CVE Cost Conundrums
Unpacking Chainguard’s “Cost of CVEs 2025” Report
If you’ve been following me for any time, you know I often speak about the absolutely overwhelming and cumbersome nature of the current vulnerability landscape. Teams are drowning in vulnerability backlogs, the pace of CVEs year-over-year (YoY) is only worsening, and attackers have a porous and problematic attack surface to make a field day of.
That said, what is the real cost of CVE toil?
The blunt truth is that toiling away with CVEs isn’t a value-added activity for organizations, nor is it part of their core competency, which leads to increased revenue, customer attraction/retention, or value delivery—it’s become the cost of doing business.
As it turns out, that cost is massive.
This new report from Chainguard investigates exactly that topic, and the findings are pretty damning.
Let’s review the “Cost of CVEs” report from Chainguard!
You can grab a copy here if you want to dive deeper into the report.
Setting the Stage
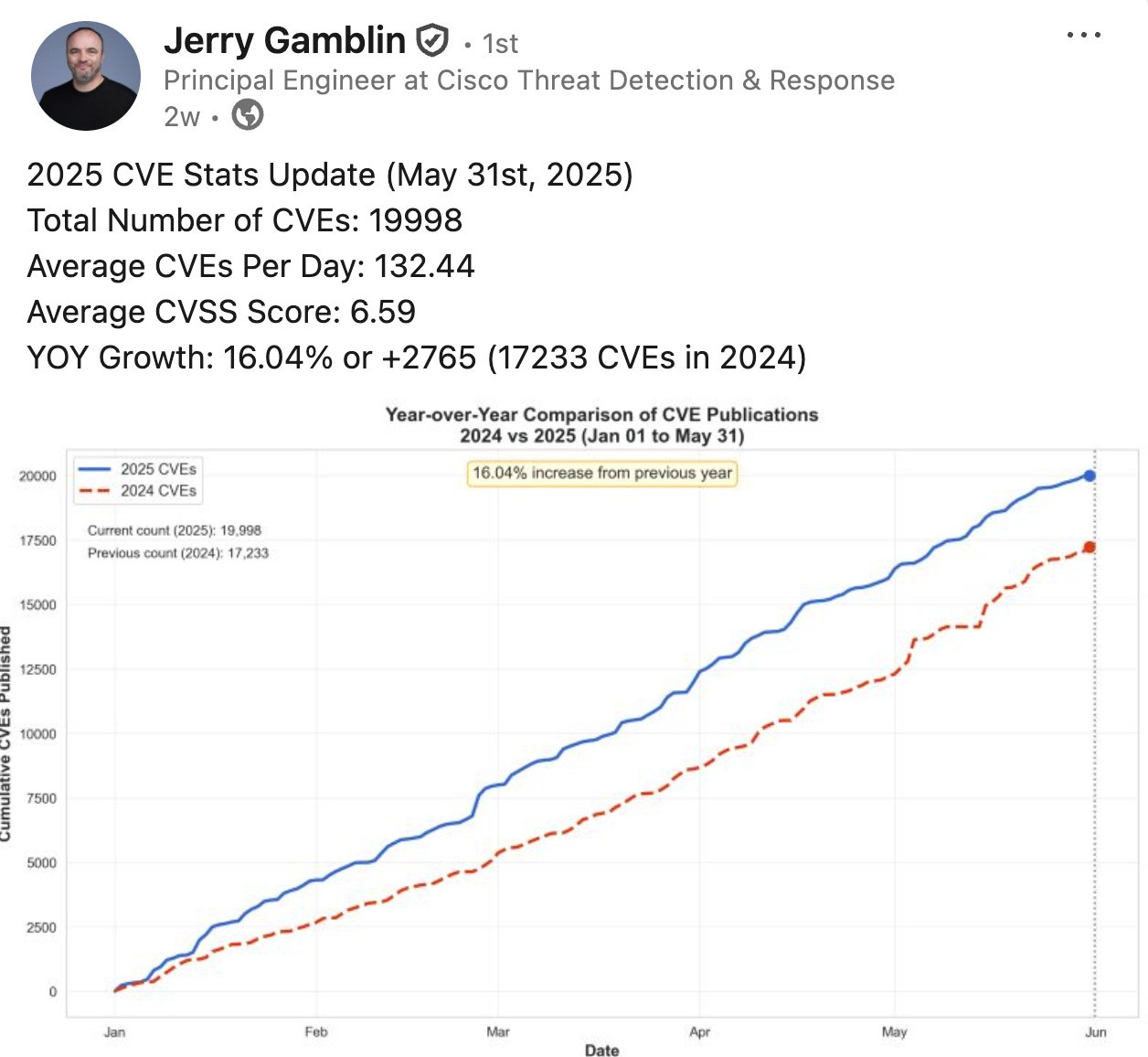
Before walking through the key findings, I wanted to emphasize how problematic the CVE landscape is. Vulnerability Researcher, Jerry Gamblin, whose insights I often share, sums it up best:
We’ve already exceeded 20,000 CVEs as of June 2025, with no signs of slowing down. That’s double-digit growth year-over-year (YoY), and it’s safe to say that organizations’ internal vulnerability teams haven’t magically experienced double-digit effectiveness and productivity gains from 2024. This means vulnerability backlogs will likely accumulate, leading to missed compliance requirements, deviations from SLAs, diminished trust among customers, and an ever-growing attack surface for attackers.
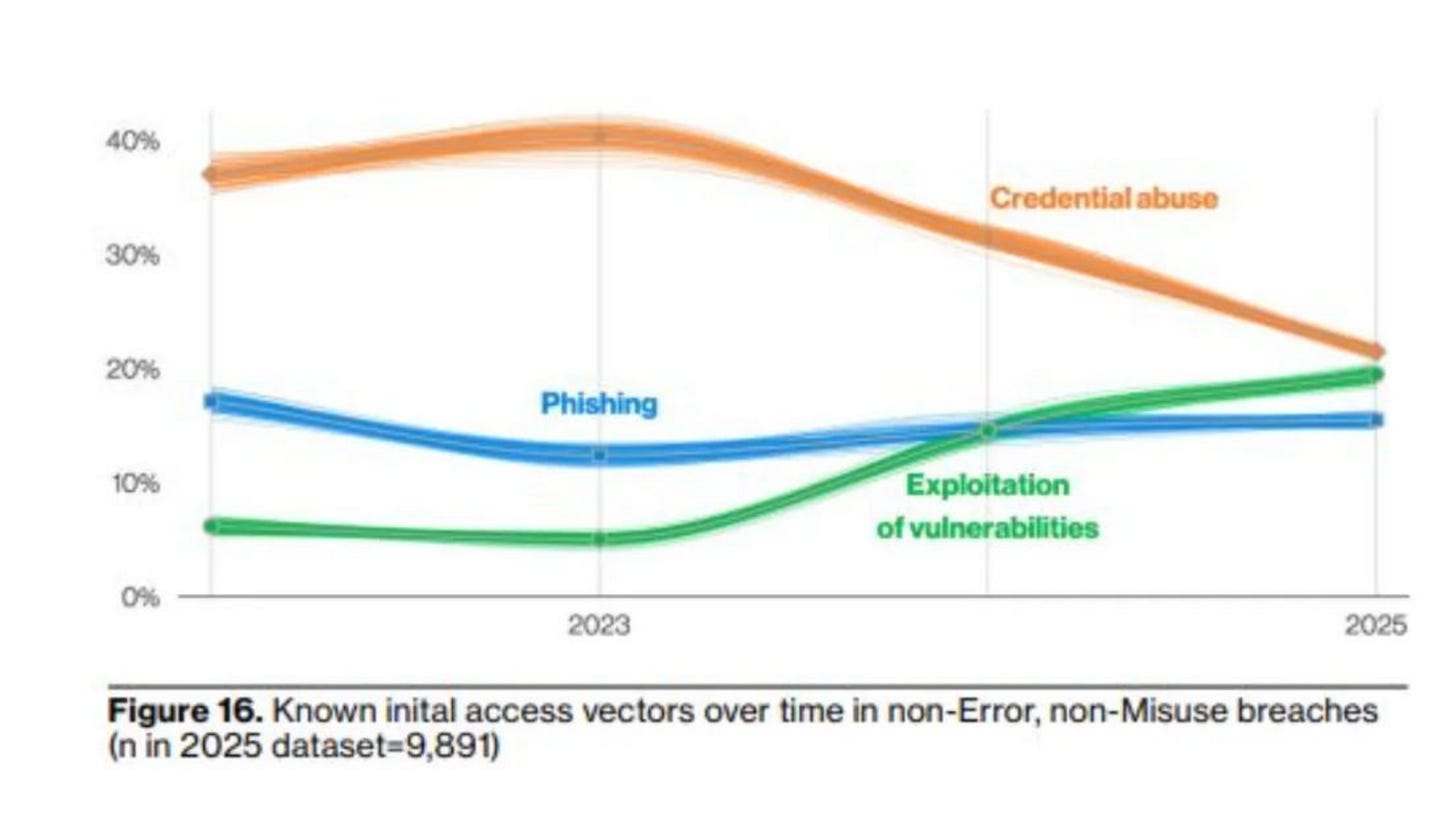
You don’t have to take my word for it either. Verizon’s DBIR demonstrated that exploitation of vulnerabilities is on the rise, surpassing phishing and posing a potential threat to credential abuse, which traditionally dominates the report.
Similarly, Google’s M-Trends report this year showed that vulnerability exploitation was the initial infection vector for 2024.
This demonstrates that organizations are drowning in vulnerabilities, and attackers know it.
Key Findings
Before diving into the weeds, let’s take a look at some of the key findings. Chainguard points out that engineering and development teams spend inordinate amounts of time on activities such as CVE management and triaging, patching, and compliance reporting, and they rightfully point out that this distracts teams from actual revenue-generating activities such as feature development and innovation.
There’s a reason security is often viewed as a cost center, and those costs sting even worse when we acknowledge that the overwhelming majority of organizations’ vulnerability management activities are driven by legacy prioritization requirements, such as fixing all vulnerabilities with High and Critical CVSS base scores. The problem, of course, is that 95%~ of those vulnerabilities are not critical whatsoever and are never exploited in a given year, and fail to account for factors such as known exploitation, exploitation probability, reachability, or compensating controls.
They are, in effect, noise.
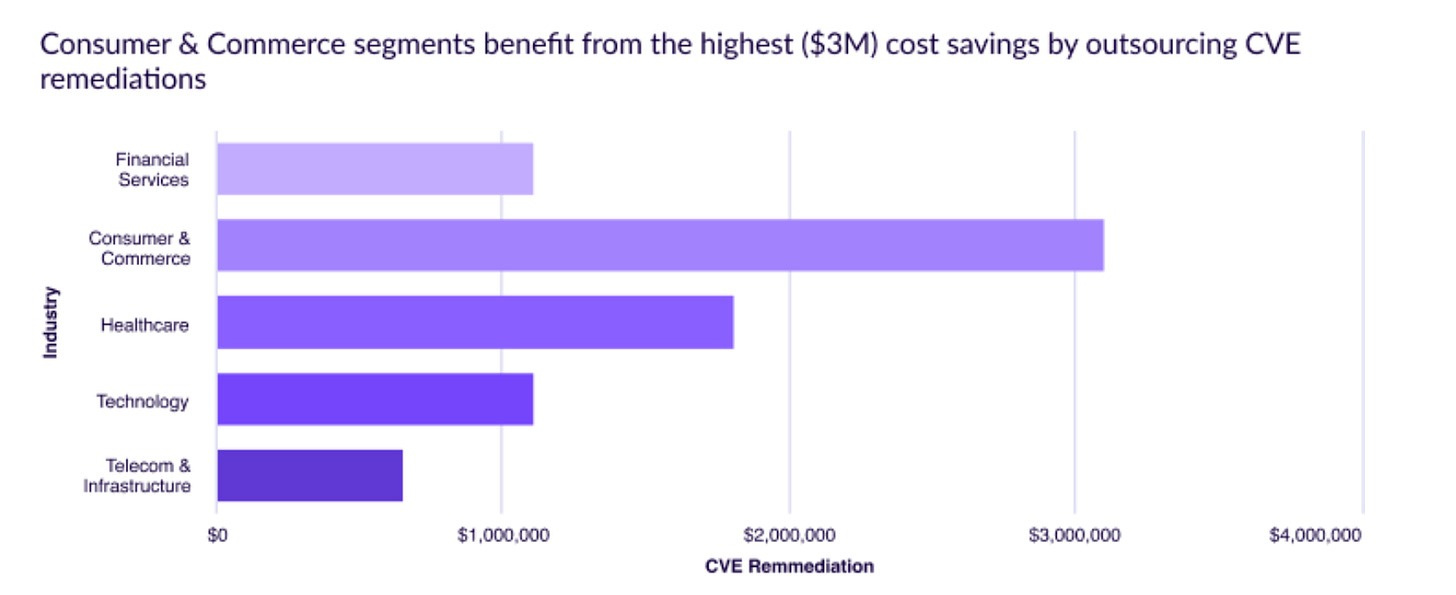
Most organizations do CVE remediation themselves, leading to significant costs in time, effort, and resources. Organizations don’t typically outsource CVE remediation, but astoundingly, Chainguard cited that those who outsourced to Chainguard realized $2.1 million in annual savings. They found even more substantial savings in specific industries such as insurance and healthcare.
Regardless of the organization’s size, $2.1 million could be quite beneficial, especially if it can be allocated to revenue-generating activities rather than CVE toil, such as unlocking value for customers through increased innovation and faster feature velocity.
We often hear tropes such as “security as a business enabler,” but the time and financial drain of in-house CVE management tell a different story. Chainguard’s report touts that outsourcing CVE management tells a different story, one of actual business value, leading to cost savings, increased revenue, faster innovation, and risk reduction.
Much of this value is delivered through Chainguard Containers and their zero-CVE container images, which free organizations to focus on revenue-generating activities, save time and costs, and streamline compliance requirements.
What’s the real cost of CVE toil?
Now that we’ve reviewed the high-level findings, let’s dive deeper into the report. Chainguard rightly points out the challenges with container CVEs and notable vulnerabilities in the last several years, such as Log4Shell and Ingress-NGINX, to name a couple (among many others). Every time a new impactful CVE is published, security teams are left scrambling to try and figure out key questions such as:
Are we impacted?
Where is it running in our environment?
Who’s responsible for the impacted systems?
How quickly can we remediate it?
What is the business impact of doing so, or conversely, the risk acceptance of not doing so?
Security teams begin furiously engaging their development and engineering peers with lengthy spreadsheets and vulnerability reports and obtuse language such as CVSS scores, severities, compliance requirements, and more, further fracturing the rapport between security and their peers and reinforcing the fact that dealing with security can be time-consuming and frustrating for the business.
Chainguard’s latest report builds on previous reporting they published, such as “The True Cost of CVE Management in Containers,” which I cited in my book Effective Vulnerability Management. This latest report boasts insights from organizations of various shapes, sizes, and industry verticals.
The study’s results were provided using factors such as cost savings, increased revenue, faster innovation, and decreased risk. This involved looking at things such as reduced time spent hardening images, meeting compliance requirements, unlocking new revenue opportunities, revenue generation through product development, and potential loss avoidance from container-based breaches.
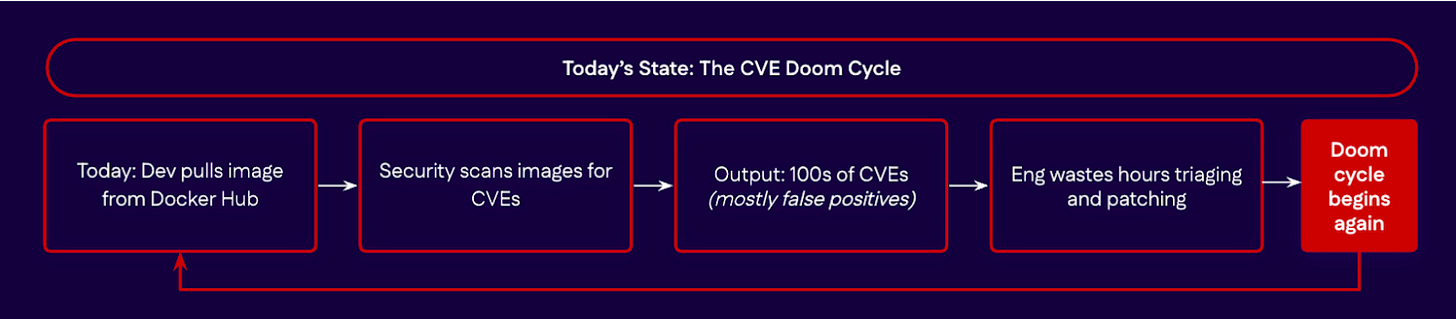
The Do It Yourself (DIY) Doom Cycle
As we discussed, most organizations handle CVE remediation entirely in-house. This involves applying patches for vendor products and software, keeping open source libraries and components up-to-date with the latest/secure versions, and much more.
Chainguard perfectly summarizes the challenges of containers. It describes a common cycle in which Developers pull images from a popular source such as Docker Hub, quickly find out from security that the images are highly vulnerable, get a massive list of findings dumped on them, and then spend hours trying to fix things or justify why findings are false positives and not actual risks, all of which impede delivery and innovation cycles.
As we discussed above, Chainguard found that on average, DIY CVE remediation is costing teams $2.1 million annually, with some industries having higher potential cost savings by outsourcing CVE remediation.
Some of the factors contributing to the increased cost-saving potential include factors such as the tech stack, with some environments having much more dynamic micro-service heavy technologies, where some industries, such as Healthcare, do not necessarily have as much modern tech but are being driven by regulatory factors, where specific compliance frameworks and requirements around vulnerability management and remediation timelines.
Chainguard pointed to many enterprises having “golden image” programs, which I’ve been a part of and have had to contribute to throughout my career. It is an endless cyclical effort to harden and distribute images with minimal vulnerability footprints across the enterprise, ensure you have the various operating systems/images development teams want, and constantly recycle through the process every time new versions of software and vulnerabilities come out. This often involves several dedicated full-time resources and associated costs, which add up for enterprises trying to sustain these golden image programs.
Image Hardening Is…Hard
Another great point of Chainguard’s research is that image hardening is challenging. In a recent blog post titled “This Shit is Hard: Inside the Chainguard Factory,” Chainguard peeled back the curtain on their processes and efforts.
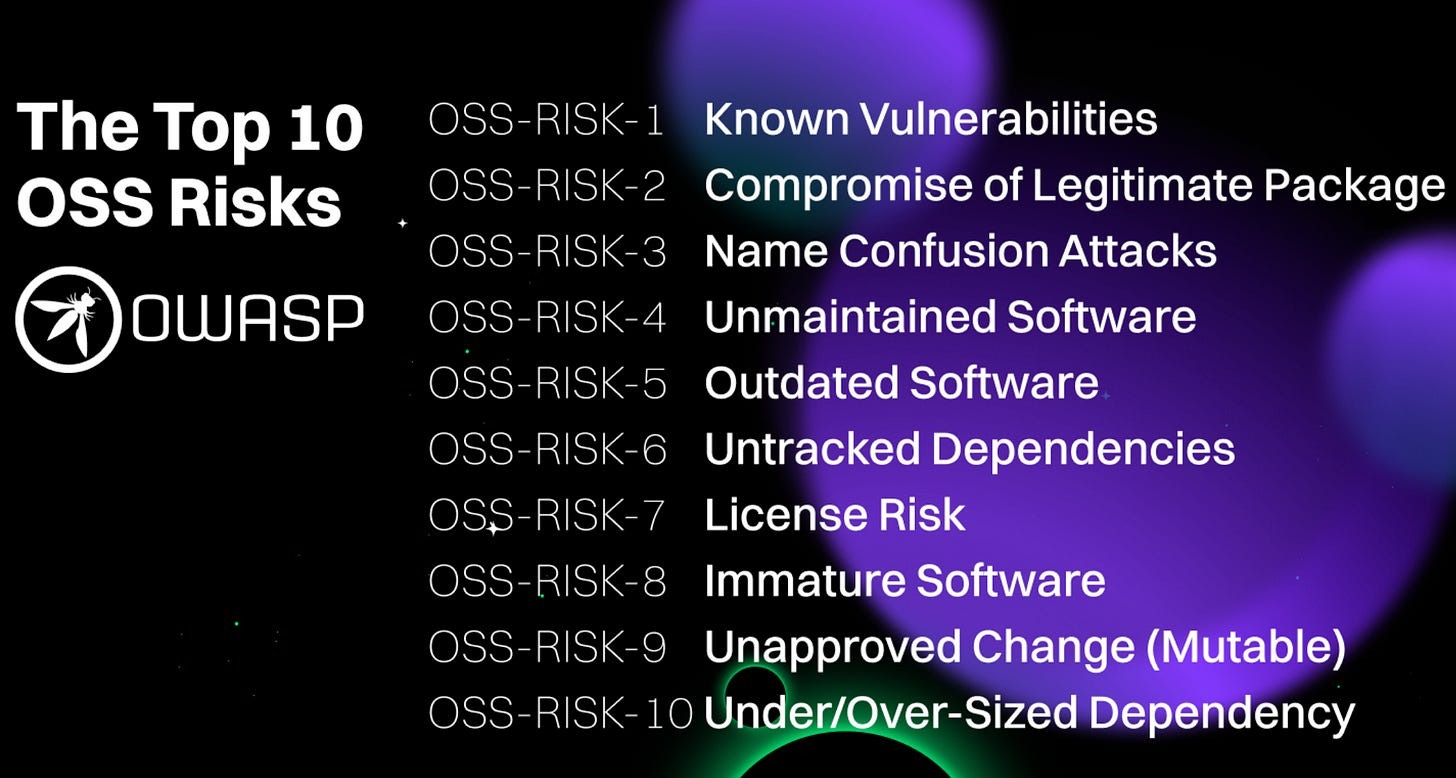
It often involves securing container-based images by minimizing unnecessary packages, applying secure configurations, and enforcing security policies. This addresses problems cited in sources such as the OWASP Open Source Software (OSS) Top 10, such as known vulnerabilities, unmaintained and outdated software, untracked dependencies, and oversized dependencies.
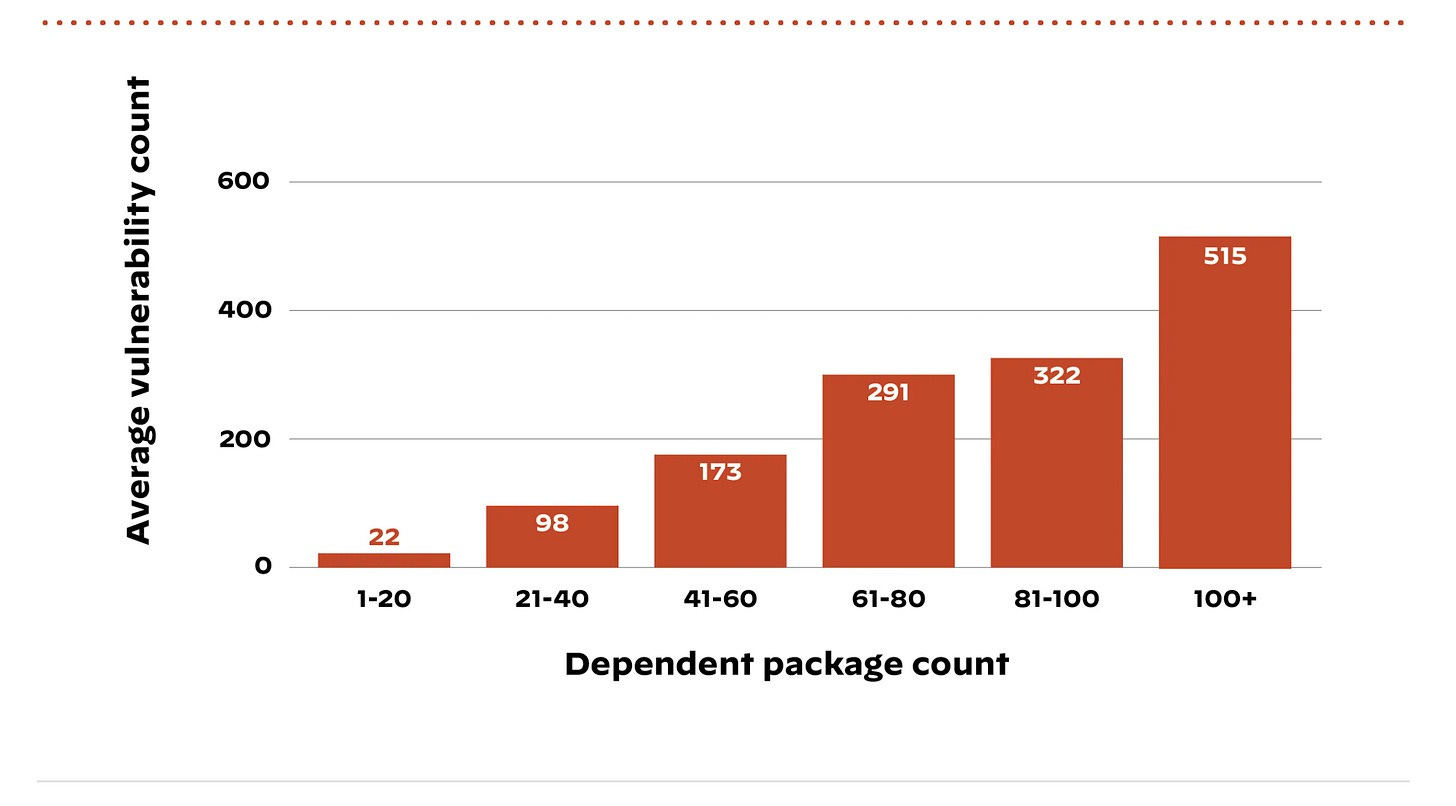
The last is pervasive and problematic in dependency bloat, where images run many libraries and components that aren’t necessary for the application’s function. This brings with it an increased attack surface and vulnerability burden, both making it easier for malicious actors and harder for defenders. It’s been found that the higher the container package count the higher the average vulnerability count, further emphasizing that over-sized containers are bloated with risks for consumers.
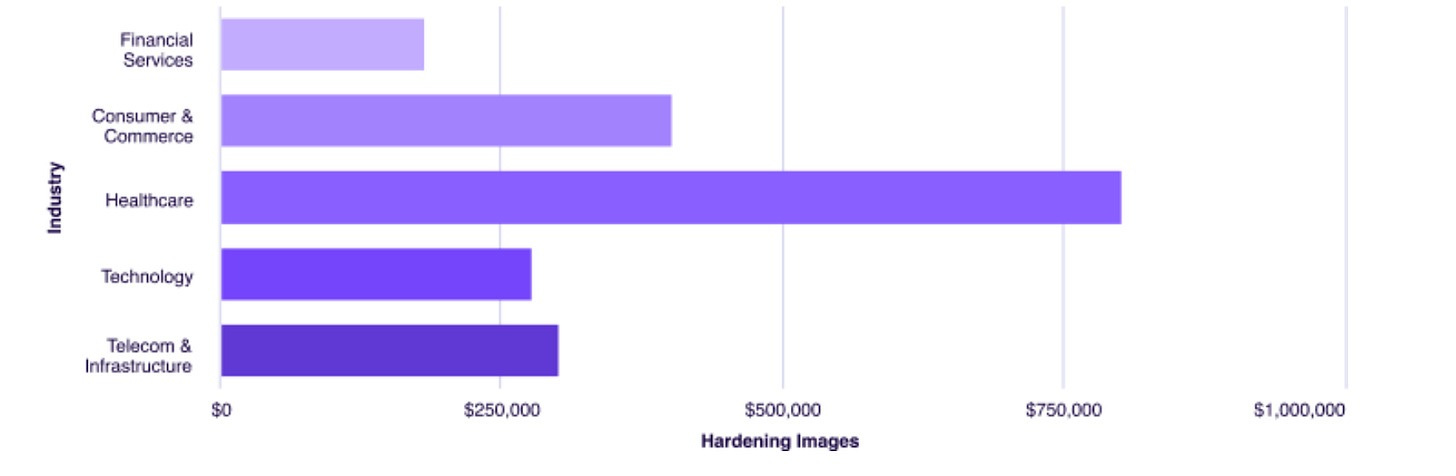
In the era of “Secure-by-Design,” it makes sense to minimize our attack surface and utilize secure base images. However, as the report highlights, doing that activity yourself comes with a substantial cost and distracts from revenue-generating activities. The cost is drastic in some cases, with Chainguard’s report finding that for Healthcare, for example, it is over $800k annually.
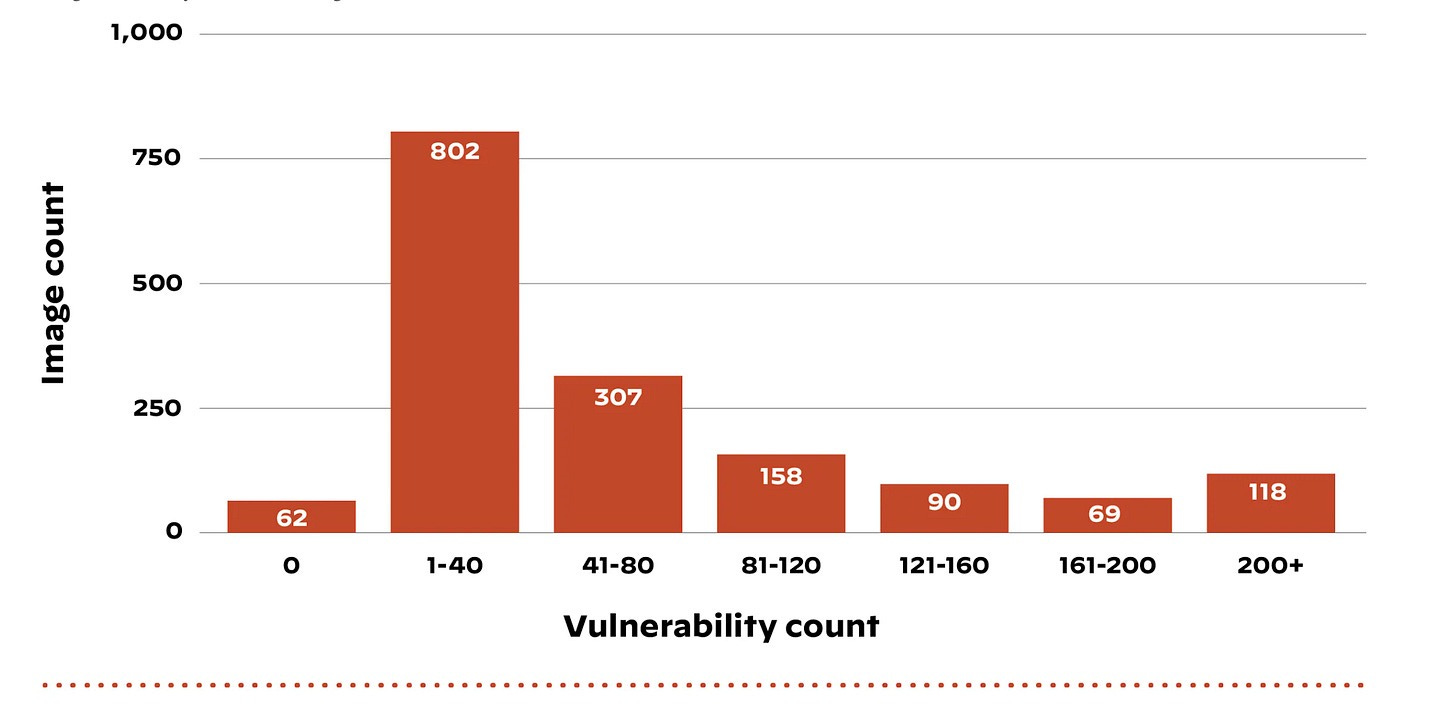
We must remember that some of the primary benefits of containers include being lightweight, portable, easy to distribute, and scalable. Those very same perks become problems when the containers are bloated, inherently insecure, and vulnerable, as the vulnerabilities proliferate across enterprise environments at scale. For example, it’s been reported that containers hosted in popular public registries have vulnerabilities in 96% of the hosted images, with 91% of the available images having at least one critical or high finding. Many organizations lack internal secure/hardened container repositories, with developers grabbing publicly available images and ingesting the associated risks alongside those images.
Compliance is Cumbersome (and Costly)
One undeniable fact nearly all cyber practitioners can agree on is that compliance is cumbersome. FedRAMP, HIPAA, HISTRUST, SOC2, 800-171, RMF, NIS2, DORA, and the acronym soup goes on. While many similarities exist across these compliance frameworks, they each have unique vulnerability management and remediation considerations. This equates to tremendous work for organizations to meet compliance requirements.
One callout by the Chainguard report I was happy to see mentioned increased compliance achievement, allowing organizations to tap into various highly regulated environments. Many markets have compliance frameworks and requirements, making it one of the leading questions from potential prospects and customers.
Demonstrating strong compliance and sound vulnerability management with minimal residual risks can boost customer credibility and trust.
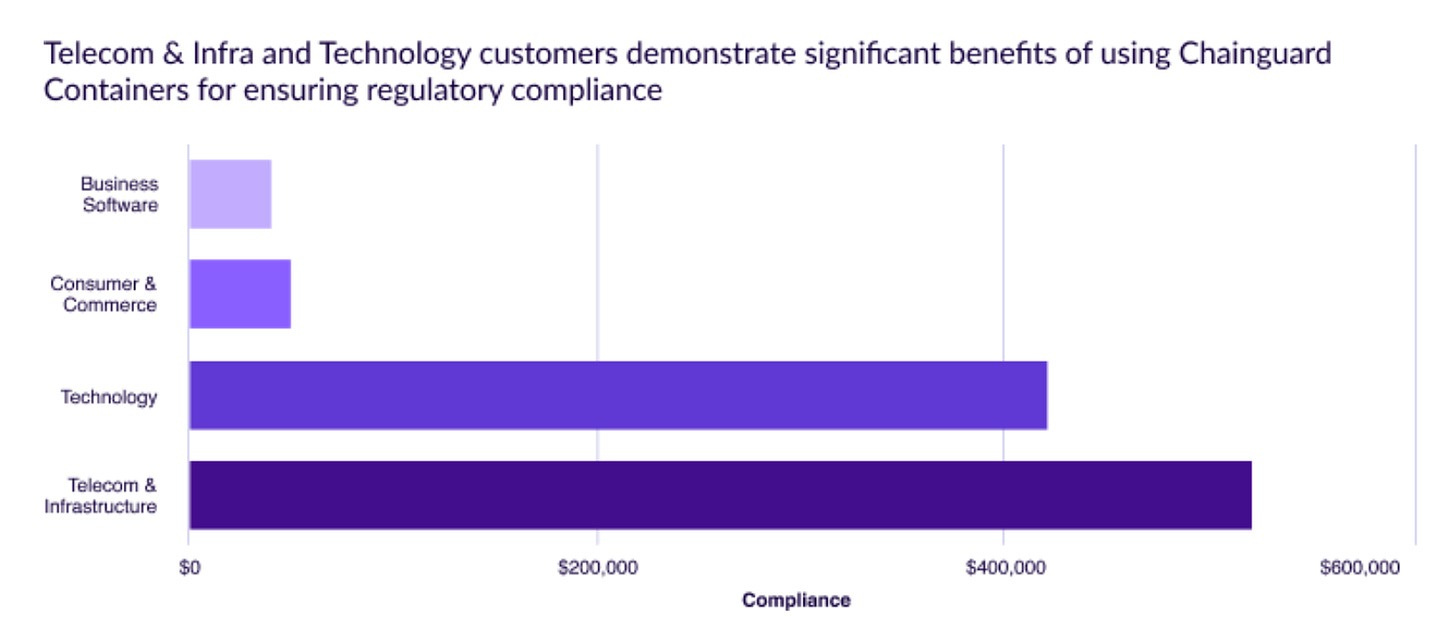
Chainguard found that technology, telecom, and infrastructure customers experience the most significant benefits of using Chainguard Containers for regulatory compliance.
As Chainguard points out, remediating vulnerabilities is often just a first step, as compliance requirements also include things such as adhering to standards for Federal Information Processing Standards (FIPS), encryption and Security Technical Implementation Guides (STIG)’s, as well as maintaining cumbersome documents related to plans to address residual risks and vulnerabilities (e.g. FedRAMP and the requirement for Plans of Actions and Milestones).
As a practitioner who has lived and breathed these exact requirements in environments such as the DoD and Federal space, this often equates to spending as much or more time just tracking residual risks and findings as you do fixing them, frequently drowning both the security and engineering teams involved and detracting from the time they can spend delivering value to customers and stakeholders and contributing to euphemisms associated with cybersecurity such as “security theater”.
Business Enablement Benefits
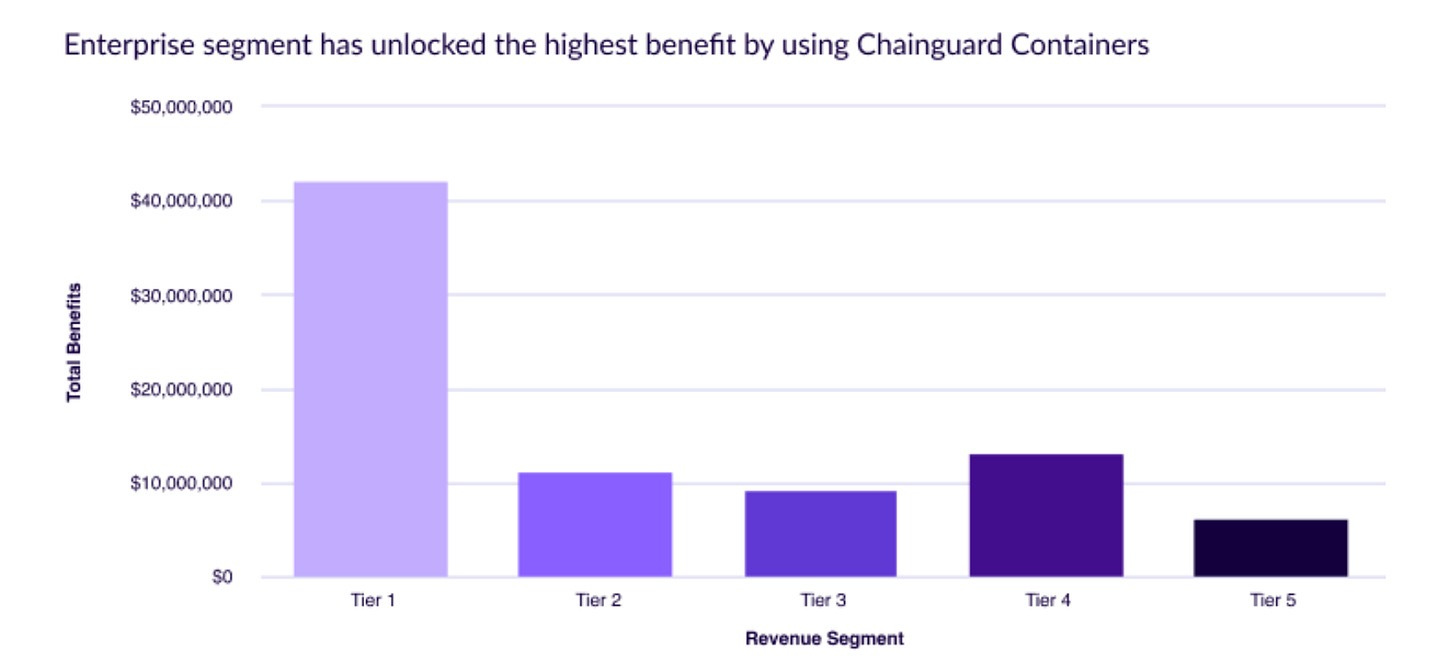
Another overlooked aspect of outsourcing CVE management is the benefits of business enablement. We hear a lot about security being a business enabler. As the Chainguard reports point out, CVEs being passed down in products and services to savvy consumers lead to customer escalations, with customers inquiring about vulnerabilities, remediation status, SLA, and mitigating controls. Organizations leaning into outsourced CVE management found an annual average savings of $70,000, with some sectors such as technology having outsized benefits approaching an annual average saving of $147,000. Mid-market and growth-stage companies experienced even more benefits, with an average savings of $327,000.
Rather than passing the vulnerability toil on to developers, engineers, and, worse, customers, those leaning into outsourced CVE management experience internal cost savings and more secure customer outcomes and trust, as demonstrated by Chainguard.
Some of the business-specific benefits cited by Chainguard include avoiding procurement delays, not breaching contractual SLA’s, avoiding disruptions to sensitive clinical systems, improved vendor assessments and overall improved customer trust, which is the currency of the cybersecurity ecosystem, as discussed by my friend
Ross Haleliuk in his article “Time to Trust: What it is, why cybersecurity must shorten it to accelerate growth, and how to do it”.
Business Value Over Vulnerabilities
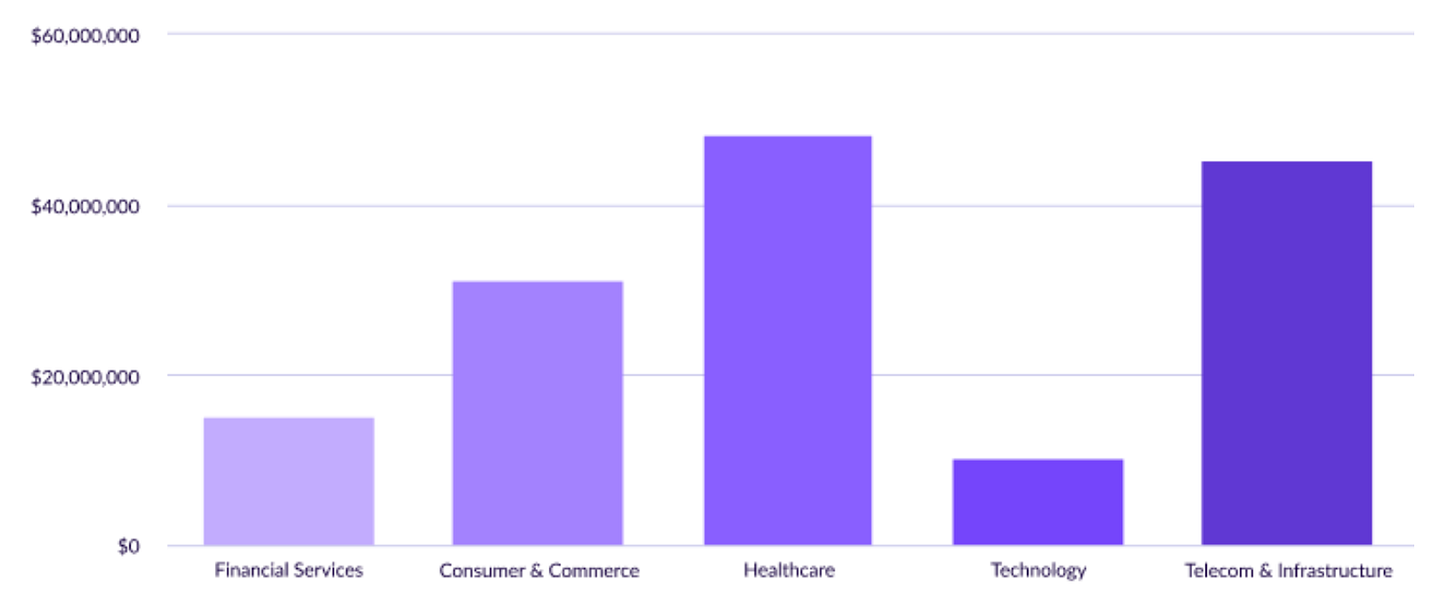
While the first part of the Chainguard report focused on cost savings, the report discusses value unlocked in critical areas such as increased revenue, faster innovation, and decreased risks. This is where the figures truly become impressive. Below, they share the amounts that organizations across each sector shared with them as part of the report process.
Sectors such as Healthcare touted $50 million in value, $39 million of which came from risk reduction tied to security breaches tied to sensitive data, regulatory requirements, and revenue loss from breaches caused by factors such as customer attrition and loss of market share.
As we mentioned earlier, too, it isn’t just savings that the organizations surveyed who adopted secure container practices and outsourced CVE management were able to add revenue through unlocking new markets and customers.
Similar trends are cited across other sectors in the report, such as Telecom, Consumer and commerce, Financial Services, and Tech. Each reaps rewards such as reduced risks, revenue gains, and improved market dynamics while offloading the tedious and cumbersome activities associated with vulnerability management.
Again, that’s tens of millions of value unlocked through a combination of decreased risk, faster innovation, and increased revenue. This includes benefits such as the ability to roll out products and services faster, shorten innovation cycles, outpace competitors, and deliver more value to customers.
While the figures speak for themselves, I want to emphasize here again, as I mentioned earlier, the importance of organizations being able to focus on their core competencies and deliver value to customers rather than the never-ending cyclical activities of vulnerability scanning, reporting, and remediation.
A great analogy here is thinking about cloud computing. One of the primary benefits was that consumers of cloud were able to focus on their core competencies as a business and their customers, rather than activities such as building or sustaining data centers, running cables, standing up physical infrastructure, physical security, media sanitization and the countless other activities now absorbed by CSPs that we take for granted.
The same thing can and is happening through outsourced CVE management.
With offerings such as Chainguard Containers, and organizations increasingly running containerized workloads, a trend only poised to grow with the rapid adoption of AI, organizations are waking up to the reality that CVE management is a burden and distraction, and one that they can outsource rather than shoulder alone.
It’s clear that Chainguards’ offering resonates with customers, as demonstrated by the team’s tremendous growth, which has been further validated by several other vendors now looking to provide a similar offering to the market.
The challenge, however, is that Chainguard has a first-mover advantage and has demonstrated that it has no plans to slow down.
Be sure to check out Chainguard Containers to learn more!