Resilient Cyber Newsletter #22
Presenting Cyber to Boards, Service-as-a-Software, U.S. Defense AI Memo, CMS Open Source Policy and Free but Not Cheap, the Open-Source Dilemma
Welcome!
Welcome to another issue of the Resilient Cyber Newsletter.
I’m excited to bring some awesome resources to you this week around cyber leadership, market dynamics, AI and AppSec.
Also, some personal notes. I’m coming off the birth of my 5th little one, and she’s been a beautiful addition to our family, less than two weeks old. I’ve held a lot of titles over my life, but Dad still continues to be the best.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 7,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cyber Leadership & Market Dynamics
Presenting to Boards - Do’s and Don’ts
We continue to hear about the importance of cybersecurity and the board. This includes the need for cybersecurity expertise on boards, as well as how CISO’s can best present organizational risks to the board.
This resource falls in the latter category. It’s a “Summary of Collective Wisdom For Presenting Cybersecurity to Boards: Preparation, Best Practices. DO’s and DONT’S of effective presentations to the board” by Rafeeq Rehman.
It leverages a collection of resources, such as Rafeeq’s popular “CISO MindMap” as well as others from the World Economic Forum (WEF), HBR and one of the best communicative security leaders I know in Omar Khawaja.
CISO’s and Security leaders continue finding themselves with a strong need to be able to effectively communicate with business peers, and these are some key recommendations to help on that front.
Stitching Together the Cybersecurity Patchwork Quit: Infrastructure
There’s no denying navigating the current regulatory and compliance landscape is both daunting and complex. So much so that the Office of the National Cyber Director (ONCD) has issued an RFI and results of inputs when it comes to regulatory harmonization, or trying to improve the problem when it comes to compliance complexity, which only continues to grow.
One of the sharpest minds I know on the topic is Jim Dempsey, Managing Director of the Cybersecurity Law Center at IAPP, Senior Policy Advisor at Stanford and Lecturer at UC Berekely.
In a follow up piece that focused on data and U.S. cyber policy, Jim published a piece recently focused on Infrastructure and connected products (e.g. cars, cloud computing, AI, Internet protocols and more).
He lays out the variety of rules, policies, requirements and more under both the current Biden administration and the previous Trump administration (which is now returning for a second term).
I will be chatting with Jim this coming Friday the 15th at 11AM ET on LinkedIn Live, as well as publishing a recording of that conversation on Substack, YouTube and podcast outlets for those who can’t make it.
We will be discussing the complex cyber regulatory landscape, where it stands now, and implications for the future based on the recent U.S. Presidential election outcome.
You can join us by clicking the image below!
I’ve had Jim on the show in the past as well, such as this episode with Chinmayi Sharma and Jim Dempsey where we discussed Software Liability and Safe Harbor.
Battery Ventures State of the OpenCloud November 2024 Report
Batter Ventures recently published their “State of the OpenCloud” report for November 2024 that was full of interesting insights.
They continued belief that AI will disrupt the services market, with what many are calling “Services-as-a-Software”, due to agentic reasoning and the ability of AI to automate traditionally manual labor intensive activities. This is something I have shared from others previously, such as Sequoia’s excellent piece on agentic-reasoning, as well as industry leader Chenxi Wang’s BSides SF talk “Navigating the AI Frontier: Investing in AI in the Evolving Cyber Landscape”, where she projected AI will disrupt the Cyber services market as well.
The massive role AI is playing in the growth of hyperscalers such as AWS, Microsoft Azure and Google.
The role that growth is still playing in multiples and valuations over profitability, despite some market corrections.
The report is full of great diagrams, charts and visualizations and I recommend giving it a read!
Congressional Warning to FTC - M&A to Open Back Up?
There’s been a lot of heated discussions around M&A scrutiny under the current administration, specifically aimed at FTC Chairwoman Lina Khan. Her scrutiny of M&A has led to various changes in the M&A landscape and organizations getting creative to avoid the increased attention from the FTC during M&A.
Senator Cruz recently penned a letter to the FTC and Lina Khan pointing out the recent electoral results, forthcoming changes to FTC leadership and warning that any additional rules, regulations and so on from the FTC should be put on hold and will receive increased Congressional oversight.
Another Blow To Security Certification Industry Credibility?
Historically cybersecurity certifications have already been questioned in terms of value. You’ll often hear practitioners say certifications =/= expertise. This is because some feel that just having a CISSP or similar automatically equates to security expertise and competence, when it doesn’t.
There are also a massive amount of certified and credentialed practitioners who still struggle to find work, meaning simply having a certification isn’t an automatic guarantee of employment (despite some claims, unfortunately).
On this existing skepticism and frustration with certification providers, news recently broke that security credential company CompTIA has recently been acquired by private equity. Many now suspect the costs may go up while the quality of the credentials go down.
Israel’s AI Startups Dominate Tech Investment Landscape
Unsurprisingly, Israeli startups seem to be dominating the AI startup landscape just like they do in other areas such as cybersecurity. We’ve discussed in previous issues how AI companies have dominated the venture landscape, and the trend appears to be the case in Israel, with AI companies where nearly half of total tech funding in Israel is tied to AI startups.
This further speaks to the dominant role of the Israeli tech startup ecosystem, as the nation now quickly positions themselves as a leader in AI, in addition to existing categories such as cybersecurity.
AI
Using LLM’s to Catch Vulnerabilities in Real-World Code
I previously discussed a blog from Google’s “Project Naptime” where they used LLM’s to demonstrate the potential to find vulnerabilities in code. This used Met’as CyberSecEval2 benchmarks and now Google’s Project Zero and Google DeepMind have announced they’ve done just that.
They recently announced the first real-world vulnerability discovered by their “Big Sleep” agent, which is an exploitable buffer underflow in SQLite, which is a widely used open source DB engine.
Their post goes into great detail on the methodology used by the team and Big Sleep to discover the vulnerability.
This demonstrates the rapidly improving potential of LLM’s to help identify vulnerabilities in widely used products and projects. While in this case it was done by a set of researchers who promptly reported it and had it fixed, that certainly won’t always be the case.
Malicious actors are absolutely experimenting with LLM’s to do similar activities but with the intent to exploit their findings, rather than report them.
OECD.AI’s Catalog of AI Tools and Metrics
I recently came across the OECD.AI Public Observatory. OECD is a global hub for AI policy and has been involved in various international efforts related to AI, from policy, to risk management to tooling and more.
This includes publishing and maintaining a comprehensive catalog of tools and metrics for trustworthy AI. Tools include those aimed at removing bias, securely collecting and processing data, measuring model performance and privacy. Metrics can be used to evaluate how AI systems align with trustworthy AI principles and popular AI frameworks.
This is definitely a rich collection of resources to keep bookmarked and use.
They even have a paper dedicated to garak, an open source AI security tool we discussed in last weeks issue about using AI to discover vulnerability, test AI systems and conduct red teaming. garak stands for “GenAI Red-teaaming and Assessment Kit” and can be used to discovery and identify vulnerabilities in a target LLM or dialog system.
Commentary on the Memorandum on Advancing the U.S. Leadership in AI
As I shared recently, the U.S. released its “Memorandum on Advancing the U.S.’s Leadership in AI”. This of course marked another example of the critical commitment of the U.S. Government and Department of Defense when it comes to AI and the future of U.S. innovation and competition related to technology.
The Center for a New American Society (CNAS) published a comprehensive editorial breaking down the AI Memo and key takeaways, providing insights from several industry leaders and analysts.
Rethinking Security Architectures: AI’s Impact on Cyber
NVIDIA recently held their AI Summit and their Chief Security Officer (CSO) David Rever had some great commentary around AI’s impact on cyber. AI is enabling new opportunities for attackers and defenders alike.
Reber broker AI’s impact on cyber defense into three areas, which are use cases for attackers, use cases for defenders and use cases for end users. We see a lot of excitement around using AI to streamline traditionally manual cumbersome activities and areas, especially SOC for example.
NVIDIA has built Cyber AI Framework dubbed “Morpheus” which can be used to improve defensive capabilities. Use cases include analyzing CVE risks using RAG, detecting sensitive information, ransomware and fraudulent transactions among others.
One aspect of Reber’s commentary that jumped out to me is the need for cyber practitioners to begin using AI now. As I have discussed in articles, Cyber tends to be a late adopter and laggard. This perpetuates the age old “bolted on not built in” despair that cybersecurity suffers from.
If we want to avoid this, we need to be an early adopter and quickly build proficiency in new technologies such as AI, so we can both better serve the business, but also keep pace with the evolutions of attackers.
AppSec, Vulnerability Management and Software Supply Chain
Centers for Medicare and Medicaid (CMS) Open Source Policy
The U.S. Federal Government continues to embrace Open Source, including pushing for each agency to establish an Open Source Program Office (OSPO). One of the most forward leaning agencies is CMS, which has an OSPO as well as a publicly published open source policy.
The policy discusses how CMS uses OSS on various internal mission critical programs and IT projects and lays out key considerations, government data rights and discusses how open source implementation and infrastructure works at CMS.
More agencies should follow CMS’ example and both codify and publish their approach to open source, which no doubt is embedded in nearly every IT project and product, whether internal to the agency, or consumed via external commercial off the shelf (COTS) products.
Vulnerability Metrics and Reporting
The Health-ISAC recently published a good whitepaper on the state of vulnerability, as well as vulnerability metrics and reporting. As they point out and I’ve discussed many times, including in my book “Effective Vulnerability Management”, the state of vulnerability management is abysmal. The number of vulnerabilities continues to grow exponentially YoY, and organizations are struggling to keep up, drowning in vulnerability backlogs in the hundreds of thousands to millions.
The paper discusses key topics such as:
Effective Communications for Metrics
Supplemental Metrics
Real world examples, such as aging vulnerability trends (see below)
Paved Roads, Secure-by-Design, Platform Engineering - Beyond the Buzzwords
We continue to see trends emerge in Cybersecurity, from Paved Roads, Secure-by-Design and more. This is a great piece from Srajan Gupta discussing some of these phrases and going beyond the surface level buzzwords to see what valuable activities and methodologies these phrases and trends offer to improve security outcomes.
He discusses how historically security struggles to keep up with engineering teams and then tries to curate a slew of policy documents for everything from authentication to encryption and secrets management.
The concept of Paved Roads has been embraced by leading engineering and security organizations such as Netflix but has begun to spread to many others. It includes a shift from policies to actual implementation and rather than a set of guidelines and policies to productizing security requirements in a way that makes adopting and implementing them easier for engineering teams.
It’s a shift summarized below:
“Are using <paved road> to <prevent-something>”
These examples may include logging packages, pre-built WAF and load balancer configurations, aimed at eliminating entire classes of vulnerabilities by systemically addressing key issues related to security. It makes doing the right thing the easy thing for security teams, making productized consumable resources.
It also intersects with Platform Engineering, or in the DoD/Federal Space “Software Factories” or Platform-as-a-Service, which aim to provide security control inheritance, leverage underlying IaaS/PaaS and provide consumable options from identity, access control, encryption and more.
The Essential Role of CVE’s in the Open Source Supply Chain
Common Vulnerabilities and Enumerations (CVE)'s. Often just called "vulnerabilities". While there are many more vulnerabilities than CVE's, CVE's are a critical and dominant source of vulnerability data for many, and serve as an authoritative identifier of vulnerabilities. They are also key in the software supply chain and open source.
This blog "Securing the open source supply chain: The essential role of CVE's" by Madison Oliver of GitHub is excellent. It covers:
What is a CVE, origins and the way it works
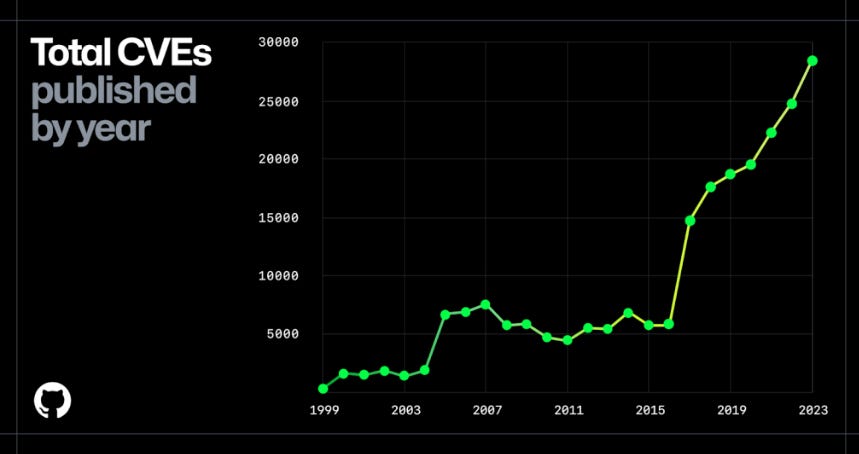
The double-edged sword of increased vulnerability data, including a 460% increase in CVE records over the past decade
The role of new vulnerability types and their widening impact through the software supply chain
Utilizing automation to tackle the overload of vulnerability data organizations are drowning in
Madison is an amazing leader in the Vulnerability Management community and I had a chance to interview her a few months ago. This article is very well researched, rich in not just information but citations and resources - I definitely recommend checking it out, along with some of the amazing work the GitHub Advisory Database team is doing!
Free but Not Cheap, the Open-Source Dilemma
The intersection of Open Source and Cyber is something I have discussed many times, from articles, talks, and both of my books, Software Transparency and Effective Vulnerability Management.
I found this conversation from TechCrunch Disrupt 2024 on the topic to be a great one, featuring Sequoia Capital’s Bogomil Balkansky, CISA’s Section Chief of Open Source Security Aeva Black and Tidelift Co-Founder Luis Villa.
They dove into the open source business models, challenges facing the open source ecosystem, the state of software supply chain attacks impacting open source and more.