Resilient Cyber Newsletter #23
Lawyers to Inherent Cyber, Navigating the Cyber Regulatory Landscape, The Future of CISA, Analyzing AI Security Investments, and CISA's 2023 Top Routinely Exploited Vulnerabilities
Welcome!
Welcome to another issue of the Resilient Cyber Newsletter.
I’m excited to bring some awesome resources to you this week around cyber leadership, market dynamics, AI and AppSec.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 7,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Simplify SecOps for Google Workspace with Material Security
Google Workspace is critical to your organizations’ day-to-day workflows. It’s where your employees work, communicate, and collaborate. It’s also a vulnerable attack surface, with inboxes and files full of sensitive data and links to other apps and services across your environment.
Material Security provides unified SecOps for all of Google Workspace, with advanced phishing protection, a unique approach to DLP, and proactive posture management. Our platform surfaces threats and risks that others miss, and automated remediations ensure problems are fixed–fast.
Cyber Leadership & Market Dynamics
Blessed Are the Lawyers, for They Shall Inherit Cybersecurity
Compliance Equals Security?
I've been writing recently about the fact that Compliance does equal security, such as my article “Compliance Does Equal Security - Just Not the Elimination of Risk”. But not for the reasons we may think. Compliance certainly doesn't equal the elimination of risk, nor was it ever intended too. However, it is certainly the most powerful forcing function to make cybersecurity a priority. Especially in the face of the fact that incidents have negligible impacts on share price, revenue etc. and markets generally don't care.
That's why I found this share from Ross Haleliuk in his recent article so fascinating. In the paper, the authors argue:
Cyber is still incredible immature and inefficient when it comes to actually quantifying impacts, investments, and ROI related to risks
We struggle to move towards tying specific technical measures to cybersecurity financial losses due to the complexity of modern environments and the continued changing nature of technology and software
The authors point out, much like Cybersecurity and Infrastructure Security Agency recently did, that we largely lack empirical data related to security investments (e.g. shift left, ROI of security expenditures and more related to efficacy of specific controls)
Lawyers will be the driving force in cyber, as concepts such as liability, regulation, and compliance dominate due to the market failure of cybersecurity
With this growing trend, we may see less, not more, information sharing and transparency, as the goal is minimizing exposure and liability at the end of the day
So to all the security practitioners bemoaning compliance, give it a second thought, because the reality is in the absence of compliance, your organizations would likely have decreased investment and take security less seriously than they already may.
Navigating the Cybersecurity Regulatory Landscape
Much like the threat landscape, the regulatory landscape in cybersecurity continues to grow increasingly complex. Last week I had a chance to sit down with return guest Jim Dempsey on my Resilient Cyber Show to dive into this exactly topic.
Jim is the Managing Director of the Cybersecurity Law Center at IAPP, Senior Policy Advisory at Stanford, and Lecturer at UC Berkeley. We will discuss the complex cyber regulatory landscape, where it stands now, and implications for the future based on the recent U.S. Presidential election outcome.
We dove into a lot of topics including:
The potential impact of the latest U.S. Presidential election, including the fact that while there are parallels between Trump’s first term and Joe Biden’s, there are also key differences. We’re likely to see a deregulatory approach related to commercial industry and consumer tech but much more alignment and firm stances related to cyber and national security.
The future of efforts around Software Liability and Safe Harbor
Contrasted differences between the EU’s tech regulatory efforts and the U.S. The U.S. has taken a much more voluntary approach. While Jim is an advocate of regulation and thinks it is needed, he simply cannot get behind the heavy-handed approach of the EU and suspects it will continue to widen the tech gap between the U.S. and the EU.
What is the potential for regulatory harmonization and the challenges due to the unique aspects of each industry, vertical, data types, and more.
Conference on Cyber Regulation and Harmonization
Speaking of cyber regulatory harmonization, Columbia University hosted a two day conference last week on the topic, features industry leaders from across the public and private sector, including the National Cyber Director.
The recording is below:
15 Tips on Presenting to a Board
CISO’s and Security leaders continue to find themselves in a position to need to effectively present to the board. Knowing how finite these chances and and how they need to be maximized for effectiveness, this is a great piece from the World Economic Forum (WEF) on 15 tips for presenting to a board.
Key recommendations include knowing what you’re walking into, doing your homework, sending documents ahead of time and knowing the boards preferences for information presentation among others.
These simple tips can help maximize the effectiveness of the limited windows security leaders get with their board of directors.
Major Federal IT Contracts Remove “Unnecessary” Degree Requirements
A constant debate in the world of IT and Cyber is that of degrees versus experience. This is often overlayed onto conversations about the workforce challenges and shortages of qualified candidates. The Federal government is making a push to allow for skill-based hiring that removes hard requirements for degrees across its government contracting workforce for some of its largest contract vehicles.
Questions about the Future of CISA
With the Presidential administration change, the Cybersecurity Infrastructure Security Agency (CISA) (where I recently wrapped up a tour as a Cyber Innovation Fellow) finds itself in the hot seat, with a lot of looming questions about its future. Headlines range from some wanting to shut the agency down entirely, while others want to severely alter its scope, size and funding.
The scrutiny largely is around CISA’s role with “misinformation” and the monitoring of online communications and interactions with tech companies and social media platforms as well as its focus on elections.
I personally am really saddened to see these headlines because outside of the above activities, CISA does an amazing amount of work on everything from cybersecurity advisories, vulnerability reports, and major initiatives such as its push for Secure-by-Design, which has really spurred a ton of great conversations around software supply chain security. CISA has also made a lot of progress around open source security and fostering a lot of great conversation and focus on this aspect of the digital supply chain.
I really hope CISA can be untangled from the politically charged topics and be able to continue some of the amazing work it does for both the Federal and Commercial cybersecurity community.
CISA Director Jen Easterly to Resign on Inauguration Day
Speaking of changes to CISA, news broke that its Director, Jen Easterly will be stepping down on inauguration day.
Jen has been an incredible advocate for a more secure and resilient digital ecosystem. She has been championing a message of Secure-by-Design/Default, the importance of cybersecurity in our modern society and the fact that we “don’t have a cybersecurity problem, we have a software quality problem”, pointing out the fact that technology vendors continue to offload the responsibility for securing systems and products onto downstream customers, consumers and society as a whole.
Her presence will definitely be missed, although I suspect she will hopefully still be around the ecosystem in a new capacity.
On that note, here is a recent keynote she delivered at Mandiant’s mWISE Conference which I thought was great.
Analyzing AI Investments
It is evident to most paying attention that AI and AI-adjacent companies are dominating the investment landscape. This has been discussed from various sources, such as Return on Security and others looking at current investment trends throughout 2024.
But what exactly do investors look for in AI-first security companies?
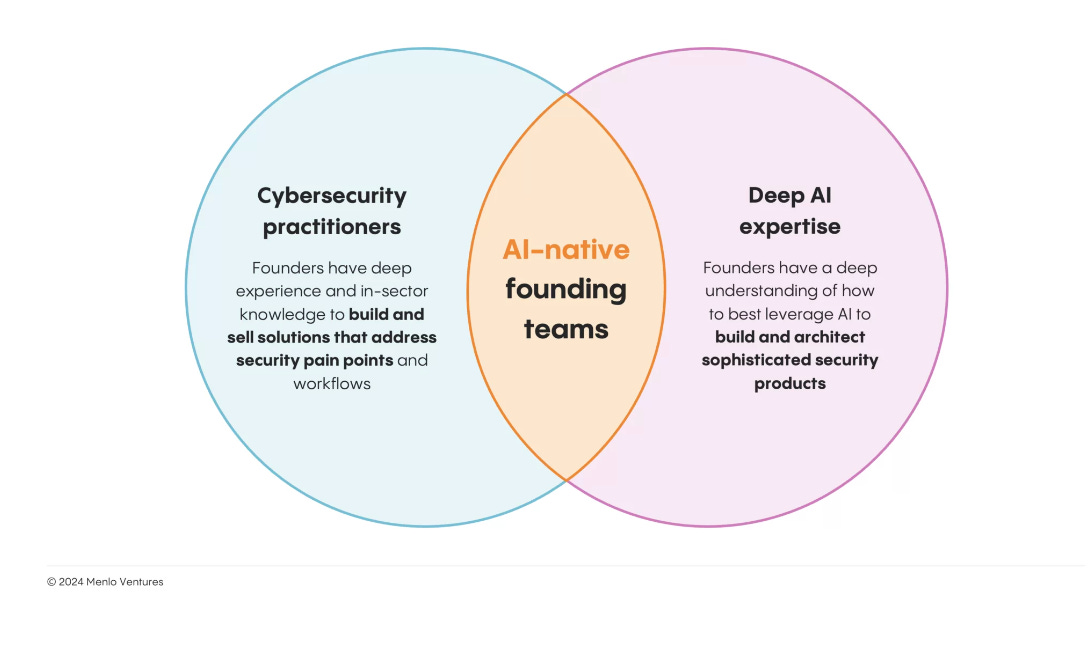
This piece from Menlo Ventures lays out just that.
Notable characteristics include:
Cloud-native and AI-native Architectures
Founding Teams with strong security and AI DNA
Teams leveraging AI agents to deliver on the Software-as-a-Service Promise
Innovative approaches to data and identity security
Products that are “dead simple”
The below checklist while not exhaustive, does provide some insight into trends and key criteria that venture firms with a focus on AI for security are looking into.
My Journey into AI Security: What Every Cybersecurity Professional Should Know
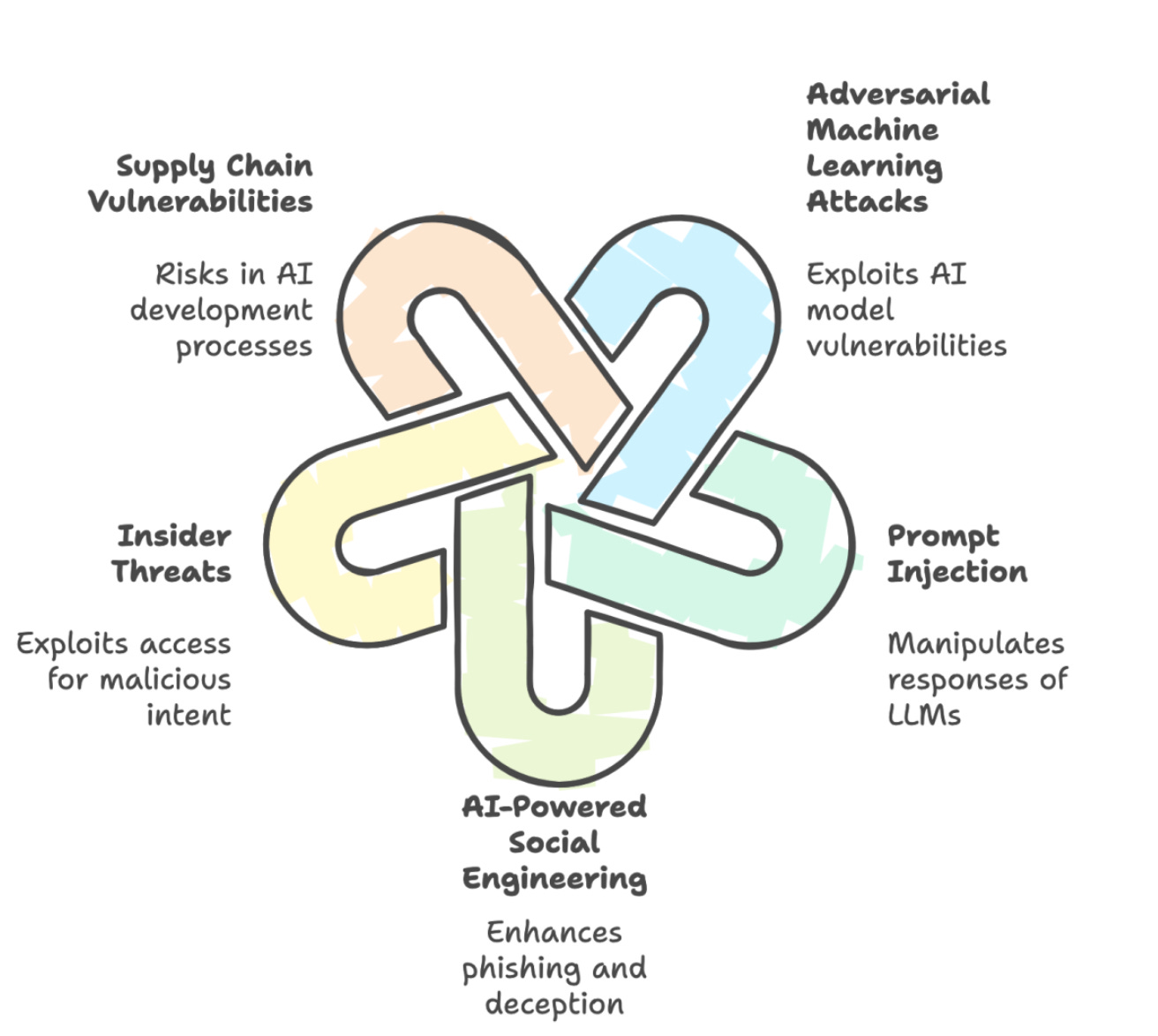
Many of us are rapidly trying to learn as much about AI and how to secure it as we can, looking to keep up with the rapid pace of business adoption. This is an excellent article from Stephen Alexander of AWS, who shared some of his early learnings, along with some great visualizations as well.
Alexander’s piece covers his wake up call about the importance of AI and its potential, as well as what some of the key threats we should be focused on are.
He also provides eight lessons from the field to help raise the bar on AI security, which I found solid:
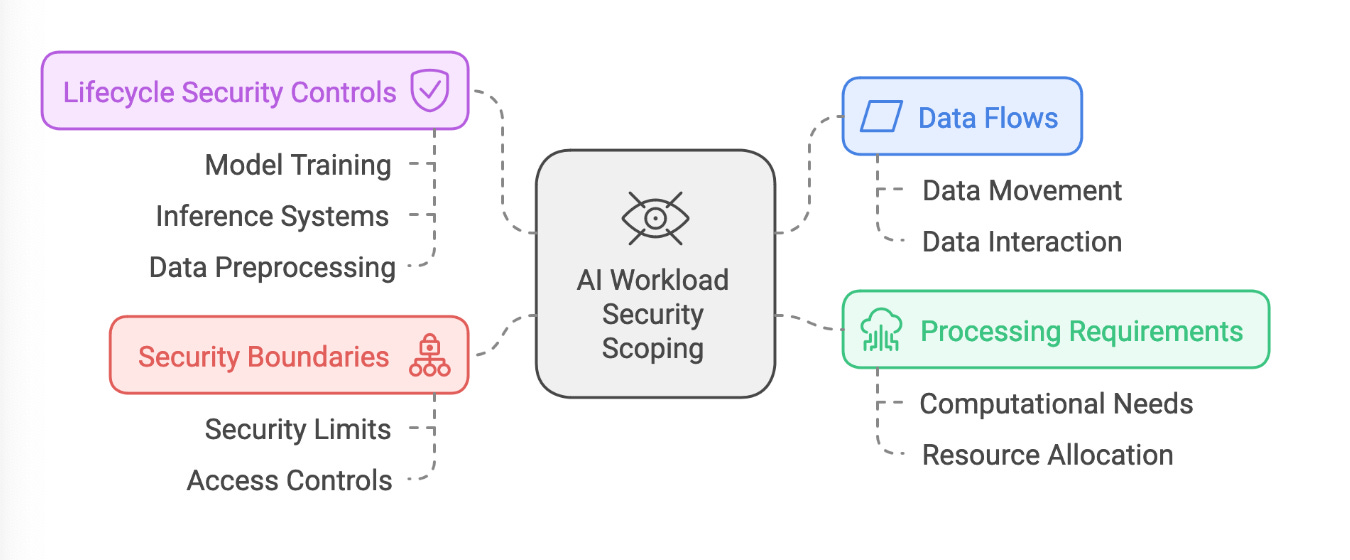
Strategic Workload Shaping is the first of the eight he discusses but I strongly checking out the article, as the entire discussion is great.
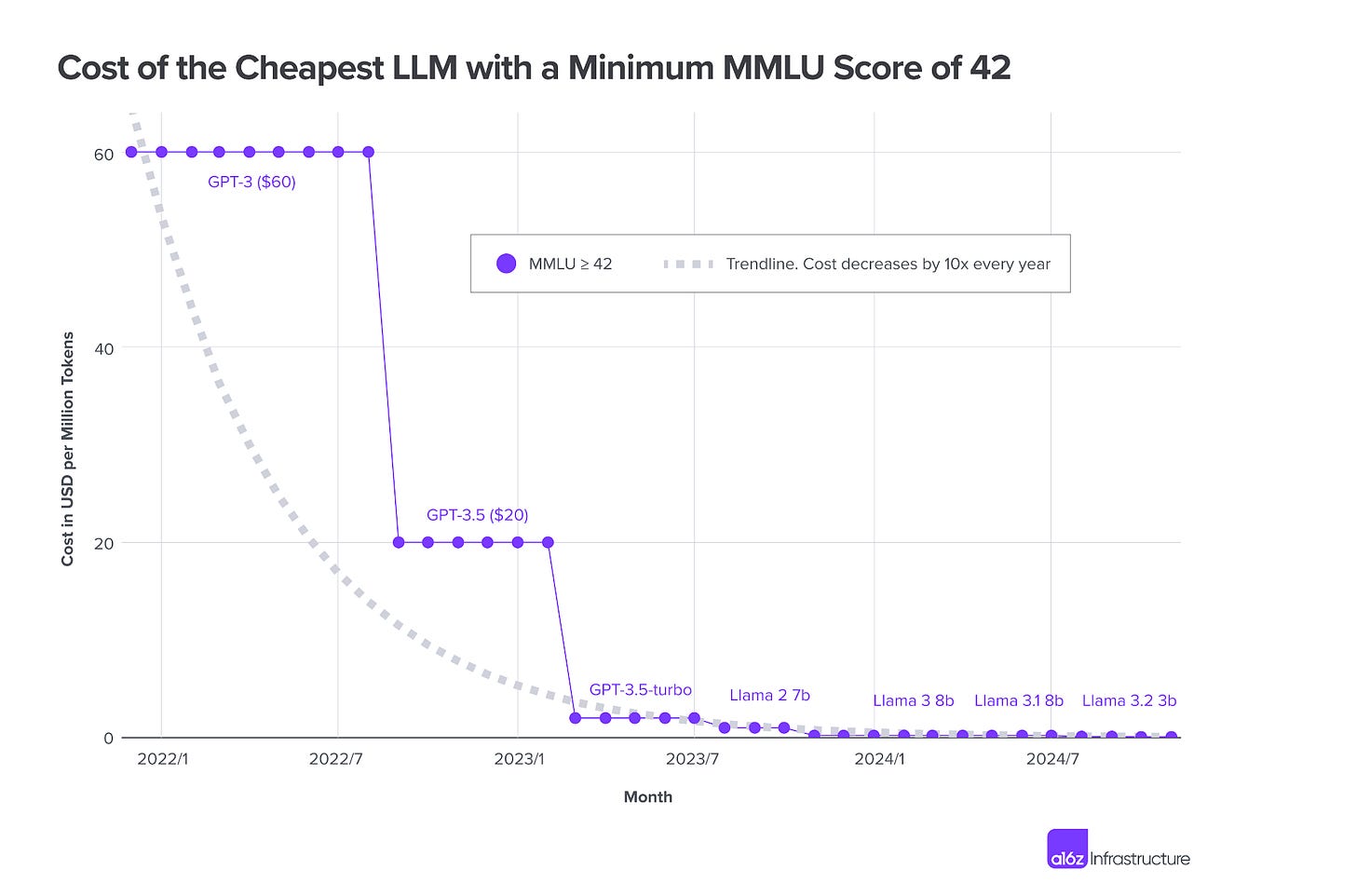
LLMflation - LLM Inference Cost is Going Down Fast
The technology industry is full of various “laws”, from Moores Law to Dennard scaling and now what this piece from Andreessen Horowitz calls “LLMflation”, which demonstrates the rapid decline is cost for LLM inference. It states “for an LLM of equivalent performance, the cost of decreasing by 10x every year”.
This of course is noteworthy given inference costs are a key part of the scale, cost and limitations as we continue to explore LLM’s and their novel use cases and potential.
The analysis is used with a metric dubbed “Massive Multitask Language Understanding” (MMLU). The article goes into detail on how this is measured, how various models measure up and discusses the probability that LLM prices continue to decline at the existing rate.
Department of Homeland Security (DHS) Releases Framework for Safe and Secure Deployment of AI in Critical Infrastructure
DHS recently released key guidance for the safe and secure deployment of AI in critical infrastructure. It was created by the AI Safety Board, which is a public private partnership established by DHS. The framework was both developed by and for stakeholders in the AI supply chain such as Cloud Service Providers (CSP)’s, AI Developers and Critical Infrastructure Owners and Operators.
The framework covers roles and responsibilities for the use of AI in critical infrastructure for each of these entities. For example CSP’s have responsibilities to secure environments and drive responsible model and system design, while whereas critical infrastructure owners and operators have responsibilities such as accounting for AI in their incident response plans (IRP)’s and ensuring system redundancy.
AppSec, Vulnerability Management and Software Supply Chain
CISA’s 2023 Top Routinely Exploited Vulnerabilities
Cybersecurity and Infrastructure Security Agency recently released a Join Cyber Advisory covering the most routinely exploited vulnerabilities in 2023. One of the things that jumped out to me is that nearly all of them except Log4j are commercial products.
Like many others, I am passionate about securing the open-source ecosystem and secure consumption and governance. That said, it is hard to argue with the fact that the most vulnerable and exploited aspect of our software supply chain is commercial products.
(One caveat here is that the most prominent vulnerability database, the NVD, isn't well suited for open-source for various reasons and we generally don't get insight into if the exploitation is of open source components and/or first-party code)
This is a bit of bad news, given we know that commercial vendors have little to no incentive to change this paradigm. There aren't sufficient market forces driving them to produce more secure products, since we know incidents have little to no impact on share price or revenue. Customers buying patterns rarely change, as confirmed by CISA themselves in another recent report, and vendors continue to grow and thrive despite security incidents and exploitation.
There also aren't currently sufficient regulatory forces to address the existing market failure, and we're headed for an even more de-regulatory administration, so that is unlikely to change.
So, it begs the question: What, if anything, will change, or will commercial vendors continue to externalize the risks and consequences of insecure products onto customers, consumers, and society?
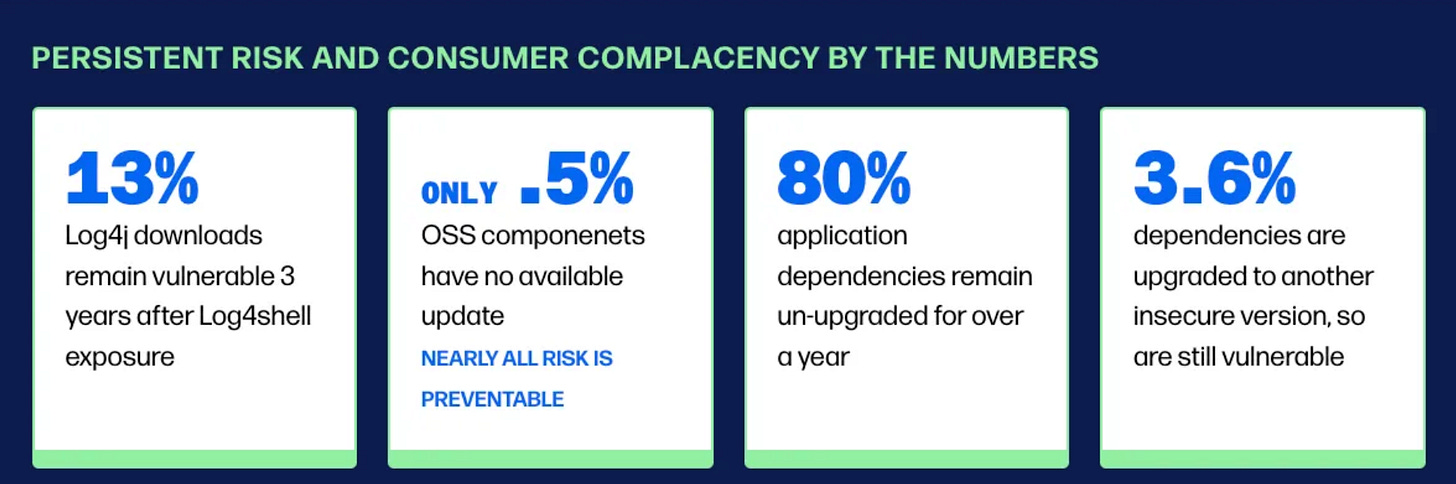
2024 State of the Software Supply Chain
Software supply chain has been a hot topic the last several years and rightfully so. I recently wrote an article taking a look at Sonatype’s 2024 State of the Software Supply Chain. This is a great annual report I cited several times in my book Software Transparency from Wiley.
A lot of great insights this year including:
Over 500,000 malicious packages discovered just since November 2023
13% of all Log4j downloads are of vulnerable versions
80% of application dependencies remain un-updated even after a year
As usual, we’re making it easier for attackers due to poor hygiene, a lack of open source governance and generally poor practices.
For a deeper analysis of the report and its finding, be sure to check out my article here.
Potential Cost Savings of Tool Consolidation
We’ve heard a ton of debate around best of breed vs. platforms, as well as the push for Application Security Posture Management (ASPM) tooling in AppSec. This piece from Ross Young of Team8 makes the case that rallying around an ASPM solution can offer not only cost savings but also improved AppSec outcomes. Challenges raised include cybersecurity tool sprawl and complexity.
I’ve written a comprehensive piece in the past on ASPM, titled “The Rise of Application Security Posture Management (ASPM) Platforms. The culmination of the convergence of ASPM, DevSecOps and Vulnerability Management” with my friend Francis Odum.









Thanks for flagging. Please be sure to take a look at the full document on lowering the cost of appsec tools. It’s really interesting
https://bunny-wp-pullzone-pqzn4foj9c.b-cdn.net/wp-content/uploads/2024/11/Fixing-AppSec-Paper.pdf