Resilient Cyber Newsletter #14
Wiz Announces "Wiz Code", Scorecarding Security, Cybersecurity Workforce Woes, How to Become a CISO and A Complete Guide to the Future of Cloud Security
Welcome!
A lot of interesting stories and resources this week. From a surge in cyber attacks target critical U.S. infrastructure, guidance on how to become a CISO, a peek into the surging AI spending and an impressive breakdown of the Cloud Native Application Protection Platform (CNAPP) space.
So let’s dive in!
DevOps Security Best Practices
Develop securely from code to cloud. This cheat sheet offers a deep dive into secure coding, infrastructure security, and vigilant monitoring and response.
A blend of industry insights and practical experience, each section combines theoretical knowledge with hands-on tips for application.
As you explore this guide, you'll uncover essential security practices, from input validation to zero-trust architecture, empowering you to create a secure DevOps environment.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 7,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Cybersecurity Leadership & Market Dynamics
Cyberattacks on U.S. Utilities surged 70% this year
Security company Check Point published metrics showing a 70% jump in cyberattacks on U.S. critical infrastructure during the same time in 2023.
The report highlighted vulnerabilities and risks impacting critical sectors such as healthcare and energy, including notable examples such as Colonial Pipeline, Haliburton and Change Healthcare.
Unlike traditional attacks which often just impact confidentiality of data, these attacks often have broader societal implications due to the presence of cyber-physical systems.
Wiz Makes a Major Announcement with “Wiz Code”
Many already know Wiz as a powerhouse cloud security company, setting records in revenue, Unicorn velocity, turning down offers from Google and more.
Now they rolled out Wiz Code, which focuses on transforming AppSec. This looks to extend their platforms coverage from code to runtime security, including during development, build/CICD and runtime environments in a unified platform.
The platform helps correlated critical attack paths from the cloud back to source code and the developer, offering remediation steps right within the code.This uses their famous security graph capabilities to tie everything together from code to runtime in the cloud including misconfigures, vulnerabilities, secrets and more.
It will be interesting to see how this new capability added to Wiz’s already impressive and highly successful platform impacts the broader AppSec space.
Second Front Raises a $70M Series C
The team at Second Front announced a $70M Series C, led by Salesforce Ventures and Batter Ventures, along with existing investors NEA, Moore Strategic Ventures and Artis.
I’ve had a chance to both watch the progress of the Second Front team, and collaborate with several folks on their staff. They offer an innovative promising Platform-as-a-Service (PaaS) dubbed “Game Warden” that accelerates the delivery of SaaS to government mission owners.
This alleviates longstanding cumbersome compliance and security requirements such as the DoD Security Requirements Guide (SRG) and FedRAMP.
I’ve written extensively about heavy handed compliance challenges in the public sector, in my article “Public Sector Compliance Conundrums: A look at the Federal and Defense communities grappling with the dichotomy between cybersecurity, innovation and compliance (FedRAMP, ATO’s & Self-Attestations)”.
The government desperately needs to achieve various digital modernization efforts on both the civil and defense sides of the house, but due to compliance requirements, innovation SaaS startups often cannot afford to navigate the compliance and security requirements which can take months to years and costs hundreds of thousands to millions of dollars in some cases.
This leads to deep gaps between commercial software innovation and Federal/Defense IT capabilities, which impact citizen services and national security outcomes alike.
Scorecarding Security
We continue to look for effective ways to incentivize and drive productive security outcomes. One of those ways involves scorecarding - which is moving aware from security being the office of no, and having an actual partner-based approach with developers, engineers and the business.
This blog from, Rami McCarthy of High Signal Security discusses the concept of Scorecarding Security, using several examples from innovative forward leaning security teams across the industry.
It provides use cases and examples, as well as key takeaways to moving the security program towards the scorecard based approach.
18F Publishes De-Risking Government Tech v2 Guide
It’s no secret that innovation and scaling technology in the Government can be tough (see my article right above this one). In fact, only 13% of Government technology projects succeed.
That’s why this “De-Risking Government Tech” from the 18F team is so useful. For those unfamiliar, 18F is a team of designers, software engineers, strategists, and product managers within the General Services Administration. They help other government agencies build, buy, and share technology products.
The guide helps with two main challenges:
How to choose a software solution
How to work with a vendor to build quality custom software
The two challenges are covered in four sections, which are:
Understanding and choosing a software solution
Four key principles for effective custom software development
Buy custom software development services
Working with a vendor development team
This is such a useful guide, because the Government outsources a TON of its IT either through purchasing commercial software solutions or paying a contractor to build it. In many, many cases, this ends up going sideways leading to cost overruns, failure to deliver, poor outcomes and more, with the citizen and tax payer ultimately paying the price.
Following the principles and recommendations in this guide can help Federal agency avoid many common pitfalls and mistakes.
Cybersecurity Workforce Woes
The workforce woes in the cybersecurity industry continue.. On one hand we keep getting gaslit and being told there are “hundreds of thousands of open cyber jobs”, meanwhile real world experience and insights tell another story, see below:
I recently wrote an article titled “Cybersecurity Workforce Woes: A look at the current cybersecurity workforce challenges and the factors involved” which breaks down the various entities, complexities and challenges at play that are leading the perceived cybersecurity workforce “crisis”.
How to Become A CISO
Many cybersecurity professionals aspire to one day be a CISO, or Chief Information Security Officer. The CISO is the perceived pinnacle of the cybersecurity practitioner career field, leading teams of security expertise to mitigate organizational risk and implement effective security programs.
But how does one actually become a CISO?
In a recent Resilient Cyber Show episode I sat down with industry leader Ross Young to discuss the keys to becoming a CISO. Ross is the current CISO at Team8, former CISO at Caterpillar Financial Services, Divisional CISO at Capital One and former CIA.
AI
Free AI Security Fundamental Course
The team at Microsoft has released a FREE AI Security Fundamentals Course. It covers basic concepts of AI Security, types of security controls that apply to AI systems and the security testing procedures that you can implement in AI systems to increase the security posture of AI environments.
The Case for Pathological AI
A thought provoking article from Sounil Yu of AI Security startup Knostic. Sounil looks to make the case for “pathological AI”, which is oriented around secrecy and the restriction of knowledge flows.
This involves the implementation of AI checks and balances and ensuring safeguarding against AI outputs that may be risky and implemented with proper oversight and governance.
Cybench - A benchmark for evaluating the cyber capabilities and risks of LLM’s
There continues to be a lot of excitement about the potential for LLM’s to help identify vulnerabilities, develop exploits, implement remediations and more. These LLM’s and agents can have potential use for both white hat defenders and researchers as well as black hat malicious actors with destructive intent.
A team at Stanford University put together a study of over 40 professional level CTF tasks from 4 CTF competitions which spanned a wide range of difficulties and use cases.
They evaluated the capabilities of 7 different models, and found that only the easiest tasks could be completed by the models, which typically take 11 minutes for human teams to solve. They also looked at subtasks to measure performance, including unguided runs and found that models had a 3.2% higher success rates when the models were given subtask guidance.
Really interesting research showing the early success rates and applicability of LLM’s for both defensive and malicious cyber activities in the realm of vulnerability discovery, exploitation and remediation.
On the surface, this shows promise, given that generally most agree that models will continue to learn, evolve and improve in terms of capabilities.
The AI Spending Spree in Charts
The amount of spending in and around AI continues to be astounding. This includes massive infrastructure investments from some of the largest hyperscale cloud and software companies.
A recent article from The Wall Street Journal really helps put it in perspective, showing in the last quarter alone, Amazon, Microsoft, Alphabet and Meta spent a combined $52.9 billion.
These investments represent one of the biggest boons in spending in U.S. history with companies betting big on the future implications of AI, and each looking to quickly establish themselves as leaders in the space.
As the CEO of Google is cited in the article as saying “The risk of underinvesting is dramatically greater than the risk of over-investing”, this is due to the great advantage their peers would get if their bets pay off and if those playing it safe get left behind.
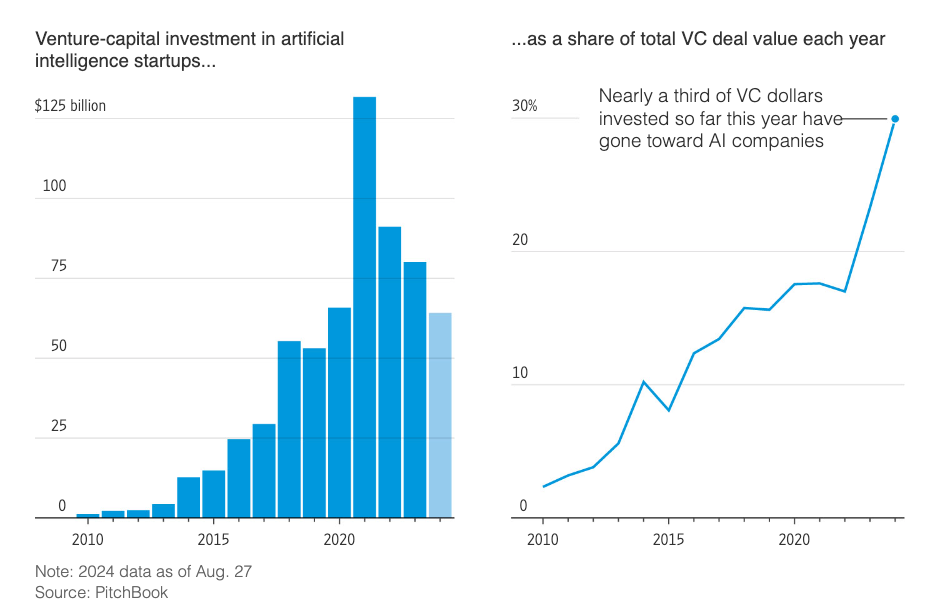
The article also points out that VC’s are heavily betting on AI, with $64.1 billion being invested in AI startups this year alone, despite most of them not actually being profitable, leading some to speculate if we’re living through a bubble as well.
Another key insight from the article is the massive investments going into new data centers and infrastructure, with Microsoft more than doubling its data centers since 2020, Google’s being up over 80% and Oracle having plans to build 100 new data centers.
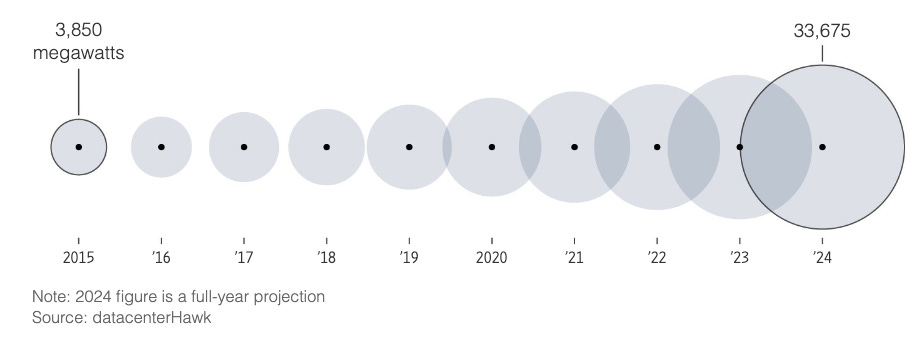
This has interesting implications and ramifications for the U.S. and Canadian energy grids, as they show commissioned power for the data centers has increased 9x since 2015. Couple that with the article I shared earlier above showing that there is a massive uptick in cyber attacks on critical infrastructure, with energy being particularly vulnerable.
AppSec, VulnMgt and Supply Chain Security
A Complete Guide to the Future of Cloud Security
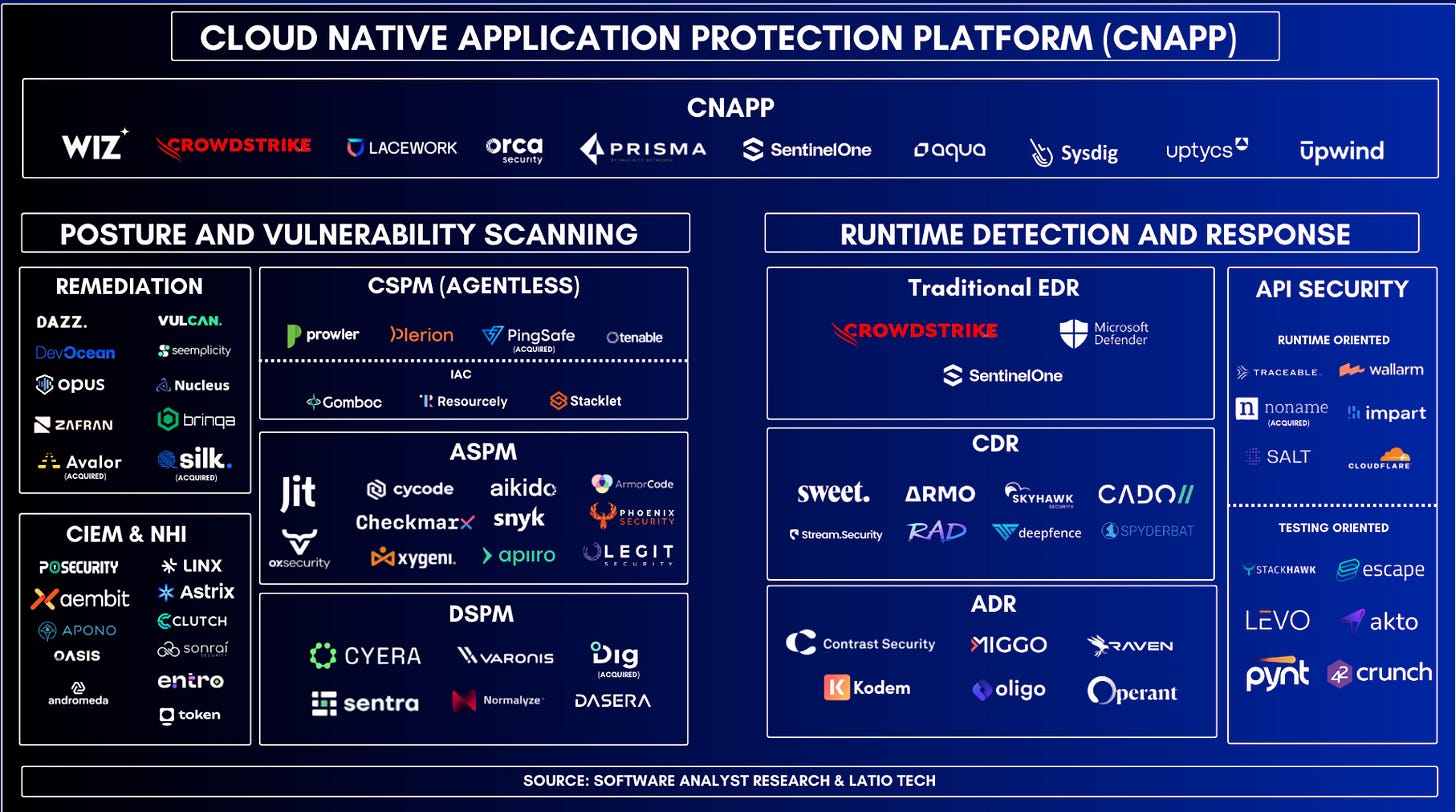
James Berthoty of Latio Tech and Francis Odum of The Software Analyst paired up to produce an absolutely powerhouse of a piece titled “Redefining CNAPP: A Complete Guide to the Future of Cloud Security”
While the piece orients around Cloud Native Application Protection Platforms (CNAPP)’s, it is MUCH deeper than that, covering the entire history of Cloud Security, where it is now, and where it is headed. This includes covering three primary phases or waves of Cloud Security, which they define as:
2010-2014: CSPM and the Shift to the Cloud
2015-2018: Innovations in Workload Security
Post 2018: Synergies around CNAPP
The article covers key vendors, open source tooling, M&A activity, the evolution of CNAPP’s and the role of agentless vs. agent-based cloud security tooling.
It also discusses numerous other emerging categories, such as Kubernetes Detection and Response (KDR), Cloud Detection and Response (CDR) and Non-Human Identities among others.
If you do anything related to securing workloads and applications in the cloud, this is an absolute MUST READ.
Microsoft Looks to Move Vendors OUTSIDE the Kernel
In the fall out of the CrowdStrike incident there has been a massive focus on the Windows Kernel. This includes the fact that many security product vendors have Microsoft Kernel level access, allowing for deep context and visibility, but also potentially disruptive activities, as we saw in the case of CrowdStrike.
As everyone is now aware, a faulty software update caused millions of PC’s around the work to have a “blue screen of death”. The kernel is the core of an operating system (OS), including Windows, and CrowdStrike and other security vendors often have this level of access to prevent malicious activity and gain deeper insights.
Removing vendor access to the Microsoft kernel is not a new topic, and Microsoft looked to do that in 2006 with Windows Vista but faced industry pushback from security vendors and regulators, who have voiced concerns about being locked out of the kernel despite Microsoft retaining kernel level access and having similar competing security products, potentially giving them a competitive advantage due to Microsoft’s dominant role in the OS ecosystem.
The feedback again has been mixed, with some praising the move, to lead to a more resilient Microsoft ecosystem, while others have voiced concerns again around the unfair advantages it would give Microsoft.
It will be interesting to see how this one plays out given the merit of points on both sides, as well as the history around the topic.
Revival Hijack - 22,000 Packages At Risk
The team at JFrog recently highlighted concerns with a PyPI hijack technique being exploited in the wild that puts 22,000 packages at risk. The technique involves re-registering PyPI packages once they have been removed from PyPI’s index by the original owner (hence the “revival” hijack name).
The team points out this puts 22,000 existing packages at risk and could lead to hundreds of thousands of malicious package downloads. They show how it has been done with the “pingdomv3” package and are looking to raise awareness around the possible attack vector and actions that can be taken to protect the PyPI community from the hijack technique.
This continues to highlight both the innovative approaches attackers are taking when it comes to software supply chain attacks, as well as the widespread pervasive impact of package managers and the open source ecosystem on downstream consumers and organizations.