Resilient Cyber Newsletter #18
Markets (still) DGAF about Security, Platform vs. Best of Breed Reframing, AI Readiness Guide, Picking an AI Governance Framework, and State of the Software Supply Chain
Welcome!
Welcome to another issue of the Resilient Cyber Newsletter. This week we will discuss a lot of great topics, including the relationship (or lack thereof) of data breaches and share prices, how the debate between best of breed vs. platforms needs to be reframed, a comprehensive AI readiness guide and the latest state of the software supply chain - so let’s dive in!
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 7,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cyber Leadership & Market Dynamics
The Relation Between Breaches and Stock Price Drops
In cybersecurity, we often try and push organizations to prioritize security by claiming incidents will damage brand, reputation, lead to financial losses and more. The truth however, is much more complex than that.
This article takes a look at the share prices of 118 companies starting the day before their public disclosure of their data breaches. It demonstrates that while there is a brief temporary dip, share prices bottomed out at just -1.4% 41 days after a breach and then began to rise, often to levels higher than when the breach originated.
The data did vary by industry, with retail for example having the least impact due to breaches and healthcare having the largest, although as discussed above, even then the impacts were not significant.
Interestingly, the study also shows breaches between 2015-2019 had little impact on share prices due to several high profile incidents and companies surviving just fine despite the incidents. This likely contributed to investors growing numb to headlines about security breaches and the incidents having decreased impact on share prices or investor confidence.
Cyber Companies Reluctant to IPO, Despite Strong Demand
This piece from the Wall Street Journal looks at the fact that funding rounds are up and customers are demanding products but cyber companies are still reluctant to list and push for IPO’s. This of course aligns with other resources we have shared and discuss showing significant slowdowns in not just Cyber but tech in general with regard to both M&A and IPO’s.
The article discusses trends such as changing in customer spending behaviors, stretched contracts and valuations for private companies plummeting in recent years. Rubrik was the first Cyber IPO since 2021 and is the only significant IPO in cyber this year.
While increased attacks and evolving compliance requirements are keeping demand high, there are still challenges with IPO’s when it comes to cyber and software. Some companies such as Abnormal and Wiz have publicly discussed their milestones to IPO, so it remains to be seen if the current lull changes anytime soon.
20VC Podcast Host Raises One of Europes Biggest Venture Funds
It was recently announced that 20VC Podcast Host Harry Stebbings raised one of Europe’s largest VC funds, at $400M. I’m a longtime listener of the 20VC podcast and can’t recommend it enough when it comes to VC, SaaS, Business and more. He has top notch guests and incredible discussions.
It also is a testament to building a personal brand, podcasting, the value of networking and an impressive fund raise in a notoriously difficult environment that is the EU.
Platform vs. Best of Breed is a Wrong Way of Looking at the Industry
There’s been a heated discussion the last year or two about best of breed point solutions vs. platforms, with large vendors such as Palo Alto and Wiz leaning into building robust platforms with broad capabilities and coverage while some vendors choose to stay focused on a specific niche problem set.
The conversation continued as security leaders looked to rationalize their portfolios due to tool sprawl and seek cost savings and arguably less fatigue for their teams. However, things have come full circle a bit, as some saw the Crowdstrike incident as an example of “concentrated” risk.
Nonetheless, in this piece from Venture in Security, Ross makes the case there are four, not two groups of security products.
Rather than there being two of best in breed vs platform, he makes the case it is a grid covering:
Types of products by areas of focus: point product (narrow), or platform (broad)
Types of products by depth of coverage: good enough (shallow), or best in class (deep)
This then leads to a four quadrant grid covering:
Best in class point products
Best in class platforms
Good enough platforms
Good enough point solutions
The article goes on to discuss the characteristics of each of the four company personas, when each may be the right fit for a buyer and more. This is a great mental model to orient yourself to the explosive product ecosystem that cybersecurity now owns.
AI
AI Readiness Guide
Rob Van Der Veer and the Software Improvement Group (SIG) have published a comprehensive “AI Readiness Guide for Organizations”. It is aimed at practice steps for leaders to implement AI in organizations, and focuses on AI governance, risk management, development and security.
For those unfamiliar, Rob is among the leading experts in AI Governance and Security, and I have had him on the Resilient Cyber Show in the past. He is also the lead of the OWASP AI Exchange, which is one of the most comprehensive vendor agnostic AI security resources available, which can be found here. I have also covered that in a separate article titled “x”.
The guide covers 19 different steps across four key areas of the organizations, such as:
The board
GRC
Security/CISO
IT, including Development (CTO)
Putting an end to the AI cyber responsibility turf wars
AI much like Cloud before it will involve a shared responsibility model. That is the case being made by Matt Keating and Malcom Harkins in this Cyberscoop piece. They cite the need for involvement from regulators, model developers, and end users to ensure effective security of AI.
They also make the case that the U.S. should follow the examples of others, most notably the EU, with their EU AI Act. They also echo the Secure-by-Design efforts from CISA, and Jen Easterly, stating speed to market over security cannot continue to be the model for innovation.
Notable AI Models
This is a massively insightful database, involving 800 models showing key insights around the level of training compute, compute costs, size of datasets and time spent training models.
It also shows the AI computing capacity of leading AI tech companies such a Google, Microsoft, Meta and Amazon, which can be seen below:
Comparing Agentic AI and GenAI in SecOps
SecOps continues to be one of the most discussed areas when it comes to the potential for AI, GenAI and LLM’s - and now, Agentic AI. This is due to the human intensive nature of SOC, the massive amount of noise, and the overwhelmingly amount of manual work required in highly performing SOC teams.
This piece from ReliQuest looks at both Agentic AI and GenAI and their potential for SecOps.
Picking AI Governance Frameworks
As AI adoption continues to accelerate, various industry frameworks have emerged to help govern AI. Some of these are internationally recognized, while others are specific to regions, such as the EU.
That said, given the global role of software and most organizations dealing with software, even nation or region specific frameworks often have a broad reach for organizations not located in those areas.
In this excellent article from Walter Haydock, he discusses three leading AI governance frameworks:
NIST AI RMF
EU AI Act
ISO 42001
AppSec, Vulnerability Management and Software Supply Chain
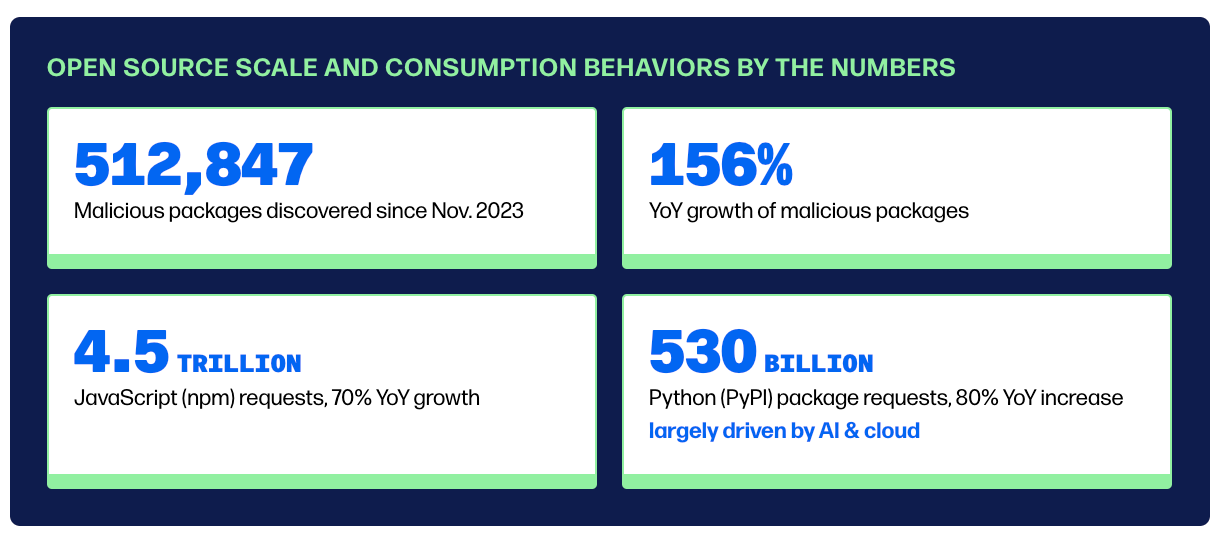
State of the Software Supply Chain
Sonatype published their 10th annual State of the Software Supply Chain report. This is one of the best annual reports on the state of open source security and software supply chain more broadly. It is something I cited several times in my book Software Transparency and a report I always am sure to check out every year.
It highlights some great insights, including both the scale of consumption of open source, as well as the massive growth in malicious activity across the open source ecosystem.
CVE Program Structure
Anyone who has worked in vulnerability management inevitably is familiar with Common Vulnerabilities and Enumerations (CVE)’s. These are often how vulnerabilities are formally identified, tracked, and reported. But few may understand how the CVE program itself is structured.
Vulnerability Research Yotam Perkal made an excellent post discussing the CVE Program Structure, including its hierarchy and entities involved.
While I won’t re-hash it all here, you can go to the post to learn more about the CVE hierarchy, CNA’s, the role of MITRE and more. It is a great concise way to understand how the CVE program itself functions.
To Platform or not to Platform
One of the hottest debates in AppSec and cyber recently has been around platform vs. point products, or best of breed vs. platforms. This piece provides insights from 451 Research, a market intelligence firms showing what is driving some of the behavior around platforms and buying behaviors.
Both perspectives of course have pros, such as in the platform approach which involves fewer vendors to manage, less distribution of accountability when things go sideways and more. This particular piece focused on SecOps, finding 99% of firms have a “primary” SecOps vendor with 36% of spending going to that primary vendor on average.
The study also surfaced some other potentially concerning findings, such as organizations saying 43% of security alerts from their SecOps systems go un-investigated due a lack of bandwidth and resources from their teams.
GitHub’s Advisory Database adds EPSS
GitHub’s Advisory Database now features EPSS scoring for vulnerabilities to aid in better prioritization.
For those unfamiliar, EPSS predicts the likelihood that a vulnerability will be exploited in the wild in the next 30 days, providing a score from 0 to 1 (e.g. 0 to 100%). It is massively helpful to reduce the noise developers deal with from scanning tools and helps them focus on findings likely to be exploited.
For those wanting to learn more, I have covered EPSS extensively in other articles, such as:
One of the best ways to view its value is looking at the diagram below, which shows the # of vulnerabilities exploited in the wild, vs the number you would be wasting resources on if you prioritized based on CVSS scores, which is the industry norm.
NVD Inflation
The rate of CVE’s in the NVD continues to expand rapidly, outpacing 2023. Researcher Jerry Gamblin pointed out that as of today (October 15th), we’re surpassing the number of CVE’s for all of 2023, with 77 days left to go in the year, we may even hit 40,000 CVE’s.
Now ask yourself, are you and your organization seeing YoY growth in your capability to identify, prioritize and remediate vulnerabilities? Research of course across the industry shows the overwhelming answer to that question is NO.
Which is why vulnerability backlogs continue to balloon out of control, and organizations desperately need to optimize their vulnerability prioritization and management approaches.