Resilient Cyber Newsletter #29
How to Say “No” Well, CISO’s Working for Security Vendors, Four Smart Questions for Boards Overseeing Cyber and the AI Security Solution Cheat Sheet
Welcome!
Welcome to the first issue of the Resilient Cyber Newsletter for 2025!
We’re starting off the year hot with a lot of great topics and resources to dive into, ranging from security leadership, AI, AppSec and more, so I hope you enjoy it.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 8,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Security questionnaires are a massive burden. Almost every customer or prospect requires them, and they can be lengthy, repetitive, and require manual back and forth that distracts security teams from actually running their security program.
But, using automation, industry-leading companies complete security questionnaires up to 5x faster. No more clunky spreadsheets or long email chains. Automation is disrupting the status quo—with proven results.
In this report from Vanta, you’ll learn:
How automation is being used to answer security questionnaires
How much time real companies save by automating security questionnaires
How often teams do—and do not—have to step in to review auto-generated answers
→ Download it here! ←
Cyber Leadership & Market Dynamics
The Cyber Industry Loses a Titan
This week, we unfortunately share the news that the CEO of Tenable and longtime industry leader Amit Yoran passed away at 54 after a battle with cancer.
The stream of industry leaders, practitioners, and enthusiasts sharing their stories about Amit has been strong. That includes me, as I shared exchanges with him several times via LinkedIn and some of his articles, which were always thought-provoking and well-articulated.
Definitely an amazing human being lost way too soon.
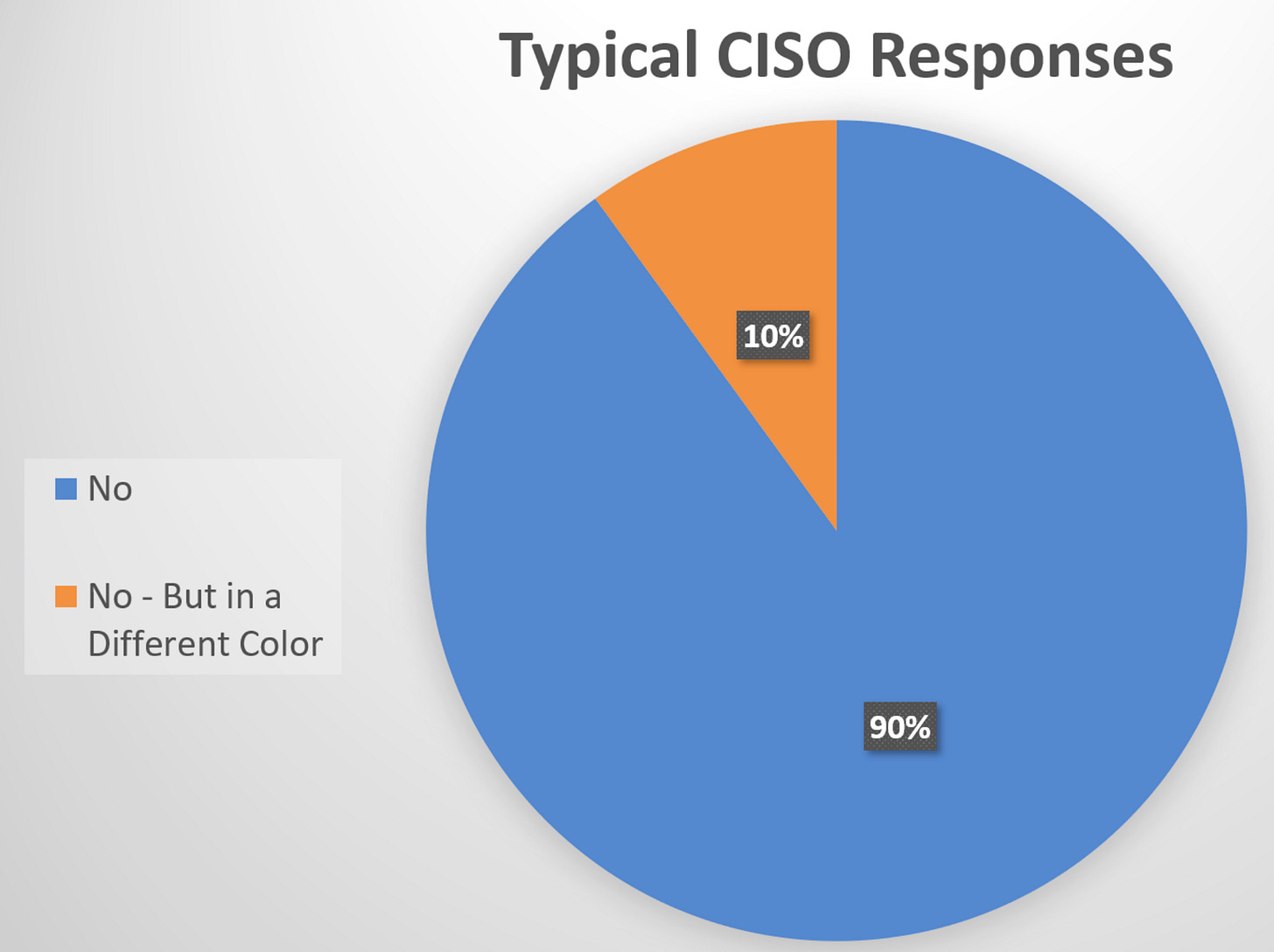
Your Security Tools May be Making You Insecure
That may be, and often is the case. In this article, I discuss the uncomfortable reality that security tools are part of the attack surface. We often hear discussions about how "the business owns the risk," but when it comes to the risks associated with our security stack? That lies at the feet of CISOs and Security Leaders.
Several of the most routinely exploited vulnerabilities and impactful security incidents in recent years involved security products and vendors. This is unsurprising, given that security tools make compelling targets for attackers. This problem impacts both point solutions and platforms, but in different ways.
Despite security tool sprawl and double-digit YoY vulnerability growth, security teams don't scale linearly either, leaving security teams managing more and more. In my latest piece, I cover all of this, using thoughts from my friend Ross Young about cyber risk ownership, Tyler J. Farrar's discussion of the "CISO Paradox," and resources such as the IANS Security Budget Benchmark Report.
Security does own risk - the risk of the security tools we introduce.
How to Say “No” Well
One theme in the last several years of cybersecurity is describing cyber as the “office of no.” As a result, the industry has, to some extent, over-corrected for this stigma and has potentially swung too far in the other direction, of never saying no, at least that is the case Rami McCarthy makes in a recent post.
Rami discusses how the cyber speaking and thought leadership circuit has been littered with people reframing security as the “department of yes.” He admits that cyber has a history of saying no, often without sufficient context, collaboration, or strategic collaboration with the business.
That said, he points out that we should indeed say no in some cases when it is the right decision for the business. To do so, we must stop “prioritizing harmony over hard truths” or blindly accepting risks to avoid upsetting our business peers.
We do this by saying "not" but not without context, ambiguously, too often, or as a complete sentence—meaning it shouldn’t be a dead end but more of a no, not like that, but this, with the this being a more secure or resilient path.
This is a great piece that reframes how we think about saying no in cybersecurity. It offers the opportunity to say no but to do so in a way that is much more effective than many have likely historically done.
Secure-by-Design vs. Secure-by-Default
We heard much about both concepts in 2024, especially by advocates such as CISA.
But what exactly is the difference between the two, and is one more important than the other? In my latest article for CSO Online, I explore the nuances of each and discuss how they are different but equally important to creating a more secure and resilient digital ecosystem.
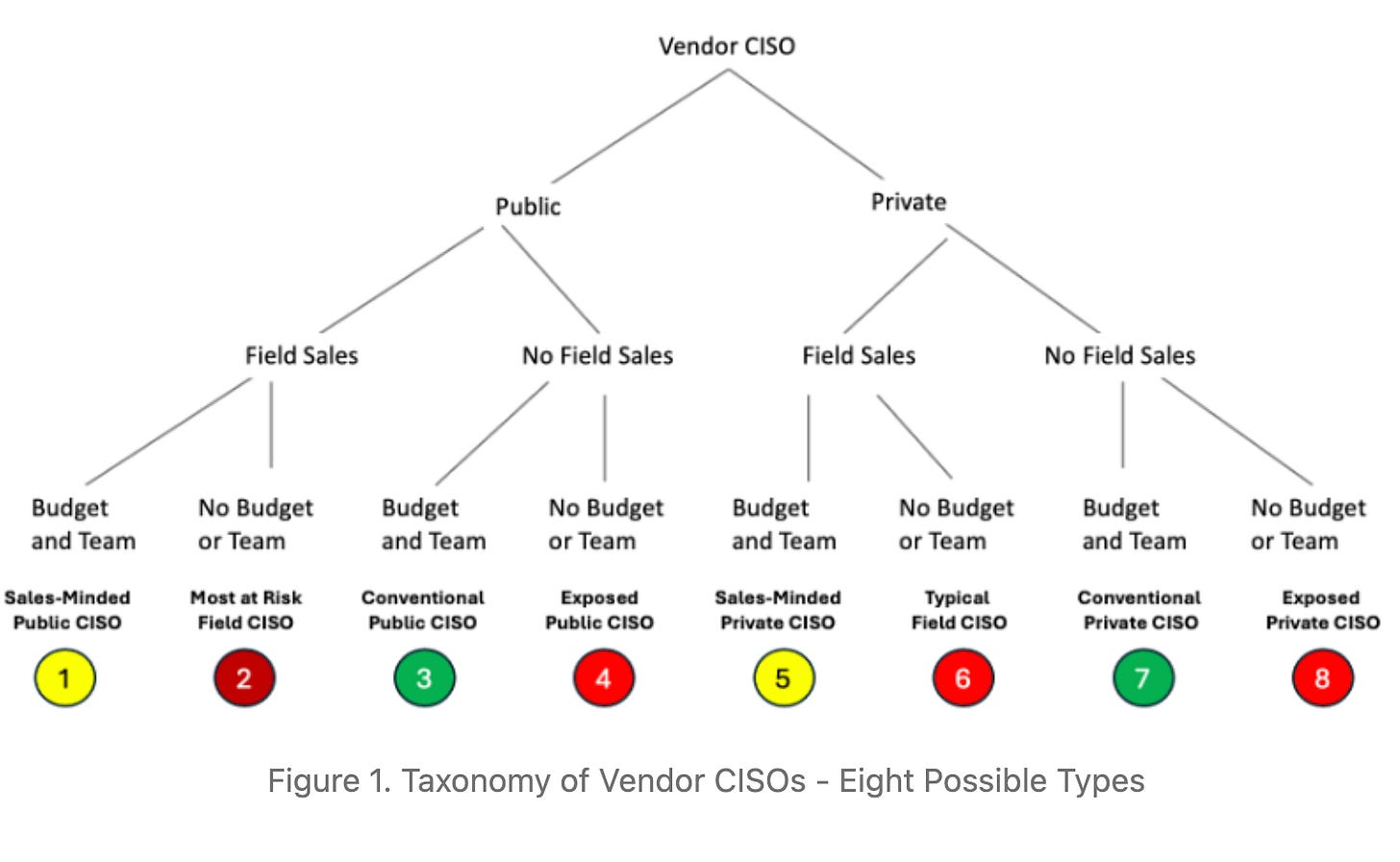
The Challenges of CISOs Working for Cybersecurity Vendors
The CISO is one of the most challenging roles in our industry. That said, not all CISO roles are created equal. There are CISOs, public or private organizations, field vs. operational CISOs, and more. What the CISO role looks like at your security vendor should also be a key focus for understanding how seriously your security vendor takes security.
This recent piece from industry leader Edward Amoroso is an excellent look at the various flavors of CISOs, their focus, and questions organizations should be asking, either directly or indirectly, when it comes to the CISO of their security vendor, and the answers have implications for the potential risks you may face in using a specific vendor.
It presents a taxonomy of vendor CISOs and eight potential types. It proposes questions for each type of CISO archetype and the potential implications for you as a consumer of their organization’s product. This aligns really well with my recent article about security tools making us insecure and is a useful mental model for practitioners considering potential CISO roles.
Four Smart Questions for Boards Overseeing Cybersecurity
We continue to hear about the need for board oversight and involvement in cybersecurity, and how cyber is increasingly becoming a board priority (or should!).
This piece from the WSJ discusses how security is becoming more of a board focus, and the number of directors with cyber experience is growing. It also discusses for questions many say directors should pose to CISO’s (and conversely could be used to hep CISOs prepare to brief the board:
Does leadership agree on the top cybersecurity risks?
What is the company culture related to cybersecurity?
What is the plan for communicating with regulators and shareholders about cyberattacks?
What would you do with more money?
Defense Tech Scaling New Heights with Incoming Administration
There continues to be high excitement around Defense Technology due to the upcoming administration change and other factors such as traction for defense tech firms, a growing relationship between Silicon Valley and the DoD, and more.
This recent piece from Michael Brown, who is currently a partner at VC firm Shield Capital but has a deep DoD background, continues that trend of enthusiasm.
He cites recent stock market climbs, especially for tech stocks, as a broader signal of the future business climate. This is coupled with extended rate reductions and a lighter regulatory environment, which many suspect will also occur. Mike points out that venture investment in DoD has been more than $100 billion since 2021, which is 40% more than the previous seven years combined.
Mike also cites language from Trump’s recent campaigning and the incoming chair of the Senate Armed Services Committee, who has called for the U.S. to increase defense spending to 5% of GDP, as opposed to the current 3$ (which is the lowest relative level in 75 years).
As discussed in the article, military superiority is increasingly tied to commercial technology, including AI, Autonomy, Cyber, Space, and more, with the Ukranian conflict being the most recent example. The venture funding ecosystem is also 2-3x the size of the DoD R&D budget, leading to commercial technologies often far outpacing DoD innovation.
Mike discusses the tremendous upside for venture-backed companies in the DoD, which currently account for 1% of DoD procurement but are expected to grow. DOGE, of course, is the elephant in the room, but Mike points out that they are much more likely to target bloated personnel budgets, maintenance of legacy platforms and weapons systems, and other areas that are a far larger part of the DoD budget than procurement.
VC’s Predictions on Enterprise Tech in 2025
We’re not out of the “prediction” time of the year yet, so here is a good piece from TechCrunch discussing the thoughts and predictions for 20 different VCs. It’s always good to see where folks in venture capital place their bets and why.
Hot areas include AI, Agentic AI, the Public Sector, Infrastructure, and more. Insights are provided by folks from leading firms such as Team8, Boldstart, Insight Partners, and many others.
Cyber was cited many times, and folks expect significant market growth as we see potential changes in interest rates, the regulatory landscape, M&A scrutiny, and more.
AI
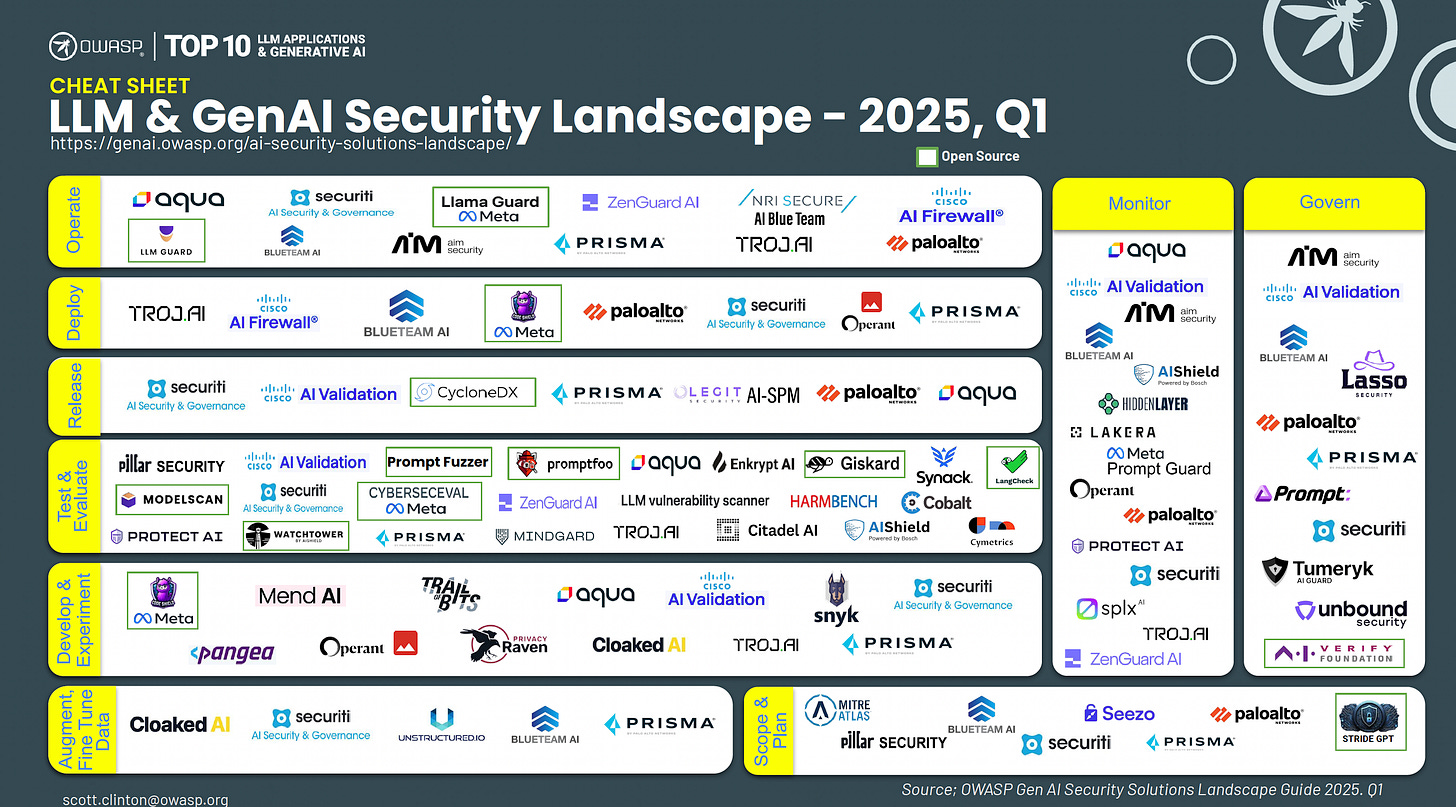
AI Security Solution Cheat Sheet Q1 - 2025
The GenAI and LLM Security ecosystem continues to evolve nearly as quickly as the adoption of the technology itself, as organizations race to keep up and secure their organization's adoption of GenAI and LLMs.
That is why it was great to see OWASP, the Top 10 LLM Applications, and the GenAI team release an “AI Security Solution Cheat Sheet Q1-2025.”
It lays out some of the leading vendors and their primary areas of focus, from Scoping/Planning, Monitor, Governance, Deployment, and Operations, among others. This serves as a quick mental and visual model of the GenAI and LLM Security space and is a bit of a pain point in emphasizing how confusing and complicated the landscape is. That said, big kudos to the OWASP team for trying to help the industry make sense of this quickly changing space and the key players.
Let’s hope it doesn’t become like the CNCF landscape, which requires zooming, scrolling, and other navigational techniques.
The landscape will undoubtedly evolve over the months and years, so it will be interesting to see how it changes and what names come and go. Currently, it represents a good mix of longstanding industry vendors and new names and faces who are helping tackle various aspects of LLM and GenAI Security.
I’ve been incredibly impressed with the volume and quality of work of the OWASP GenAI/LLM Security team, and I’ve decided to jump in and collaborate with my friends such as Steve Wilson and others in 2025, especially focusing on areas such as Agentic AI, so stay tuned for some resources in that area soon.
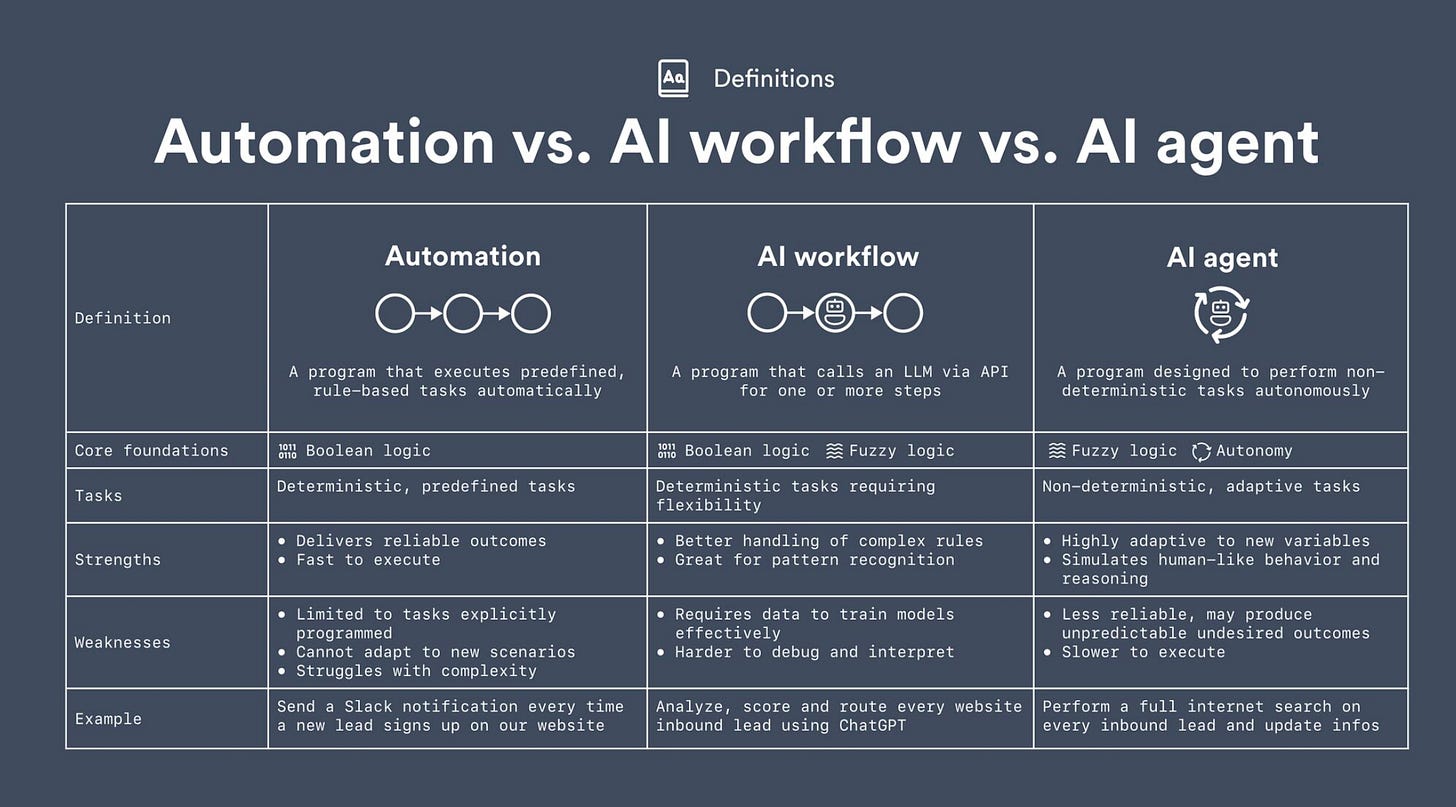
Automation vs. AI Workflow vs. AI Agent
One unfortunate downside of all of the excitement around Agentic AI right now is that there are many different words being used with different definitions depending on the audience. Among those are automation, AI workflows, and AI agents. In my opinion, this image/table does a great job discussing some key distinctions.
AppSec, Vulnerability Management & Software Supply Chain
Vulnerability Management & ASPM From Commercial to Federal
I’ll be joining my friend Francesco Cipollone of Phoenix Security to dive into a wide-ranging discussion, including:
Modern Vulnerability Management Approaches:
Explore the critical differences between traditional vulnerability management and application security in a cloud-first, hybrid world. Sully chain, reachability analysis and need to prioritize vulnerability that matters most.
ASPM and Vulnerability management in a changing environment
Learn how ASPM bridges the gap between development teams and security teams by consolidating vulnerabilities into actionable, prioritized workflows.
Supply Chain Security Threats:
Understand the challenges of modern supply chain attacks in the federal government and commercial sectors and how to defend against them.
Best Practices for Federal & Non-Federal Organizations:
Dive into frameworks, tools, and approaches to align with evolving regulatory environments like SBOM requirements while ensuring security goals are met.
PDLC and SDLC: Partners, Not Rivals
There continues to be a lot of interest in the intersection of Application Security (AppSec) and Product Security (ProdSec). Many even suspect that the former will eventually replace the latter, as more and more products are now digital, and the application/code is a subset of the broader product and its security.
This is a good article from Prime Security discussing the Product Development Lifecycle (PDLC) and Software Development Lifecycle (SDLC). It discusses how the PDLC and SDLC complement one another and are not competitors.
PyPI Project Quarantine
As malicious attacks on the software supply chain continue, major package repositories such as PyPI are prime targets and in a position to help drive down systemic risks to the entire ecosystem. This latest block from Mike Fielder, PyPI Admin, discussing their Project Quarantine is an excellent read on how they are doing that.
It discusses the persistent problems of malware on PyPI and how they are trying to tackle them and mitigate their impacts. While this sheds light on their internal process for addressing malware on PyPI, it also has some concerning insights, like the fact that their entire security team is one, yes, one.
“With the current full-time security staff for PyPI == 1, there is potential for malware to remain installable for users for longer periods of time, and asking volunteer PyPI Admins for extra hours of work is not sustainable”.
This again highlights just how fragile our open-source ecosystem is.
The Many Ways to Obtain Credentials in AWS
Credential compromise remains one of the most common ways security incidents and breaches occur via sources such as Verizon’s DBIR. This article is an awesome resource from cloud security Scott Piper from Wiz, discussing how credentials can be obtained in AWS (Hint: it’s a lot!).