned before, Ken is one of the leading industry voices on AI security. This book covers excellent topics such as:
The fundamentals of GenAI and securing it
Establishing policies, processes, and mature GenAI security practices
GenAI security in areas such as SecOps and AppSec
Some of the leading tools, solutions, and vendors tackling this emerging technology from the security angle
It’s definitely worth checking out. Its interesting blend of theory and practice appeals to audiences from both the academic and practitioner communities.
MCP and the Future of AI Tooling
By now, it is clear that the Model Context Protocol (MCP) is seeing rapid adoption. Organizations are very excited about Agentic AI and its ability to enable agent-based workflows, leverage tools, and perform autonomous tasks with data and services.
This is a great blog from Andreessen Horowitz discussing:
🤔 What is MCP?
⭐ Popular Use Cases
♾️ The MCP Ecosystem
🚀 Future Possibilities and the Implications of AI Tooling
This is a great read both for those looking to better understand MCP, as well as thinking about how it will change enterprises moving forward.
A lot of key security considerations to go along with it this potential too!
They also provided a MCP Market Map:
AppSec, Vulnerability Management, and Software Supply Chain
CISO Tradecraft - Vulnerability Management, Software Supply Chain and Compliance
I’ve been a longtime listener and fan of the show CISO Tradecraft. If you haven’t checked it out and don’t subscribe, you should!
That is why I was excited to join the team and G Mark Hardy for an episode myself. We dove into:
The state of vulnerability management, including challenges around vulnerability scoring, prioritization and databases
Software supply chain risks across both open source and commercial products
The compliance landscape both in the U.S., EU and abroad, and how despite us bemoaning compliance, it often does more to move security than anything else in the ecosystem
Nuances around DevSecOps, security tooling and automation.
I really enjoyed this wide ranging discussion and hope you do too!
Runtime Cloud Security in 2025
Cloud Application Detection & Response (CDR) continues to become a growing market category when it comes to the cloud security space. I’ve previously written articles on this topic, such as:
How ADR Addresses Gaps in the Detection & Response Landscape
Prevention is Ideal but Detection and Response is a Must: Introducing Wiz Defend
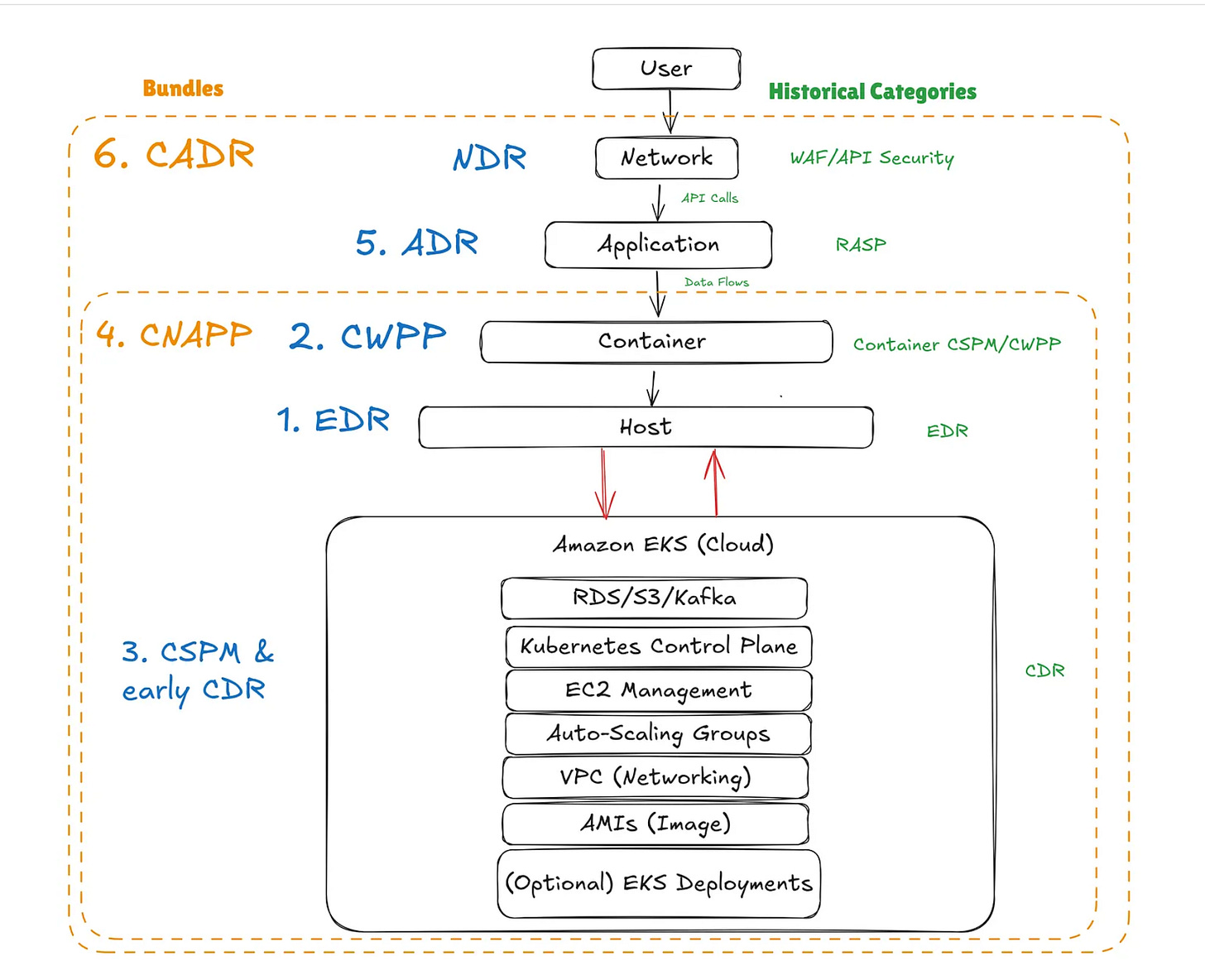
However, this latest piece from James Berthoty of Latio Tech dives deep into the CDR topic, discussing how it addresses the gaps of the current Cloud Native Application Protection Platforms (CNAPP), specifically around applications.
In typical James fashion, he put together some great visualizations to go along with the article.
For example, below he demonstrates the evolution of these platforms, and how Cloud Application Detection and Response (CADR) addresses areas typically not deeply addressed by CNAPP’s, most notable the application layer.
The biggest distinction among CADR tools is that they are purpose-built to address runtime threats to cloud applications. I dove into this in my own interview with Miggo’s founder Daniel Shechter.
To make his point, James lays out the MoveIT incident, demonstrating how traditional tools wouldn’t have caught it, but ADR tooling, specifically with eBPF could do so given they could catch both a SQL injection and process creation via a payload.
James uses several other example incidents showing a common pattern of:
Initial compromise at the App layer
Pivoting to the workload layer
Spreading across the Cloud layer
He states no legacy existing solutions that are siloed can catch this sort of activity and is precisely why we need CADR. In his “Runtime Security Map” you can see some of the vendors orienting around this CADR solution, with some heavily on the cloud focus, others more on the container side, and lastly, some most focused on apps.
He closes out with some discussions of what vendors to watch and the fact that CSPM and CNAPP vendors simply don’t have the context and visibility into the application and network/process layers to provide the needed data. This is why we are seeing the rise of CADR vendors.
Resilient Cyber w/ Jit - Agentic AI for AppSec is Here
In this episode, we sat down with David Melamed and Shai Horovitz of the Jit team. We discussed Agentic AI for AppSec and how security teams use it to get real work done.
We covered a lot of key topics, including:
What some of the systemic problems facing AppSec are, even before the widespread adoption of AI, such as vulnerability prioritization, security technical debt, and being outnumbered exponentially by Developers.
The surge of interest and investment in AI and agentic workflows for AppSec and why AppSec is an appealing space for this sort of investment and excitement.
How the prior wave of AppSec tooling was focused on finding problems, riding the wave of shift left but how this has led to alert fatigue and overload, and how the next era of AppSec tools will need to focus on not just finding but actually fixing problems.
Some of the unique capabilities and features the Jit team has been working on, such as purpose-built agents in areas such as SecOps, AppSec, and Compliance, as well as context graphs with organizational insights to drive effective remediation.
The role of Agentic AI and how it will help tackle some systemic challenges in the AppSec industry.
Addressing concerns around privacy and security when using AI by leveraging offerings from CSPs and integrating guardrails and controls to mitigate risks.
If you prefer, you can listen below on other platforms:
Please be sure to subscribe as well!
Oracle Confirms Cloud Hack
The majority of cloud security incidents are tied to customers and activities such as misconfigurations. We don't often hear about breaches of hyper-scale CSPs.
But, when we do, they can be very bad.
That seems to be the case here, with Oracle now confirming their cloud had an incident, with the hacking claiming to have impacted over 140,000 customer tenants and looking to sell data, including credentials.
Oracle originally denied the incident and said there was no breach of Oracle Cloud. However, they now seem to be publicly confirming that their environment and systems were indeed impacted, raising many concerns and questions from customers running workloads on Oracle Cloud.