Identity Threat Detection & Response for NHI's - What Does Right Look Like?
Approaching NHI ITDR using Permiso's ITDR Playbook for NHI Compromise
While Non-Human Identities (NHI) are no longer a foreign term to most organizations due to the rise of NHI-related incidents and exposures, many are still in the early stages of modernizing their threat detection and response when it comes to NHI.
That’s why I wanted to take some time to dive into what right can look like and where teams can get started by using Permiso’s ITDR Playbook for NHI Compromise as a guide.
That said, for those who are still unfamiliar with NHIs, I wanted to recommend a couple of prior articles I’ve written on the topic, which discuss aspects such as the rise of NHI threats, challenges organizations have in managing NHIs, and how the explosive growth of these credentials exacerbates longstanding identity and access management (IAM) challenges.
With those fundamentals out of the way, let’s take a deeper look at what Identity Threat Detection & Response (ITDR) looks like for NHIs.
Interested in sponsoring an issue of Resilient Cyber?
This includes reaching over 40,000 subscribers, ranging from Developers, Engineers, Architects, CISO’s/Security Leaders and Business Executives
Reach out below!
Setting the Stage
Permiso’s guide’s opening act emphasizes a key point: the majority of incidents based on industry-leading reports can be traced back to credential compromise. While some attack vectors, such as application exploitation, have seen a surge in recent years, others fluctuate; however, credential compromise consistently ranks as the leading attack vector in the report.
Worse yet, while the trend of credential compromise has remained dominant and consistent, organizations’ ability to actually detect these incidents within 24 hours has dropped drastically, from 90.3% to 60.6% in a single year. Much of this could likely be traced back to the fact that while organizations have reached some level of maturity around traditional human user ITDR, the same can’t be said when it comes to NHIs, as most lack fundamentals, such as a solid inventory, let alone the ability to detect the compromise of NHIs effectively. In fact, it is so bad that the compromise of credentials, such as service accounts, goes undetected for over 200 days.
That is a massive amount of dwell time for malicious actors to conduct activities such as moving laterally, establishing persistence, exfiltrating sensitive data, and more. To reduce this dwell time, effectively identify NHI compromises and mitigate organizational risks, teams need to modernize their ITDR to account for NHIs as a key growing attack vector.
Malicious actors are only increasing their targeting of NHIs as well, with the list of notable incidents in recent years only growing, with examples such as the U.S. Treasury Network, HuggingFace incident, and even nation-state attacks targeting leaders, such as Microsoft, to name a few.
What do Compromised NHI Indicators Look Like?
A foundational aspect of detecting NHI compromise is knowing what to look for, which is where the report starts its focus. Some of the key indicators of compromise (IoC) include:
Credential exposure events
Privilege accumulation
Operational pattern breaks
Secret lifecycle violations
Cross-boundary usage
Given the variety of NHs, their exposure can vary depending on the credential involved. In some cases, it may be API keys or secrets committed to or exposed in source management repositories. In other cases, it may include secrets being exposed in organizational ChatOps and environments, or perhaps exposed on internal wikis. Having the capability to monitor these environments for the exposure of NHIs is key.
Much like their human counterparts, NHIs often function like a black hole, exerting a gravitational pull when it comes to the accumulation of privileges. Despite the broad industry push for zero trust and foundational controls such as least permissive access control, most human users, along with NHIs, tend to accumulate excessive privileges. Maintaining visibility and governance of the permissions associated with NHIs can reap significant benefits, as it limits the blast radius and potential organizational impact if they are subsequently compromised.
Another key indicator to monitor is any changes in anomalous behavior patterns, particularly those related to usage and activities associated with NHIs. Permiso highlights examples such as APIs being called from new source addresses, activities occurring outside of standard windows, or accessing resources not commonly used for that NHI, as these may indicate something nefarious is happening and may require intervention.
Secret lifecycle violations can also be indicative of malicious activity. Examples such as authentication attempts with expired credentials or revoked certificates still validating could demonstrate not only an incident involving NHIs but also the trusted credentialing systems that underpin their operations.
Permiso rounds out the indicators with cross-boundary usage, such as production credentials from development environments or cloud credentials being utilized from on-premise environments. These often indicate that a credential may be compromised and reused across environmental boundaries in ways it wasn’t intended for.
Don’t Overlook Logging
You can’t protect what you can’t see.
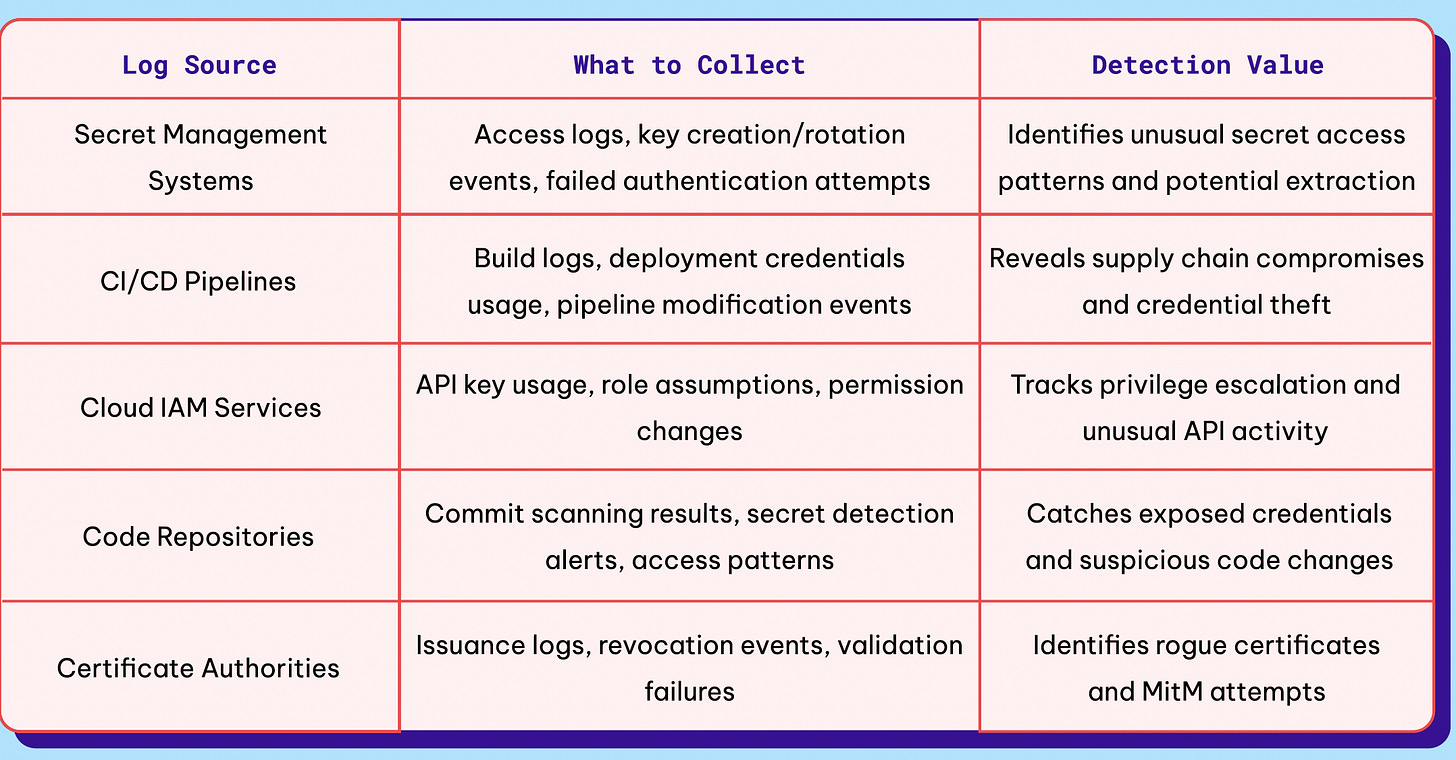
The above line is a common retort in cybersecurity and for good reason. It is impossible to protect systems and environments for which you have poor visibility, and a key aspect of gaining that visibility is logging sources. Permiso provides an excellent summary of logs, including log sources, what should be collected, and how it can help drive ITDR for NHIs.
All of the identified log sources are key locations where NHIs can and often are exposed, as well as locations where malicious actors are seeking exposed NHIs. Being able to monitor these sources provides tremendous detection value from an ITDR perspective.
What does an ITDR Process Look Like?
While many organizations have now experienced an NHI-related incident, most don’t have formalized or structured processes for responding to them. This is problematic, especially as NHIs grow as both part of the attack surface and as an enticing target for attackers.
Once organizations have alerting and detections in place, knowing how to respond can be the difference between a disaster and order. This includes determining the validity of an alert and engaging the appropriate teams with context to validate if the behavior is anomalous or not.
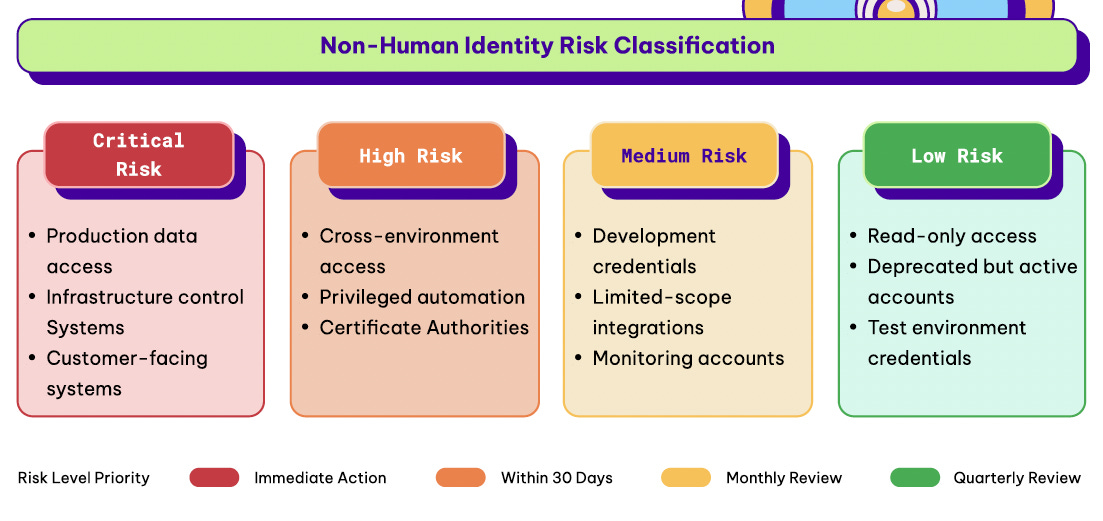
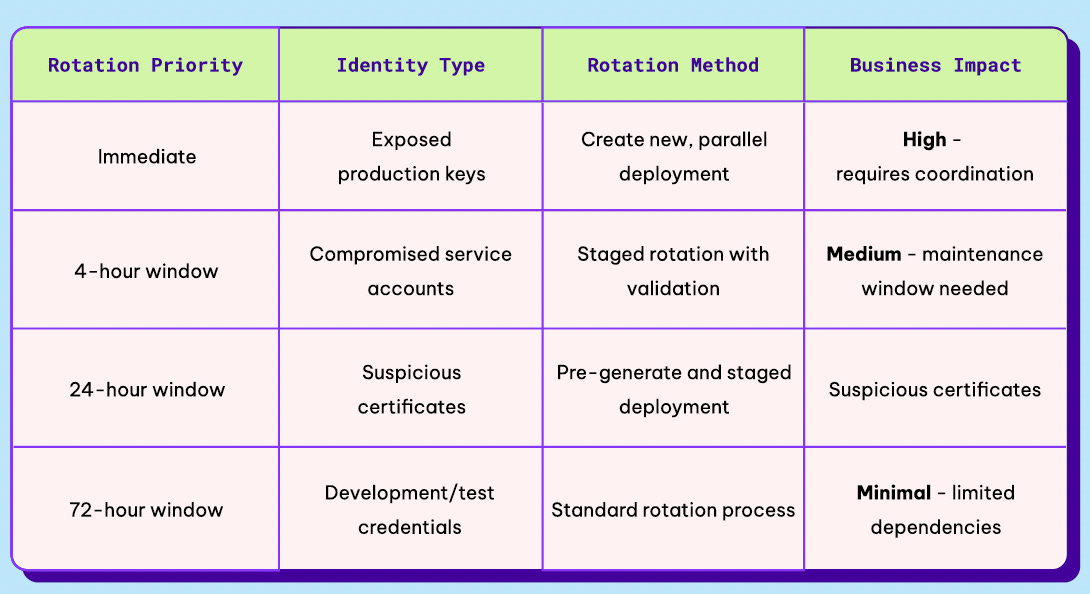
One aspect of the ITDR NHI Guide from Permiso I really liked was the NHI Risk Classification Guide. While it isn’t exhaustive, it can help organizations put some guardrails around how they prioritize alerts and incidents based on organizational context, see below:
Determining how to classify and prioritize NHI risks is crucial when it comes to IR, as we know that not all incidents in cybersecurity warrant the same level of responsiveness. For example, as Permiso points out, NHIs tied to production data or customer-facing systems are much more critical than test environments that don’t touch production data. This type of analysis is often referred to as conducting a Business Impact Assessment (BIA) in common security frameworks, such as NIST’s CSF or RMF. When paired with an accurate NHI inventory and governance, it can help enable effective ITDR for NHIs.
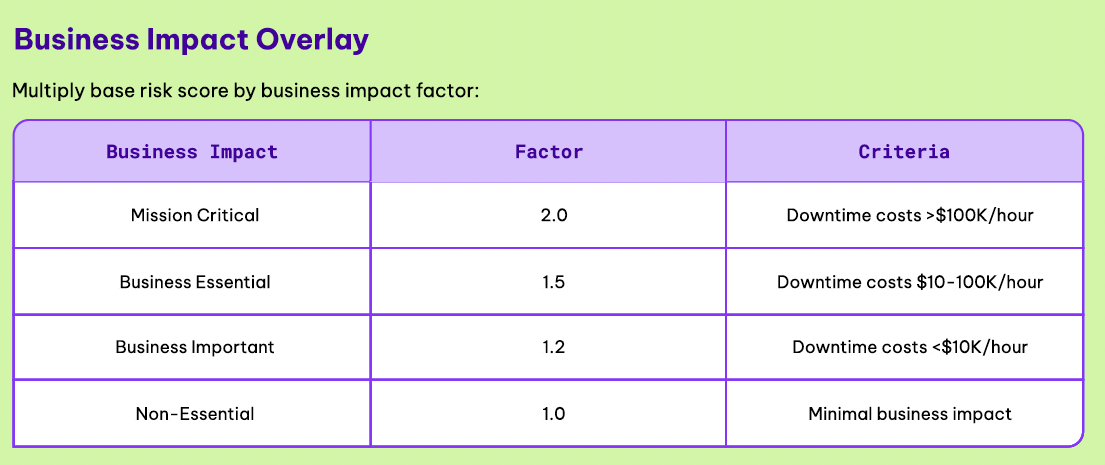
In fact, Permiso lays out an example of a Business Impact Overlay which can be used as part of prioritizing NHI activities focused on security. Each has a different level of business impact and is defined by specific criteria for categorization.
Containing and Investigating NHI Incidents
So, you’ve conducted an initial assessment of your NHI landscape and have some basic structure in place when it comes to classifying NHI risks and preparing to respond when, not if, they happen. The next step is developing containment and investigation strategies.
As Permiso’s guide discusses, NHIs are often more complex than human users when it comes to isolation and resolution. This may involve several applications, or, as we discussed above, be unfortunately lurking in other systems, making their containment and remediation more complicated.
Permiso recommends a structured approach to establishing new credentials, isolating affected systems, enhancing logging, and inspecting to determine malicious activity. Depending on observations, the revocation is escalated accordingly. If an incident isn’t as urgent or impacting critical systems, revocation and rotation can be conducted during scheduled downtime, for example.
Any incident also serves, sometimes painfully, as an opportunity to capture and implement lessons learned to bolster secret management. Permiso’s NHI guide also rightfully points out that malicious actors often establish persistence once they gain an initial foothold, as they exploit compromised credentials to infiltrate organizations.
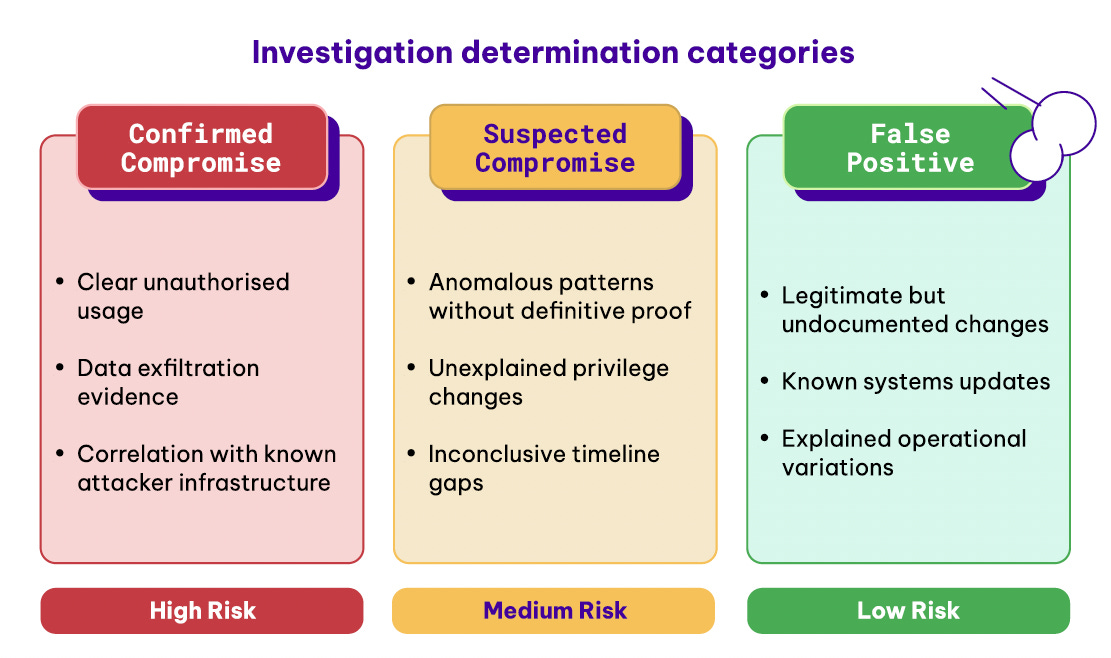
Much like their approach to classifying risks, Permiso provides categories of investigation determination, ranging from a false positive to a confirmed compromise, each with different levels of risk and corresponding levels of response.
We’ve discussed risk classification, investigation, and containment, the last of which involves NHI rotation based on business impact, as seen below:
Even the most urgent NHI rotation tied to high business impact still requires a structured and coherent approach. This is why Permiso recommends generating new credentials, testing their functionality, identifying any missed systems/environments, and revoking the impacted credentials once you confirm that the new credentials are authenticating properly.
You may have already experienced business impact and disruption from the incident itself; you don’t want to exacerbate the situation with a haphazard approach to revocation and rotation.
Bolstering NHI Security
Approaching a concept such as NHI governance and security can be overwhelming, especially considering the broad type of credentials that fall under NHI, and the numerous environments, systems, and applications they apply to.
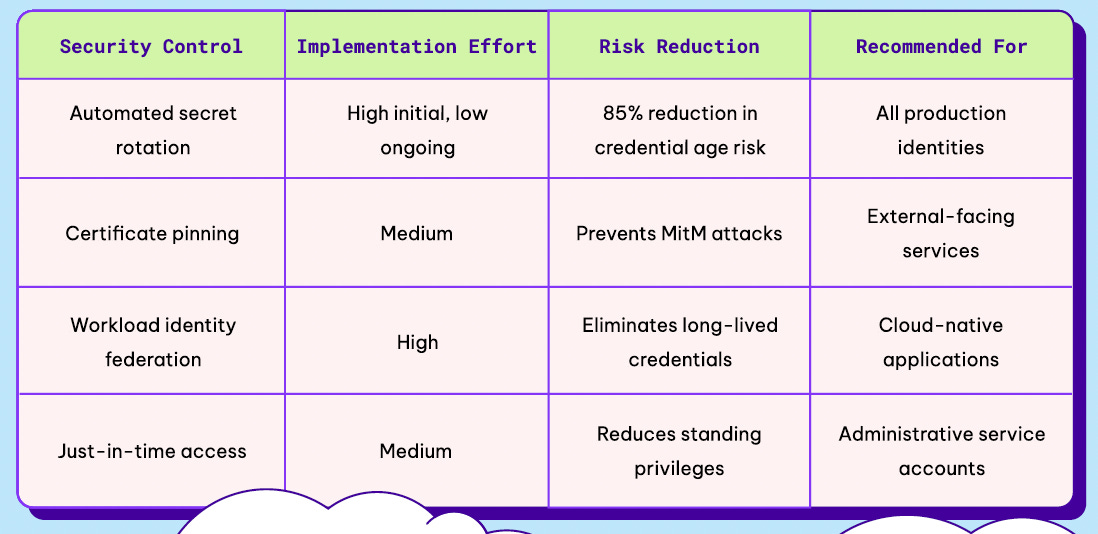
That’s why Permiso’s guide provides recommendations to help make systemic security improvements when it comes to NHI security. They lay out various security controls, each of which has different levels of implementation effort and risk reduction, providing key recommendations on where organizations can get started and make the most significant impact in terms of mitigating organizational risks related to NHIs:
Some activities require a higher implementation effort but mitigate specific risks, while others are less cumbersome to implement but may also be less broad-reaching and impactful.
As Permiso points out, many of the activities we’ve discussed are not one-and-done, but instead require continuous verification and monitoring to ensure they remain ongoing. This encompasses aspects of people, process, and technology.
Organizations require clear policies and processes for activities such as secret storage and rotation, while also conducting routine penetration tests focused on service accounts and API keys to identify deficiencies in technical and procedural controls that require remediation.
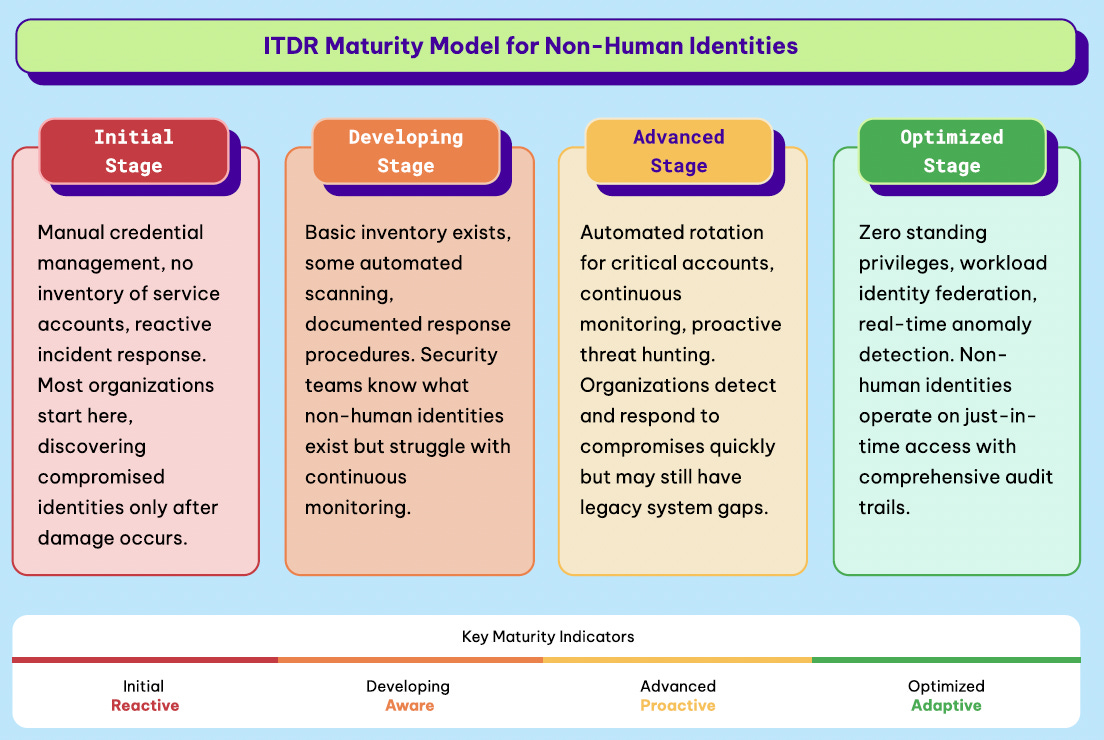
NHI Maturity
Permiso wraps up their NHI ITDR guide, discussing strategic prevention initiatives as well as how to build maturity into organizational NHI ITDR activities. Much like other aspects of cybersecurity, such as AppSec with the OWASP Software Assurance Maturity Model (SAMM), bolstering ITDR related to NHIs requires a structured approach to maturity, given that none of the activities can be accomplished overnight, and many are ongoing.
Permiso lays out some key strategic efforts organizations should focus on, such as:
Adopting workload identity federation wherever possible
Building secrets management into your development pipeline
Implementing comprehensive secret scanning across your entire digital footprint
Permiso even provides an ITSDR Maturity Model for NHIs, as seen below:
Regardless of where an organization is on this maturity curve, there is undoubtedly room for improvement, especially with the rise of factors such as Agentic AI. The ITDR Playbook concludes by providing an NHI Risk Assessment Matrix and a Risk Scoring Framework, which organizations can use to conduct an internal assessment of their NHI security controls, policies, and technical capabilities.
This helps organizations measure their current position versus their desired position in terms of NHI security. I definitely recommend giving it a try and identifying where your organization has gaps, especially as NHIs continue to grow exponentially in numbers, as well as increase in visibility on the radar of malicious actors looking to exploit organizations.
We will inevitably continue to see NHI incidents in the months and years to come. Still, by implementing the Permiso NHI ITDR Playbook, your organization can get ahead of the curve and be prepared for this growing attack vector.




For NHI’s, getting ITDR right means ensuring every user, system, and device is continuously verified, every identity event is monitored in real time, and any anomaly is contained within minutes because in healthcare, identity protection is patient protection.