Resilient Cyber Newsletter #19
Cyber Anti-Patterns, Cyber is Going Private, Shift Left Was Founded on a Lie, OWASP Top 10 Proactive Controls and ASPM LinkedIn Learning
Welcome!
Welcome to another issue of the Resilient Cyber Newsletter.
This week we cover a lot of great content, including discussing common Cyber Security Anti-Patterns, sitting down with Palantir’s CTO to cover the importance of Digital Dominance when it comes to U.S. National Security and the fact that the “shift left” movement in Cyber was built on a lie.
So let’s dive in!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 7,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cybersecurity Leadership & Market Dynamics
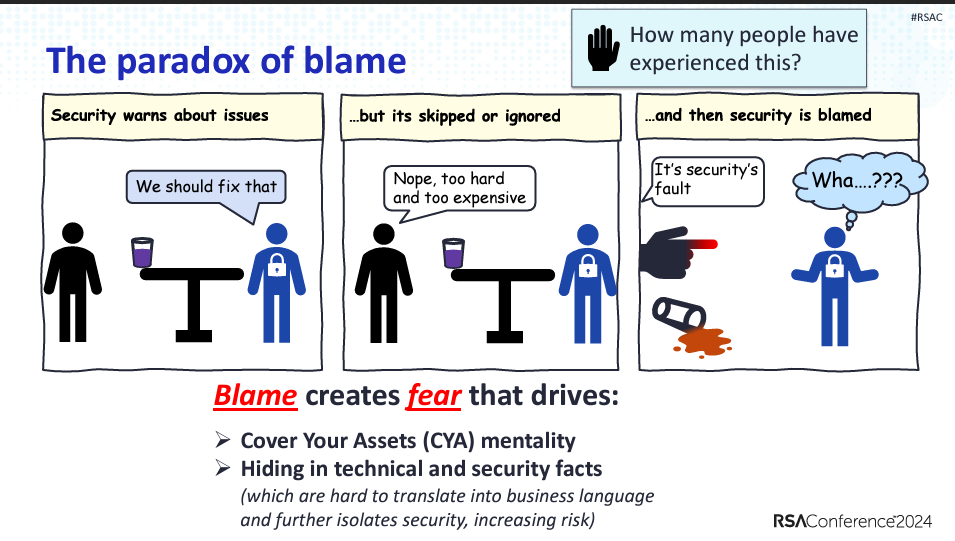
Common Cybersecurity Anti-Patterns
When we take a step back and look at things we do in Cybersecurity, we see that we are often our own worst enemy. From being the office of no, failing to consider business objectives, neglecting to embrace emerging technologies and the list goes on.
In fact, we have so many anti-patterns that someone could deliver a talk on it, and as it turns out, they have.
I had a chance to interview Mark Simos who delivered a talk at RSA earlier this year titled “You’re Doing it Wrong! Common Security Anti Patterns”.
The anti-patterns are also a core part of Microsoft’s Security Adoption Framework.
Find out talk below, as well as Mark’s talk at RSA here.
The Primacy of Digital Dominance
I’m personally very passionate about the intersection of commercial innovation and defense, as well as the crucial tie between economic prosperity and national security (a concept some in tech seem to miss).
That’s why I was so excited to get to hangout and chat with Palantir’s CTO Shyam Sankar. Shyam was among the early employees of Palantir, working up from IC engineering roles to CTO, seeing the firm grow over nearly two decades. He also runs a great Substack titled “First Breakfast” where he focuses on the the defense tech ecosystem, which I strongly recommend subscribing to.
In this episode of Resilient Cyber Shyam and I dove into:
The need for an “American Industrial Base” rather than the current paradigm where we have a Defense Industrial Base (DIB) and broader economy, with an ever growing gap between the two
The importance of commercial innovation when it comes to sustaining national security, especially in the age of digital warfare
The need for more competition in the defense ecosystem and avoiding misaligned incentives and ill intended outcomes
And much more.
I really enjoyed this one I hope everyone gives it a listen!
Cybersecurity is Going Private
While the headlines are often dominated by the latest rumors of who may IPO and when, the reality is that cybersecurity is increasingly going private.
In this excellent piece from Cole Grolmus of Strategy of Security he lays out how since 2022 twelve cyber-related companies have disappeared from the private market, including nine pure-play cyber focused companies, and the trend is likely to continue in the near future.
He also discusses how its been over 1,100+ days and counting since a pure-play cyber company went public. Not only are companies going private, but they are staying private far longer than previous eras, such as 2021.
2021 saw eight cyber-related companies go public on the U.X. exchanges, including the recording setting IPO of SentinelOne which was valued at $8.9 billion.
Cole argues the factors driving this trend include being able to make more strategic moves without scrutiny when private, increased concerns around M&A headwinds with Government oversight, and also an overall shift to focus on the actual profitability and long term financial health of companies as opposed to growth at all costs fueled by low interest rates (e.g. the “ZIRP” era).
While these figures may be depressing for some, the fact is that it also could be viewed positively and that when we do see companies go public they are likely to be in a far better financial situation than previous era due to these shifts in focus on financial health, sustainability and controlled growth.
AI
OpenAI’s Influence and Cyber Operations Report
As often discussed, AI is a double edged sword in the sense that on one hand it has the promise to improve the efficiency and effectiveness of cybersecurity but on the other, the potential to be abused by malicious actors.
OpenAI published an updated report into their observations of over 20 global operations and deceptive networks who have been trying to use OpenAI for nefarious purposes throughout 2024.
As summarized by Yotam Perkal:
𝐊𝐞𝐲 𝐓𝐚𝐤𝐞𝐚𝐰𝐚𝐲𝐬
- 𝐀𝐈 𝐚𝐬 𝐚 𝐃𝐨𝐮𝐛𝐥𝐞-𝐄𝐝𝐠𝐞𝐝 𝐒𝐰𝐨𝐫𝐝: While adversaries explore AI’s potential, defenders are using the same technology to quickly identify and counter suspicious behavior. OpenAI's tools can now compress analysis times from days to minutes.
- 𝐋𝐢𝐦𝐢𝐭𝐞𝐝 𝐈𝐦𝐩𝐚𝐜𝐭 𝐨𝐧 𝐄𝐥𝐞𝐜𝐭𝐢𝐨𝐧𝐬: There is currently no evidence of election-related influence operations successfully gaining viral traction or building sustained audiences using AI models.
- 𝐀𝐈 𝐂𝐨𝐦𝐩𝐚𝐧𝐢𝐞𝐬 𝐚𝐬 𝐓𝐚𝐫𝐠𝐞𝐭𝐬: A suspected China-based group, SweetSpecter, attempted spear-phishing OpenAI employees. While unsuccessful, these type of attempts indicate that AI companies are actually uniquely positioned to detect and disrupt cyber threats.
- 𝐌𝐢𝐧𝐢𝐦𝐚𝐥 𝐀𝐈 𝐈𝐦𝐩𝐚𝐜𝐭 𝐨𝐧 𝐌𝐚𝐥𝐰𝐚𝐫𝐞 𝐂𝐫𝐞𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐕𝐢𝐫𝐚𝐥 𝐄𝐧𝐠𝐚𝐠𝐞𝐦𝐞𝐧𝐭: So far, it seems that AI’s influence on advanced malware creation or large-scale disinformation campaigns remains limited.
The report also includes several case studies that illustrate real-world malicious activities detected and disrupted.
Beyond The Hype: Addressing the Security Risks of AI Co-Pilots
Interesting article from Forbes discussing challenges that AI Co-Pilots pose when it comes to amplifying longstanding challenges such as least-permissive access control. We know that Co-Pilots claimed productivity boosts involve needing access to robust sets of data within organizations and about users.
However, without appropriate implementation of fundamentals such as need to know and least-permissive access control scoped to users roles and functions, this has the potential to go very badly.
Given reports from Data Dog and others show 99% of existing permissions users have go unused (e.g. overly prescribed and too much access), we can likely guess where this will go.
Marc Benioff even took a swing at Microsoft Copilot and the general concept and its success so far.
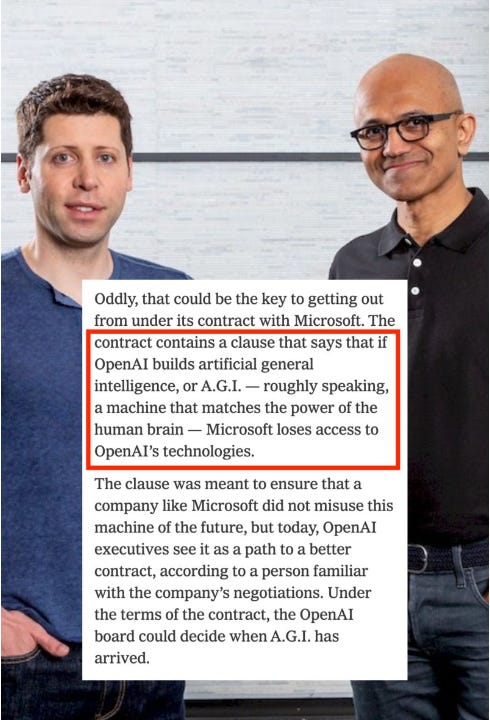
OpenAI Drama Continues
OpenAI is already no stranger to publicity and drama. From turnover among the founding team, massing funding rounds, and more.
Now, in the latest news, there are claims that OpenAI is threatening to execute a clause in its contract with Microsoft that if they achieve Artificial General Intelligence (AGI) that Microsoft loses access to OpenAI’s technologies.
This of course is a poised to be a hotly debated one given the definition of AGI is widely diverse and changes depending on who you ask.
Three GenAI Leagues Emerging
An interesting report from Accel titled “AI Eating Software” shows there are three leagues emerging as it relates to GenAI. They are the tech titans, AI majors and then AI challenges, as shown below:
The report goes into great detail on the broader state of the market, growth, cloud, AI and more. It is a quick read and worth the time. It shows that the NASDAQ is up 38% in the last 12 months, it shows of the $8.4T of value created in the past year, $5.3T of that was from the six tech leaders investing in AI.
AppSec, Vulnerability Management and Supply Chain Security
Shift Left Was Founded on a Lie
Anyone who has been around AppSec in the past 5+ years has heard the phrase “shift left”. Commonly used to describe moving security earlier the SDLC to identify and fix problems before they reach production.
This of course intuitively makes sense and it is logical to try and remediate defects before they can be exploited in production. The problem though has come in a recent report delivered by CISA and one of their subcommittee’s who pointed out the origins of “shift left” and the claims of cost savings are bunk.
The subcommittee recently submitted a series of reports to CISA, and check this out from the Secure-by-Design section of the report:
- It's a commonly held belief that fixing vulnerabilities is more cost effective (e.g. Shift Left) ↩️
- The software/security industry commonly references an IBM Systems Science Institute study that claims that fixing bugs during the design phase is 100 times cheaper than after implementation
The problem?
"Upon further research, there is 𝗡𝗢 evidence to show that the IBM Systems Science Institute was an official research body. It appears to be an internal IBM program that has not existed since the 1980's"
"There are also references to a 1988 claim by Barry Boehm that finding and fixing a software problem after delivery is often 100 times more expensive than finding it during the design phase"
The problem again?
"The specific cost factors used for this cost estimate 𝘂𝗻𝗰𝗹𝗲𝗮𝗿 and software development practices have evolved since the 1980's to be more agile"
This means the entire push for "Shift Left" in fundamentally built on false, non-official and speculative "research" and claims.
The real problem here is that the entire security industry has rallied around this battle cry.
Stuffing an acronym soup of low-fidelity noisy tools into CI/CD pipelines (e.g. SAST, SCA, IaC, Container Scanning and the list goes on)
Organizations now have vulnerability backlogs in the hundreds of thousands to millions
Security beats Developers over the head with these poor quality noisy outputs, slowing down velocity and ultimately the business.
If you're going to "shift left", you damn sure better do it with context, and high-fidelity findings that have true organizational risk.
Otherwise you're literally a business blocker, not an enabler.
OWASP Top 10 Proactive Controls
We know that by nature security is almost always reactive, rather than proactive. However, we continue to see industry efforts to try and change that paradigm.
The latest push comes from OWASP, in the form of the “OWASP Top 10 Proactive Controls”, authored by Andreas Happe, Jim Manico and Katy Anton.
They state the goal os the project is to “raise awareness about AppSec by describing the most important areas of concern that software developers must be aware of”.
Let’s take a look at the 10 controls in brief summary (I will likely author a more comprehensive piece examining them in detail later).
Implement Access Control
Use Cryptography to Protect Data
Validate all Input and Handle Exceptions
Address Security from the start
Secure-by-Default Configurations
Keep your Components Secure
Secure Digital Identities
Leverage Browser Security
Implement Security Logging and Monitoring
Stop Server Side Request Forgery
While the list is far from exhaustive (nothing in Security is), it definitely covers some absolutely fundamental controls that can mitigate outsized aspects of cyber risk.
Also notice how Secure-by-Design/Default are baked into the list.
That said, while the list may be simple, it is far from easy, especially in large complex environments.
ASPM LinkedIn Learning Course by James Berthoty
James Berthoty, of Latio Tech recently published his LinkedIn Learning course “Application Security Posture Management: Security from the Supply Chain to Cloud Runtime”.
James has quickly become one of my go-to resources when it comes to AppSec, as I really enjoy his perspectives coupled with my own and my experience and have had some great chats with him on various AppSec topics.
I jumped around his course and this is an excellent resource for the community when it comes to Application Security Posture Management (ASPM) and more broadly, better understanding AppSec in the age of cloud.
Be sure to check it out!
PRIscope: PR Inspector for Security Concerns and Open Source
Protection
Came across a really neat open source software supply chain tool that leverages a small AI model for AI-powered code analysis.
PRIscope is a Python-based tool designed to analyze the history of code changes in open-source repositories primarily to address software supply chain risks. It helps identify potential security risks or malicious code modifications by examining merged pull requests using an AI-powered code analysis.