Resilient Cyber Newsletter #41
Frothy Startups & Liquidity Shifts, FedRAMP Scraps ConMon, MCP Wins the Agent Tooling Wars, Critical AI Security Guidelines & Ingress NGINX Nightmare
Welcome!
Welcome to issue #41 of the Resilient Cyber Newsletter.
The year continues to heat up, with major updates from the venture and startup community and the rapid adoption of a protocol in MCP to facilitate the Agentic AI wave and a major vulnerability in a widely used aspect of Kubernetes.
So, let’s dive in and unpack it all!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 45,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cyber Leadership & Market Dynamics
Software-Defined Warfare: A Blueprint for Sustaining a Competitive Military Edge 🪖 💻
Software powers everything from consumer goods to critical infrastructure, even modern warfare.
That's why this "Commission on Software-Defined Warfare" final report from the Atlantic Council is timely. It aims to provide a practical roadmap for the DoD's transformation from a hardware-centric organization to a software-centric organization in the digital age.
Key recommendations include
Mandating enterprise data and investing in AI enablers
Ensuring software interoperability and integration
Enforcing a commercial as the default software approach
Measuring what matters for DoD software and establishing a DoD software
The Atlantic Council also hosted a panel with some of the authors and leaders of the Software-Defined Warfare effort, which can be caught below:
If You Work In Cybersecurity and Live in Maryland, You Should be Concerned
Legendary Cyber leader and investor Ronald Gula shared an article bringing to light a recent change in the state of Maryland, which passed a 3% tax on data and IT services.
As Ron points out, this increases the cost of cybersecurity for everyone in the state of Maryland, including Cyber companies based there and is leading to some industry leading companies such as Tenable and Huntress considering leaving the State of MD.
This is a really interesting political move by the state of MD, especially given their rich ecosystem of cybersecurity companies and proximity to key organizations such as the DoD’s DISA, the NSA and more.
Ron raises key concerns such as the fact that Cyber companies don’t just employe cyber expertise, but also various other folks from programming, HR, marketing and more. Additionally, it is very easy and tempting to leave MD, with VA just next door, which lacks a similar tax, and lastly the fact that the state of MD’s startup ecosystem is shrinking, at a time when states should be looking to foster startup and business growth, not drive them out.
This seems to be following a similar pattern of other states like NY and CA, which have done quite a bit of damage to their own economies with higher taxes and cost of living increases, seeing a decrease in populations for more business friendly and lower cost of living states.
CrowdStrike CEO George Kurtz on SIEM “Inflection Point”, Wilz-Google Deal
It is always interesting to see what industry-leading CEOs have to say about the latest trends. This interview with CrowdStrike’s CEO does just that. The interview discusses how CrowdStrike is making a push via its channel partners with its Falcon “Next-Gen” SIEM offering. This includes touting how the product is AI-led and focuses on automation and the need for organizations to shift from legacy manual SIEM processes and tooling.
Are US Startup Valuations Too “Frothy” Right Now?
Peter Walker, who I often share content from, is the Head of Insights at Carta. He recently shared some details on the current state of U.S. software companies using Carta. This involved 10,000 rounds since Q4 2021.
The data showed that:
Media seed-stage startup valuations are 32% higher than in the peak of Q4 2021, which is pretty surprising
Fewer rounds are happening, so competition is higher
Seed is an outlier, as valuations are below the 2021 peak
AI again proves to be a bit of a unicorn, with higher valuations and larger round sizes
The Great Liquidity Shift
There’s been a lot of talk about M&A in the wake of Wiz’s acquisition by Google and about IPOs, with the U.S. presidential administration change. But, what does the data say?
This piece from Teomasz Tunguz shows 71% of exit dollars in 2024 came via secondaries, rather than IPO’s and M&A.
This demonstrates venture capital (VC) is starting to follow a similar path as private equity (PE), with the rise in secondary transactions as a key pathway to liquidity for existing shareholders.
Wiz’s $32B GTM Playbook: Unpacking the Formula
Analysis of Wiz’s performance from founding through acquisition to Google for a whopping $32B continues. This latest one comes from my friend Darwin Salazar over at The Cybersecurity Pulse (TCP).
He covers both finding Product Market Fit (PMF) and the importance of branding, unpacking how Wiz did both with excellence. Darwin starts by discussing how Wiz set a record pace for reaching $100M in annual recurring revenue (ARR) just 18 months after launching and never looked back.
Key factors Darwin covers that played a role in their success included:
A strong founding team
A capable and sticky product
Solving deep pain points
Timing
Key investors and network effects
Huge early funding (fuel)
As the article points out, Wiz wasn’t the first to market in their category, and in fact, executed in a highly saturated and competitive market space due to factors mentioned above, as well as ease of deployment, quick time to value and a hyper-focus on UX and an enjoyable customer experience.
Darwin provides insights directly from Wiz’s CMo, Raaz Herzberg, with whom I had the honor of doing a panel at RSA in 2024 at Wiz’s RSA adjacent security event.
Wiz was able to create a quickly iconic brand that customers loved, competitors dreaded facing and that brought a lighthearted nature to an otherwise doom and gloom space sometimes in Cybersecurity.
This piece from Darwin covers it all, and if you’re an early stage founder, or focusing on product and branding, I definitely recommend giving it a read.
Signal For Secure Comms: Convenience Over Security Without the Record-Keeping
In the recent fall out of the SecDef and others using Signal for highly sensitive communications, and looping in a civilian reporter, articles have been running about Signal and secure communications. This article dives deep into the topic of secure communications and why Signal is attractive, albeit a problematic option as well.
FedRAMP Scraps Continuous Monitoring (ConMon)
The U.S. Governments cloud authorization program continues to roll out updates to the community, on the heals of announcing their “FedRAMP 20x” effort, where details are still scarce but is predicated on just accepting evidence and assertions from CSP’s and 3PAO’s to clear the backlog of cloud service offerings awaiting authorizations.
The FedRAMP team shared an additional update this week, which was that they are “shifting their posture and only focusing on providing those services that meet their statutory obligations”. This means the additional ConMon services FedRAMP provided to agencies will come to a halt due to a lack of resources and manpower and it will be left to the agencies to do their own ConMon of CSP’s and SaaS services they are consuming and no longer be able to rely on FedRAMP.
This is concerning given many agencies also face the same manpower and resource constraints, so not only will we have CSP’s quickly ushered through authorization but fewer, if any of them will be deeply monitored for ongoing risks such as vulnerabilities, supply chain concerns and more.
AI
AI Model Context Protocol (MCP) & Security
By now, the industry is clearly shifting towards Agentic AI and agent-based workflows. The use cases are incredibly expansive, and the potential is promising. But what are the implications for security?
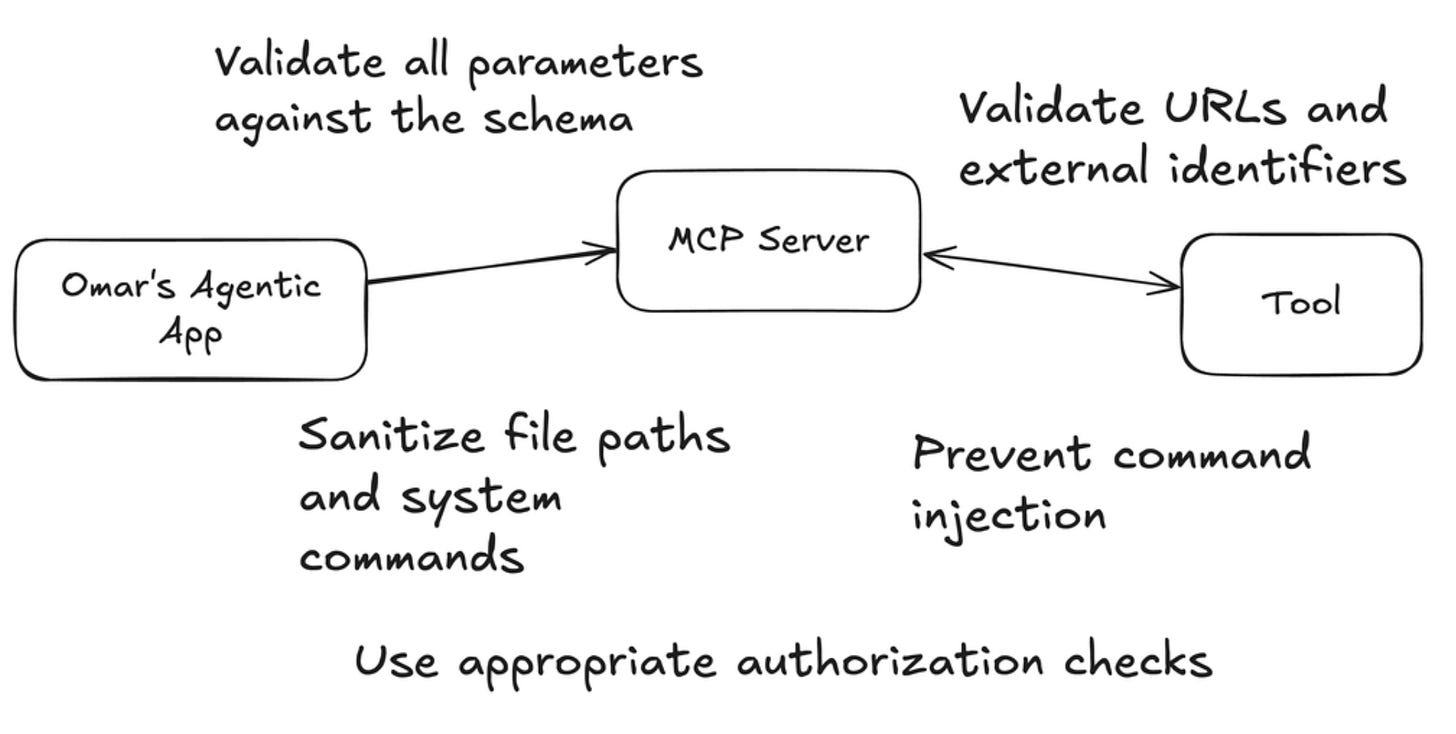
This excellent article from Omar Santos looks at the AI Model Context Protocol (MCP) and key security considerations, such as:
- Overview of MCP and its Security Architecture
- Security Considerations when using MCP
- Secure and Authenticated Model Interactions
- Security Considerations when Exposing Tools
- Additional Security Considerations and Best Practices
As agentic workflows and agents become pervasive across the enterprise, security must focus on these factors to ensure we realize the promise of Agentic AI without introducing additional risks.
The article has some great diagrams to begin thinking about MCP overall, as well as from a security perspective.
MCP Overview:
Secure and Authenticated Model Interaction:
Security Considerations when Exposing Tools:
MCP is the New Interface For Security Tools
On the heels of the previous article, Maya Kaczorowski wrote a great succinct article discussing why MCP is the new interface for security tools. Maya discusses the rapid rise of MCP and how it implements tool calling with a common format and spec, to connect agents to tools.
She even jokes that rather than build their own protocol, OpenAI has now adopted MCP.
Maya lays out three key reasons for the security benefits from MCP, and I agree with her, especially as we prepare to see agentic architectures become pervasive.
Security is fragmented
Not all security professionals code
Security drowns in data
All of Maya’s points are valid, and they will help security manage the expansive amount of data and required telemetry from agentic architectures and achieve the required visibility and governance security.
One interesting insight Maya draws is that the job isn’t UI anymore for those building security tools but data and interfaces to help make sense of our fragmented security tooling landscape. That said, Maya raises the critical point I hope the industry doesn’t miss, which is that securing MCP services and agentic identities will now be critical, such as implementing secure authentication for audit logs, approval flows, least-permissive access control, mitigating credential compromise of these sprawling non-human identities.
Why MCP Won the Agent Tooling Wars (and How it Won)
Rounding out my MCP resources for the week, the “AI Daily Brief: AI News” is a show I follow via podcast and produces excellent daily bite sized updates around AI. Over the weekend they published an episode focusing on how MCP won the agent tooling wars, and how. It is a great concise discussion of how MCP has emerged and quickly been adopted, you can listen to it below:
Critical AI Security Guidelines v1.1
As organizations rapidly adopt AI, from self-hosted open source models, external model service providers, and AI being integrated into countless modern products, we need a way to understand critical AI security controls.
SANS Institute has provided a great, concise resource focused on just that. It covers:
🔐 Access Controls
🗞️ Data Protection
🚧 Deployment Strategies
🧠 Inference Security
🔎 Monitoring
✅ Governance, Risk and Compliance (GRC)
This is a timely and actionable resource with key considerations for security leaders and teams regarding securing your organization's adoption of AI.
A Framework for Evaluating Emerging Cyberattack Capabilities of AI
We continue to see the exploring of both using AI for security and securing AI. This includes looking to understand the cyberattack capabilities of AI. Google’s DeepMind recently released a framework to evaluate the cyberattack capabilities of AI.
Their approach involves
Examing the end-to-end attack chain
Helping to identify gaps in the valuation of AI threats
Helping defenders prioritize targeted mitigations and conduct AI-enabled adversary emulation to support red teaming
Their efforts involved over 12,000 instances of real-world attempts to use AI in cyberattacks, which were cataloged by Google’s Threat Intelligence Group. This highlights not only the scope and diversity of the research but also just how quickly attackers are exploring the use of AI in their malicious activities.
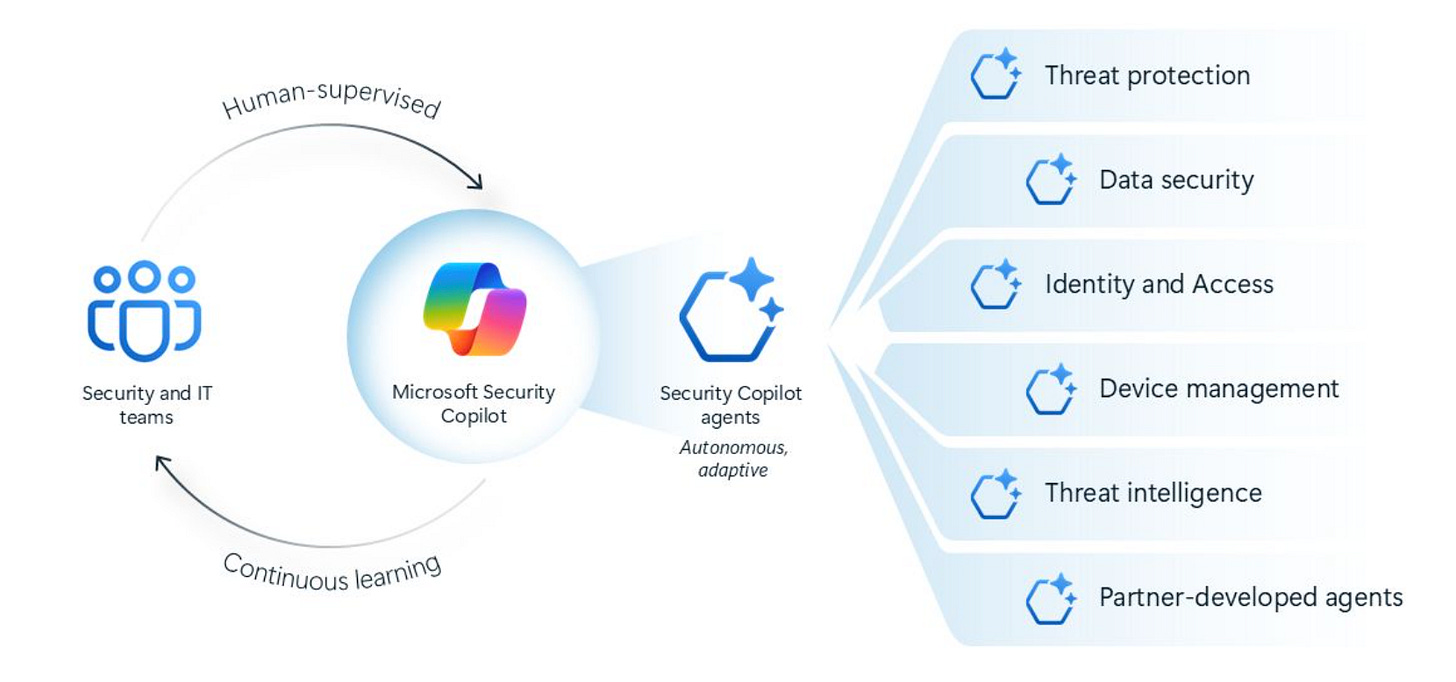
Security Copilot Agents
You’re catching onto the agentic theme, including for Security. Microsoft recently announced its agentic capability, and Semah Younis took to LinkedIn to share the below image, showing many of the potential use cases that both Microsoft and the broader industry are looking to agents for.
“Secure” Vibe Coding Guide
It is clear that “vibe coding” is now a thing. It boils down to leveraging the native capabilities of LLMs for development, not getting bogged down in the details or nuances, and just running with what is produced.
That raises some glaring security concerns for many in the community. Ken Huang, who I consider one of the leading voices around AI security, published a comprehensive blog titled the “Secure Vibe Coding Guide.”
He lays out:
Key features of “vibe coding”
Why security is crucial in vibe coding
The Secure Vibe Coding Checklist
Secure Vibe Coding Prompts
Key books on the topic of Agentic AI and AI more broadly
Ken’s book is set to come out this summer and I had a chance to co-author a few chapters!
Rethinking Security in the Age of AI
There’s no doubt that security needs to change to adapt to novel threats in the age of of widespread AI adoption. This includes both securing AI, and leveraging AI for security. This piece from recently launched AI startup “Straiker” lays out re-thinking security in the age of AI and addresses the key pillars of AI security, such as:
Web
Memory Poisoning
Agent Orchestration
Identity
Data
Models
Resilient Cyber w/ Piyush Sharrma - AI-Powered Defense & Security Mesh
In this episode, we sit down with Piyush Sharrma, CEO and co-founder of the Tuskira team. They're an AI-powered defense optimization platform innovating around leveraging an Agentic Security Mesh.
We will dive into topics such as Platform vs. Point Solutions, Security Tool Sprawl, Alert Fatigue, and how AI can create "intelligent" layers to unify and enhance security tooling ROI.
We discussed:
What drove Piyush to jump back into the startup space after successfully exiting from a previous startup he helped found
The industry debate around Platform vs. Point Solutions or Best-of-Breed and the perspectives between industry industry leaders and innovative startups
Dealing with the challenge of alert fatigue security and development teams and the role of AI in reducing cognitive overload and providing insight into organizational risks across tools, tech stacks, and architectures
The role of AI in providing intelligence layers or an Agentic Security Mesh across existing security tools and defenses and mitigating organizational risks beyond isolated vulnerability scans by looking at compensating controls, configurations, and more.
Shifting security from a reactionary model around incident response and exploitation to a preemptive risk defense model that minimizes attack surface and optimizes existing security investments and architectures
Resilient Cyber w/ Elad Schulman - Secure Enterprise LLM/GenAI Adoption
We sit with Lasso Security CEO and Co-Founder Elad Schulman in this episode.
Lasso focuses on secure enterprise LLM/GenAI adoption, from LLM Applications, GenAI Chatbots, Code Protection, Model Red Teaming, and more. Check them out at https://lasso.security
We dove into a lot of great topics, such as:
Dealing with challenges around visibility and governance of AI, much like previous technological waves such as mobile, Cloud, and SaaS
Unique security considerations for different paths of using and building with AI, such as self-hosted models and consuming models as-a-service from SaaS LLM providers
Potential vulnerabilities and threats associated with AI-driven development products such as Copilots and Coding assistants
Software Supply Chain Security (SSCS) risks such as package hallucinations, and both safeguarding the data that goes out to external coding tools, as well as secure consumption of the data coming into the organization
Securing AI itself and dealing with risks and threats such as model poisoning and implementing model red teaming
Lasso discovered several critical concerns in their AI security research, such as Microsoft’s Copilot exposing thousands of private GitHub repos
AppSec, Vulnerability Management and Supply Chain Security (SSCS)
IngressNightmare: CVE-2025-1974 - Unauthenticated RCE Vuln in Ingress NGINX
News recently broke of a critical vulnerability in Ingress NGINX, which doesn’t require authentication, and Wiz says over 40% of cloud environments are vulnerable, potentially leading to complete cluster takeovers.
The vulnerability can allow unauthorized access to all secrets stored across all namespaces in Kubernetes clusters, and lead to cluster takeovers. This is tied to the admission controller aspect of Ingressx NGINX on Kubernetes. Wiz was able to identify 6,500 publicly exposed clusters, including those from Fortune 500 companies that have the vulnerability.
This is particularly concerning since the Ingress NGFINX controller is one of the most popular ways to publicly expose Kubernetes applications to external connections and organizations.
The always reliable James Berthoty at Latio Tech does a great breakdown of how the vulnerability works and what can be done if exploited.
CVE2EPSS
We continue to see vendors and organizations use the Exploit Prediction Scoring System (EPSS) to focus on exploitation probability as a key metric for vulnerability prioritization. This neat tool, dubbed “CVE2EPSS,” lets you look up specific CVEs and see their EPSS score.




















Another week. Another amazing newsletter issue! 🔥