Resilient Cyber Newsletter #30
Corporate Cyber Governance, Compliance as Security, 5 Cyber Laws to Know, Agentic AI and AppSec, & the 2025 Vulnerability Forecast
Welcome!
Welcome to another issue of the Resilient Cyber Newsletter.
This week, we have a range of resources and topics to cover, including boardroom cyber governance, compliance as a forcing function for security, key cyber laws to know in the coming year, and the 2025 vulnerability forecast. So let’s get to it!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 8,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
You need to offload as much of your email security workflow as possible to automation and AI–but you don’t want to hand over total control of your program to a black box. You need to strike the right balance to free your team up for mission-critical tasks while still maintaining visibility across your entire environment.
Material streamlines SecOps by automating detections and remediations across your productivity suite with controls that are as hands-off or hands-on as you want. Material stops sophisticated attacks, secures sensitive data in files and mailboxes, detects and contains account takeovers, and reduces risk across your environment.
Discover why companies like Lyft, Databricks and Carta trust Material Security with protecting their cloud office environment.
Cyber Leadership & Market Dynamics
Corporate Cyber Governance: Owning Cyber Risk at the Board Level
Cybersecurity continues to a risk more boards are thinking and talking about. This is a good high-level piece from Jen Easterly discussing that transition from IT risk to board level concern.
She also covers some key behavioral changes boards can take to properly govern cybersecurity risks, such as:
Fully empowering CISOs with influence, resources and decision input.
Education and awareness for senior executives and CxO's so that cybersecurity isn't just something the CISO is concerned with
Robust cyber-risk management frameworks that are adopted organization-wide
Collaboration over self-preservation and actively working with the broader industry as well as Government agencies to mitigate systemic risks
Wiz Signals IPO Ambitions of new CFO
Wiz made a lot of headlines in 2024 for allegedly turning down an offer from Google worth tens of billions. The rumors were that Wiz instead had IPO ambitions of its own, which seem to be the case as signaled by comments from their leadership as well as their announcement of hiring Fazal Merchant as CFO. Fazal is the former Co-CEO of Tanium, and will be joining Wiz to lead their financial strategy and operational growth.
Compliance as Cybersecurity: A reality check on checkbox risk management
We often hear tired phrases like “compliance doesn’t equal security”, and while there is truth to it, the real truth is that in the absence of compliance, the security of the digital ecosystem would also be worse than it is now. I’ve been stating that compliance is the floor, not the ceiling, and without it, we would be in free fall, as compliance is the primary driver that gets businesses to take security seriously.
I joined ReversingLabs for a piece recently to discuss compliance vs. security, the intersection of the two and various industry trends making compliance even more of a focal point when it comes to cybersecurity. These include changes to the SEC rules around cybersecurity, the push for liability for CISO’s, efforts by the EU, CISA and others.
The State of the Cyber Nation 2024
I recently shared a very comprehensive and detailed report breaking down the Israeli Cyber exit and M&A landscape for 2024. Recently, another venture firm, this time YL Ventures published their “State of the Cyber Nation 2024” which is a similar report but from another perspective.
Similar to the previous report I shared, it details how much of a challenging year it was for Israel but despite those circumstances, how amazing the founders, investors, startups and innovators did in the face of the challenges.
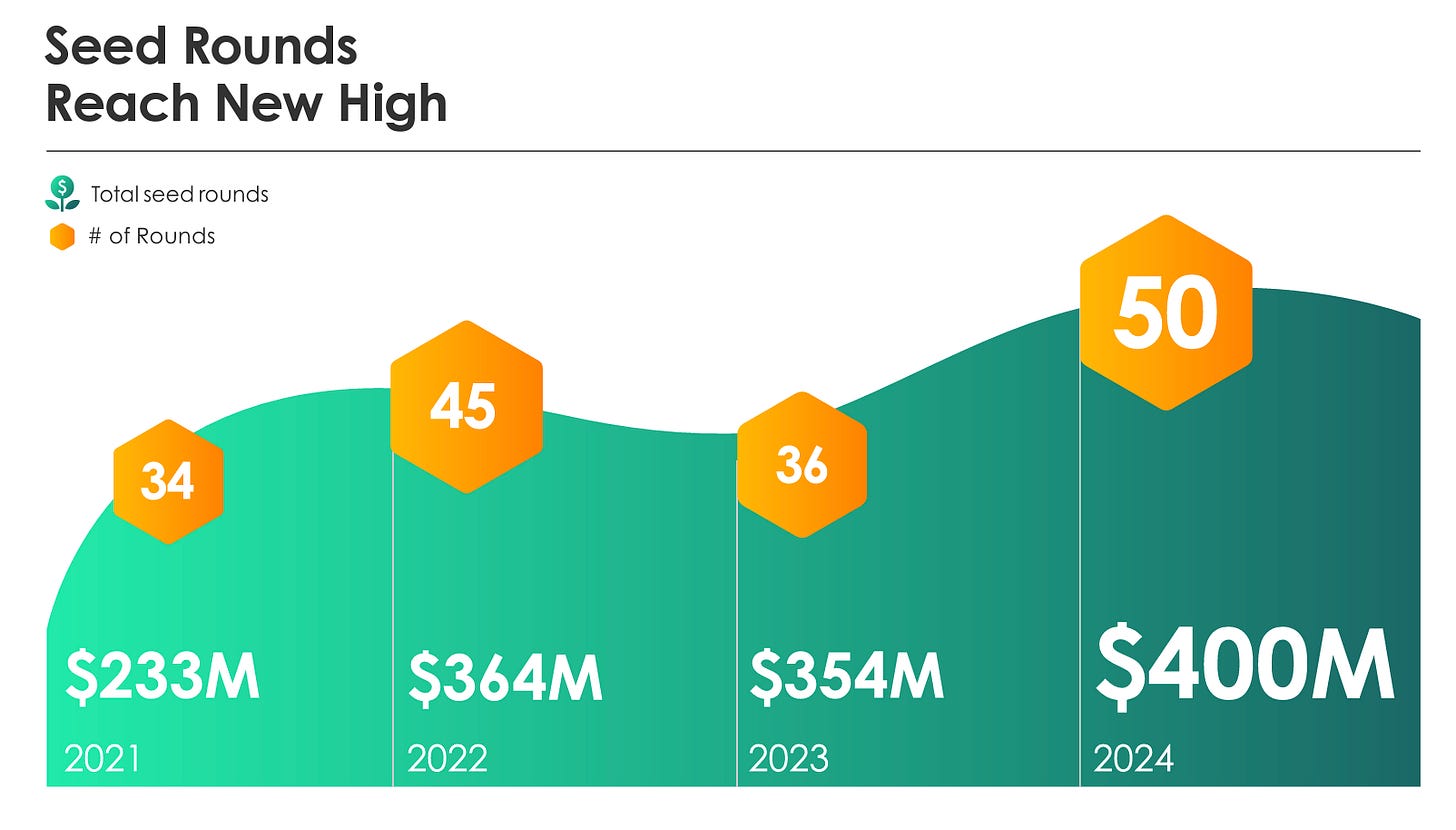
This includes some incredible growth in terms of funding changes YoY across number of rounds and overall funding, with a snapshot from 2022-2024.
As they discuss, the majority the funding came via overseas investors, demonstrating how much appeal and trust the Israeli cyber ecosystem draws from the broader global community. I have discussed this many times, but there is no denying what an outlier Israel is when it comes to their contributions around cybersecurity, from innovation, startups, founders and promising capabilities and products.
The report states there were 50 seed rounds in 2024, an increase of 14 over 2023 and the funding total was particularly high at $400M for seed funding rounds.
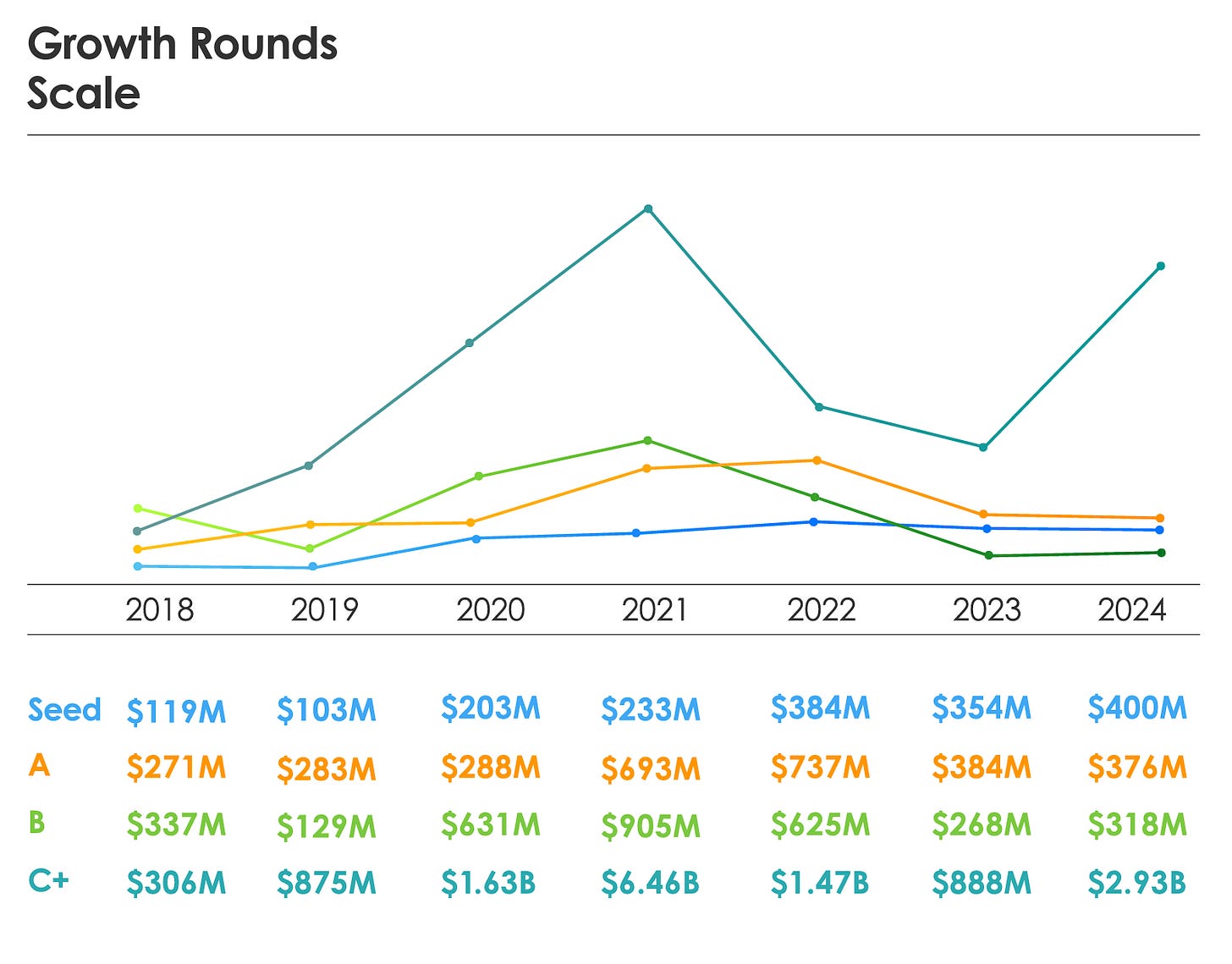
It wasn’t just seed rounds that saw an increase either, as the numbers were also up in Series C+ (but down in Series A and B). The biggest growth occurred in both Seed and Series C+, both of which more than doubled.
One interesting metric was that repeat founders also raised much larger seed rounds than first-time founders, undoubtedly a nod from investors in terms of their trust and ability to execute with a proven track record. 2024 saw an increase in seed rounds by repeat founders of roughly about 1/3 over 2023.
The below chart provides a good look at 2018-2024 in terms of growth round scale:
Series A and B both saw a decline in terms of the number of rounds in 2024 from 2023, emphasizing that those struggling to find product market fit, traction, adoption and early success may be struggling to raise subsequent rounds. This aligns with data from the other Israeli Cyber Venture/M&A report I shared, which also pointed out those who find early success and traction are more likely to succeed overall.
The report goes on to discuss some of the hot spaces both for new startups and overall.
This is underpinned by the emphasis that AI was leading the pack, both in terms of securing AI, as well as those looking to use AI to fundamental change and innovate how we do security, especially in SecOps most notably.
The YL Ventures report represents a great overview of the Israeli Cyber ecosystem in 2024, and I recommend checking out the full report for more details.
5 Big Cybersecurity Laws You Need to Know About Ahead of 2025
Speaking of compliance, there are several key cybersecurity laws and regulations coming into effect that organizaton’s should be aware of in 2025. This is a good article from Jordan Hicks of Schellman discussing some of them, including:
NIS 2 Directive
The EU’s Digital Operational Resilience Act (DORA)
EU Cyber Resilience Act (CRA)
The EU AI Act
Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA)
As you’ll notice, it is heavily EU-centric, which aligns with EU’s aspirations to be a “regulatory super power”, arguably in exchange for a shrinking economy, limited investment landscape and broader challenging landscape when contrasted with the U.S. startup, investor and innovation landscape as I have discussed previously.
Nonetheless, we live in a global economy, and businesses need to be aware of these laws, especially if they do business in the EU. We we will see businesses take specific precautions for their EU markets and customers, as well as some businesses outright now release specific products or versions of products and features in the EU, which many could argue comes as a loss to the EU consumer, but you get what you vote for, for better or worse.
CISA Publishes IT Sector-Specific Goals (SSGs)
Speaking of CISA, they recently published voluntary practices with high-impact security actions that outline measures the IT sector and its respective businesses and critical infrastructure owners are able to use to mitigate cyber threats.
There are a list of 11 Software Development (SD) Process Goals, that include activities such as separating environments used in the SDLC, enforcing MFA, securely storing and transmitting credentials and establishing a software supply chain risk management (SCRM) program among others.
It also includes 7 Product Design (PD) goals that include actions such as reducing default passwords, reducing entire classes of vulnerabilities and providing customers with security patching in a timely manner.
While these of course are great practices for secure software development and product design, much like the broader CISA Secure-by-Design initiative and pledge, these are voluntary - meaning organizations should do them, but don’t have to do them. That means it will remain to be seen how widespread their implementation is.
How CISOs can forge the best relationships for cybersecurity investment
I recently shared the IANS 2024 Security Budget Benchmark Summary report, which demonstrated that while security budgets are increasing 8% on average the past year, it is at a lower rate than previous years.
This piece from CSO Online provides some perspectives from CISOs and security leaders when it comes to building buy-in across the organization to help bolster their chances of obtaining their desired security budget. This involves stakeholders ranging from CxO peers to Developers and more across the business.
AI
Agentic AI and AppSec
We’ve heard a ton of excitement about AI Agents, Agentic AI, and its potential for Cybersecurity. This ranges in areas such as GRC, SecOps, and, of course, Application Security (AppSec).
That is why I was excited to sit down with Ghost Security Co-Founder/CEO Greg Martin. In this episode, we sit down with Ghost Security CEO and Co-Founder Greg Martin to chat about Agentic AI and AppSec. Agentic AI is one of the hottest trends going into 2025, and we will discuss what it is, the role it plays in AppSec, and what system industry challenges it may help tackle.
Greg and I chatted about a lot of great topics, including:
The hype around Agentic AI and what makes AppSec in particular such a promising area and use case for AI to tackle longstanding AppSec challenges such as vulnerabilities, insecure code, backlogs, and workforce constraints.
Greg’s experience as a multi-time founder, including going through acquisitions but what continues to draw him back to being a builder and operational founder.
The challenges of historical AppSec tooling and why the time for innovation, new ways of thinking and leveraging AI is due.
Whether we think AI will end up helping or hurting more in terms of defenders and attackers and their mutual use of this promising technology.
And much more, so be sure to tune in and check it out, as well as checking out his team at Ghost Security and what they’re up to!
The Battle or Brilliant Minds: From the Nuclear Age to AI
While much of the conversation AI focuses on tools, technologies and more technical topics, there also is a critical aspect that involves talent and the workforce. This piece from War on the Rocks discusses the need to preserve homegrown AI talent in the U.S. to remain competitive, most notably with peers such as China.
It points out that China produces roughly 50% of the worlds top AI researchers, whereas the U.S. only produces 18 percent. I’ll say anecdotaly when I look at AI publications that I often read and share, this seems about right in terms of where they are originating from and being published. They even point out that this isn’t confined to AI and that by next year, China will be generating twice as many Ph.D’s in STEM as the U.S.
The author also notes trends of graduates choosing to stay in China, rather than seeking opportunities overseas, such as in the U.S., which was the case in the past. China has also deliberately been looking to lure talent and scientists back home from abroad via bonuses and research grants, labs and other enticing offers.
The piece goes on to discuss how we need to invest and curate our own domestic AI talent as well as work to capture foreign AI talent through various enticing programs and incentives to draw them to the U.S.
Awesome List of Cybersecurity and AI
There is a lot of great AI resources floating around related to cybersecurity and it can be difficult to keep track of them all. This is a great GitHub repository titled “Awesome List of Cybersecurity and AI” that captures a lot of good resources, including a talk, and a look at the Hype Cycle around AI and Cyber.
AppSec, Vulnerability Management & Software Supply Chain
2025 Vulnerability Forecast
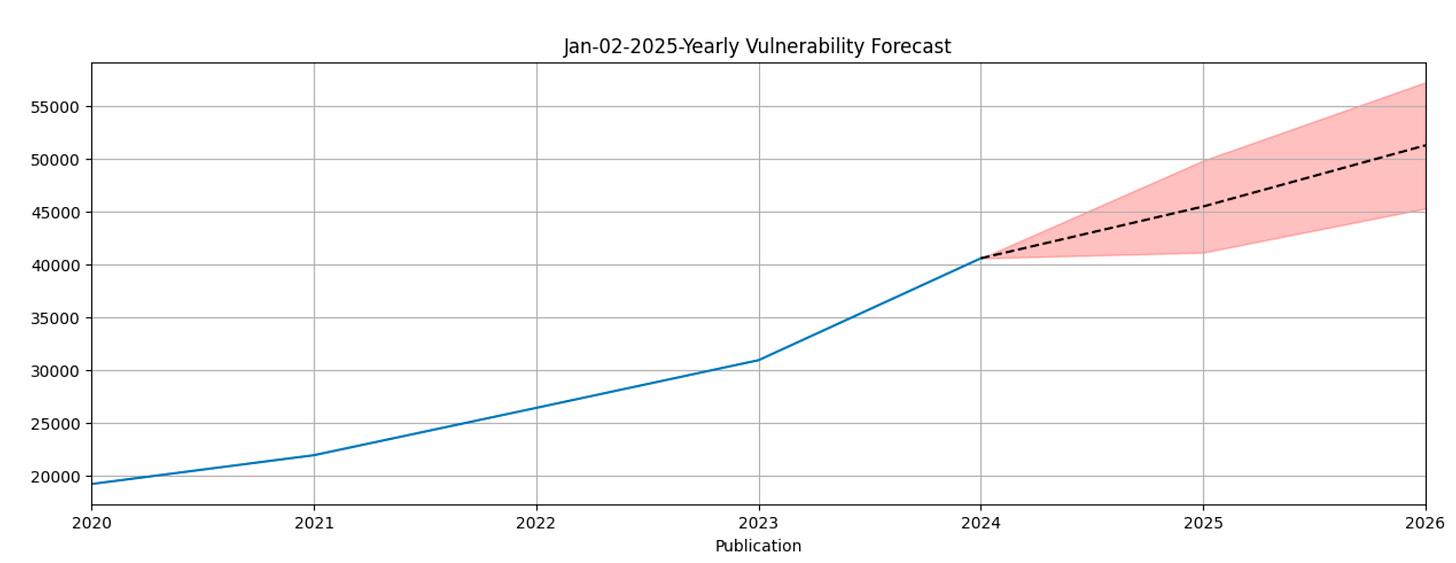
2024 was another record setting year for vulnerabilities, at least as Common Vulnerabilities and Enumerations (CVE)’s captured in the NIST National Vulnerability Database (NVD), which is the primary/leading vulnerability database in the industry.
The trend of double digit year-over-year (YoY) vulnerability growth shows little signs of slowing down, as FIRST published the Vulnerability Forecast for 2025. They anticipate 45,505 +/- 4,363 CVE’s in CY 2025.
The numbers are only projected to continue to climb, which is both good and bad. The CVE growth is being driven by factors such as more software, more digital products, improved vulnerability research and disclosure as well as recently the boon in GenAI code pilots and tooling to boost developer productivity, and soon, vulnerability discovery.
The glaring challenge is that CVE’s saw 30%+ YoY growth from 2023 > 2024, most vulnerability programs and teams did not see double digit growth in terms of efficiency and effectiveness. This is why vulnerability backlogs continue to balloon, teams continue to fall behind and modern security tooling that emphasizes known exploitation, exploitability, reachability and business context to bring signal to the noise continue to grow in the market in terms of adoption.
LLM Empowered Proactive Cloud Security Defense
There's no denying that cloud security can be complex.
This is especially true in multi-cloud environments with dynamic, ephemeral workloads, constantly changing environments, data flows, complicated IAM relationships, and more.
This paper looks at leveraging LLMs to empower a proactive rather than a reactive defensive model for cloud security. It aims to mitigate live threats by conducting comprehensive data analysis and dynamically creating and deploying defense mechanisms in cloud environments based on real-time data, reasoning, and responsiveness.
It's safe to bet that future cloud security will look very different. Vendors and CSPs will leverage GenAI and LLMs to implement a more proactive and resilient ecosystem.
Google Publishes “Future of the SOC: Transform the How”
This past week Anton Chuvakin and Google published the fifth paper in a series between Google Cloud Future and Deloitte, this one titled “Future of SOC: Transform the How”. This specific paper covers change decision trees through the lens of three common scenarios that drive transformation, including cloud migration, managed detection and response (MDR) adoption and DevOps evolutions.
Another Week, Another Security Vendor Being Exploited
I’ve been talking quite a bit about how security tools are part of your attack surface and are risks that CISO’s do own, unlike broader business risks that are often outside of the direct control of the CISO.
This week we saw the announcement of yet another new zero-day being exploited belonging to “secure” VPN vendor Ivanti. Ivanti also boasts an impressive 23 vulnerabilities actively listed on CISA’s Known Exploited Vulnerability (KEV) catalog. In my opinion, this does beg the question of when will security vendors be held accountable or to a higher standard, given their products are supposed to make organizations more, not less secure.
What’s Next for Open Source Software Security in 2025?
I had a chance to catch up with TechRepublic for an interview about what’s next for OSS security in 2025. We covered a lot of ground from the state of the ecosystem, attacks that made headlines in 2024 such as xz utils, the intersection of open source and AI and more.