Resilient Cyber Newsletter #17
CISO Salaries, Threat-Informed Defense to Secure AI, NVD to Add AI, and Vulnerability Remediation Timelines
Welcome
Welcome to another issue of the Resilient Cyber Newsletter.
This week we have a lot of great resources and stories around CISO salaries, AI and AppSec, so let’s get to it!
I also wanted to give a special shout out to my friend Steve Wilson for the official publication of his book “The Developer’s Playbook for Large Language Model Security: Building Secure AI Applications”.
I have been reading a pre-released copy of the book for the past several months and can’t recommend it enough, especially as we dive in and grow around GenAI, LLM’s and broader AI security to keep up with the business adoption of these emerging technologies. I had a chance to provide an endorsement quote for the text.
You can grab a copy on Amazon here.
Thanks for reading Resilient Cyber Newsletter! Subscribe for FREE and join 7,000+ readers to receive weekly updates with the latest news across AppSec, Leadership, AI, Supply Chain and more for Cybersecurity.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 7,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cyber Leadership & Market Dynamics
Average North American CISO Pay now $565k
Insights from the IANS CISO Compensation Benchmark Summary Report, which surveys 755 CISO’s across the U.S. and Canada showed that the average North American CISO pay is now $565k.
Interestingly, the survey found that the most effective way for CISO’s to get pay increases was to either leave jobs, or threaten to, which led to an average compensation increase of 31%, versus just waiting around for a salary increase, which was only 6.3% annually on average.
This demonstrates that most organizations are very reluctant to lose their current CISO’s and willing to go to great lengths to retain them. This makes sense given it takes years to build cohesive and effective security programs in most large complex enterprise environments, through a combination of people, process and technology.
Another interesting note is that CISO turnover was down 50% since 2022, when 21% of those surveyed had changed jobs in the previous 12 months.
DoD Putting its Money Where its Mouth Is
The DoD recently announced they will be issuing nearly $1 Billion USD in loans to private companies to scale the production of technologies that the DoD has deemed critical. This will be facilitated via the Office of Strategic Capital.
Investments will range from $10M to $150M and they are looking to invest in 31 critical technology areas which were laid out in the 2024 National Defense Authorization Act (NDAA).
This continues the DoD’s push to bridge the divide between the DoD and commercial tech sector, as they urgently try and modernize, keep pace with foreign powers such as China and get innovative technologies into the hands of DoD Mission Owners and Warfighters.
Pentagon Gives Thumbs Down to Cyber Service
There’s been a lot of debate in recent years about establishing a separate cyber service within the DoD. However, this week the DoD asked lawmakers to kill a proposal that would require an independent assessment of establishing a separate cyber service.
Some lawmakers voiced frustration with the move by the Pentagon, stating they feel the U.S. “is not postured to overwhelm and out maneuver our enemies in cyberspace”.
There is still the potential that the DoD makes decisions around a cyber service based on previous studies and efforts, such as one that was commissioned and completed in 2023 by the RAND corporation.
Some some speculated the move originated within Cyber Command, who currently holds significant responsibilities for the DoD/U.S. in Cyberspace.
Venture Capital and Profitability: Navigating the New Investment Paradigm
Great piece of out Forbes discussing the paradigm shift in the VC space, where we are no longer seeing “growth at all costs”, facilitated by market fervor, zero interest rate percentages and a hyper focus on growing with little to no path to profitability in some cases.
The focus was all on valuations, becoming the next $1Bn “unicorn” and it didn’t matter how much borrowing or spending it took to get there. It was dubbed the era of “Blitzscaling” by Reif Hoffman and focused on capturing first mover advantages and quickly capturing market share over competitors.
The article lays out how it worked during the ZIRP era, but with the rising cost of capital, organizations are focused on sustainable business growth and either becoming profitable, or at least having a path to profitability. This means key business practices such as healthy margins, and operational efficiency.
It does discuss some potential downsides of this focus on financial discipline which may be the potential for it to hinder disruptive startups who need significant capital investment to drive their ideas to fruition (such as OpenAI, although they have had no issues raising insane levels of capital) - and the need to strike a balance between significant investments that may take a while to have an ROI as well as not just hyper-focusing on growth at all costs and neglecting sound business fundamentals, such as actually being profitable.
EU Could Die, Warns Macron
French President Macron warns that the EU could due to over-regulation and under-investment. He claimed the EU continues to fall behind the U.S. and China for these reasons and if things don’t change in 2-3 years, the EU would be “out of the market”.
We continue to see the EU take a much more aggressive approach to regulation than the U.S. from things such as GDPR, and recently the EU AI Act, the latter of which is leading technology companies to delay rolling out specific features and capabilities to the EU, such as Apple Intelligence.
Further making the point is the fact that the majority of European Defense Tech investments this year have come from U.S. investors and funds.
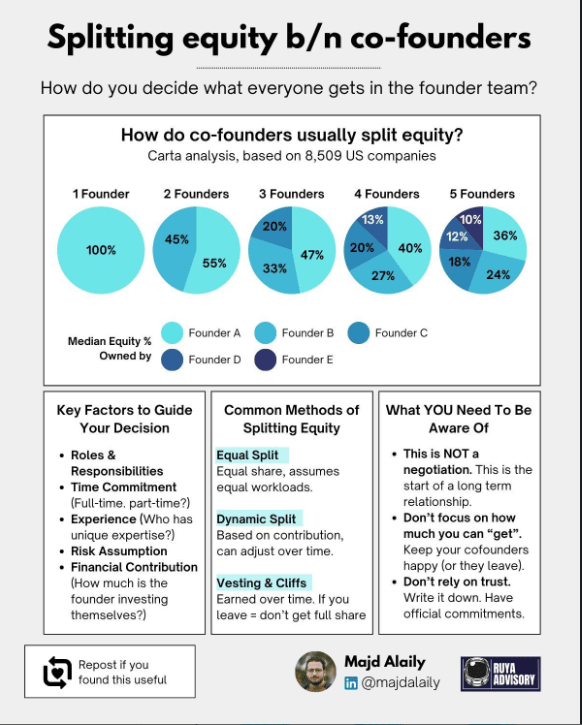
Splitting Equity Between Co-Founders
It is very common to see either two or more co-founders in most modern tech startups, including in cybersecurity. Usually you may see one founder with a deep technical background, while another may have complimentary skills such as marketing, business development, growth and business.
But how do most organizations go about splitting equity between co-founders?
Majd Alaily published some insights that include:
Key factors to guide equity decisions
Common methods of splitting equity
What you need to be aware of
Data from Carta, which was based on 8,509 US companies show potential common scenarios in companies with 1-5 co-founders, including median equity owned by each founder.
AI
Threat-Informed Defense to Secure AI
As organizations continue the rapid experimentation, adoption and integration of AI, there is a need for the community to stay up to date on relevant threats, vulnerabilities, incidents and mitigations.
That's why this "Secure AI Research Project" from MITRE ATLAS and Center for Threat-Informed Defense is really awesome.
It will facilitate the rapid information sharing for AI incidents, across government, industry, and academia to lead to a bolstered collective defense. It includes an AI Incident Sharing site
Leverages real-world case studies of AI attacks and incidents to help organization design and implement appropriate defenses
Utilizes MITRE ATLAS' knowledge base including attacks and mitigations to minimize and prevent the impact of AI-centric incidents
It also uses the Structured Threat Information Expression (STIX) to exchange cyber threat intelligence (CTI) related to AI attack, incidents and threats
Really awesome effort by Tabitha Colter, Shiri Bendelac, Lily Wong, Christina Liaghati, PhD and Keith Manville for the security and AI community
If you’re looking to learn more about MITRE ATLAS, you can:
My article “Navigating AI Risks with ATLAS”
My Resilient Cyber interview with MITRE ATLAS Project Lead Christina Liaghati
title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
How GenAI Can Transform Security Tools: Innovation Ahead
Forrester Principal Analyst Allie Mellen, who I’ve had on the Resilient Cyber Show in the past wil be hosting a free webinar discussing GenAI and security tools. She will be covering:
The current state of generative AI in security tools across security operations, Zero Trust, and risk management
The evolving role of generative AI in the CISO role, application security, and privacy and data protection
The true value that security teams can achieve with generative AI
The risks that generative AI in security tools can pose to security teams and how to prepare
The innovations leading the market in generative AI capabilities
Congress Advances Bill to Add AI to NVD
Congress recently advanced a bill dubbed the “AI Incident Reporting and Security Enhancement Act”, which would allow NIST to create a process for reporting and tracking vulnerabilities in AI systems.
However, it is worth noting that NIST currently suffers significant funding constraints and has a backlog of tens of thousands of vulnerabilities they haven’t processed yet, so I don’t have much hope for this.
AppSec, Vuln Management and Software Supply Chain Security
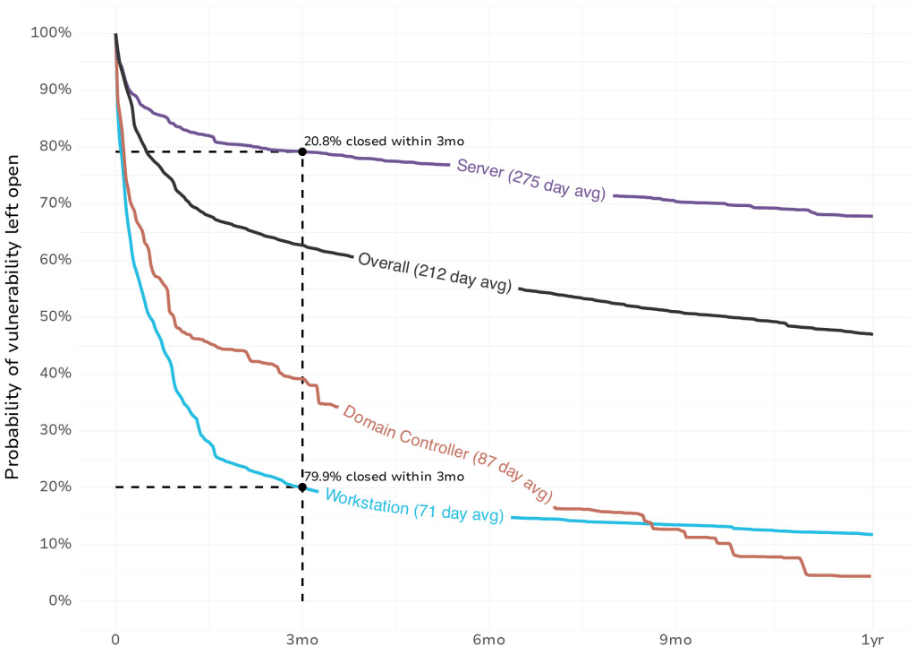
Vulnerability Remediation Timelines
Wade Baker of Cyentia recently shared some insights from a study they collaborated with vendor NopSec on, which shows average timelines for vulnerability remediation. Overall the average is 212 days, though timelines vary across workstations, domain controllers and servers.
These of course aren’t ideal, given that we know exploitation timelines for attackers continue to grow more aggressively, often attempting exploitation very soon after a PoC or exploit is made public.
This just further emphasizes the struggle organizations have, as vulnerability backlogs grow in the hundreds of thousands to millions, organizations are drowning in a sea of noise, making vulnerability prioritization absolutely critical.
Wade will be part of a webinar to discuss the findings here.
NSA’s Top Ten Cybersecurity Mitigation Strategies
The NSA released their Top Ten Cybersecurity Mitigation Strategies document which lays out a broad range of exploitation techniques commonly used by APO’s It lays out key 10 Cyber mitigation strategies and maps them to the NIST CSF Functions (e.g. Identify, Protect, Detect, Respond and Recover).
The list of the top 10 mitigation strategies is as follows:
Update and Upgrade Software Immediately
Defend Privileged Accounts
Enforce Signed Software Execution Policies
Exercise a System Recovery Plan
Actively Manage Systems and Configurations
Continuously Hunt for Network Intrusions
Leverage Modern Hardware Security Features
Segment Networks and Deploy Application Aware Defenses
Integrate Threat Reputation Services
Transition to MFA
Why Higher Education Should Prioritize Teaching Secure-by-Design
Veracode Founder Chris Wysopal makes the case that a key part of improving the security of software involves high education needing to prioritize teaching cybersecurity to software developers. The article points out several recent notable incidents, as well as the Secure-by-Design push from CISA.
The argument is that most computer science programs don’t teach cybersecurity, and if they do, it is an optional elective. Secure coding practices should be taught in the classroom, at the onset of developers education journey. The point is also made that some in academia lack real world exposure to modern development practices, toolchains and technologies, which will soon include GenAI coding assistants more and more as well.
While I understand the argument being made here, and think some level of cybersecurity education would be helpful for computer science students, I personally think a foundational knowledge of cyber and secure coding practices will still fall short because at the end of the day, incentives drive behavior within organizations, and organizations of course prioritize speed to market, revenue, and feature velocity over security, and understandingly so, given the market doesn’t punish those who produce insecure software and/or have significant security incidents, as mentioned about in the article about SEC 8-K’s and market reactions.