Resilient Cyber Newsletter #2
Cyber for Board Directors, AI Red Teaming, WTF is CDR? Why the NVD is/was important and Beyond CVE's
👋 Hello, and welcome to Issue #2 of the Resilient Cyber Newsletter.
This week we dive into a wide variety of topics from Cybersecurity for Board Directors, AI Red Teaming, Cloud Detection and Response and more.
If you’re enjoying the content, be sure to subscribe below, and also please share it with your friends and network! 👇
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 6,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cybersecurity Leadership and Markets
Transparency vs. Risk Exposure - Analyzing Cyber Insurance and Public Disclosures
There continues to be a lot of attention to the level of transparency organizations have around the maturity of their security programs. This includes whether or not organizations maintain cyber insurance for example. Some may wonder whether transparency introduces more risk in same cases such as making yourself more of a target to attackers who know you have coverage.
This article from Andrew Heighington dives into the Pros and Cons of Publicly Disposing A Company Maintainers Cyber Insurance and any associations with increased risk.
It does this through analyzing publicly available 10-K and 8-K forms, the latter of which have been used as of late to disclosure security incidents that are “material” as part of the new SEC rules that were implemented.
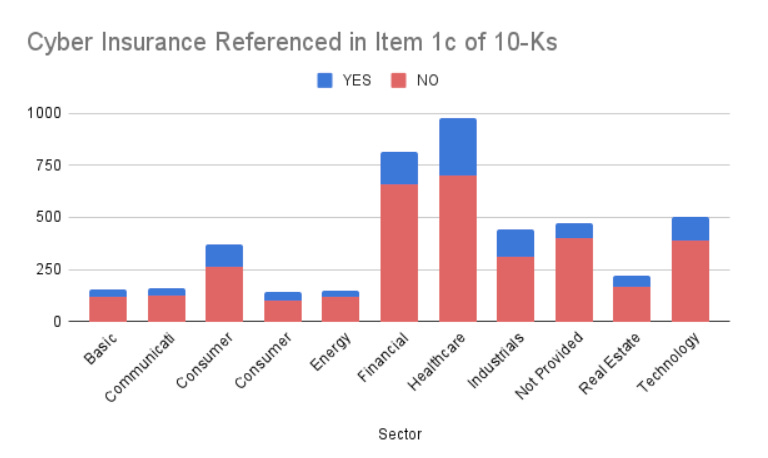
He found that the majority of organizations do not disclose that they maintain cyber insurance in annual 10-K’s, with roughly 25% of organizations doing so at this time.
Another interesting insight is that he found differences in organizations based on revenue size, as well as despite 26 8-K’s having been filed since the new SEC ruling took effect in December 2023, only one of the filings references cyber insurance.
Many are either not disclosing their use of cyber insurance, or choosing to self-insure (e.g. like United Health did).
Cybersecurity Academy for Board Directors
As we see the push for board of directors awareness, involvement and expertise around Cybersecurity, recently Jen Easterly shared that the CISA’s Advisory Committee, led by Dave DeWalt made several key recommendations for Corporate Cyber Responsibility.
This included a Cybersecurity Academy for Board Directors and they established a pilot program that took place at the U.S. Secret Service Training Center along with collaboration from NACD.
The Perilous Role of the CISO: Navigating Modern Minefields
Many have begun to question if the CISO role is actually worth it, as we continue to see burnout, increased regulations, legal troubles for CISO’s and more.
This is an excellent article from SecurityWeek discussing some of those challenges and the impacts they’re having on the CISO career field and industry as whole.
The article includes some good quotes from Robert Hansen, a Managing Director at Grossman Ventures and former CTO of Tenable. Robert shared the article on LinkedIn and said:
“It paints me personally to admit it, but the more people I talk to the more I think CISO’s simply need to hire that technical talent and focus themselves on the bureaucracy and relationship management required to be successful”
Many agreed with him, and it aligns with the push for the CISO to become a business leader among the CxO suite.
I personally think it is beneficial for CISO’s to have a sound technical foundation and be able to call bullsh*t when they see it from vendors and more.
That said, there’s no denying that the CISO role is increasingly becoming a business-oriented one.
I’ll also add that it depends heavily on the size of the organization. A CISO at a bootstrapped startup trying to get product market fit looks drastically different than a F500 CISO in a massive organization juggling a myriad of regulatory and legal requirements.
Microsoft Claims It Is Exempt from China’s National Intelligence Law, Echoing Huawei and TikTok
In a Congressional testimony around Microsoft’s security incidents and failures that continue to impact the U.S. Federal Government among the broader industry, Microsoft’s Vice Chairman and President Brad Smith claimed his company is not subject to China’s national intelligence law.
The law is used to compel companies to cooperate with China’s intelligence service, and it is widely known all companies operating in China are subject to it.
In a verbal exchange during the testimony Brad Smith claimed requests come across his desks that he refuses.
This topic of course is highly controversial due to the U.S. Government’s heavy reliance on Microsoft products, continued security incidents, and the potential that Microsoft due to its Chinese presence and relationship may be compelled to do things that further put U.S. national security at risk.
Ironically, in the story below, The White House is banning Kaspersky software for U.S. firms and citizens due to national security concerns, while many could argue the U.S. national security is much more at risk with Microsoft as of late, as we discussed last week in Resilient Cyber Newsletter #1.
Michael McLaughlin, author of “Battlefield Cyber” and former U.S. Cyber Command Senior Counterintelligence and Human Intelligence Strategic Advisory blasted Microsoft on LinkedIn, pointing out EVERYONE operating in China is subject to Chinese laws that compel access to networks and data.
If you haven’t read Battlefield Cyber by the way, I strongly recommend you do.
Biden Administration Bans Americans from Using Russian-made Cybersecurity Software Over National Security Concerns
This week it was announced that The White House was taken the uncommon step of outright banning U.S. firms and citizens from using software from the Russian firm Kaspersky Labs.
This comes in the long debate around the use of Kaspersky software, particularly in Government environments but now extends to the commercial industry as well.
The decision was made due to concerns that the company helps facilitate spying by Russia on U.S. citizens and organizations. Kaspersky of course denied the claims and even offered for a verified trusted third party to evaluate their software.
What is odd is the announcement will allow continued installed versions of the software to continue to be used but will not allow new versions/downloads and updates. As we all know, a lack of updates often leads to vulnerable software that can be exploited, in this case by others beyond Russia of course as well.
The irony of the discussion around national security concerns is that it comes at a time when U.S. based software company Microsoft, as discussed in last weeks newsletter saw extensive exploitation by foreign malicious actors, impacting organizations and individuals across the DoD and Federal Civilian Agencies alike.
AI
3 Promising AI Use Cases for Cybersecurity
Among all the fear of how AI will be leveraged by attackers and potentially make our digital landscape even more dangerous than it already is, many have hope for the role AI will play in bolstering our defenses and addressing longstanding challenges.
Among those are Google Cloud CISO, Phil Venables, who published a piece titled “3 Promising AI Use Cases for Cybersecurity”.
The three AI Use Cases for Cyber Phil lays out include:
Malware Analysis
Boosting SecOps Teams
Scaling Security Solutions
Phil discusses how Google has been using AI capabilities to perform Malware Analysis with great speed and accuracy, Google customers have been using NLP queries to expedite and improve security operations and the success Google has been having with improving vulnerability findings via Fuzzing with the use of AI models and tooling.
A Guide to AI Red Teaming
Red Teaming is a longstanding military and even cybersecurity activity. It is used to simulate adversarial activity and test the defenses and capabilities of systems/organizations.
The approach is being called for when it comes to AI as well, from the White House AI Executive Order (AI EO) to the EU AI Act.
That said, many don’t know what AI Red Teaming is, the differences between Red Teaming, Penetration Testing and Vulnerability Assessments, or what the benefits of AI Red Teaming are.
AI startup HiddenLayer produced a great blog discussing AI Red Teaming, which is worth a read, given the calls for the use of this activity in leading industry regulation and requirements.
Project Naptime: Evaluating Offensive Security Capabilities of Large Language Models
Google’s “Project Zero” team released a detailed update discussing the ability of LLM’s to effectively play a role in OffSec.
They built on earlier tests released by Meta in 2024 that included LLM benchmarks for discovering and exploiting memory safety. The Meta authors concluded “LLM’s have a ways to go before performing well” with regard to benchmark testing around OffSec and memory safety exploitation.
In the same vein, Project Zero, while improving the scores of LLM-powered vulnerability research testing, also concluded that “substantial progress is still needed before these tools can have a meaningful impact on the daily work of security researchers”.
Cloud & AppSec
WTF is CDR?
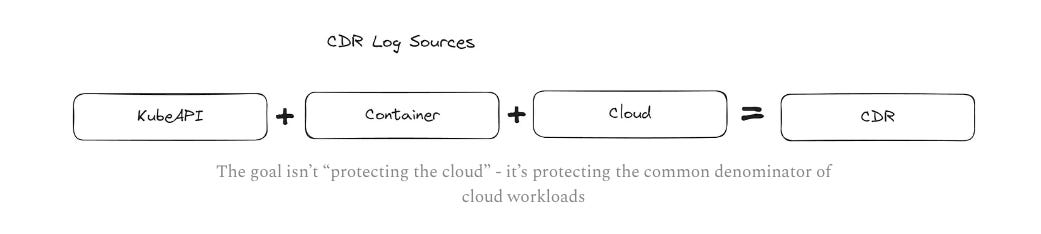
As an industry, we love our acronyms. One of the latest to come into use is CDR, which stands for Cloud Detection & Response. But what exactly is CDR?
This article from James Berthoty of Latio Tech dives into the topic and points out how many early Cloud Security Posture Management (CSPM) tools lacked coverage and capabilities around Kubernetes, despite it being the de facto container orchestration tool of choice in the industry, and many organizations increasingly running containerized workloads.
In fact, James points out that cloud workloads are 90% Linux, 76% containerized and 64% Kubernetes. This demonstrates the critical need for Kubernetes coverage when looking at CDR tooling.
He discusses how modern CDR tools such as Rad Security (whom I happen to be an advisor for, and an organization who was featured in the RSA Innovation Sandbox in 2024) are leaning into capabilities around eBPF and ensuring organizations are actually prepared and capable to perform CDR when it comes to Kubernetes and Containerized environments.
James’ proposed CDR definition is below:
Modern Approaches to Network Access Security
Despite our industry wide push to proclaim “the perimeter-based model of security is dead!” there is still a real need to discuss network access security. CISA released a paper titled “Modern Approaches to Network Access Security” where they discuss this topic.
It includes an emphasis on tens of Known Exploited Vulnerabilities (KEV)’s for traditional network access devices (e.g. VPN)’s being involved in incidents in the last year and the need to move towards more robust security solutions, including Zero Trust, Secure Service Edge (SSE) and Secure Access Service Edge (SASE).
fwd:cloudsec 2024 Playlist
One of the premier cloud security events wrapped up recently and their playlist of talks has been made available.
This includes a ton of excellent topics, such as:
Mapping Cloud Incidents to MITRE’s ATT&CK
Open-Sourcing AWS Pentest Methodology
Detecting Cloud Threats
The EKS Hacking Playbook
And a bunch more.
I’m a big fan of fwd:cloudsec creator/organizer Scott Piper and the amazing community of cloud security professionals he’s brought together.
I’ve interviewed Scott in the past in S5E2 of Resilient Cyber, in an episode titled “Modern Cloud Security and Resilience” which is here if anyone wants to give it a listen.
Common Vulnerability Scoring System (CVSS) V4 Impacts
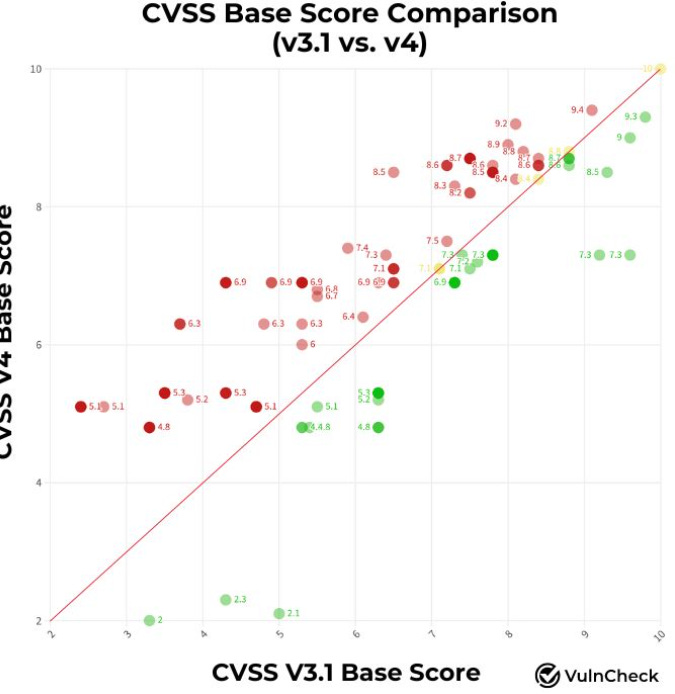
The CVSS is the most commonly used scoring system for applying severity ratings to vulnerabilities. Recently, some vulnerabilities began being scored in CVSS V4 as opposed to V3.1 and Vulnerability Researcher Patrick Garrity provided some insights into those impacts.
Overall, the shift to V4 is leading to an overall increase in CVSS base scores. The reason this is important is that most organizations take a generic approach of prioritizing vulnerabilities for remediation based on CVSS base scores (e.g. fixing “Critical’s” and “High’s”).
The problem of course is that <5% of ALL vulnerabilities (e.g. CVE’s) per year are ever actually exploited in the wild, so the approach of prioritizing based on CVSS base scores is incredibly inefficient and organizations need to shift to focusing on vulnerability intelligence factors such as known exploitation (e.g. KEV), exploitation probability (e.g. EPSS), reachability, business criticality and more.
Why NVD is/was important
By now, most in the industry have some exposure to the very public struggles of the NIST National Vulnerability Database (NVD). For those who weren’t following, or want more details, you can see my article “Death Knell of the NVD?”
To summarize, NIST’s NVD is the most widely used vulnerability database in our industry, with a longstanding history and pervasive use. Earlier this year they ran into technical, logistical and organizational challenges which led to the outright stalling of their activities around enriching vulnerabilities (e.g. CVE’s) with data such as CPE’s and more.
This excellent detailed blog from Security Researcher Ben Edwards dives into:
Why NVD is/was important
Where else can we look for data
The role of CISA’s Vulnrichment program
Road to recovery from NVD dependence
This is a great read backed by hard data (as Ben tends to do) discussing the NVD and broader industry vulnerability database considerations, and it is a key discussion for those responsible for their organizations vulnerability management programs.
The article is rich in graphs, such as the one below showing the number of CVE’s added to NVD in 2024 that were analyzed (or not!)
Ben’s article points out key insights around the vulnerability enrichment process, such as the fact that 37% of the time when a CNA submits a CVE they fail to provide the vendor and product information for which the CVE impacts. You can clearly see the downstream potential for organizations running vulnerability scans and being entirely blind to which products in their environment are actually impacted by a vulnerability due to this lack of data in the CVE record.
Ben also provided a useful diagram showing the number of CVE’s added to the NVD in 2024 and the number that are: Unanalyzed, enriched by CISA’s (DHS) Vulnrichment project, CNA analysis and NVD analyzed.
Beyond the CVE: Analyzing the Depth of GitHub Security Advisories
CVE's or Common Vulnerability and Enumerations are a core part of the vulnerability management ecosystem. That said, they are far from the full picture.
In fact, the more pervasive open source software (OSS) becomes, the more valuable alternative databases from the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) become. One of those amazing examples is the GitHub Security Advisory Database
This is an excellent article from Kyle Kelly covering:
- Background on the GitHub Security Advisory Database, including its overview and programming language coverage
- Evaluating the security advisory coverage contrasted with the broader OSS ecosystem
- The role of manual reviews, and the speed of CVE reviews at GitHub
Kyle demonstrates there are thousands of known advisories in GitHub's database with CVE's that are NOT in the NVD. He also touches on other OSS focused vulnerability databases, such as osv.dev
As the software ecosystem continues to become more complex, navigating the identifiers, databases, coverage, accuracy and ultimately prioritization becomes absolutely critical to mitigating organizational risks.
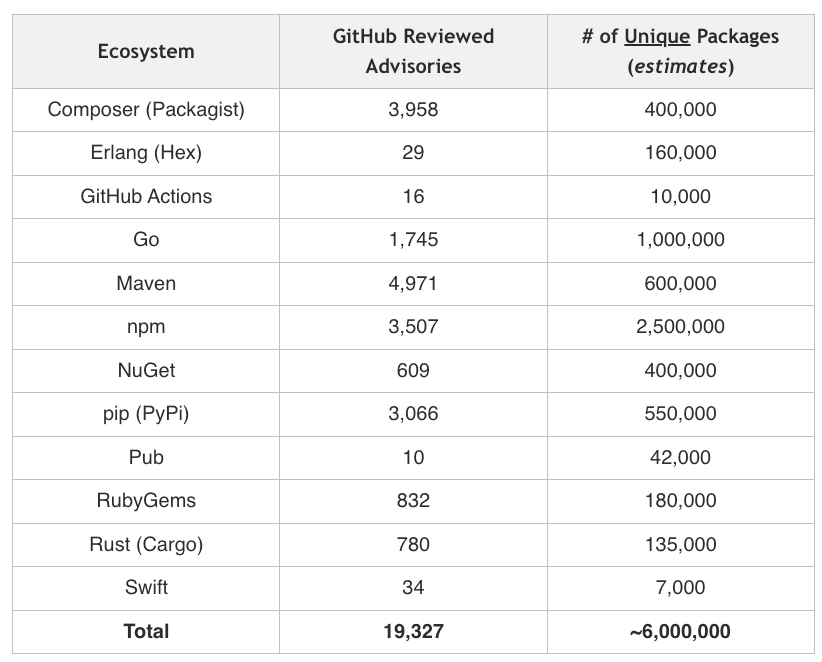
Below is a diagram of the package management ecosystem, # of GitHub Reviewed Advisories and estimated # of Unique Packages.
As the article points out, advisories generally require a manual review to be officially “approved”, and there are over 220,000 waiting to be reviewed. Many of them could be legitimate and critical vulnerabilities that simply haven’t been reviewed by GitHub yet. As the author also points out, there are roughly 20,000 security advisories in the GitHub database out of an estimated 60,000,000 software packages.
It’s not hard to imagine how many vulnerabilities have yet to be discovered, let alone reported, or reviewed, or approved.
Safe to say, we’re sitting on a massive pile of potential risk, making the chance of zero day discovery/exploitation likely, many times over.
NHI Attacks Making Waves: Insights on the latest 5 incidents
There continues to be a focus on Non-Human Identity (NHI) attacks in the industry, both from organizations realizing this attack vector and trying to make sense of it, as well as attackers increasingly looking to exploit NHI’s.
For those unfamiliar with NHI’s, you can see my article “What Are Non-Human Identities and Why Do They Matter?”
This article from Astrix Security discusses the latest 5 notable incidents involving NHI’s, including Snowflake, NYT and HuggingFace.
Snowflake’s incident made quite a few headlines and impacted hundreds of organizations. Most notable was the criticisms from practitioners around the lack of MFA enforcement from Snowflake and the need for customers to enable MFA - something many argued should have been a default requirement implemented by Snowflake on customers.
This has started a revived “the Shared Responsibility Model is broken!” chant for many.
Google has been championing a revision to the traditional Shared Responsibility Model, and I discussed it in my article “Cloud Shared Responsibility Model: Time for a (R)evolution?” where they propose a new model of “Shared Fate”.
Closing Thoughts 🧠
Several industry trends continue to gain traction, from calls for more governance, oversight, and expertise among boards when it comes to cybersecurity to novel exploration of AI use cases as well as potential remaining gaps.
We also continue to see widespread pervasive vulnerabilities and an imperfect vulnerability ecosystem that leaves many organizations struggling to build effective vulnerability management programs.
I’ve tried to provide resources in my latest book Effective Vulnerability Management when it comes to the vulnerability management landscape and how organizations can modernize their vulnerability management programs.
For those interested, you can find it on Amazon as well.